Geographic Information System Approach in Evaluating Security Challenges to Critical Infrastructures
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
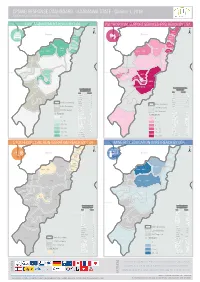
CPSWG RESPONSE DASHBOARD - ADAMAWA STATE - Quarter 1, 2019 Child Protection Sub Working Group, Nigeria
CPSWG RESPONSE DASHBOARD - ADAMAWA STATE - Quarter 1, 2019 Child Protection Sub Working Group, Nigeria YobeCASE MANAGEMENT REACH BY LGA PSYCHOSOCIALYobe SUPPORT SERVICES (PSS) REACH BY LGA 78% 14% Madagali ± Madagali ± Borno Borno Michika Michika 86% 10% 82% 16% Mubi North Mubi North Hong 100% Mubi South 5% Hong Gombi 100% 100% Gombi 10% 27% Mubi South Shelleng Shelleng Guyuk Song 0% Guyuk Song 0% 0% Maiha 0% Maiha Chad Chad Lamurde 0% Lamurde 0% Nigeria Girei Nigeria Girei 36% 81% 11% 96% Numan 0% Numan 0% Yola North Demsa 100% Demsa 26% Yola North 100% 0% Adamawa Fufore Yola South 0% Yola South 100% Fufore Mayo-Belwa Mayo-Belwa Adamawa Local Government Area Local Government (LGA) Target Area (LGA) Target LGA TARGET LGA TARGET Demsa 1,170 DEMSA 78 Fufore 370 Jada FUFORE 41 Jada Ganye 0 GANYE 0 Girei 933 GIREI 16 Gombi 4,085 State Boundary GOMBI 33 State Boundary Guyuk 0 GUYUK 0 LGA Boundary Hong 16,941 HONG 6 Ganye Ganye LGA Boundary Jada 0 JADA 0 Not Targeted Lamurde 839 LAMURDE 6 Not Targeted Madagali 6,321 MADAGALI 119 % Reach Maiha 2,800 MAIHA 12 % REACH Mayo-Belwa 0 0 MAYO - BELWA 0 0 Michika 27,946 Toungo 0% MICHIKA 232 Toungo 0% 1 - 36 Mubi North 11,576 MUBI NORTH 154 1 - 5 Mubi South 11,821 MUBI SOUTH 139 37 - 78 Numan 2,250 NUMAN 14 6 - 11 Shelleng 0 SHELLENG 0 79 - 82 12 - 16 Song 1,437 SONG 21 Teungo 25 83 - 86 TOUNGO 6 17 - 27 Yola North 1,189 YOLA NORTH 14 Yola South 2,824 87 - 100 YOLA SOUTH 47 28 - 100 SOCIO-ECONOMICYobe REINTEGRATION REACH BY LGA MINEYobe RISK EDUCATION (MRE) REACH BY LGA Madagali Madagali R 0% I 0% ± -

Comparative Economics of Fresh and Smoked Fish Marketing in Some Local Government Areas in Adamawa State, Nigeria
COMPARATIVE ECONOMICS OF FRESH AND SMOKED FISH MARKETING IN SOME LOCAL GOVERNMENT AREAS IN ADAMAWA STATE, NIGERIA. ONYIA, L.U., ADEBAYO, E.F., ADEWUYI, K.O., EKWUNIFE, E.G., OCHOKWU,I.J, OUTLINE OF PRESENTATION • INTRODUCTION • MATERIALS AND METHODS • RESULTS AND DISCUSSIONS • CONCLUSIONS • RECOMMENDATIONS INTRODUCTION ü FISH IS A MAJOR SOURCE OF ANIMAL PROTEIN, ü ESSENTIAL FOOD ITEM IN THE DIET OF NIGERIANS (JIM-SAIKI AND OGUNBADEJO, 2003), ü AN IMPORTANT SOURCE OF LIFE AND LIVELIHOODS FOR MILLIONS OF PEOPLE AROUND THE WORLD AND FOR THAT MATTER THE SELECTED COMMUNITIES, ü PROVIDES A SPENDABLE INCOME FOR MANY FAMILIES IN THE DEVELOPING WORLD (JERE AND MWENDO-PEHIRI, 2004). INTRODUCTION CONTINUED v IN NIGERIA, FISH IS SOLD TO CONSUMERS AS: ü FROZEN OR ICED, ü CURED (SMOKED), ü SUN DRIED, ü FRESH EITHER FROM A CULTURED POND OR FROM THE WILD. OBJECTIVES OF THE STUDY • TO IDENTIFY SOCIOECONOMIC CHARACTERISTICS OF THE FISH MARKETERS • TO COMPARE ECONOMIC BENEFITS OF FRESH AND SMOKED FISH ENTERPRISES IN THE STUDY AREAS. MATERIALS AND METHODS THE STUDY AREA ü SEVEN LOCAL GOVERNMENT AREAS OF ADAMAWA STATE (NGURORE, YOLA SOUTH, YOLA NORTH, GIREI, DEMSA, FUFORE AND NUMAN) WERE RANDOMLY SELECTED BASED ON THEIR PROXIMITY TO THE FISH LANDING SITES, ü DATA COLLECTED THROUGH WELL-STRUCTURED QUESTIONNAIRE OF FRESH AND SMOKED FISH MARKETERS FROM 7 MARKETS, ü 286 QUESTIONNAIRES WERE RANDOMLY DISTRIBUTED AMONG THE FISH MARKETERS. METHOD OF DATA ANALYSIS • DESCRIPTIVE STATISTICS IN TERMS OF FREQUENCIES AND PERCENTAGES • GROSS MARGIN ANALYSIS WAS USED TO DETERMINE -

LGA Demsa Fufore Ganye Girei Gombi Guyukk Hong Jada Lamurde
LGA Demsa Fufore Ganye Girei Gombi Guyukk Hong Jada Lamurde Madagali Maiha Mayo Belwa Michika Mubi North Mubi South Numan Toungo Shellenge Song Yola North Yola South PVC PICKUP ADDRESS Along Gombe Road, Demsa Town, Demsa Local Govt. Area Gurin Road, Adjacent Local Govt. Guest House, Fufore Local Govt. Area Along Federal Government College, Ganye Road, Ganye Lga Adjacent Local Govt. Guest Road, Girei Local Govt. Area Sangere Gombi, Aong Yola Road, Gombi L.G.A Palamale Nepa Ward Guyuk Town, Guyuk Local Govt. Area Opposite Cottage Hospital Shangui Ward, Hong Local Govt. Area Old Secretariat, Jada Along Ganye Road, Jada Lafiya Lamurde Road, Lamurde Local Govt. Area Palace Road, Gulak, Near Gulak Police Station, Madagali Lga Behind Local Govt. Secretariat, Mayonguli Ward, Maiha Jalingo Road Near Maternity Mayo Belwa Lga Michika Bye-Pass Zaibadari Ward Michika Lga Inside Local Govt. Secretariat, Mubi North Lumore Street, Opposite District Head's Palace, Gela, Mubi South Councilors Quarters, Off Jalingo Road, Numan Lga Barade Road, Oppoiste Sss Office, Toungo Old Local Govt Secretariat Street, Shelleng Town, Shelleng Lga Opp. Cattage Hospital Yola Road, Song Local Govt. Area No. 7 Demsawo Street, Demsawo Ward, Yola North Lga Yola Bye-Pass Fufore Road Opp. Aliyu Mustapha College, Bako Ward, Yola Town, Yola South Lga Yola Bye-Pass Fufore Road Opp. Aliyu Mustapha College, Bako Ward, Yola Town, Yola South Lga. -

Adamawa - Health Sector Reporting Partners (April - June, 2020)
Nigeria: Adamawa - Health Sector Reporting Partners (April - June, 2020) Number of Local Reporting PARTNERS PER TYPE Government Area Partners OF ORGANIZATIONS BREAKDOWN OF PEOPLE REACHED PER CATEGORY NGOs/UN People Reached PiN/Target IDP Returnee Host Agencies Community 21 Partners14 including 230,996 LGAs with ongoing International NGOs and activities 95,764 13,922 1,268 80,573 UN Agencies 11/3 212,433 DEMSA (4 Partners) MICHIKA (6 Partners) FSACI, IOM, JHF, WHO GZDI, IRC, JHF, PLAN, WHO, ZSF MADAGALI REACHED: 6,070 REACHED: 6,578 FUFORE (4 Partners) MUBI NORTH (7 Partners) MICHIKA GDZI, IOM, JHF, LESGO, PLAN, IOM, JHF, UNICEF, WHO SWOGE, WHO REACHED: 17,309 REACHED: 6,924 MUBI NORTH GANYE (2 Partners) MUBI SOUTH (6 Partners) HONG JHF GDZI, IOM, JHF, LESGO, RHHF, ZSF GOMBI MUBI SOUTH REACHED: - REACHED: 4,090 GIREI (4 Partners) NUMAN (1 Partner) SHELLENG JHF AGUF, IOM, JHF, WHO MAIHA REACHED: 22,348 REACHED: - SONG GUYUK GOMBI (3 Partners) SHELLENG (1 Partner) JHF GDZI, JHF, WHO LAMURDE REACHED: 220 REACHED: - GIREI GUYUK (2 Partners) SONG (2 Partners) NUMAN AGUF, JHF JHF DEMSA REACHED: - REACHED: 7,355 YOLA SOUTH YOLA NORTH HONG (3 Partners) TOUNGO (1 Partner) GDZI, JHF, WHO JHF MAYO FUFORE REACHED: 423 REACHED: - BELWA JADA (1 Partner) YOLA NORTH (4 Partners) HARAF, IOM, JHF, UNICEF JHF JADA REACHED: - REACHED: 1,224 LAMURDE (1 Partner) YOLA SOUTH (4 Partners) GANYE JHF IOM, JHF, SWOGE, UNICEF Number of Organizations REACHED: - REACHED: 7,355 (3 Partners) MADAGALI 1 7 JHF, PLAN, WHO TOUNGO REACHED: 4,537 MAIHA (2 Partners) JHF, WHO -

NORTHEAST NIGERIA CAMP MANAGEMENT BI-WEEKLY TRACKER REPORT Report No
NORTHEAST NIGERIA CAMP MANAGEMENT BI-WEEKLY TRACKER REPORT Report No. 23 | 01-15 October 2020. 164 189,562 823,344 154 IDP camps managed by partners Households (HH) reached by CCCM partner Individuals (ind) reached by CCCM partner Site facilitators managing in Adamawa and Borno state. agencies. agencies in Adamawa and Borno state. camps. The Camp Management bi-weekly tracker report is a service monitoring and gap analysis tool produced by the CCCM/Shelter/NFI sector. The tracker supports humanitarian partners in iden�fying gaps in assistance and service YOBE delivery. It enables stakeholders to track ac�vi�es, iden�fy gaps and thereby improving the delivery of assistance. BORNO As of September 2020, 164 camps were covered by partner agencies in the following Local Government Areas (LGAs) in Adamawa State: Fufore, Girei, Mubi South, Yola South and Yola North while in Borno State, the sites are located in Bama, Biu, Damboa, Dikwa, Gwoza, Jere, Kaga, Konduga, Mafa, Magumeri, Maiduguri, Monguno, Ngala and Nganzai LGA. KEY HIGHLIGHTS ADAMAWA The CCCM, Shelter and NFI sector in the repor�ng period of 1st -15th October received a series of Ad-hoc reports on the widespread destruc�on and damages to shelters in camps and camps-like se�ng as a result of exceeded shelters life-span and vandalism. Hence, a total of 9,656 vulnerable households in dire need of shelter, shelter repairs and essen�al non-food items (NFIs) were recorded. The affected persons are currently living in precarious LGA with CCCM activity condi�ons and are exposed to a range of protec�on threat and concerns. -

The Use of Remote Sensing and Geographic Information System in Land Use Management in Karu, Nasarawa State, Nigeria
THE USE OF REMOTE SENSING AND GEOGRAPHIC INFORMATION SYSTEM IN LAND USE MANAGEMENT IN KARU, NASARAWA STATE, NIGERIA BY JONAH, KUNDA JOSHUA M.Sc/SCIE/05624/2009/2010 A DISSERTATION SUBMITTED TO THE POSTGRADUATE SCHOOL, AHMADU BELLO UNIVERSITY, ZARIA, NIGERIA IN PARTIAL FULFILLMENT FOR THE AWARD OF MASTERS IN REMOTE SENSING AND GEOGRAPHIC INFORMATION SYSTEM DEPARTMENT OF GEOGRAPHY, AHMADU BELLO UNIVERSITY, ZARIA, NIGERIA APRIL, 2014 1 THE USE OF REMOTE SENSING AND GEOGRAPHIC INFORMATION SYSTEM IN LAND USE MANAGEMENT IN KARU, NASARAWA STATE, NIGERIA BY JONAH KUNDA JOSHUA M.Sc/SCIE/05624/2009/2010 A DISSERTATION SUBMITTED TO THE POSTGRADUATE SCHOOL, AHMADU BELLO UNIVERSITY, ZARIA, NIGERIA IN PARTIAL FULFILLMENT FOR THE AWARD OF MASTERS IN REMOTE SENSING AND GEOGRAPHIC INFORMATION SYSTEM DEPARTMENT OF GEOGRAPHY, AHMADU BELLO UNIVERSITY, ZARIA, NIGERIA APRIL, 2014 2 DECLARATION I declare that the work in the dissertation entitled “The Use of Remote Sensing and Geographic Information System in Land Use Management in Karu, Nasarawa State, Nigeria” has been performed by me in the Department of Geography under the supervision of Prof. EO Iguisi and Dr. DN Jeb. The information derived from the literature has been duly acknowledged in the text and list of references provided. No part of this dissertation was previously presented for another degree or diploma at any university. Jonah Kunda Joshua --------------------------- -------------------------- Signature Date 3 CERTIFICATION This thesis entitled “THE USE OF REMOTE SENSING AND GEOGRAPHIC INFORMATION SYSTEM IN LAND USE MANAGEMENT IN KARU, NASARAWA STATE, NIGERIA” by Jonah Kunda Joshua meets the regulations governing the award of the degree of MASTERS of Remote Sensing and Geographic Information System, Ahmadu Bello University, Zaria and is approved for its contribution to knowledge and literary presentation. -

Annual Report of the Colonies, Northern Nigeria, 1911
COLONIAL REPORTS—ANNUAL • • No. 788, NOBTHERN NIGERIA* REPORT fOn 1911. (For Report for 1910-11, see No. 704.) $xt*mttb to both %wi»t» at $*xlhmtnt fcg fcoromani *f P§ JR*)**tg» November, 10ft. LONDON: PUBLISHED BY HIS MAJESTY'S STATIONERY OFFICE. To be purchased, either directly or through any Bookseller, from WYMAN AND SONS, LIMITED, Fmn LANE, E.C., and 32, ABINGDON STREET, S.W., or H.M. STATIONERY OFFICE (SCOTTISH BRJLNCH), 23, FORTH STRUT, EDINBURGH ; or E. PONSONBY, LIMITED, 116. GRAFTON STRUT, Drawn; or from the Agencies in the British Colonies sad Dependencies, the United States of America, the Continent of Europe and Abroad of T. FISHER UNWIN, LONDON, W.d PRINTED BY DARLING AND SON, LTD., BACON STREET, E. bis. [CU. 6007-*$.] Price tyi Page H.—TRADE AND CUSTOMS ... ... ... ... .. ... 8 III.—LEGISLATION AND JUDICIAL ... ... 'M 8 IV.—OAMTOlfMBETS 11 VI.—HOSPITALS . ... ... ... ... ••• is VH^Btetis DEPARTMENT ... ... ... ... ... 13 mi.—POLICE ..< ... ... .... ... ... ... 16 IX.—PRISONS ... ... ... ... ... ... ... *•• 1& X.—CRIMINAL STATISTICS ... ... ... ... ... W XI.—VITAL STATISTICS ... ... ... ... ... ... ... *.• XII.—SANITATIOK ... ... ... ... ... ... ... ... 18 XHI.—VACCINATION ... ... sc. ... •** 19 XIV.—METEOROLOGY ... .<*. ... ... ... ... ... 20 XV.—POST AND TELEGRAPHS SERVICES ... ... ... ... 20 XVL—MILITARY ... ... ... , 21 XVII—MEANS OF COMMUNICATION ... 22 XVIII.—'RAILWAYS ... ... ... ..«* ... ... ... ... 24 XIX,—PUBLIC WORKS ... ... ... ... ... ... ... 25 XX.—PROVINCIAL ADMINISTRATION ... ... ... ... ... 26 APPRNDIX I.—REPORT ON INVESTIGATIONS CONDUCTED AT THE SI IMPERIAL INSTITUTE DURING 1911. APPENDIX II—BAEO-KANO RAILWAY ... 82 o TABLE I.—PROVINCIAL STATISTICS 86 TABLE II.—COST OP PROVINCIAL ADMINIBTBATION, &C. ... ... 88 TABLE III.-—BEIT-E^-MAL ... ... ... ... ... ... * ... 88 TABLE IV.—STATEMENT ot RECEIPTS (GOVERNMENT SHARE) PROM 89 LOCAL REVENUE. No. 738. NORTHERN NIGERIA. (For Report for 1910-11, see No. 704.) THE ACTING GOVEBKOB to THE SECRETARY OP STATE. -

Improved Quality of Rice Processing (NIG 225)
Winrock International Nigeria Farmer-to-Farmer Program Improved Quality of Rice Processing (NIG 225) Consultant Report: Richard (Dick) Tinsley1 Professor Emeritus, Colorado State University July 2011 1 http://lamar.colostate.edu/~rtinsley/Author.htm Table of Contents Table of Contents. i List of Figures . ii List of Tables. ii List of Acronyms. iii Executive Summary. iv Introduction . 1 Time of Consultancy . 2 Rice Production . 3 AADIL . 5 Limitations of Agronomy . 6 Estate Mode . 7 Chisel Plows . 8 Support Services . 8 Full Water Control . 9 Rice Value Chain . 10 Parboiling . 11 Rice Quality . 13 Paddy Results . 13 Parboiled Rice . .15 Raw Rice . 16 Milling . 17 Other Ways to Improve Quality & Recovery . 19 Small Combines . 20 Winnowing Machines . 21 Other Concerns to Consider . 21 Value Added vs. Outsourcing . 21 Basic Business Model . 22 Access to Mechanization . 23 Micro-Credit . 24 Summary and Recommendations . 24 Appendix Daily Activity Log . A – 1 Monthly Rainfall Varibility . A – 5 i List of Figures 1. Map of Nigeria with Adamawa State, and Yola in box . 1 2. Typical manual harvesting of rice in Ghana . 2 3. Intermediate deep water rice production system around Yola . 4 4. Destoner used to remove mud clods and stones from rice . 4 5. Section of a village used for buying paddy from farmers . .10 6. The parboiling process . 11 7. Larger vat used for parboiling rice and holding up to 10 bags . 12 8. Hotel staff assisting with separating head rice from brokens, etc. 13 9 Paddy samples showing degree of good paddy and trash . 14 10. Vietnamese women demonstrating how placing grain in the sun can help control weevils 14 11. -

Biometric Registration 4 December 2018
State: LGA: Ward: DTM Dakri, Damare, Nigeria Adamawa Girei Girei Girei 1, Modire/Vinikilang Biometric Registration 4 December 2018 Yobe Total Registered Borno individuals households Gombe 16,479 6,327 Adamawa PPP Girei 1 76% 16% Cameroon Dakri SANGERE DUTSE _IDPs Women and Children Children under 5 years Taraba P SABON GARI P 43% 57% Male Female ± Girei 2 Girei 3% 11% Elderly People with ANGWAN KARA vulnerabilities P FEDERAL HOUSING P LGA of origin of registered individuals LGA % Household size distribution MADAGALI 40% % Damare % GWOZA 24% 20 20 BADIRISA/LAINDE MICHIKA 12% % P HONG 4% 5 BAJABURE 1 ASKIRA / UBA 3% % % P Modire 3 MUBI NORTH 2% 2 1 1 DAMBOA 2% NUMAN 2% % 9 BAMA 2% Others 10% % JABBORE 5 P % P 3 Registration site 1% Percentage of households Percentage 1% 1% Yola North 0 0.75 1.5 3 Km Ward boundary 1 2 3 4 5 6 7 8 9 1 0 1 1 Household size Recently concluded Biometric Registra�on in Girei Local Government Area (LGA), within the period of 13 November – 28 November 2018, has brought the total number of Returnees and Displaced persons in Girei (LGA) to 16,476 individuals (6,327 households). The average family size within the loca�on is 3, with 33 per cent of families comprising of 1 - 2 members; 35 per cent comprising of 3 - 4 members; 21 per cent comprising of 5-6 members; 8 per cent comprising of 7-8 members; and 3 per cent comprising of 9 and above members. During the registra�on exercise, the enumerators collected vulnerability data to iden�fy individuals who may require addi�onal humanitarian assistance. -
Week 29 Report
CCCM - NIGERIA Multi Sector Tracker weekly report Date of report 29 July 2017 17 to 23 July 2017 (Week 29) INTRODUCTION The site tracker is a weekly gap analysis and monitoring of services tool used by the site facilitators and site management agencies, in support of the Government camp management agencies and in areas with no camp managers, to identify and refer gaps in delivery and assistance in IDP sites. It enables stakeholders to track activities and avoid duplication of eorts, in support of the sectors as a basis of follow-up on quality of services delivered. It contributes to speed up the time of response by concerned partners and avoid unnecessary delays. As of July 2017, over 87 camps are covered in Borno and Adamawa by the IOM site facilitators in support of the Government Site Managers, either dedicated or mobile team, to strengthen camp management mechanisms and coordination of delivery. The areas sites covered are located in the following LGAs: Girei,Yola South, Yola North and Fufore. The report must not be misconstrued to represent the situation of all IDP camps in North-eastern Nigeria and covers only the sites in review during the week. 17 Sites in, GIREI, YOLA NORTH and YOLA SOUTH LGAs in ADAMAWA State in review this week GIREI EYN CHURCH VINIKILANG, SEGERE DUTSE, CHEKAMIDERI, LOWCOST QUARTERS, NANA VILLA, UNGWAN ABUJA FUFORE DAWARE CAMP, WURO AHI, FUFORE CAMP YOLA ST. THERESAS CATHEDRAL NORTH YOLA MALKOHI CAMP, DOKKITILLA WUROCHEKKE, HULLERE, SABON DEAL NGURORE, MALKOHI VILLAGE, KILBAJE EXTENSION SOUTH Yobe Borno Adamawa -

Mapping Poverty and Deprivation in Barikin-Sale, Minna, Nigeria
World Academics Journal of ______________________________________________ Research Paper . Management Vol.7, Issue.2, pp.54-59, December (2019) E-ISSN: 2321-905X Mapping Poverty and Deprivation in Barikin-Sale, Minna, Nigeria Isaac I.1*, Habila J.2, Salami H.3, Salami R.O.4, Abutu P.5 1Department of Urban and Regional Planning, Federal University of Technology, Minna 2Department of Urban and Regional Planning, Federal Polytechnic, Nekede, Imo State 3Department of Urban and Regional Planning, University of Ibadan 4,5University Library Services, Federal University of Technology, Minna *Corresponding Author: [email protected], Tel. +2349098575008 Available online at: www.isroset.org Received: 05/Dec/2019, Accepted: 20/Dec/2019, Online: 31/Dec/2019 Abstract- Poverty is a very serious problem facing currently bedevilling a large proportion of the global population. This problem is becoming intensified with the rapid rate of global population growth and unprecedented urbanisation. More worrisome is the fact that this phenomenon has translated into urbanisation of poverty. This study aimed at mapping poverty and deprivation in Barikin Sale neighbourhood of Minna, Nigeria; and the objectives are to obtain the base map of the study area, acquire data on household deprivation in the study area, assess the rate of deprivation in the neighbourhood and produce poverty maps of the study area. Barikin Sale was subdivided into 10 small areas which were termed sub-neighbourhoods which form the units of analysis and mapping. Ten households were randomly sampled from each sub-neighbourhood. Descriptive and inferential analyses were carried out and it was discovered that household deprivation is more obvious at sub- neighbourhoods level than at the general neighbourhood level. -

Geospatial Analysis of Flood Problems in Jimeta Riverine Community of Adamawa State, Nigeria
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by International Institute for Science, Technology and Education (IISTE): E-Journals Journal of Environment and Earth Science www.iiste.org ISSN 2224-3216 (Paper) ISSN 2225-0948 (Online) Vol.5, No.12, 2015 Geospatial Analysis of Flood Problems in Jimeta Riverine Community of Adamawa State, Nigeria Innocent E. Bello 1* Steve O. Ogedegbe 2 1. MP, IT and Data Management Dept., National Space Research and Development Agency (NASRDA), Obasanjo Space Centre, Airport Road, PMB 437 Garki, Abuja, Nigeria. 2. Department of Geography, College of Education, Igueben, Edo State, Nigeria Abstract Floods are among the most devastating natural disasters in the world, claiming more lives and causing more property damages than any other natural phenomena. In recent times, the incidence of flooding across Nigeria has left both the government and the governed devastated. It is no longer news that flooding and its attendant consequences are injurious to man while the spatial dimensions are often not mapped. This study, therefore, examined the nature of water level/extent and vulnerability in the riverine community of Jimeta, Adamawa State. Using time series analysis, four epoch satellite images covering the study area was used to evaluate the geospatial coverage of water along the watercourse of Upper Benue bordering the study area. Using ILWIS 3.8, ArcGIS 10.1 and statistical analysis, the spatial extent and vulnerability of settlements was mapped. Highly vulnerable (50m buffer) were differentiated from low risk zones (100m buffers). Study revealed that besides rainfall, excess water from Cameroun dam is largely responsible for the identified high level of inundation.