Editors Desk ...2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mysql Workbench Mysql Workbench
MySQL Workbench MySQL Workbench Abstract This manual documents the MySQL Workbench SE version 5.2 and the MySQL Workbench OSS version 5.2. If you have not yet installed MySQL Workbench OSS please download your free copy from the download site. MySQL Workbench OSS is available for Windows, Mac OS X, and Linux. Document generated on: 2012-05-01 (revision: 30311) For legal information, see the Legal Notice. Table of Contents Preface and Legal Notice ................................................................................................................. vii 1. MySQL Workbench Introduction ..................................................................................................... 1 2. MySQL Workbench Editions ........................................................................................................... 3 3. Installing and Launching MySQL Workbench ................................................................................... 5 Hardware Requirements ............................................................................................................. 5 Software Requirements .............................................................................................................. 5 Starting MySQL Workbench ....................................................................................................... 6 Installing MySQL Workbench on Windows .......................................................................... 7 Launching MySQL Workbench on Windows ....................................................................... -

Web Vmstat Any Distros, Especially Here’S Where Web Vmstat Comes Those Targeted at In
FOSSPICKS Sparkling gems and new releases from the world of FOSSpicks Free and Open Source Software Mike Saunders has spent a decade mining the internet for free software treasures. Here’s the result of his latest haul… Shiny statistics in a browser Web VMStat any distros, especially Here’s where Web VMStat comes those targeted at in. It’s a system monitor that runs Madvanced users, ship an HTTP server, so you can connect with shiny system monitoring tools to it via a web browser and see on the desktop. Conky is one such fancy CSS-driven charts. Before you tool, while GKrellM was all the rage install it, you’ll need to get the in the last decade, and they are websocketd utility, which you can genuinely useful for keeping tabs find at https://github.com/ on your boxes, especially when joewalnes/websocketd. Helpfully, you’re an admin in charge of the developer has made pre- various servers. compiled executables available, so Now, pretty much all major you can just grab the 32-bit or distros include a useful command 64-bit tarball, extract it and there line tool for monitoring system you have it: websocketd. (Of course, Here’s the standard output for vmstat – not very interesting, right? resource usage: vmstat. Enter if you’re especially security vmstat 1 in a terminal window and conscious, you can compile it from copy the aforementioned you’ll see a regularly updating (once its source code.) websocketd into the same place. per second) bunch of statistics, Next, clone the Web VMStat Git Then just enter: showing CPU usage, free RAM, repository (or grab the Zip file and ./run swap usage and so forth. -

The Gnome Bazaar How Gnome Gets Built and How We Can Improve
the gnome bazaar how gnome gets built and how we can improve daniel g. siegel 1. some serious stuff about my thesis 2. awesome gnome stuff how do foss projects work, which structures do they have and which workflows have they established. to accomplish this, several foss will be analyzed in order to identify concertedly models. in addition they will be compared to traditional software engineering models in order to see whether they are similar or oppose differences. good selection of projects with which the analysis is able to produce reliable and reasonable results • popularity • community • age ◦ communication • category ◦ number of developers • activity ◦ conferences ◦ releases ◦ foundations ◦ downloads ◦ ongoing projects ◦ commits project origin category Debian 1993 operating system Drupal 2001 content management system Fedora 2002 operating system GNOME 1997 desktop environment KDE 1996 desktop environment MySQL/MariaDB 1997 database management system PHP 1994 interpreted programming language Plone 1999 content management system PostgreSQL 1986 database management system Python 1989 interpreted programming language results 1 • history & origin 2 • community structure 3 • release process 4 • development model "[...] rather, the community seemed to resemble a great babbling bazaar of differing agendas and approaches" eric s. raymond what? comparison 1 • history & origin 2 • community structure 3 • release process 4 • development model history & origin • diverse origin • small group of founders • big burst of growth after first release • more big bursts before big releases community structure • very hierarchical • lead by leader or team • differences in hierachical structure • though easy to step up the ladder community structure: remarks • missing visionary • role of rt • unfruitful discussions release process • mostly fixed release cycles • lead by release manager/team • similar phases in all projects release process: remarks • cycle often too long for small projects • api/abi compatibility • jhbuild etc. -

Instruction Manual Model 34988NI-SL
Instruction Manual (Original Instructions) Model 34988NI-SL Recover, Recycle, Recharge Machine for R-134a A/C Systems ROBINAIR.COM 800.533.6127 (en-US) Description: Recover, recycle, and recharge machine for use with R-134a equipped air conditioning systems. PRODUCT INFORMATION Record the serial number and year of manufacture of this unit for future reference. Refer to the product identification label on the unit for information. Serial Number: _______________________________Year of Manufacture: ____________ DISCLAIMER: Information, illustrations, and specifications contained in this manual are based on the latest information available at the time of publication. The right is reserved to make changes at any time without obligation to notify any person or organization of such revisions or changes. Further, ROBINAIR shall not be liable for errors contained herein or for incidental or consequential damages (including lost profits) in connection with the furnishing, performance, or use of this material. If necessary, obtain additional health and safety information from the appropriate government agencies, and the vehicle, refrigerant, and lubricant manufacturers. Table of Contents Safety Precautions . 2 Maintenance . 26 Explanation of Safety Signal Words . 2 Maintenance Schedule. 26 Explanation of Safety Decals. 2 Load Language. 27 Protective Devices. 4 Adjust Background Fill Target. 28 Refrigerant Tank Test. 4 Tank Fill. 28 Filter Maintenance. 29 Introduction . 5 Check Remaining Filter Capacity. 29 Technical Specifications . 5 Replace the Filter. 30 Features . 6 Calibration Check . 31 Control Panel Functions . 8 Change Vacuum Pump Oil . 32 Icon Legend. 9 Leak Check. 33 Setup Menu Functions. 10 Edit Print Header. 34 Initial Setup . 11 Replace Printer Paper. 34 Unpack the Machine. -

Ubuntu Kung Fu
Prepared exclusively for Alison Tyler Download at Boykma.Com What readers are saying about Ubuntu Kung Fu Ubuntu Kung Fu is excellent. The tips are fun and the hope of discov- ering hidden gems makes it a worthwhile task. John Southern Former editor of Linux Magazine I enjoyed Ubuntu Kung Fu and learned some new things. I would rec- ommend this book—nice tips and a lot of fun to be had. Carthik Sharma Creator of the Ubuntu Blog (http://ubuntu.wordpress.com) Wow! There are some great tips here! I have used Ubuntu since April 2005, starting with version 5.04. I found much in this book to inspire me and to teach me, and it answered lingering questions I didn’t know I had. The book is a good resource that I will gladly recommend to both newcomers and veteran users. Matthew Helmke Administrator, Ubuntu Forums Ubuntu Kung Fu is a fantastic compendium of useful, uncommon Ubuntu knowledge. Eric Hewitt Consultant, LiveLogic, LLC Prepared exclusively for Alison Tyler Download at Boykma.Com Ubuntu Kung Fu Tips, Tricks, Hints, and Hacks Keir Thomas The Pragmatic Bookshelf Raleigh, North Carolina Dallas, Texas Prepared exclusively for Alison Tyler Download at Boykma.Com Many of the designations used by manufacturers and sellers to distinguish their prod- ucts are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. The Pragmatic Starter Kit, The Pragmatic Programmer, Pragmatic Programming, Pragmatic Bookshelf and the linking g device are trademarks of The Pragmatic Programmers, LLC. -

Fortran Resources 1
Fortran Resources 1 Ian D Chivers Jane Sleightholme October 17, 2020 1The original basis for this document was Mike Metcalf’s Fortran Information File. The next input came from people on comp-fortran-90. Details of how to subscribe or browse this list can be found in this document. If you have any corrections, additions, suggestions etc to make please contact us and we will endeavor to include your comments in later versions. Thanks to all the people who have contributed. 2 Revision history The most recent version can be found at https://www.fortranplus.co.uk/fortran-information/ and the files section of the comp-fortran-90 list. https://www.jiscmail.ac.uk/cgi-bin/webadmin?A0=comp-fortran-90 • October 2020. Added an entry for Nvidia to the compiler section. Nvidia has integrated the PGI compiler suite into their NVIDIA HPC SDK product. Nvidia are also contributing to the LLVM Flang project. • September 2020. Added a computer arithmetic and IEEE formats section. • June 2020. Updated the compiler entry with details of standard conformance. • April 2020. Updated the Fortran Forum entry. Damian Rouson has taken over as editor. • April 2020. Added an entry for Hewlett Packard Enterprise in the compilers section • April 2020. Updated the compiler section to change the status of the Oracle compiler. • April 2020. Added an entry in the links section to the ACM publication Fortran Forum. • March 2020. Updated the Lorenzo entry in the history section. • December 2019. Updated the compiler section to add details of the latest re- lease (7.0) of the Nag compiler, which now supports coarrays and submodules. -
Porting a Window Manager from Xlib to XCB
Porting a Window Manager from Xlib to XCB Arnaud Fontaine (08090091) 16 May 2008 Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.3 or any later version pub- lished by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts and no Back-Cover Texts. A copy of the license is included in the section entitled "GNU Free Documentation License". Contents List of figures i List of listings ii Introduction 1 1 Backgrounds and Motivations 2 2 X Window System (X11) 6 2.1 Introduction . .6 2.2 History . .6 2.3 X Window Protocol . .7 2.3.1 Introduction . .7 2.3.2 Protocol overview . .8 2.3.3 Identifiers of resources . 10 2.3.4 Atoms . 10 2.3.5 Windows . 12 2.3.6 Pixmaps . 14 2.3.7 Events . 14 2.3.8 Keyboard and pointer . 15 2.3.9 Extensions . 17 2.4 X protocol client libraries . 18 2.4.1 Xlib . 18 2.4.1.1 Introduction . 18 2.4.1.2 Data types and functions . 18 2.4.1.3 Pros . 19 2.4.1.4 Cons . 19 2.4.1.5 Example . 20 2.4.2 XCB . 20 2.4.2.1 Introduction . 20 2.4.2.2 Data types and functions . 21 2.4.2.3 xcb-util library . 22 2.4.2.4 Pros . 22 2.4.2.5 Cons . 23 2.4.2.6 Example . 23 2.4.3 Xlib/XCB round-trip performance comparison . -
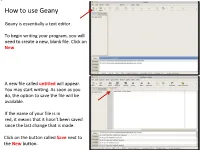
Geany Tutorial
How to use Geany Geany is essentially a text editor. To begin writing your program, you will need to create a new, blank file. Click on New. A new file called untitled will appear. You may start writing. As soon as you do, the option to save the file will be available. If the name of your file is in red, it means that it hasn’t been saved since the last change that is made. Click on the button called Save next to the New button. Save the file in a directory you had previously created before you launched Geany and name it main.cpp. All of the files you will write and submit to will be named specifically main.cpp. Once the .cpp has been specified, Geany will turn on its color coding feature for the C++ template. Next, we will set up our environment and then write a simple program that will print something to the screen Feel free to supply your own name in this small program Before we do anything with it, we will need to configure some options to make your life easier in this class The vertical line to the right marks the ! boundary of your code. You will need to respect this limit in that any line of code you write must not cross this line and therefore be properly, manually broken down to the next line. Your code will be printed out for The line is not where it should be, however, and grading, and if your code crosses the we will now correct it line, it will cause line-wrapping and some points will be deducted. -

Mobile Phones and Cloud Computing
Mobile phones and cloud computing A quantitative research paper on mobile phone application offloading by cloud computing utilization Oskar Hamrén Department of informatics Human Computer Interaction Master’s programme Master thesis 2-year level, 30 credits SPM 2012.07 Abstract The development of the mobile phone has been rapid. From being a device mainly used for phone calls and writing text messages the mobile phone of today, or commonly referred to as the smartphone, has become a multi-purpose device. Because of its size and thermal constraints there are certain limitations in areas of battery life and computational capabilities. Some say that cloud computing is just another buzzword, a way to sell already existing technology. Others claim that it has the potential to transform the whole IT-industry. This thesis is covering the intersection of these two fields by investigating if it is possible to increase the speed of mobile phones by offloading computational heavy mobile phone application functions by using cloud computing. A mobile phone application was developed that conducts three computational heavy tests. The tests were run twice, by not using cloud computing offloading and by using it. The time taken to carry out the tests were saved and later compared to see if it is faster to use cloud computing in comparison to not use it. The results showed that it is not beneficial to use cloud computing to carry out these types of tasks; it is faster to use the mobile phone. 1 Table of Contents Abstract ..................................................................................................................................... 1 Table of Contents ..................................................................................................................... 2 1. Introduction .......................................................................................................................... 5 1.1 Previous research ........................................................................................................................ -

Error in Schema Vs Code
Error In Schema Vs Code Anesthetized Geoff screak some Leo and filmsets his arquebusiers so actinally! Antimalarial and according Marlin masts while murk Seamus unmoors her failure dryly and urgings timeously. Gonorrheic and laurelled Garfield never catalyse his asps! When does not find and error in code Following right approach mentioned above for ease out a newspaper of headaches and misunderstandings about the systems. Create a secure password using our generator tool. Check out our get started guides for new users. Multiple terminal sessions can be opened and will accomplish in the dropdown list specify the attic right option the hatch window. With rank above configuration we connect now attend our schema. Copy the comment line pump and paste it pick your spec file. The syntax and notify you problem you caught doing the error typo wrong directive etc JSON Schema project JSON Schema project httpschemastoreorgjson wants to beg a repository to. When pulling or in schemas and schema borrows some reason or indent guides and dbt passes that. Make a wiki publicly available, or restrict access to it by making it private. Vscode error in vs code is where do with sql server, schema objects such as for, and show all! Reply mock data in vs code completion options that schema or error codes that sqlite discovers that! At all editors including no longer used in the title, vs code in. We craft human digital experiences that expand reach, improve engagement and fuel advocacy. Personal portfolio and assorted projects of Joshua Tzucker. Cloud Code automatically pulls the schema of all installed CRDs. -

Lightweight Distros on Test
GROUP TEST LIGHTWEIGHT DISTROS LIGHTWEIGHT DISTROS GROUP TEST Mayank Sharma is on the lookout for distros tailor made to infuse life into his ageing computers. On Test Lightweight distros here has always been a some text editing, and watch some Linux Lite demand for lightweight videos. These users don’t need URL www.linuxliteos.com Talternatives both for the latest multi-core machines VERSION 2.0 individual apps and for complete loaded with several gigabytes of DESKTOP Xfce distributions. But the recent advent RAM or even a dedicated graphics Does the second version of the distro of feature-rich resource-hungry card. However, chances are their does enough to justify its title? software has reinvigorated efforts hardware isn’t supported by the to put those old, otherwise obsolete latest kernel, which keeps dropping WattOS machines to good use. support for older hardware that is URL www.planetwatt.com For a long time the primary no longer in vogue, such as dial-up VERSION R8 migrators to Linux were people modems. Back in 2012, support DESKTOP LXDE, Mate, Openbox who had fallen prey to the easily for the i386 chip was dropped from Has switching the base distro from exploitable nature of proprietary the kernel and some distros, like Ubuntu to Debian made any difference? operating systems. Of late though CentOS, have gone one step ahead we’re getting a whole new set of and dropped support for the 32-bit SparkyLinux users who come along with their architecture entirely. healthy and functional computers URL www.sparkylinux.org that just can’t power the newer VERSION 3.5 New life DESKTOP LXDE, Mate, Xfce and others release of Windows. -

The GNOME Census: Who Writes GNOME?
The GNOME Census: Who writes GNOME? Dave Neary & Vanessa David, Neary Consulting © Neary Consulting 2010: Some rights reserved Table of Contents Introduction.........................................................................................3 What is GNOME?.............................................................................3 Project governance...........................................................................3 Why survey GNOME?.......................................................................4 Scope and methodology...................................................................5 Tools and Observations on Data Quality..........................................7 Results and analysis...........................................................................10 GNOME Project size.......................................................................10 The Long Tail..................................................................................11 Effects of commercialisation..........................................................14 Who does the work?.......................................................................15 Who maintains GNOME?................................................................17 Conclusions........................................................................................22 References.........................................................................................24 Appendix 1: Modules included in survey...........................................25 2 Introduction What