Integration of Uavs with Real Time Operating Systems And
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Signature Redacted
Long-range Outdoor Monocular Localization with Active Features for Ship Air Wake Measurement by Brandon J. Draper B.S., Aerospace Engineering, Univ. of Maryland, College Park (2016) Submitted to the Department of Aeronautics and Astronautics in partial fulfillment of the requirements for the degree of M•s-tttr BBJchdM of Science in Aerospace Engineering at the MASSACHUSETTS INSTITUTE OF TECHNOLOGY February 2019 © Massachusetts Institute of Technology 2019. All rights reserved. Author..-Signature redacted . ................ Departme~t of Aeronautics and Astronautics October 1, 2019 Signature redacted Certified by .......... Jonathan P. How R. C. Maclaurin Professor of Aeronautics and Astronautics, MIT Thesis Supervisor --- . / Signature redacted Accepted by .... \..._..,/ Sertac Karaman Associate Professor of Aeronautics and Astronautics, MIT MASSACHUSETTSINSTITUTE Chair, Graduate Program Committee OF TECHNOLOGY MAR 12 2019 LIBRARIES ARCHIVES 2 Long-range Outdoor Monocular Localization with Active Features for Ship Air Wake Measurement by Brandon J. Draper Submitted to the Department of Aeronautics and Astronautics on October 1, 2019, in partial fulfillment of the requirements for the degree of Bachelor of Science in Aerospace Engineering Abstract Monocular pose estimation is a well-studied aspect of computer vision with a wide ar- ray of applications, including camera calibration, autonomous navigation, object pose tracking, augmented reality, and numerous other areas. However, some unexplored areas of camera pose estimation remain academically interesting. This thesis provides a detailed description of the system hardware and software that permits operation in one application area in particular: long-range, precise monocular pose estimation in feature-starved environments. The novel approach to pose extraction uses special hardware, including active LED features and a bandpass-interference optical filter, to significantly simplify the image processing step of the Perspective-n-Point (PnP) problem. -

Team Members: Pooja Bansal (Pbansal2) Suraj Shanbhag (Smshanbh)
ARDUROVER with BBBmini Project made for ECE 785 Advanced Computer Design Team Members: Pooja Bansal (pbansal2) Suraj Shanbhag (smshanbh) OVERVIEW: The aim of the project was to interface the beaglebone with the APM rover in order to impart autonomy to the vehicle. The idea was to make the beaglebone as the gateway between the remote control and the vehicle and also interface with the sensors and communicate with the Ground Control Station(GCS) to give the commands to the rover. The GCS software is called Mission Planner and it runs on Windows OS. This report contains the details about the hardware and software required and procedure to be followed to build and launch the system. HARDWARE: The basic hardware consists of a rover built to be compatible with the APM arduover software (we used the APM rover provided to us), Beagle Bone Black which forms the heart of the system, the BBB mini which is a cape on the BBB to interface with the other sensors and the Remote Control for providing the motion commands to the rover. The hardware of the BBBMini requires the following sensors: 1. MPU-9250 IMU 2. MS5611 barometer 3. 3Dr GPS 4. Wifi adapter 5. RC remote (Taranis capable of combined PWM output on one pin) When all these components are connected to the beaglebone, an external power supply is required. In this project a battery pack with usb output of 5V and 2A was used. The connections are as shown below. The output to servo and ESC has to be on RC2(servo) and RC4(throttle). -

Dragon Bee University of Central Florida EEL 4915C Senior Design II Spring 2016 Group 34
Dragon Bee University of Central Florida EEL 4915C Senior Design II Spring 2016 Group 34 Group Members Ayoub Soud(CpE) Younes Enouiti (EE) Akash Patel(CpE) Nishit Dave(EE) Table of Content 1 Executive Summary…………………………………………………………..……1 2 Project Description ………………………………………………………..………2 2.1 Project Motivation……………………………………………….…………2 2.2 Goals and Objectives…………………………………………..………….3 2.3 Specifications………………………………………………………….……4 2.4 Design Constraints and Standards……………….…………………….. 5 2.4.1 Battery/Power Consumption……………………………...…….11 2.4.2 Video Streaming………………………………………………....12 2.4.3 Budget Allocation………………………………..……………….13 3 Research……………………………………………………………………….……..14 3.1 Quad Rotor Frame…………………………………………………………14 3.1.1 Quad Rotor Frame……………………………………………….14 3.1.2 Motors………………………………………………………..……16 3.1.3 Propellers……………………………………………….…….......20 3.1.4 Electric Speed Controllers (ESC)……………………………... 21 3.1.5 Flight Controller/ArduPilot……………………………………….22 3.2 Microcontroller………………………………………………..…………….24 3.2.1 PCB………………………………………………………………..26 3.3 Communication Technologies…………………..……………………….. 28 3.3.1 Wi-Fi Module for MSP430……………………………………….30 3.3.2 Ardupilot/MSP430 Communication………………..……………31 3.4 Position Detection Sensors………………………..………………………35 3.4.1 Ultrasonic Sensors………………………..………………………35 3.5 Wi-Fi Camera………………………………………….……………………..36 3.6 GPS…………………………………………………….……………………. 38 3.7 Power Consumption Management…………………………………………41 3.7.1 Batteries…………………………………………………………….43 3.7.2 Power Module ……………………………..………………………46 3.7.3 Power Distribution Board …………………………….…………..47 -
Attachment A
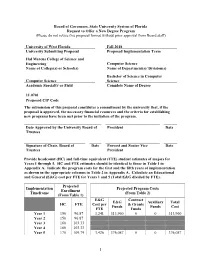
Board of Governors, State University System of Florida Request to Offer a New Degree Program (Please do not revise this proposal format without prior approval from Board staff) University of West Florida Fall 2018 University Submitting Proposal Proposed Implementation Term Hal Marcus College of Science and Engineering Computer Science Name of College(s) or School(s) Name of Department(s)/ Division(s) Bachelor of Science in Computer Computer Science Science Academic Specialty or Field Complete Name of Degree 11.0701 Proposed CIP Code The submission of this proposal constitutes a commitment by the university that, if the proposal is approved, the necessary financial resources and the criteria for establishing new programs have been met prior to the initiation of the program. Date Approved by the University Board of President Date Trustees Signature of Chair, Board of Date Provost and Senior Vice Date Trustees President Provide headcount (HC) and full-time equivalent (FTE) student estimates of majors for Years 1 through 5. HC and FTE estimates should be identical to those in Table 1 in Appendix A. Indicate the program costs for the first and the fifth years of implementation as shown in the appropriate columns in Table 2 in Appendix A. Calculate an Educational and General (E&G) cost per FTE for Years 1 and 5 (Total E&G divided by FTE). Projected Implementation Projected Program Costs Enrollment Timeframe (From Table 2) (From Table 1) E&G Contract E&G Auxiliary Total HC FTE Cost per & Grants Funds Funds Cost FTE Funds Year 1 150 96.87 3,241 313,960 0 0 313,960 Year 2 150 96.87 Year 3 160 103.33 Year 4 160 103.33 Year 5 170 109.79 3,426 376,087 0 0 376,087 1 Note: This outline and the questions pertaining to each section must be reproduced within the body of the proposal to ensure that all sections have been satisfactorily addressed. -

Downloaded Model to the Curved Shape of the IRIS+ Belly
Abstract This project involves the design of a vision-based navigation and guidance system for a quadrotor unmanned aerial vehicle (UAV), to enable the UAV to follow a planned route specified by navigational markers, such as brightly colored squares, on the ground. A commercially available UAV is modified by attaching a camera and an embedded computer called Raspberry Pi. An image processing algorithm is designed using the open-source software library OpenCV to capture streaming video data from the camera and recognize the navigational markers. A guidance algorithm, also executed by the Raspberry Pi, is designed to command with the UAV autopilot to move from the currently recognized marker to the next marker. Laboratory bench tests and flight tests are performed to validate the designs. Fair Use Disclaimer: This document may contain copyrighted material, such as photographs and diagrams, the use of which may not always have been specifically authorized by the copyright owner. The use of copyrighted material in this document is in accordance with the “fair use doctrine”, as incorporated in Title 17 USC S107 of the United States Copyright Act of 1976. I Acknowledgments We would like to thank the following individuals for their help and support throughout the entirety of this project. Project Advisor: Professor Raghvendra Cowlagi II Table of Authorship Section Author Project Work Background Real World Applications AH N/A Research AH N/A Navigation, Guidance, and Control JB N/A GPS AH N/A Python and OpenCV JB, KB N/A System Design Image Processing -

A Step-By-Step Guidance to Build a Drone from Scratch Using Ardupilot APM Navio2 Flight Controller
A step-by-step guidance to build a drone from scratch using Ardupilot APM Navio2 Flight controller Prepared by Sim Kai Sheng Yew Chang Chern 1 Table of Contents Full Component List ............................................................................................................................... 1 Navio2 Emlid Flight Controller ................................................................................................ 2 Raspberry Pi3 Model B ............................................................................................................ 2 Airframe .................................................................................................................................. 3 Motors 2216/950KV ................................................................................................................ 4 Electronic Speed Controller (ESC) ........................................................................................... 5 Propellers ................................................................................................................................ 6 GNSS receiver with antenna ................................................................................................... 7 Transmitter ............................................................................................................................. 8 Receiver ................................................................................................................................... 8 MicroSD card .......................................................................................................................... -

Implementation of a Trusted I/O Processor on a Nascent Soc-FPGA Based Flight Controller for Unmanned Aerial Systems
Implementation of a Trusted I/O Processor on a Nascent SoC-FPGA Based Flight Controller for Unmanned Aerial Systems Akshatha J Kini Thesis submitted to the Faculty of the Virginia Polytechnic Institute and State University in partial fulfillment of the requirements for the degree of Master of Science in Computer Engineering Cameron D. Patterson, Chair Paul E. Plassmann Lynn A. Abbott February 21, 2018 Blacksburg, Virginia Keywords: SoC, UAV, FPGA, ZYNQ, MicroBlaze, autopilot, ArduPilot, ArduPlane, GPS, Mission Planner, Sensor, Vulnerabilities, Mailbox Copyright 2018, Akshatha J Kini Implementation of a Trusted I/O Processor on a Nascent SoC-FPGA Based Flight Controller for Unmanned Aerial Systems Akshatha J Kini (ABSTRACT) Unmanned Aerial Systems (UAS) are aircraft without a human pilot on board. They are comprised of a ground-based autonomous or human operated control system, an unmanned aerial vehicle (UAV) and a communication, command and control (C3) link be- tween the two systems. UAS are widely used in military warfare, wildfire mapping, aerial photography, etc primarily to collect and process large amounts of data. While they are highly efficient in data collection and processing, they are susceptible to software espionage and data manipulation. This research aims to provide a novel solution to enhance the secu- rity of the flight controller thereby contributing to a secure and robust UAS. The proposed solution begins by introducing a new technology in the domain of flight controllers and how it can be leveraged to overcome the limitations of current flight controllers. The idea is to decouple the applications running on the flight controller from the task of data validation. -

Conceptual Design Document
Aerospace Senior Projects ASEN 4018 2017 University of Colorado Department of Aerospace Engineering Sciences Senior Projects – ASEN 4018 SHAMU Search and Help Aquatic Mammals UAS Conceptual Design Document 2 October 2017 1.0 Information Project Customers Jean Koster James Nestor 872 Welsh Ct. Louisville, CO 80027 San Francisco, CA Phone: 303-579-0741 Phone: Email: [email protected] Email: [email protected] Team Members Severyn V. Polakiewicz Samuel N. Kelly [email protected] [email protected] 818-358-5785 678-437-6309 Michael R. Shannon Ian B. Barrett [email protected] [email protected] 720-509-9549 815-815-5439 Jesse R. Holton Grant T. Dunbar [email protected] [email protected] 720-563-9777 720-237-6294 George Duong Brandon Sundahl [email protected] [email protected] 720-385-5828 303-330-8634 Benjamin Mellinkoff Justin Norman [email protected] [email protected] 310-562-3928 303-570-5605 Lauren Mcintire [email protected] 267-664-0889 Conceptual Design Assignment Conceptual Design Document 2017 Aerospace Senior Projects ASEN 4018 1.1 List of Acronyms AP Autopilot API Application Programming Interface ARM Advanced RISC Machine A(M)SL Above (Mean) Sea Level CETI Cetacean Echolocation Translation Initiative CLI Command Line Interface CPU Central Processing Unit CONOPS Concept of Operations COTS Commercial Off The Shelf EPS Expanded Polystyrene FBD Functional Block Diagram GCS Ground Control Station GPS Global Positioning System GPU Graphics Processing -

Problems and Alternative Approaches Expanding the Scope of Software
Expanding the Scope of Software Product Families: Problems and Alternative Approaches Jan Bosch VP, Head of Software and Application Technologies Laboratory Nokia Research Center Helsinki, Finland [email protected] © 2006 Nokia QoSA/CBSE 2006/ June 2006 Some background • Nokia Research Center since fall 2004 • Professor and Head of Software Engineering group at University of Groningen, The Netherlands - earlier head of RISE research group @ Blekinge Institute of Technology, Sweden. • Collaboration through research and consulting with, among others, Philips, Bosch, Thales, Baan, Avaya, Ericsson, etc. • Working IEEE/IFIP Conference on Software Architecture series, programme chair (2002), general chair (2004), steering committee member • Software Product Line Conference series • EU and ITEA projects, e.g. SeCSE (Service Centric Software Engineering) © 2006 Nokia QoSA/CBSE 2006/ June 2006 Overview • Introduction • Nokia and Nokia Research Center • Trends in Software • Platforms for Nokia Mobile Devices • Problems and Challenges • Alternative approaches • Conclusions © 2006 Nokia QoSA/CBSE 2006/ June 2006 R&D in Nokia • Global network with R&D centers in 11 countries • Over 20,882 people in R&D at the end of 2005 • R&D personnel represents 36% of Nokia’s total workforce • Nokia’s R&D expenditure totaled EUR 3,825 million in 2005 (11.2% of net sales) All figures are from Dec, 2005 © 2006 Nokia QoSA/CBSE 2006/ June 2006 Nokia Research Center – world-class expertise • Founded in 1986 • 1,097 employees at the end of 2005, or 5% of Nokia’s R&D -

Reef Rover: a Low-Cost Small Autonomous Unmanned Surface Vehicle (USV) for Mapping and Monitoring Coral Reefs
Article Reef Rover: A Low-Cost Small Autonomous Unmanned Surface Vehicle (USV) for Mapping and Monitoring Coral Reefs George T. Raber 1,* and Steven R. Schill 2,* 1 The University of Southern Mississippi, School of Biological, Environmental, and Earth Sciences, Hattiesburg, MS 39406, USA 2 The Nature Conservancy, Caribbean Division, Coral Gables, FL 33134, USA * Correspondence: [email protected] (G.T.R.); [email protected] (S.R.S.); Tel.: +1-1601-434-9489 (G.T.R.); +1-1435-881-7838 (S.R.S.) Received: 8 March 2019; Accepted: 15 April 2019; Published: 17 April 2019 Abstract: In the effort to design a more repeatable and consistent platform to collect data for Structure from Motion (SfM) monitoring of coral reefs and other benthic habitats, we explore the use of recent advances in open source Global Positioning System (GPS)-guided drone technology to design and test a low-cost and transportable small unmanned surface vehicle (sUSV). The vehicle operates using Ardupilot open source software and can be used by local scientists and marine managers to map and monitor marine environments in shallow areas (<20 m) with commensurate visibility. The imaging system uses two Sony a6300 mirrorless cameras to collect stereo photos that can be later processed using photogrammetry software to create underwater high-resolution orthophoto mosaics and digital surface models. The propulsion system consists of two small brushless motors powered by lithium batteries that follow pre-programmed survey transects and are operated by a GPS-guided autopilot control board. Results from our project suggest the sUSV provides a repeatable, viable, and low-cost (<$3000 USD) solution for acquiring images of benthic environments on a frequent basis from directly below the water surface. -

Autonomous Landing of a Multicopter Using Computer Vision
Autonomous Landing of a Multicopter Using Computer Vision Thesis of 30 ECTS submitted to the Department of Computer Science in partial fulfillment of the requirements for the degree of Master of Science in Computer Science Joshua Springer Reykjavík University; Department of Computer Science Mälardalen University; School of Innovation, Design, and Engineering June 12, 2020 Acknowledgements I would like to thank my family for their undying love, support, and encouragement which have gotten me this far. My thanks go to Mälardalen University, Reykjavík University, and the Nordic Council, without whose generosity in the MDH Scholarship and the Nordic Master Programme, I would not have had the opportunity to study my passion in two wonderful countries. 2 Abstract Takeoff, normal flight, and even specialized tasks such as taking pictures, are essentially solved problems in autonomous drone flight. This notably excludes landing, which typically requires a pilot because of its inherently risky nature. This project attempts to solve the problem of autonomous drone landing using computer vision and fiducial markers - and specifically does not use GPS as a primary means of navigation during landing. The system described in this thesis extends the functionality of the widely-used, open-source ArduPilot software which runs on many drones today, and which has only primitive functionality for autonomous landing. This system is implemented as a set of ROS modules which interact with ArduPilot for control. It is designed to be easily integrated into existing ArduPilot drone systems through the addition of a companion board and gimbal-mounted camera. Results are presented to evaluate the system’s performance with regard to pose estimation and landing capabilities within Gazebo 9 simulator. -

Pweb Peer-To-Peer Web Hosting Communication System and Dynamic Web Hosting
pWeb Peer-to-Peer Web Hosting Communication System and Dynamic Web Hosting Alexander Pokluda1, Abdalla Aartail2, Md. Faizul Bari1, Reaz Ahmed1, and Raouf Boutaba1 1David R. Cheriton School of Computer Science University of Waterloo [apokluda | mfbari | r5ahmed | rboutaba]@uwaterloo.ca 2American University of Beirut [email protected] University of Waterloo Technical Report: CS-2013-15∗ ∗This report is a modified version of an internal technical report produced for Orange Labs, the project's sponsor. The original technical report was submitted to Orange Labs in August 2013. Abstract During the main phase of this project we identified and provided solution for the major challenges related to peer-to-peer (P2P) web hosting. More specifically, our solutions for naming, availability, ranking, indexing and dynamic web-hosting have been provided in previous reports. In this report we present a more concrete view of the pWeb infrastructure and address the issues related to a real-life deployment of the system. First we provide an overview of the light-weight P2P communication protocol between pWeb clients for signaling and media streaming in Part I. In Part II we provide an architectural overview of pWeb system and show the mapping of the abstract components in pWeb architec- ture to real life devices and technologies. In order to make pWeb compatible with the existing Web technology we have developed a DNS gateway. In Part II Section 3, we provide the design and implementation of this DNS gateway. For efficient indexing and fast discovery of end-user devices and multimedia content, we have developed a cloud-based solution for crawling, indexing and searching.