Debugging and Optimization of Scientific Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fortran Resources 1
Fortran Resources 1 Ian D Chivers Jane Sleightholme October 17, 2020 1The original basis for this document was Mike Metcalf’s Fortran Information File. The next input came from people on comp-fortran-90. Details of how to subscribe or browse this list can be found in this document. If you have any corrections, additions, suggestions etc to make please contact us and we will endeavor to include your comments in later versions. Thanks to all the people who have contributed. 2 Revision history The most recent version can be found at https://www.fortranplus.co.uk/fortran-information/ and the files section of the comp-fortran-90 list. https://www.jiscmail.ac.uk/cgi-bin/webadmin?A0=comp-fortran-90 • October 2020. Added an entry for Nvidia to the compiler section. Nvidia has integrated the PGI compiler suite into their NVIDIA HPC SDK product. Nvidia are also contributing to the LLVM Flang project. • September 2020. Added a computer arithmetic and IEEE formats section. • June 2020. Updated the compiler entry with details of standard conformance. • April 2020. Updated the Fortran Forum entry. Damian Rouson has taken over as editor. • April 2020. Added an entry for Hewlett Packard Enterprise in the compilers section • April 2020. Updated the compiler section to change the status of the Oracle compiler. • April 2020. Added an entry in the links section to the ACM publication Fortran Forum. • March 2020. Updated the Lorenzo entry in the history section. • December 2019. Updated the compiler section to add details of the latest re- lease (7.0) of the Nag compiler, which now supports coarrays and submodules. -
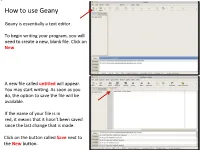
Geany Tutorial
How to use Geany Geany is essentially a text editor. To begin writing your program, you will need to create a new, blank file. Click on New. A new file called untitled will appear. You may start writing. As soon as you do, the option to save the file will be available. If the name of your file is in red, it means that it hasn’t been saved since the last change that is made. Click on the button called Save next to the New button. Save the file in a directory you had previously created before you launched Geany and name it main.cpp. All of the files you will write and submit to will be named specifically main.cpp. Once the .cpp has been specified, Geany will turn on its color coding feature for the C++ template. Next, we will set up our environment and then write a simple program that will print something to the screen Feel free to supply your own name in this small program Before we do anything with it, we will need to configure some options to make your life easier in this class The vertical line to the right marks the ! boundary of your code. You will need to respect this limit in that any line of code you write must not cross this line and therefore be properly, manually broken down to the next line. Your code will be printed out for The line is not where it should be, however, and grading, and if your code crosses the we will now correct it line, it will cause line-wrapping and some points will be deducted. -
Fira Code: Monospaced Font with Programming Ligatures
Personal Open source Business Explore Pricing Blog Support This repository Sign in Sign up tonsky / FiraCode Watch 282 Star 9,014 Fork 255 Code Issues 74 Pull requests 1 Projects 0 Wiki Pulse Graphs Monospaced font with programming ligatures 145 commits 1 branch 15 releases 32 contributors OFL-1.1 master New pull request Find file Clone or download lf- committed with tonsky Add mintty to the ligatures-unsupported list (#284) Latest commit d7dbc2d 16 days ago distr Version 1.203 (added `__`, closes #120) a month ago showcases Version 1.203 (added `__`, closes #120) a month ago .gitignore - Removed `!!!` `???` `;;;` `&&&` `|||` `=~` (closes #167) `~~~` `%%%` 3 months ago FiraCode.glyphs Version 1.203 (added `__`, closes #120) a month ago LICENSE version 0.6 a year ago README.md Add mintty to the ligatures-unsupported list (#284) 16 days ago gen_calt.clj Removed `/**` `**/` and disabled ligatures for `/*/` `*/*` sequences … 2 months ago release.sh removed Retina weight from webfonts 3 months ago README.md Fira Code: monospaced font with programming ligatures Problem Programmers use a lot of symbols, often encoded with several characters. For the human brain, sequences like -> , <= or := are single logical tokens, even if they take two or three characters on the screen. Your eye spends a non-zero amount of energy to scan, parse and join multiple characters into a single logical one. Ideally, all programming languages should be designed with full-fledged Unicode symbols for operators, but that’s not the case yet. Solution Download v1.203 · How to install · News & updates Fira Code is an extension of the Fira Mono font containing a set of ligatures for common programming multi-character combinations. -

Metadefender Core V4.12.2
MetaDefender Core v4.12.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

The Glib/GTK+ Development Platform
The GLib/GTK+ Development Platform A Getting Started Guide Version 0.8 Sébastien Wilmet March 29, 2019 Contents 1 Introduction 3 1.1 License . 3 1.2 Financial Support . 3 1.3 Todo List for this Book and a Quick 2019 Update . 4 1.4 What is GLib and GTK+? . 4 1.5 The GNOME Desktop . 5 1.6 Prerequisites . 6 1.7 Why and When Using the C Language? . 7 1.7.1 Separate the Backend from the Frontend . 7 1.7.2 Other Aspects to Keep in Mind . 8 1.8 Learning Path . 9 1.9 The Development Environment . 10 1.10 Acknowledgments . 10 I GLib, the Core Library 11 2 GLib, the Core Library 12 2.1 Basics . 13 2.1.1 Type Definitions . 13 2.1.2 Frequently Used Macros . 13 2.1.3 Debugging Macros . 14 2.1.4 Memory . 16 2.1.5 String Handling . 18 2.2 Data Structures . 20 2.2.1 Lists . 20 2.2.2 Trees . 24 2.2.3 Hash Tables . 29 2.3 The Main Event Loop . 31 2.4 Other Features . 33 II Object-Oriented Programming in C 35 3 Semi-Object-Oriented Programming in C 37 3.1 Header Example . 37 3.1.1 Project Namespace . 37 3.1.2 Class Namespace . 39 3.1.3 Lowercase, Uppercase or CamelCase? . 39 3.1.4 Include Guard . 39 3.1.5 C++ Support . 39 1 3.1.6 #include . 39 3.1.7 Type Definition . 40 3.1.8 Object Constructor . 40 3.1.9 Object Destructor . -

Php Editor Mac Freeware Download
Php editor mac freeware download Davor's PHP Editor (DPHPEdit) is a free PHP IDE (Integrated Development Environment) which allows Project Creation and Management, Editing with. Notepad++ is a free and open source code editor for Windows. It comes with syntax highlighting for many languages including PHP, JavaScript, HTML, and BBEdit costs $, you can also download a free trial version. PHP editor for Mac OS X, Windows, macOS, and Linux features such as the PHP code builder, the PHP code assistant, and the PHP function list tool. Browse, upload, download, rename, and delete files and directories and much more. PHP Editor free download. Get the latest version now. PHP Editor. CodeLite is an open source, free, cross platform IDE specialized in C, C++, PHP and ) programming languages which runs best on all major Platforms (OSX, Windows and Linux). You can Download CodeLite for the following OSs. Aptana Studio (Windows, Linux, Mac OS X) (FREE) Built-in macro language; Plugins can be downloaded and installed from within jEdit using . EditPlus is a text editor, HTML editor, PHP editor and Java editor for Windows. Download For Mac For macOS or later Release notes - Other platforms Atom is a text editor that's modern, approachable, yet hackable to the core—a tool. Komodo Edit is a simple, polyglot editor that provides the basic functionality you need for programming. unit testing, collaboration, or integration with build systems, download Komodo IDE and start your day trial. (x86), Mac OS X. Download your free trial of Zend Studio - the leading PHP Editor for Zend Studio - Mac OS bit fdbbdea, Download. -

Red Hat Developer Toolset 9 User Guide
Red Hat Developer Toolset 9 User Guide Installing and Using Red Hat Developer Toolset Last Updated: 2020-08-07 Red Hat Developer Toolset 9 User Guide Installing and Using Red Hat Developer Toolset Zuzana Zoubková Red Hat Customer Content Services Olga Tikhomirova Red Hat Customer Content Services [email protected] Supriya Takkhi Red Hat Customer Content Services Jaromír Hradílek Red Hat Customer Content Services Matt Newsome Red Hat Software Engineering Robert Krátký Red Hat Customer Content Services Vladimír Slávik Red Hat Customer Content Services Legal Notice Copyright © 2020 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. -

Download Chapter 3: "Configuring Your Project with Autoconf"
CONFIGURING YOUR PROJECT WITH AUTOCONF Come my friends, ’Tis not too late to seek a newer world. —Alfred, Lord Tennyson, “Ulysses” Because Automake and Libtool are essen- tially add-on components to the original Autoconf framework, it’s useful to spend some time focusing on using Autoconf without Automake and Libtool. This will provide a fair amount of insight into how Autoconf operates by exposing aspects of the tool that are often hidden by Automake. Before Automake came along, Autoconf was used alone. In fact, many legacy open source projects never made the transition from Autoconf to the full GNU Autotools suite. As a result, it’s not unusual to find a file called configure.in (the original Autoconf naming convention) as well as handwritten Makefile.in templates in older open source projects. In this chapter, I’ll show you how to add an Autoconf build system to an existing project. I’ll spend most of this chapter talking about the fundamental features of Autoconf, and in Chapter 4, I’ll go into much more detail about how some of the more complex Autoconf macros work and how to properly use them. Throughout this process, we’ll continue using the Jupiter project as our example. Autotools © 2010 by John Calcote Autoconf Configuration Scripts The input to the autoconf program is shell script sprinkled with macro calls. The input stream must also include the definitions of all referenced macros—both those that Autoconf provides and those that you write yourself. The macro language used in Autoconf is called M4. (The name means M, plus 4 more letters, or the word Macro.1) The m4 utility is a general-purpose macro language processor originally written by Brian Kernighan and Dennis Ritchie in 1977. -

Editors Desk ...2
The content of this magazine is released under the Creative Commons Attribution-Share Alike 3.0 Unported license. For more information visit user http://creativecommons.org/licenses/by-sa/3.0 TM Issue #1 - April 2009 EDITORS DESK ................................ 2 COMMUNITY NEWS ........................ 3 CHOOSING A DE/WM ...................... 4 HARDENING SSH IN 60 SECONDS .................................... 6 GAMERS CORNER .......................... 9 TIPS & TRICKS ............................... 10 PIMP MY ARCH .............................. 11 SOFTWARE REVIEW ......................12 Q&A ..................................................14 EEDDIITTOORRSS DDEESSKK Welcome to the first issue of Arch User Magazine! ARCH USER STAFF Daniel Griffiths (Ghost1227) ........... Editor ello, and thank you for picking up issue #1 of Arch User Magazine! While David Crouse (Crouse) .......... Contributor the vast majority of you probably know me (or have at least seen me H around the forums), I feel that I should take a moment to introduce myself. My name is Daniel Griffiths, and I am a 26-year-old independent contractor in Delaware, US. Throughout my life, I have wandered through various UNIX/Linux systems including (but not limited to) MINIX, RedHat, Mandrake, Slackware, Gentoo, Debian, and even two home made distributions based on Linux From Scratch. I finally found Arch in 2007 and instantly fell in love with its elegant simplicity. Some of our more attentive readers may note that Arch already has a monthly newsletter. With the existence of the aformentioned newsletter, what is the point of adding another news medium to the mix? Fear not, newsletter readers, I have no intention of letting Arch User Magazine take the place of the newsletter. In fact, Arch User Magazine and the newsletter are intended to fill two very different needs in the Arch community. -
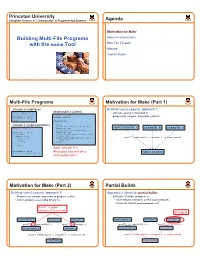
Building Multi-File Programs with the Make Tool
Princeton University Computer Science 217: Introduction to Programming Systems Agenda Motivation for Make Building Multi-File Programs Make Fundamentals with the make Tool Non-File Targets Macros Implicit Rules 1 2 Multi-File Programs Motivation for Make (Part 1) intmath.h (interface) Building testintmath, approach 1: testintmath.c (client) #ifndef INTMATH_INCLUDED • Use one gcc217 command to #define INTMATH_INCLUDED #include "intmath.h" int gcd(int i, int j); #include <stdio.h> preprocess, compile, assemble, and link int lcm(int i, int j); #endif int main(void) { int i; intmath.c (implementation) int j; printf("Enter the first integer:\n"); #include "intmath.h" scanf("%d", &i); testintmath.c intmath.h intmath.c printf("Enter the second integer:\n"); int gcd(int i, int j) scanf("%d", &j); { int temp; printf("Greatest common divisor: %d.\n", while (j != 0) gcd(i, j)); { temp = i % j; printf("Least common multiple: %d.\n", gcc217 testintmath.c intmath.c –o testintmath i = j; lcm(i, j); j = temp; return 0; } } return i; } Note: intmath.h is int lcm(int i, int j) #included into intmath.c { return (i / gcd(i, j)) * j; testintmath } and testintmath.c 3 4 Motivation for Make (Part 2) Partial Builds Building testintmath, approach 2: Approach 2 allows for partial builds • Preprocess, compile, assemble to produce .o files • Example: Change intmath.c • Link to produce executable binary file • Must rebuild intmath.o and testintmath • Need not rebuild testintmath.o!!! Recall: -c option tells gcc217 to omit link changed testintmath.c intmath.h intmath.c -

Assessing Unikernel Security April 2, 2019 – Version 1.0
NCC Group Whitepaper Assessing Unikernel Security April 2, 2019 – Version 1.0 Prepared by Spencer Michaels Jeff Dileo Abstract Unikernels are small, specialized, single-address-space machine images constructed by treating component applications and drivers like libraries and compiling them, along with a kernel and a thin OS layer, into a single binary blob. Proponents of unikernels claim that their smaller codebase and lack of excess services make them more efficient and secure than full-OS virtual machines and containers. We surveyed two major unikernels, Rumprun and IncludeOS, and found that this was decidedly not the case: unikernels, which in many ways resemble embedded systems, appear to have a similarly minimal level of security. Features like ASLR, W^X, stack canaries, heap integrity checks and more are either completely absent or seriously flawed. If an application running on such a system contains a memory corruption vulnerability, it is often possible for attackers to gain code execution, even in cases where the applica- tion’s source and binary are unknown. Furthermore, because the application and the kernel run together as a single process, an attacker who compromises a unikernel can immediately exploit functionality that would require privilege escalation on a regular OS, e.g. arbitrary packet I/O. We demonstrate such attacks on both Rumprun and IncludeOS unikernels, and recommend measures to mitigate them. Table of Contents 1 Introduction to Unikernels . 4 2 Threat Model Considerations . 5 2.1 Unikernel Capabilities ................................................................ 5 2.2 Unikernels Versus Containers .......................................................... 5 3 Hypothesis . 6 4 Testing Methodology . 7 4.1 ASLR ................................................................................ 7 4.2 Page Protections .................................................................... -

AMD Optimizing CPU Libraries User Guide Version 2.1
[AMD Public Use] AMD Optimizing CPU Libraries User Guide Version 2.1 [AMD Public Use] AOCL User Guide 2.1 Table of Contents 1. Introduction .......................................................................................................................................... 4 2. Supported Operating Systems and Compliers ...................................................................................... 5 3. BLIS library for AMD .............................................................................................................................. 6 3.1. Installation ........................................................................................................................................ 6 3.1.1. Build BLIS from source .................................................................................................................. 6 3.1.1.1. Single-thread BLIS ..................................................................................................................... 6 3.1.1.2. Multi-threaded BLIS .................................................................................................................. 6 3.1.2. Using pre-built binaries ................................................................................................................. 7 3.2. Usage ................................................................................................................................................. 7 3.2.1. BLIS Usage in FORTRAN ................................................................................................................