Cluster Installation Guide in Crossgrid Lcfgng for Dummies
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Getting Started on a Mac with Macgamut Download
Getting started on a Macintosh computer with MacGAMUT 6 (Download) These step-by-step instructions will get you started on any Macintosh OS X computer, when you make a Download purchase of MacGAMUT 6 from the MacGAMUT website. Getting started with MacGAMUT 6 is EASY, but it's still a good idea to follow these printed instructions as you proceed step by step, marking off each step as you complete it. Follow these steps to install MacGAMUT 6 as a download: 1. First, download and install the MacGAMUT 6 software. Yes, you can complete the download and installation even before you make your online purchase. You just won’t be able to use the installed program until you’ve paid for it! a. From the Home page at www.macgamut.com, follow the links from the Installers link on the left-hand side of the screen to go to the MacGAMUT Web Installers page. b. Read the “How-to” Videos paragraph before scrolling down to click the appropriate installer for your computer and system. c. You’ll find the downloaded Installer in your Macintosh’s Downloads folder. (If you are not working on your own computer, you can copy the Installer to a flash drive so you can install it later on your computer.) d. The Installer will start automatically when you open the Installer package. Just follow the instructions to complete your installation. e. If you are installing MacGAMUT 6 for the first time, you will need to restart your computer after the installation process is finished. f. The program installs in a folder labeled MacGAMUT 6 in your computer’s Applications folder. -

Dropdmg 3.6.2 Manual
DropDMG 3.6.2 Manual C-Command Software c-command.com February 16, 2021 Contents 1 Introduction 4 1.1 Feature List..............................................4 2 Installing and Updating 6 2.1 Requirements.............................................6 2.2 Installing DropDMG.........................................7 2.3 Updating From a Previous Version.................................7 2.4 Reinstalling a Fresh Copy......................................8 2.5 Uninstalling DropDMG.......................................9 2.6 Security & Privacy Access......................................9 3 Using DropDMG 13 3.1 Basics................................................. 13 3.2 Making a Bootable Device Image of a Hard Drive......................... 14 3.3 Backing Up Your Files to CD/DVD................................ 16 3.4 Burning Backups of CDs/DVDs................................... 17 3.5 Restoring Files and Disks...................................... 18 3.6 Making Images With Background Pictures............................. 19 3.7 Protecting Your Files With Encryption............................... 20 3.8 Transferring Files Securely...................................... 21 3.9 Sharing Licenses and Layouts.................................... 21 3.10 Splitting a File or Folder Into Pieces................................ 22 3.11 Creating a DropDMG Quick Action................................ 22 4 Menus 23 4.1 The DropDMG Menu........................................ 23 4.1.1 About DropDMG...................................... 23 4.1.2 Software -

Mac OS X: an Introduction for Support Providers
Mac OS X: An Introduction for Support Providers Course Information Purpose of Course Mac OS X is the next-generation Macintosh operating system, utilizing a highly robust UNIX core with a brand new simplified user experience. It is the first successful attempt to provide a fully-functional graphical user experience in such an implementation without requiring the user to know or understand UNIX. This course is designed to provide a theoretical foundation for support providers seeking to provide user support for Mac OS X. It assumes the student has performed this role for Mac OS 9, and seeks to ground the student in Mac OS X using Mac OS 9 terms and concepts. Author: Robert Dorsett, manager, AppleCare Product Training & Readiness. Module Length: 2 hours Audience: Phone support, Apple Solutions Experts, Service Providers. Prerequisites: Experience supporting Mac OS 9 Course map: Operating Systems 101 Mac OS 9 and Cooperative Multitasking Mac OS X: Pre-emptive Multitasking and Protected Memory. Mac OS X: Symmetric Multiprocessing Components of Mac OS X The Layered Approach Darwin Core Services Graphics Services Application Environments Aqua Useful Mac OS X Jargon Bundles Frameworks Umbrella Frameworks Mac OS X Installation Initialization Options Installation Options Version 1.0 Copyright © 2001 by Apple Computer, Inc. All Rights Reserved. 1 Startup Keys Mac OS X Setup Assistant Mac OS 9 and Classic Standard Directory Names Quick Answers: Where do my __________ go? More Directory Names A Word on Paths Security UNIX and security Multiple user implementation Root Old Stuff in New Terms INITs in Mac OS X Fonts FKEYs Printing from Mac OS X Disk First Aid and Drive Setup Startup Items Mac OS 9 Control Panels and Functionality mapped to Mac OS X New Stuff to Check Out Review Questions Review Answers Further Reading Change history: 3/19/01: Removed comment about UFS volumes not being selectable by Startup Disk. -
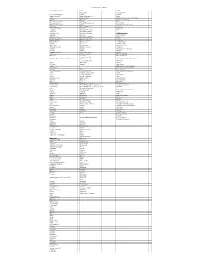
Software List (1-3-2017)
Software List (1-3-2017) Information Commons BU 104 LLCD Adobe Flash Academic online JVC Pro HD Manager Chrome Acrobat Adobe Reader DC Adobe Photoshop CS6 Adobe Itunes Adobe Reader XI Comprehensive Medical Terminology Maple 16 Drive M:\ Glencoe Keyboarding Microsoft Office 2016 Firefox Itunes Microsoft Publisher Irwin/GDP Keyboarding Kurzeil 3000 MS visual studio 2015 Itunes Microsoft Office Suite 2007 Quicktime Kurzweil 3000 v.12 Quick time SPSS for Windows Maple 16 Skills bank real player Microsoft Office 2016 Vista 3-Scanners MS platform installer Windows 7 & 10 Microsoft Visio 2016 Wellington Center sharepoint MS SQL Internet Explorer XPS viewer MS Visual Studio 2015 ITunes Express for desktop Quicken deluxe 2014 McAfee Express for Web VLC Media Player Quicktime MS silverlight Windows 10 " " Media Player Statdisk Scanner Mozilla Firefox Skype 2016 MS silverlight Adobe Reader XI windows dvd maker wolfram cdf player Windows 8 Onedrive Filezilla Microsoft Office Suite 2013 notepad++ Gimp 2 Maple 16 respounds/lockdown opera mobile emulator Statdisk 3D builder VM ware/ vsphere Wolfram CDF Player MS Azure wire shark VLC Media Player cisco packet tracker MACS Software (Information Commons) 3D builder Brunswick Front Desk Computers java development kit Windows 7 System project 2016 Adobe 9 Developer notepad++ Apple Itunes Utilities IBM Iseries access for windows Time Machine Intel Management and Security TextEdit UC 222 Iseries navigator System Preferences Acrobat Reader XI Malware Bytes Anti Malware Stickies Adult Clinical Simulation Mcaffe -

Introduction to Xgrid: Cluster Computing for Everyone
Introduction to Xgrid: Cluster Computing for Everyone Barbara J. Breen1, John F. Lindner2 1Department of Physics, University of Portland, Portland, Oregon 97203 2Department of Physics, The College of Wooster, Wooster, Ohio 44691 (First posted 4 January 2007; last revised 24 July 2007) Xgrid is the first distributed computing architecture built into a desktop operating system. It allows you to run a single job across multiple computers at once. All you need is at least one Macintosh computer running Mac OS X v10.4 or later. (Mac OS X Server is not required.) We provide explicit instructions and example code to get you started, including examples of how to distribute your computing jobs, even if your initial cluster consists of just two old laptops in your basement. 1. INTRODUCTION Apple’s Xgrid technology enables you to readily convert any ad hoc collection of Macintosh computers into a low-cost supercomputing cluster. Xgrid functionality is integrated into every copy of Mac OS X v10.4. For more information, visit http://www.apple.com/macosx/features/xgrid/. In this article, we show how to unlock this functionality. In Section 2, we guide you through setting up the cluster. In Section 3, we illustrate two simple ways to distribute jobs across the cluster: shell scripts and batch files. We don’t assume you know what shell scripts, batch files, or C/C++ programs are (although you will need to learn). Instead, we supply explicit, practical examples. 2. SETTING UP THE CLUSTER In a typical cluster of three or more computers (or processors), a client computer requests a job from the controller computer, which assigns an agent computer to perform it. -

How to Disable Gatekeeper and Allow Apps from Anywhere in Macos Sierra
How to Disable Gatekeeper and Allow Apps From Anywhere in macOS Sierra Gatekeeper, first introduced in OS X Mountain Lion, is a Mac security feature which prevents the user from launching potentially harmful applications. In macOS Sierra, however, Apple made some important changes to Gatekeeper that seemingly limit the choices of power users. But don’t worry, Gatekeeper can still be disabled in Sierra. Here’s how. Stand out at the party or promote your business with colorful powder coated and custom engraved Yeti tumblers from Perfect Etch. Traditionally, Gatekeeper offered three settings of increasing security: anywhere, App Store and identified developers, and App Store only. The first choice, as its name describes, allowed users to launch applications from any source, effectively disabling the Gatekeeper feature. The second choice allowed users to run apps from the Mac App Store as well as from software developers who have registered with Apple and securely sign their applications. Finally, the most secure setting limited users to running apps obtained from the Mac App Store only. While the secure options were good ideas for less experienced Mac users, power users found Gatekeeper to be too limiting and typically sought to disable it by setting it to “Anywhere.” In macOS Sierra, however, the “Anywhere” option is gone, leaving “App Store” and “App Store and identified developers” as the only two options. Disable Gatekeeper in macOS Sierra The Gatekeeper settings can be found in System Preferences > Security & Privacy > General. The Gatekeeper options are located beneath “All apps downloaded from:” with the choice of “Anywhere” missing. Thankfully, the “Anywhere” setting can be restored to Gatekeeper in Sierra with a Terminal command. -

The Apple Ecosystem
APPENDIX A The Apple Ecosystem There are a lot of applications used to manage Apple devices in one way or another. Additionally, here’s a list of tools, sorted alphabetically per category in order to remain vendor agnostic. Antivirus Solutions for scanning Macs for viruses and other malware. • AVG: Basic antivirus and spyware detection and remediation. • Avast: Centralized antivirus with a cloud console for tracking incidents and device status. • Avira: Antivirus and a browser extension. Avira Connect allows you to view device status online. • BitDefender: Antivirus and malware managed from a central console. • CarbonBlack: Antivirus and Application Control. • Cylance: Ransomware, advanced threats, fileless malware, and malicious documents in addition to standard antivirus. • Kaspersky: Antivirus with a centralized cloud dashboard to track device status. © Charles Edge and Rich Trouton 2020 707 C. Edge and R. Trouton, Apple Device Management, https://doi.org/10.1007/978-1-4842-5388-5 APPENDIX A THe AppLe ECOSYSteM • Malware Bytes: Antivirus and malware managed from a central console. • McAfee Endpoint Security: Antivirus and advanced threat management with a centralized server to track devices. • Sophos: Antivirus and malware managed from a central console. • Symantec Mobile Device Management: Antivirus and malware managed from a central console. • Trend Micro Endpoint Security: Application whitelisting, antivirus, and ransomware protection in a centralized console. • Wandera: Malicious hot-spot monitoring, jailbreak detection, web gateway for mobile threat detection that integrates with common MDM solutions. Automation Tools Scripty tools used to automate management on the Mac • AutoCasperNBI: Automates the creation of NetBoot Images (read: NBI’s) for use with Casper Imaging. • AutoDMG: Takes a macOS installer (10.10 or newer) and builds a system image suitable for deployment with Imagr, DeployStudio, LANrev, Jamf Pro, and other asr or Apple Systems Restore-based imaging tools. -

Download the Os X Mavericks Application from the Mac App Store
Download the os x mavericks application from the mac app store CLICK HERE TO DOWNLOAD Nov 01, · Open the App Store and search for “OS X Mavericks” or just click the direct App Store link (free, downloading one times or is always free) Click the “Download” button and confirm that you want to download the OS X Installer again by choosing “Continue”. Nov 07, · Connecting to the Mac App Store. The "Install OS X Mavericks" should be on the order of 5 or 6GB in size (I do not have the exact size at the moment, but GB is way too small). More Less. Question: Q: where can I download OS X Mavericks Update More Less. Apple Footer. May 28, · About Mac OS Mavericks Apple OS X Mavericks was first announced in June and was then released in October of It was the tenth big release of the Apple OS X line. At the same time, Mavericks was promoted and marketed as a major release just as was the case with the Lion and Mountain Lion OS X updates which came before the Mavericks. Oct 22, · Apple released OS X Mavericks today, Download Free from mac app store. plus new features compatible for macbook, mac mini, imac and macbook air models. OS X Mavericks -- the latest update to Apple's desktop OS -- noticeably improves the overall experience on for both new and older renuzap.podarokideal.ru:Free: Mac OS. Oct 23, · OS X Server requires Mavericks and is available from the Mac App Store for $ (US). Apple designs Macs, the best personal computers in the world, along with OS X, iLife, iWork and professional software. -

Simplified Macos Upgrade Workflow This Guide Walks You Through the Workflow Process for Deciding How to Upgrade Your Mac Fleet to Macos High Sierra Using Jamf Pro
Simplified macOS Upgrade Workflow This guide walks you through the workflow process for deciding how to upgrade your Mac fleet to macOS High Sierra using Jamf Pro. With the release of a new Apple operating system, it’s recommended to first check compatibility with existing software, test the stability of the OS, and make sure it meets the organization’s needs prior to upgrading. That’s why the first question you need to ask is—Do you want to upgrade now? NO Jamf Pro has the ability to block the install file for any macOS upgrade. If you want to wait on upgrading, simply create a policy that will block the macOS High Sierra installer app from running. YES Once you have decided to move forward with an upgrade you need to determine what to do with the existing data on your Macs. Are these shared Macs in a lab? Are they assigned to a specific user? The bottom line is— Do you want to keep the data intact? There are 4 methods to deploy the new macOS for your users with the data intact. In all KEEP DATA these options, using the Caching Service within macOS will help reduce network traffic. Consider using this service on your network. Macs enrolled via the Device Enrollment Program (DEP) and running 10.11.4 or later can be upgraded by sending a mobile device management (MDM) command to download and install macOS High Sierra. No user interaction or admin rights required for this option. Download the “Install macOS High Sierra” app from the Mac App Store. -

Basics of Apple Device Security
AN OVERVIEW FOR MAC, IPAD AND IPHONE Basics of Apple Device Security SMALL BUSINESS A well-planned cyberattack or an accidental download of 2 malware can mean the difference between a productive day and all work grinding to a halt. As hackers get more sophisticated, organizations concerned about their bottom line and security of their customer, employee or student data must stay on top of security. This guide is for anyone that has been tasked with Apple security concerns, like all IT security concerns, are real. managing Apple devices in your organization and wants to get serious about their organizational While Apple has invested a great deal in its security features security of their Apple devices, and offers basic and has rapidly become the leader in device and data privacy information for newcomers or a simple refresher for and security, no operating system is immune to security Apple management veterans. challenges. This means that administrators must not only respond quickly to security issues, but also proactively guard against them. 3 The basic building blocks Several factors work together to ensure the security of your organization’s hardware and data, and you can break them down into six main areas: Securing devices Apple native security Data encryption Keeping your physical devices Security systems already built-in The basics of encrypting data at Introduction secure and protecting those to macOS, iOS and iPadOS rest and data in transit using them to Apple Page 4 Page 7 Page 6 Security Compliance Secure monitoring Application -

Mac Os High Sierra App Store Background Download Question: Q: How to Download Full Installer of High Sierra
mac os high sierra app store background download Question: Q: How to Download full installer of High sierra. i have Purchased macbook pro mid 2014 13" today. it currently have Mac Os X Yosemite .I want to download Mac Os High Sierra . When ever i tried to download it from app store, it just download a 19.9MB file instead of 4.80GB. i have 4 MacBooks. i want to download full installer and then make a bootable USB from it to update my all 4 MacBooks. what should i do? how can i download full installer . MacBook Pro with Retina display, OS X Yosemite (10.10.5), Macbook Pro Mid 2014 13" Download the New macOS High Sierra 10.13 Wallpaper for your Mac. Apart from the amazing hardware announcements at WWDC 2017, Apple unveiled a new operating system for Mac called macOS High Sierra. The new operating system comes with many performance improvements under-the-hood and new features, such as the Apple File System, support for HVEC format, better user privacy in Safari, and much more. As is the case with every new iteration of macOS, a new wallpaper was also added to macOS 10.13 that looks beautiful. Below is a preview of the macOS High Sierra wallpaper. To download it, click on the link below it and save to your desktop. The first beta version of macOS can be downloaded by developers via the software update mechanism in the Mac App Store or through the Apple Developer Center. The public beta will be released by the end of June, while the official release will be made later this year as a free software update from the MacApp Store. -

Certified Data Cabling Installer (DCI) Competency Requirements
Certified Data Cabling Installer (DCI) Competency Requirements Data Cabling Installers (DCI) are expected to obtain knowledge of basic concepts of copper cabling installation and service, which are then applicable to all the functions required to safely and competently install communications cabling and low voltage premises cabling. Network cabling has many options now and is being used for many applications in addition to data. Copper cabling is also combined with other media applications to create these networks. Once a DCI has acquired these skills, abilities and knowledge and with minimal training, the DCI should be able to enter employment in the telecommunications cabling field. Data Cabling Installers must be knowledgeable and have abilities in the following technical areas: 1.0 SAFETY 1.1 Describe the various forms of personal protective equipment (PPE) that data cabling technicians have at their disposal 1.2 Explain the safety best practices associated with the work area 1.3 Provide an overview of emergency response information and techniques for the workplace that can be found in Material Safety Data Sheets (MSDS or SDS) described in the Hazard Communication Standard (HCS) (29 CFR 1910.1200(g)), revised in 2012, and detailed in Appendix D of 29 CFR 1910.1200 2.0 BASIC ELECTRICITY 2.1 Describe the relationships between voltage, current, resistance and power 2.2 Identify components called resistors and also non-component types of resistance in cabling technology 2.3 Use Ohm’s law to calculate power usage and power losses in cabling