Guardian of the Galaxy: EU Cyber Sanctions and Norms in Cyberspace
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
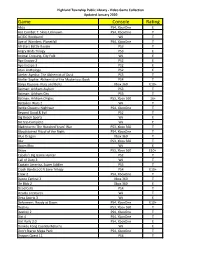
Game Console Rating
Highland Township Public Library - Video Game Collection Updated January 2020 Game Console Rating Abzu PS4, XboxOne E Ace Combat 7: Skies Unknown PS4, XboxOne T AC/DC Rockband Wii T Age of Wonders: Planetfall PS4, XboxOne T All-Stars Battle Royale PS3 T Angry Birds Trilogy PS3 E Animal Crossing, City Folk Wii E Ape Escape 2 PS2 E Ape Escape 3 PS2 E Atari Anthology PS2 E Atelier Ayesha: The Alchemist of Dusk PS3 T Atelier Sophie: Alchemist of the Mysterious Book PS4 T Banjo Kazooie- Nuts and Bolts Xbox 360 E10+ Batman: Arkham Asylum PS3 T Batman: Arkham City PS3 T Batman: Arkham Origins PS3, Xbox 360 16+ Battalion Wars 2 Wii T Battle Chasers: Nightwar PS4, XboxOne T Beyond Good & Evil PS2 T Big Beach Sports Wii E Bit Trip Complete Wii E Bladestorm: The Hundred Years' War PS3, Xbox 360 T Bloodstained Ritual of the Night PS4, XboxOne T Blue Dragon Xbox 360 T Blur PS3, Xbox 360 T Boom Blox Wii E Brave PS3, Xbox 360 E10+ Cabela's Big Game Hunter PS2 T Call of Duty 3 Wii T Captain America, Super Soldier PS3 T Crash Bandicoot N Sane Trilogy PS4 E10+ Crew 2 PS4, XboxOne T Dance Central 3 Xbox 360 T De Blob 2 Xbox 360 E Dead Cells PS4 T Deadly Creatures Wii T Deca Sports 3 Wii E Deformers: Ready at Dawn PS4, XboxOne E10+ Destiny PS3, Xbox 360 T Destiny 2 PS4, XboxOne T Dirt 4 PS4, XboxOne T Dirt Rally 2.0 PS4, XboxOne E Donkey Kong Country Returns Wii E Don't Starve Mega Pack PS4, XboxOne T Dragon Quest 11 PS4 T Highland Township Public Library - Video Game Collection Updated January 2020 Game Console Rating Dragon Quest Builders PS4 E10+ Dragon -

Internet Infrastructure Review Vol.27
Internet Infrastructure Vol.27 Review May 2015 Infrastructure Security Increasingly Malicious PUAs Messaging Technology Anti-Spam Measure Technology and DMARC Trends Web Traffic Report Report on Access Log Analysis Results for Streaming Delivery of the 2014 Summer Koshien Inte r ne t In f r ast r uc t ure Review Vol.27 May 2015 Executive Summary ———————————————————3 1. Infrastructure Security ———————————————4 Table of Contents Table 1.1 Introduction —————————————————————— 4 1.2 Incident Summary ——————————————————— 4 1.3 Incident Survey ——————————————————— 11 1.3.1 DDoS Attacks —————————————————————— 11 1.3.2 Malware Activities ———————————————————— 13 1.3.3 SQL Injection Attacks —————————————————— 16 1.3.4 Website Alterations ——————————————————— 17 1.4 Focused Research —————————————————— 18 1.4.1 Increasingly Malicious PUAs —————————————— 18 1.4.2 ID Management Technology: From a Convenience and Security Perspective ————— 22 1.4.3 Evaluating the IOCs of Malware That Reprograms HDD Firmware —————————————————————— 25 1.5 Conclusion —————————————————————— 27 2. Messaging Technology —————————————— 28 2.1 Introduction ————————————————————— 28 2.2 Spam Trends ————————————————————— 28 2.2.1 Spam Ratios Decline Further in FY2014 ————————— 28 2.2.2 Higher Risks Despite Lower Volumes —————————— 29 2.3 Trends in Email Technologies ——————————— 29 2.3.1 The DMARC RFC ————————————————————— 29 2.3.2 Problems with DMARC and Reporting —————————— 30 2.3.3 Use of DMARC by Email Recipients ——————————— 30 2.3.4 Domain Reputation ——————————————————— 31 2.3.5 -

Gothic Panda Possibly Used Doublepulsar a Year Before The
Memo 17/05/2019 - TLP:WHITE Gothic Panda possibly used DoublePulsar a year before the Shadow Brokers leak Reference: Memo [190517-1] Date: 17/05/2019 - Version: 1.0 Keywords: APT, DoublePulsar, China, US, Equation Group Sources: Publicly available sources Key Points Gothic Panda may have used an Equation Group tool at least one year before the Shadow Brokers leak. It is unknown how the threat group obtained the tool. This is a good example of a threat actor re-using cyber weapons that were originally fielded by another group. Summary According research conducted by Symantec, the Chinese threat actor known as Gothic Panda (APT3, UPS, SSL Beast, Clandestine Fox, Pirpi, TG-0110, Buckeye, G0022, APT3) had access to at least one NSA-associated Equation Group tool a year before they were leaked by the Shadow Brokers threat actor. On April 14, 2017, a threat actor called the Shadow Brokers released a bundle of cyber-attack tools purportedly coming from the US NSA, also referred to as the Equation Group. Among the released material there was the DoublePulsar backdoor implant tool, which was used alongside EternalBlue in the May 2017 destructive WannaCry attack. DoublePulsar is a memory-based kernel malware that allows perpetrators to run arbitrary shellcode payloads on the target system. It does not write anything on the hard drive and will thus disappear once the victim machine is rebooted. Its only purpose is to enable dropping other malware or executables in the system. According to Symantec, Gothic Panda used the DoublePulsar exploit as early as in 2016, a full year before the Shadow Brokers release. -

Cyberwar: the ISIL Threat & Resiliency in Operational Technology
Cyberwar: The ISIL Threat & Resiliency in Operational Technology Thesis Presented to the Faculty of the Department of Information and Logistics Technology University of Houston In Partial Fulfillment of the Requirements for the Degree Master’s of Information Systems Security By Gregory S. Anderson May 2017 Cyberwar: The ISIL Threat & Resiliency in Operational Technology ____________________________________ Gregory S. Anderson Approved: Committee Chair: ____________________________________ Wm. Arthur Conklin, PhD Computer Information Systems and Information System Security Committee Member: ____________________________________ Chris Bronk, PhD Computer Information Systems and Information System Security Committee Member: ____________________________________ Paula deWitte, PhD Computer Information Systems and Information System Security ____________________________________ ____________________________________ Rupa Iyer, PhD Dan Cassler Associate Dean for Research and Graduate Interim Chair for Department of Information Studies, College of Technology and Logistics Technology THIS PAGE INTENTIONALLY LEFT BLANK Acknowledgments First, I would like to thank Dr. Chris Bronk and Dr. Art Conklin for their support and guidance throughout my time at the University of Houston. Their dedication to students is unparalleled for any other professor I have come across during my education. I would also like to thank my family for their ongoing encouragement and love. The fostering environment to peruse knowledge and “never settle for less” has been a constant inspiration throughout my life. Lastly, to my partner of 7 years, Lorelei. None of my achievements these past few years would have come to fruition without her continuous love, support, and willingness to sacrifice for the greater good is deeply appreciated. Thank you for being the most patient and steadfast person I have ever known, I love you. -

Make Technology Great Again
Make Technology Great Again Michał „rysiek” Woźniak [email protected] Everything is Broken – Quinn Norton https://medium.com/message/everything-is-broken-81e5f33a24e1 "Malicious Word Doc Uses ActiveX To Infect" https://www.vmray.com/blog/malicious-word-doc-uses-activex-infect/ "Word Malware: OLE Exploited in Zero-Day Attack" https://www.vadesecure.com/en/word-doc-malware/ "Dynamic Data Exchange was frst introduced in 1987 with the release of Windows 2.0” https://en.wikipedia.org/wiki/Dynamic_Data_Exchange "As part of the December 2017 Patch Tuesday, Microsoft has shipped an Ofce update that disables the DDE feature in Word applications, after several malware campaigns have abused this feature to install malware.” https://www.bleepingcomputer.com/news/microsoft/microsoft-disables-dde-feature-in-word- to-prevent-further-malware-attacks/ "Dynamic Data Exchange was frst introduced in 1987 with the release of Windows 2.0” https://en.wikipedia.org/wiki/Dynamic_Data_Exchange "As part of the December 2017 Patch Tuesday, Microsoft has shipped an Ofce update that disables the DDE feature in Word applications, after several malware campaigns have abused this feature to install malware.” https://www.bleepingcomputer.com/news/microsoft/microsoft-disables-dde-feature-in-word- to-prevent-further-malware-attacks/ "Microsoft Ofce macro malware targets Macs" https://blog.malwarebytes.com/cybercrime/2017/02/microsoft-ofce-macro- malware-targets-macs/ "Beware PowerSniff Malware uses Word macros and PowerShell scripts" https://www.grahamcluley.com/beware-powersnif-malware/ -

Avengers Dissemble! Transmedia Superhero Franchises and Cultic Management
Taylor 1 Avengers dissemble! Transmedia superhero franchises and cultic management Aaron Taylor, University of Lethbridge Abstract Through a case study of The Avengers (2012) and other recently adapted Marvel Entertainment properties, it will be demonstrated that the reimagined, rebooted and serialized intermedial text is fundamentally fan oriented: a deliberately structured and marketed invitation to certain niche audiences to engage in comparative activities. That is, its preferred spectators are often those opinionated and outspoken fan cultures whose familiarity with the texts is addressed and whose influence within a more dispersed film- going community is acknowledged, courted and potentially colonized. These superhero franchises – neither remakes nor adaptations in the familiar sense – are also paradigmatic byproducts of an adaptive management system that is possible through the appropriation of the economics of continuity and the co-option of online cultic networking. In short, blockbuster intermediality is not only indicative of the economics of post-literary adaptation, but it also exemplifies a corporate strategy that aims for the strategic co- option of potentially unruly niche audiences. Keywords Marvel Comics superheroes post-cinematic adaptations Taylor 2 fandom transmedia cult cinema It is possible to identify a number of recent corporate trends that represent a paradigmatic shift in Hollywood’s attitudes towards and manufacturing of big budget adaptations. These contemporary blockbusters exemplify the new industrial logic of transmedia franchises – serially produced films with a shared diegetic universe that can extend within and beyond the cinematic medium into correlated media texts. Consequently, the narrative comprehension of single entries within such franchises requires an increasing degree of media literacy or at least a residual awareness of the intended interrelations between correlated media products. -

Star of Malware Galaxy
Star of Malware Galaxy By GReAT on February 16, 2015. 6:55 pm Download “Equation group: questions and answers” PDF “Houston, we have a problem” One sunny day in 2009, Grzegorz Brzęczyszczykiewicz1 embarked on a flight to the burgeoning city of Houston to attend a prestigious international scientific conference. As a leading scientist in his field, such trips were common for Grzegorz. Over the next couple of days, Mr Brzęczyszczykiewicz exchanged business cards with other researchers and talked about the kind of important issues such high level scientists would discuss (which is another way of saying “who knows?”). But, all good things must come to an end; the conference finished and Grzegorz Brzęczyszczykiewicz flew back home, carrying with him many highlights from a memorable event. Sometime later, as is customary for such events, the organizers sent all the participants a CDROM carrying many beautiful pictures from the conference. As Grzegorz put the CDROM in his computer and the slideshow opened, he little suspected he had just became the victim of an almost omnipotent cyberespionage organization that had just infected his computer through the use of three exploits, two of them being zero-days. A rendezvous with the “God” of cyberespionage It is not known when the Equation2 group began their ascent. Some of the earliest malware samples we have seen were compiled in 2002; however, their C&C was registered in August 2001. Other C&Cs used by the Equation group appear to have been registered as early as 1996, which could indicate this group has been active for almost two decades. -

NEW THIS WEEK from MARVEL... Wolverine #1 Guardians of the Galaxy #2 Fantastic Four #19 Captain America #19 Daredevil #18 New Mu
NEW THIS WEEK FROM MARVEL... Wolverine #1 Guardians of the Galaxy #2 Fantastic Four #19 Captain America #19 Daredevil #18 New Mutants #7 Captain Marvel #15 Deadpool #3 Marauders #8 Marvels Voices #1 Revenge of Cosmic Ghost Rider #3 (of 5) Conan the Barbarian #13 Amazing Mary Jane #5 Valkyrie Jane Foster #8 2020 Machine Man #1 (of 2) Ghost-Spider #7 Marvels Black Widow Prelude #2 (of 2) Atlantis Attacks #2 (of 5) Runaways #30 True Believers Iron Man 2020 Jocasta ($1) NEW THIS WEEK FROM DC... Batman #89 Dceased Unkillables #1 (of 3) Justice League #41 Flash Forward #6 (of 6) Legion of Super Heroes #4 Nightwing #69 Teen Titans #39 Aquaman #57 Joker Killer Smile #3 (of 3) Low Low Woods #3 (of 6) Wonder Woman Dead Earth #2 (of 4) Superman's Pal Jimmy Olsen #8 (of 12) Wonder Twins #12 (of 12) Titans Burning Rage #7 (of 7) Wonder Woman Giant #3 Lucifer #17 Superman Smashes the Klan #3 (of 3) Dollar Comics New Teen Titans #2 NEW THIS WEEK FROM IMAGE... Plunge #1 (of 6) Undiscovered Country #4 On the Stump #1 American Jesus New Messiah #3 Oblivion Song #24 Spawn #305 Middlewest #15 Bitter Root #6 Deadly Class #43 Family Tree #4 Old Guard Force Multiplied #3 (of 5) Hardcore Reloaded #3 (of 5) Lucy Claire Redemption #3 ALSO NEW THIS WEEK... Red Mother #3 Bang #1 (of 5) Godkillers #1 Skulldigger & Skeleton Boy #3 (of 6) Bloodshot #0 Canopus #1 Five Years #8 Doctor Tomorrow #1 (of 5) Goon #8 Hellboy & the BPRD Return of Effie Kolb #1 (of 2) Heartbeat #4 (of 5) Red Sonja Age of Chaos #2 Adventures of Byron One Shot Black Clover Vol. -

Threat Landscape Report – 1St Quarter 2018
TLP-AMBER Threat Landscape Report – 1st Quarter 2018 (FINAL) V1.0 – 10/04/2018 This quarterly report summarises the most significant direct cyber threats to EU institutions, bodies, and agencies (EU-I or 'Constituents') in Part I, the development of cyber-threats on a broader scale in Part II, and recent technical trends in Part III. KEY FINDINGS Direct Threats • In Europe, APT28 / Sofacy threat actor (likely affiliated to Russia military intelligence GRU) targeted government institutions related to foreign affairs and attendees of a military conference. Another threat actor, Turla (likely affiliated to Russia’s security service FSB) executed a cyber-operation against foreign affairs entities in a European country. • A spear-phishing campaign that targeted European foreign ministries in the end of 2017 was attributed to a China-based threat actor (Ke3chang) which has a long track record of targeting EU institutions (since 2011). As regards cyber-criminality against EU institutions, attempts to deliver banking trojans are stable, ransomware activities are still in decline and cryptojacking on the rise. Phishing lures involve generic matters (’invoice’, ‘payment’, ‘purchase’, ‘wire transfer’, ‘personal banking’, ‘job application’) and more specific ones (foreign affairs issues, European think tanks matters, energy contracts, EU delegation, EU watch keeper). Almost all EU-I are affected by credential leaks (email address | password) on pastebin-like websites. Several credential- harvesting attempts have also been detected. Attackers keep attempting to lure EU-I staff by employing custom methods such as spoofed EU-I email addresses or weaponisation of EU-I documents. Broader Threats • Critical infrastructure. In the energy sector, the US authorities have accused Russian actors of targeting critical infrastructure (including nuclear) for several years and are expecting this to continue in 2018. -
TV LISTINGS Lake Geneva Regional News
C6 | THURSDAY, JUNE 3, 2021 TV LISTINGS LAKE GENEVA REGIONAL NEWS THURSDAY EVENING MOVIES JUNE 3, 2021 SUNDAY EVENING MOVIES JUNE 6, 2021 7 PM 7:30 8 PM 8:30 9 PM 9:30 10 PM 10:30 11 PM 11:30 7 PM 7:30 8 PM 8:30 9 PM 9:30 10 PM 10:30 11 PM 11:30 Young United Mom (s) B Positive Clarice Catherine News The Late Show With James The 43rd Annual Kennedy Center Honors: NCIS: New Orleans News Seinfeld Paid Pro- Storm of # WISC Sheldon States (cc) (s) (cc) Martin escapes. (s) Stephen Colbert (s) Corden # WISC Entertainers receive recognition. (N) (s) (cc) “Stashed” (s) (s) (cc) gram (cc) Suspicion Manifest “Duty Free” Law & Order: Special Law & Order: Orga- TMJ4 Tonight Show-J. Seth Mey- (6:00) Gymnastics: America’s Got Talent “Auditions 1” Variety TMJ4 TMJ4 Paid Pro- Paid Pro- $ WTMJ (N) (s) (cc) Victims Unit (N) nized Crime (N) (cc) News Fallon ers $ WTMJ U.S. Championships. acts audition. (s) (cc) News News gram (cc) gram (cc) Beat Shazam “Every- House- Duncan- FOX 6 News at 9 FOX 6 Seinfeld Seinfeld Extra (N) The Simp- The Great The Moodys (N) FOX 6 News at 9 FOX 6 FOX 6 Graham Seinfeld & WITI body Dance Now!” Broken ville (s) (N) (cc) News (cc) (s) (cc) (s) (cc) & WITI sons North (s) (s) (cc) (N) (cc) News Sports Bensinger (s) (cc) Station 19 “Forever Grey’s Anatomy Rebel Lana confronts News at Jimmy Kimmel Live! Nightline Celebrity Family The Chase “We’re To Tell the Truth ABC7 Eyewitness Inside Best of _ WLS and Ever, Amen” (N) (Season Finale) (s) Grady about his past. -

Cyber Security Management: a Review Kouroush Jenab1 and Saeid Moslehpour2
Business Management Dynamics Vol.5, No.11, May 2016, pp.16-39 Cyber Security Management: A Review Kouroush Jenab1 and Saeid Moslehpour2 Key words: Computer, Cyber, Abstract Security, Attack This paper presents a review of selected literature on cyber security topics. A wide range of topics is looked at that relate to cyber security. Several references Available online are provided. www.bmdynamics.com ISSN: 2047-7031 INTRODUCTION The online IT dictionary Techopedia defines cyber attacks as “…deliberate exploitation of computer systems, technology-dependent enterprises and networks.” “Cyber attacks use malicious code to alter computer code, logic or data, resulting in disruptive consequences that can compromise data and lead to cybercrimes, such as information and identity theft.” (Techopedia online dictionary, n.d.) Cyber attacks are unleashed on corporations and personal computers every day. In a green paper published by the Department of Commerce Internet Policy Task Force (2011), Secretary of Commerce Gary Locke states that, “Protecting security of consumers, businesses and the Internet infrastructure has never been more difficult. Cyber attacks on Internet commerce, vital business sectors and government agencies have grown exponentially. Some estimates suggest that, in the first quarter of this year, security experts were seeing almost 67,000 new malware threats on the Internet every day. This means more than 45 new viruses, worms, spyware, and other threats were being created every minute – more than double the number from January 2009. As these threats grow, security policy, technology and procedures need to evolve even faster to stay ahead of the threats.” (Cybersecurity, innovation and the internet economy, 2011). -

Iranian Cyber-Activities in the Context of Regional Rivalries and International Tensions
CSS CYBER DEFENSE PROJECT Hotspot Analysis: Iranian cyber-activities in the context of regional rivalries and international tensions Zürich, May 2019 Version 1 Risk and Resilience Team Center for Security Studies (CSS), ETH Zürich Iranian cyber-activities in the context of regional rivalries and international tensions Authors: Marie Baezner © 2019 Center for Security Studies (CSS), ETH Zürich Contact: Center for Security Studies Haldeneggsteig 4 ETH Zürich CH-8092 Zürich Switzerland Tel.: +41-44-632 40 25 [email protected] www.css.ethz.ch Analysis prepared by: Center for Security Studies (CSS), ETH Zürich ETH-CSS project management: Tim Prior, Head of the Risk and Resilience Research Group Myriam Dunn Cavelty, Deputy Head for Research and Teaching, Andreas Wenger, Director of the CSS Disclaimer: The opinions presented in this study exclusively reflect the authors’ views. Please cite as: Baezner, Marie (2019): Hotspot Analysis: Iranian cyber-activities in context of regional rivalries and international tensions, May 2019, Center for Security Studies (CSS), ETH Zürich. 1 Iranian cyber-activities in the context of regional rivalries and international tensions Table of Contents 1 Introduction 4 2 Background and chronology 5 3 Description 9 3.1 Attribution and actors 9 Iranian APTs 9 Iranian patriotic hackers 11 Western actors 12 3.2 Targets 12 Iranian domestic targets 12 Middle East 12 Other targets 13 3.3 Tools and techniques 13 Distributed Denial of Service (DDoS) attacks 13 Fake personas, social engineering and spear phishing 13