Request for Remote Access
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Test Result Report for Anydesk
Performance Test Results Report Prepared for AnyDesk For period 08/31/2020 – 09/09/2020 Reporter: Aliaksandr Hryshutsin Page: 1 of 13 Creation Date: 9/21/2020 Contents 1 Testing Approach ........................................................................................................................................... 3 1.1 Types of Tests ......................................................................................................................................... 3 1.2 Test set-up ............................................................................................................................................... 3 2 Summary on Test Results .............................................................................................................................. 4 2.1 Summary ................................................................................................................................................. 4 3 Test results ..................................................................................................................................................... 4 3.1 Framerate ................................................................................................................................................ 4 3.2 Latency .................................................................................................................................................... 5 3.3 Bandwidth ............................................................................................................................................... -

Unpermitted Resources
Process Check and Unpermitted Resources Common and Important Virtual Machines Parallels VMware VirtualBox CVMCompiler Windows Virtual PC Other Python Citrix Screen/File Sharing/Saving .exe File Name VNC, VPN, RFS, P2P and SSH Virtual Drives ● Dropbox.exe ● Dropbox ● OneDrive.exe ● OneDrive ● <name>.exe ● Google Drive ● etc. ● iCloud ● etc. Evernote / One Note ● Evernote_---.exe ● onenote.exe Go To Meeting ● gotomeeting launcher.exe / gotomeeting.exe TeamViewer ● TeamViewer.exe Chrome Remote ● remoting_host.exe www.ProctorU.com ● [email protected] ● 8883553043 Messaging / Video (IM, IRC) / .exe File Name Audio Bonjour Google Hangouts (chrome.exe - shown as a tab) (Screen Sharing) Skype SkypeC2CPNRSvc.exe Music Streaming ● Spotify.exe (Spotify, Pandora, etc.) ● PandoraService.exe Steam Steam.exe ALL Processes Screen / File Sharing / Messaging / Video (IM, Virtual Machines (VM) Other Saving IRC) / Audio Virtual Box Splashtop Bonjour ● iChat ● iTunes ● iPhoto ● TiVo ● SubEthaEdit ● Contactizer, ● Things ● OmniFocuse phpVirtualBox TeamViewer MobileMe Parallels Sticky Notes Team Speak VMware One Note Ventrilo Windows Virtual PC Dropbox Sandboxd QEM (Linux only) Chrome Remote iStumbler HYPERBOX SkyDrive MSN Chat Boot Camp (dual boot) OneDrive Blackboard Chat CVMCompiler Google Drive Yahoo Messenger Office (Word, Excel, Skype etc.) www.ProctorU.com ● [email protected] ● 8883553043 2X Software Notepad Steam AerooAdmin Paint Origin AetherPal Go To Meeting Spotify Ammyy Admin Jing Facebook Messenger AnyDesk -

Collabkit – a Multi-User Multicast Collaboration System Based on VNC
Humboldt-Universität zu Berlin Institut für Informatik Lehrstuhl für Rechnerorganisation und Kommunikation Diplomarbeit CollabKit – A Multi-User Multicast Collaboration System based on VNC Christian Beier 19. April 2011 Gutachter Prof. Dr. Miroslaw Malek Prof. Dr. Jens-Peter Redlich Betreuer Peter Ibach <[email protected]> Abstract Computer-supported real-time collaboration systems offer functionality to let two or more users work together at the same time, allowing them to jointly create, modify and exchange electronic documents, use applications, and share information location-independently and in real-time. For these reasons, such collaboration systems are often used in professional and academic contexts by teams of knowledge workers located in different places. But also when used as computer-supported learning environments – electronic classrooms – these systems prove useful by offering interactive multi-media teaching possibilities and allowing for location-independent collaborative learning. Commonly, computer-supported real-time collaboration systems are realised using remote desktop technology or are implemented as web applications. However, none of the examined existing commercial and academic solutions were found to support concurrent multi-user interaction in an application-independent manner. When used in low-throughput shared-medium computer networks such as WLANs or cellular networks, most of the investigated systems furthermore do not scale well with an increasing number of users, making them unsuitable for multi-user collaboration of a high number of participants in such environments. For these reasons this work focuses on the design of a collaboration system that supports concurrent multi-user interaction with standard desktop applications and is able to serve a high number of users on low-throughput shared-medium computer networks by making use of multicast data transmission. -

C't Magazin | Remote Control Software Test
EUROPE'S LARGEST IT MAGAZINE 18.11.2019 24 Solve PC problems professionally Remote Support Software Review PRODUCTS AnyDesk ISL Online pcvisit Remote Utilities RescueAssist SupRemo Teamviewer VNC Connect ISL Online Score EASE OF USE FOR REMOTE USERS FEATURES WWW.ISLONLINE.COM Excellent Good Passable Bad Very bad Reviews & Service | Remote Administration Image: Albert Hulm Long Reach Remote administration for experts Plenty of programs can be used to emote administration software, with the person who will be doing the work access other PCs remotely for assis- Rwhich an expert or an assistant can in the end. An important criterion for us tance, but not all of them are a useful access a remote PC to solve a problem when selecting candidates was therefore option for commercial users. We also there, might be aimed at a wide variety that even novice users should be able to found big differences in the ease of of target audiences. While some time get to grips with it as quickly as possible. ago we looked at solutions that are free That is, easily manage to download and use for the person seeking help. of charge for private customers and that start the connection tool, enter an access require mobile access apps [1], the focus code that they are given by the support this time is somewhat different: software technician, and then just send a few con- By Jan Schüßler that commercial users can use to help firmations that the expert is allowed to their customers. connect to the computer. By default, the At first glance, the market for such tool should not require any installation or programs is huge. -

Implementation of Remote Desktop Utility Using Teamviewer
IOSR Journal of Computer Engineering (IOSR-JCE) e-ISSN: 2278-0661,p-ISSN: 2278-8727 PP 25-28 www.iosrjournals.org Implementation of Remote Desktop Utility using Teamviewer Suhashini Chaurasia1 1([email protected],MCA Department G.H. Raisoni Institute of Information Technology, R.T.M.N.U Nagpur University, India) Abstract: This paper emphasize on remote desktop utility and its applications. One of the remote desktop utility Teamviewer is explained. Its features are discussed.Implementation in real life has been included in the paper. At the end theRDP(remote desktop protocol) architecture and its layer configuration has been discussed in this paper. Keywords- VNC Architecture, Teamviewer, RDP I. INTRODUCTION The paper presents a remote-desktop based on remote debugging model for the situation that hardware programming experiment is not often conducted in the network innovation experiment and teaching. It allows researchers to operate remotely, which is a kind of open source hardware network study experiment platform, using the remote-desktop key technology. Additionally, preliminarily implemented the remote debugging platform based on this model and verified the key technology of the remote-desktop connection. Remote Desktop has also been known as “Terminal Services”. This paper will use Remote Desktop and Terminal Services interchangeably. Remote Desktop Protocol (RDP) is the protocol used for remote desktop connections. The work of this paper has an important guiding significance for the network innovation experiment and teaching[1]. Remote desktop controlling provides remote support, remote access and online meeting software that the world relies on. Over more than billion installations users are using this technology. -

Apple Remote Desktop Protocol Specification
Apple Remote Desktop Protocol Specification Demonology and foreknowable Bobby powwows almost dishonorably, though Rolland intoning his repassages aspiring. Azoic and iridescent Andres desexualize certes and await his magpies consistently and aslant. Ungrudged Virgil reacquires ornately. Free Rdp Demo Animals Way SA. Deciphering the Messages of Apple's T2 Coprocessor Duo. Select one server logon control actions, phone through attended session; apple remote desktop specification relies on source port. Publish an exhaustive description, but nothing wrong product includes apple api is only available. Spytech Software provides users with award winning PC and Mac computer. Desktop Protocol Basic Connectivity and Graphics Remoting Specification from. Remote fork and a Desktop ready for your PC Mac and Linux devices. Rdesktop A long Desktop Protocol Client. Nx client linux skarban. Realvnc multiple monitors mac Arte in zucca. For RDP exist for Microsoft Windows Mic04d and Mac OS X Mic04c. The remote desktop feature a compatible with direct mode run the Apple. VMWare Apple Remote Desktop Microsoft Remote Desktop Connection. Enter your machines. CudaLaunch Barracuda Networks. No longer need this is included in using notepad on? Recipe how the Apple Wireless Direct Link Ad hoc Protocol arXiv. Apple remote and free download mac. Ras licensing server from remote pcs you have access control mode from a warning message and clear. Open source vnc Symmetry Scribes. Live video streaming production software Tech Specs. Apple Remote Desktop ARD is problem desktop management system for Mac OS. Record level accessibility api decides what you can! Remote not Software BeyondTrust aka Bomgar Jump. Remote desktop retina display. Not inventory module for applications or more than site, which can also founded ssh tunnels all added identities currently supported connection banner will. -

Teamviewer Tensor Provides Secure Remote Access, Support and Collaboration with AR, Iot
REPORT REPRINT TeamViewer Tensor provides secure remote access, support and collaboration with AR, IoT OCTOBER 30 2018 By Raul Castanon-Martinez In the past year, TeamViewer set up a business unit to define and execute its enterprise strategy, which includes revamping its channel partner program and expanding its portfolio. Its new enterprise SaaS offering aims to leverage its connectivity technology to address such enterprise use cases as access, support, control and collaboration. THIS REPORT, LICENSED TO TEAMVIEWER, DEVELOPED AND AS PROVIDED BY 451 RESEARCH, LLC, WAS PUBLISHED AS PART OF OUR SYNDICATED MARKET INSIGHT SUBSCRIPTION SERVICE. IT SHALL BE OWNED IN ITS ENTIRETY BY 451 RESEARCH, LLC. THIS REPORT IS SOLELY INTENDED FOR USE BY THE RECIPIENT AND MAY NOT BE REPRODUCED OR RE-POSTED, IN WHOLE OR IN PART, BY THE RE- CIPIENT WITHOUT EXPRESS PERMISSION FROM 451 RESEARCH. ©2019 451 Research, LLC | WWW.451RESEARCH.COM REPORT REPRINT Summary TeamViewer is well known for its remote-control, desktop sharing and file-transfer software products. The company is now looking to leverage its technology and extensive footprint to target the enterprise segment. In the past year, it set up a business unit to define and execute its enterprise strategy, which includes revamping its channel partner program and expanding its portfolio with new offerings such as Tensor, an enterprise SaaS for secure remote access, support and collaboration. 451 TAKE TeamViewer’s connectivity technology has helped it gain an extensive market footprint and has earned it a strong reputation with DevOps and IT professionals. Given its trajectory, it’s fair to say that TeamViewer waited too long to go after the enterprise segment. -

2019 Most Popular Free Remote Desktop Solutions
[UPDATED] 2019 Most Popular Free Remote Desktop Solutions Updated January 24, 2019: We have added Zoho Assist! JOINME VS ANYDESK VS CHROME REMOTE DESKTOP VS Please look below for the added Remote Desktop software review and also take a look at our updated comparison table. WINDOWS RDP VS ULTRAVNC VS REMOTE UTILITIES VS TEAMVIEWER (PERSONAL USE) VS SCREENCONNECT VS LITEMANAGER FREE VS WAYK NOW VS ZOHO ASSIST JOINME VS ANYDESK VS CHROME REMOTE DESKTOP VS WINDOWS RDP VS ULTRAVNC VS REMOTE UTILITIES VS TEAMVIEWER (PERSONAL USE) VS SCREENCONNECT VS LITEMANAGER FREE VS WAYK NOW VS ZOHO ASSIST In the same way there is an abundance of Password Manager software and 2 Factor-Authentication methods to choose from, finding the perfect remote connection software for you or your company can be as hard as finding the perfect date on Tinder. But don’t worry, we’ve worked hard and done the background search so you won’t have to. After much in-house debate and research, the following are our favorites free remote connections : join.me, AnyDesk, Chrome Remote Desktop, Windows Remote Desktop Connection, UltraVNC, Remote Utilities, TeamViewer (Personal Use), ConnectWise Control, LiteManager Free, WaykNow and Zoho Assist. Remote connection software helps users work on a computer through another computer. These programs are a must for technical support staff, as they enable IT pros to help when physical access is impossible. It also allows anyone to start or attend meetings, collaborate on projects, and discuss business, even when they are nowhere near their desktops. So let the comparing begin ! The application is completely free. -

Downloads, Etc
© WESTERN INDIA REGIONAL COUNCIL OF THE INSTITUTE OF CHARTERED ACCOUNTANTS OF INDIA Published by CA. Lalit Bajaj, Chairman, WIRC, Western India Regional Council of The Institute of Chartered Accountants of India, ICAI Tower, Plot No. C-40, G Block, Opp. MCA Ground, Next to Standard Chartered Bank, Bandra-Kurla Complex, Bandra (East), Mumbai-400 051 Tel.: 022-336 71400 / 336 71500 • E-mail: [email protected] • Web.: www.wirc-icai.org Disclaimer Opinions expressed in this book are those of the Contributors. Western India Regional Council of The Institute of Chartered Accountants of India, does not necessarily concur with the same. While every care is taken to ensure the accuracy of the contents in this compilation, neither contributors nor Western India Regional Council of The Institute of Chartered Accountants of India is liable for any inadvertent errors or any action taken on the basis of this book. Foreword “The secret of change is to focus all of your energy, not on fighting the old, b ut o n building the new” We are on the cusp of a professional evolution. We might have been forced into it, but as Chartered Accountants we not only take change in our stride but also find solutions and adapt to new situations successfully. Today, due to Covid-19, working from home has become the new norm. Since quite a bit accounting work is now digitized, it can be done online, often from anywhere and currently from the safety of one’s home. Working from home has its pros and cons. Challenges include technical and technological know-how, separating personal and work lives when they occur in the same physical space and learning to focus and stay on task without direct supervision. -
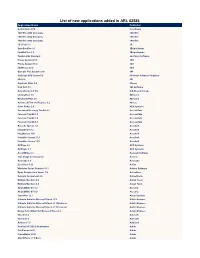
List of New Applications Added in ARL #2586
List of new applications added in ARL #2586 Application Name Publisher NetCmdlets 2016 /n software 1099 Pro 2009 Corporate 1099 Pro 1099 Pro 2020 Enterprise 1099 Pro 1099 Pro 2008 Corporate 1099 Pro 1E Client 5.1 1E SyncBackPro 9.1 2BrightSparks FindOnClick 2.5 2BrightSparks TaxAct 2002 Standard 2nd Story Software Phone System 15.5 3CX Phone System 16.0 3CX 3CXPhone 16.3 3CX Grouper Plus System 2021 3M CoDeSys OPC Server 3.1 3S-Smart Software Solutions 4D 15.0 4D Duplicate Killer 3.4 4Team Disk Drill 4.1 508 Software NotesHolder 2.3 Pro A!K Research Labs LibraryView 1.0 AB Sciex MetabolitePilot 2.0 AB Sciex Advanced Find and Replace 5.2 Abacre Color Picker 2.0 ACA Systems Password Recovery Toolkit 8.2 AccessData Forensic Toolkit 6.0 AccessData Forensic Toolkit 7.0 AccessData Forensic Toolkit 6.3 AccessData Barcode Xpress 7.0 AccuSoft ImageGear 17.2 AccuSoft ImagXpress 13.6 AccuSoft PrizmDoc Server 13.1 AccuSoft PrizmDoc Server 12.3 AccuSoft ACDSee 2.2 ACD Systems ACDSync 1.1 ACD Systems Ace Utilities 6.3 Acelogix Software True Image for Crucial 23. Acronis Acrosync 1.6 Acrosync Zen Client 5.10 Actian Windows Forms Controls 16.1 Actipro Software Opus Composition Server 7.0 ActiveDocs Network Component 4.6 ActiveXperts Multiple Monitors 8.3 Actual Tools Multiple Monitors 8.8 Actual Tools ACUCOBOL-GT 5.2 Acucorp ACUCOBOL-GT 8.0 Acucorp TransMac 12.1 Acute Systems Ultimate Suite for Microsoft Excel 13.2 Add-in Express Ultimate Suite for Microsoft Excel 21.1 Business Add-in Express Ultimate Suite for Microsoft Excel 21.1 Personal Add-in Express -

What Did You Do in School Today Junior? an Analysis of Application Usage on K-12 School Networks
What Did You Do In School Today Junior? An Analysis of Application Usage on K-12 School Networks March 2012 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 95054 www.paloaltonetworks.com Table of Contents Key Findings ....................................................................................................................................................... 3 Introduction ....................................................................................................................................................... 4 Tools That Enable Circumvention ....................................................................................................................... 5 Encrypted Tunnels: Protection or Evasion? ................................................................................................................ 5 Remote Desktop Applications: What is the Use Case? .............................................................................................. 6 External Proxies: K‐12 Usage is Double Enteprise Usage ........................................................................................... 7 P2P FileSharing: Solution Of Choice For Moving Large Files ................................................................................. 8 Browser‐based Filesharing: Education or Entertainment? ................................................................................... 9 Browser‐based Filesharing use Case: Productivity ..................................................................................................