Mobile Forensics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Jailbreak D'ios
Jailbreak d'iOS Débridage d'iOS Un outil similaire à Blackra1n, Limera1n, est par la suite développé et publié lors de la sortie de la version 4.1 Pour les articles homonymes, voir Jailbreak. d'iOS, malgré un problème présent dans la première ver- sion de cet outil. Le jailbreak d'iOS, également appelé débridage Des outils comme redsn0w, Pwnage Tool et Sn0wbreeze d'iOS, déverrouillage ou déplombage est un proces- ainsi que GreenPois0n, Absinthe (pour l'iPhone 4S et sus permettant aux appareils tournant sous le système l'iPad 2) permettent de jailbreaker les versions plus ré- d'exploitation mobile d'Apple iOS (tels que l'iPad, centes du terminal. l'iPhone, l'iPod touch, et plus récemment, l'Apple TV) d'obtenir un accès complet pour déverrouiller toutes les Depuis le 6 janvier 2013, il est possible de jailbreaker fonctionnalités du système d'exploitation, éliminant ain- les terminaux sous l'iOS 6, et ce jusqu'à la version 6.1.2, si les restrictions posées par Apple. Une fois iOS débri- par le biais d'un outil connu sous le nom d'Evasi0n. Cette dé, ses utilisateurs sont en mesure de télécharger d'autres méthode s’applique pour tous les terminaux supportant applications, des extensions ainsi que des thèmes qui ne IOS 6 mise à part l'Apple TV. Les versions 6.1.2 jus- sont pas proposés sur la boutique d'application officielle qu’à 6.1.6 ont été libéré en janvier 2014 grâce au logiciel d'Apple, l'App Store, via des installeurs comme Cydia. -

Blackhatonomics.Pdf
Blackhatonomics This page is intentionally left blank Blackhatonomics An Inside Look at the Economics of Cybercrime Will Gragido Daniel Molina John Pirc Nick Selby Andrew Hay, Technical Editor AMSTERDAM • BOSTON • HEIDELBERG • LONDON NEW YORK • OXFORD • PARIS • SAN DIEGO SAN FRANCISCO • SINGAPORE • SYDNEY • TOKYO Syngress is an Imprint of Elsevier Acquiring Editor: Steve Elliot Development Editor: Heather Scherer Project Manager: Malathi Samayan Designer: Mark Rogers Syngress is an imprint of Elsevier 225 Wyman Street, Waltham, MA 02451, USA Copyright © 2013 Elsevier, Inc. All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or any information storage and retrieval system, without permission in writing from the publisher. Details on how to seek permission, further information about the Pub- lisher’s permissions policies and our arrangements with organizations such as the Copyright Clearance Center and the Copyright Licensing Agency, can be found at our website: www.elsevier.com/permissions This book and the individual contributions contained in it are protected under copy- right by the Publisher (other than as may be noted herein). Notices Knowledge and best practice in this field are constantly changing. As new research and experience broaden our understanding, changes in research methods or professional practices, may become necessary. Practitioners and researchers must always rely on their own experience and knowledge in evaluating and using any information or methods described herein. In using such information or methods they should be mindful of their own safety and the safety of others, including parties for whom they have a profes- sional responsibility. -

Protección De Aplicaciones Móviles En Ios
Protección de Aplicaciones Móviles en iOS Trabajo Final de Máster Curso 2017-18 Máster Interuniversitario de Seguridad de las Tecnologías de la Información y de las Comunicaciones (MISTIC) Realizado por: Félix Garcia Lainez Consultor: Pau del Canto Rodrigo Profesor de la Asignatura: Victor García Font Fecha de Entrega: Junio de 2018 TFM - Protección de Aplicaciones Móviles en iOS ! Esta obra está sujeta a una licencia de Reconocimiento- NoComercial-SinObraDerivada 3.0 España de Creative Commons "2 TFM - Protección de Aplicaciones Móviles en iOS Ficha del Trabajo Final! Título del trabajo: Protección de Aplicaciones Móviles en iOS Nombre del autor: Félix Garcia Lainez Nombre del consultor/a: Pau del Canto Rodrigo Nombre del PRA: Victor García Font Fecha de entrega (mm/aaaa): 06/2018 Titulación:: MISTIC Área del Trabajo Final: Trabajo Final de Máster Idioma del trabajo: Castellano Palabras clave Seguridad, Aplicaciones Móviles, iOS "3 TFM - Protección de Aplicaciones Móviles en iOS Resumen! El objetivo de este trabajo ha sido la creación de una guía o manual de referencia para el desarrollo de aplicaciones móviles nativas seguras en iOS.! Para poner en contexto este trabajo, tal y como se describe en los capítulos 2.1 y 2.2 de esta memoria, la gran popularidad que han alcanzado las aplicaciones móviles en los últimos años ha propiciado la aparición de una gran cantidad de riesgos y amenazas asociadas a este tipo de tecnologías. ! Con el objetivo de mitigar y prevenir estos riesgos y amenazas, tal y como se recoge en el capítulo 2.3, el OWASP trató de estandarizar el desarrollo de este tipo de aplicaciones a través de la creación del MASVS [1]. -

Terminos Iphone
Ing. Jhonis Bermudez En el Mundo Iphone Terminos más Comunes en el Mundo IPhone • iPhone 2G o EDGE: Es el iPhone de primera generación que tiene una velocidad de conexion EDGE. • IPhone 3G: iPhone de segunda generación más delgado que el primero y con una velocidad de conexion 3G • IPhone 3GS: iPhone de tercera generación, a diferencia del 3G, posee mejor procesador, mas memoria y mejor cámara. • IPhone 4: iPhone de cuarta generación, rediseñado completamente y con mejoras en todos los sentidos. • iPad: Primera generación del Tablet de Apple • iPod touch 1G: Primera generación de iPod Touch. • iPod Touch 2G: Segunda generación del iPod Touch. • iPod Touch 3G: Tercera generación del iPod touch, más rápido que el 2G. • iDevice: Forma simple de referirse a los dispositivos iPhone iPod Touch e iPad. Terminos iPhone: • Acelerómetro: Dispositivo de forma nativa en el iPhone, iPod touch y iPad, que detecta cualquier movimiento e inclinación del iDevice. • App Store: La App Store es la tienda en línea creada por Apple para descargar aplicaciones para el iPhone, iPod Touch e IPAD. • Base Band: La BaseBand es un subsistema del iPhone que controla todas las funciones que requieren una antena, como ser el teléfono. Un desbloqueo se obtiene cambiando el subsistema. La banda se separa del sistema operativo, posee su propio procesador y su propio firmware. Articulo original: http://www.locuraiphone.net/wiki-locuraiphone/#ixzz1Sc0abRYF Ing. Jhonis Bermudez En el Mundo Iphone • Botón de Inicio: El botón Inicio se encuentra en la parte baja del iDevice, se usa por ejemplo, para cerrar una aplicación. • Botón de encendido: El botón de encendido se encuentra en la parte superior del iDevice, se usa, por ejemplo, para apagar el dispositivo. -

Managing Jailbreak Threats on Ios Enterprise Mobile Security WHITEPAPER
WHITEPAPER Managing Jailbreak Threats on iOS Enterprise Mobile Security WHITEPAPER I. Introduction Apple strongly discourages iOS users from jailbreaking their devices and for good reason: the practice can impair Jailbreakers can easily avoid detection key device functionality, such as OS upgrades, and can 3 also introduce significant security risks, such as the ability using free tools such as xCon or to download and execute unvetted and potentially FLEX4 that fool standard jailbreak malicious applications. detection tests. Nonetheless, many people ignore these risks and jailbreak their devices to unlock capabilities or content that Apple otherwise prohibits on iOS. A range of free tools and tutorials have made jailbreaking widely accessible, even to non-technical users. Consequently, an estimated 7.5% II. The Path to Jailbreaking of all iPhones, more than 30 million devices worldwide, are jailbroken. Jailbreaking is especially prevalent in China Motivation where an estimated 13% of all iPhones are jailbroken1. A wide variety of Apple-restricted iOS customisations and content might incentivise a user to jailbreak their device, Jailbreaking entails removing restrictions on iOS by such as: modifying system kernels to allow read and write access to the file system. This form of administrative privilege • Enabling app-multitasking with split-screen views escalation permits custom software installation and device • Locking individual apps with Touch ID behaviour modification. • Creating mobile wifi hotspots without paying While Apple diligently patches new jailbreak vulnerabilities, additional carrier charges it’s a constant game of Whack-A-Mole with the jailbreaking community racing to find new vulnerabilities whenever • Unlocking the phone to use the device internationally Apple releases iOS upgrades. -

Seven Deadliest USB Attacks.Pdf
Syngress is an imprint of Elsevier 30 Corporate Drive, Suite 400, Burlington, MA 01803, USA The Boulevard, Langford Lane, Kidlington, Oxford, OX5 1GB, UK Seven Deadliest USB Attacks © 2010, Elsevier, Inc. All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or any information storage and retrieval system, without permission in writing from the publisher. Details on how to seek permission, further information about the Publisher’s permissions policies and our arrangements with organizations such as the Copyright Clearance Center and the Copyright Licensing Agency, can be found at our website: www.elsevier.com/permissions. This book and the individual contributions contained in it are protected under copyright by the Publisher (other than as may be noted herein). Notices Knowledge and best practice in this field are constantly changing. As new research and experience broaden our understanding, changes in research methods, professional practices, or medical treatment may become necessary. Practitioners and researchers must always rely on their own experience and knowledge in evaluating and using any information, methods, compounds, or experiments described herein. In using such information or methods they should be mindful of their own safety and the safety of others, including parties for whom they have a professional responsibility. To the fullest extent of the law, neither the Publisher nor the authors, contributors, or editors, assume any liability for any injury and/or damage to persons or property as a matter of products liability, negligence or otherwise, or from any use or operation of any methods, products, instructions, or ideas contained in the material herein. -

Ebook Sobre Jailbreak Y Cydia
eBookJailbreak.es Autor: @DavidRandulfe eBook sobre Jailbreak y Cydia El eBook que estabas esperando para aprovechar el Jailbreak al máximo eBookJailbreak.es © - Todos los Derechos Reservados Esta prohibida la copia, modificación de textos y enlaces y la extracción de contenidos bajo ningún medio o sistema independientemente de su finalidad. © David Randulfe - Todos los Derechos Reservados Página 1! eBookJailbreak.es Autor: @DavidRandulfe Agradecimientos Quería antes de nada agradecer a la gente que ha colaborado conmigo en la creación de este eBook ya sea aportando cosas como dando ideas o sugiriendo secciones o tutoriales por lo que paso a citarlos a -Pablo Asekas (@PabloAsekas) continuación: -Antonio Durán (@matrix_i4) -Gonzalo Arilla (@gadc333) -Hugo (@iHache_Hugo) -Antonio Expósito (@Antonioexp) -José Antonio (@jar77jar) -Diego Rodriguez (@DiegoGaRoQui) -Luis Manuel Villanueva (@Lu1sma) Si has obtenido este eBook sobre el Jailbreak y Cydia de forma ilegal por favor dirígete a la página oficial http://ebookjailbreak.es y realiza la compra del eBook de forma oficial por tan solo 2,99€, ya que he puesto ese precio accesible a todos para evitar temas de pirateria y además ha llevado mucho trabajo su realización y escritura. © David Randulfe - Todos los Derechos Reservados Página 2! eBookJailbreak.es Autor: @DavidRandulfe 1. Sobre el eBook ....................................................................................................... Página 4 2. Historia del Jailbreak en iOS .................................................................................. -

A Framework for Digital Forensics in I-Devices: Jailed and Jail Broken Devices Iphone – a Fascinating Piece of Engineering Changed the Way of Telecommuters
1. Introduction A Framework for Digital Forensics in I-Devices: Jailed and Jail broken Devices iPhone – a fascinating piece of engineering changed the way of telecommuters. iPad is yet another revelation. The rising popularity these devices have N. Kala made it prevalent more and more in criminal cases. Scientific Officer, There is an increasing need to develop a framework Computer Forensics Division, since there are lots of challenges in performing Forensic Sciences Department examination on such devices. Huge volume of data Chennai – 4 and personal information are stored on these devices and its portability had made the dominance of Apple R. Thilagaraj mobile devices. Individuals store more data on Professor and Head idevices than on their systems or laptops. These Department of Criminology, activities make the iPhone take the place of personal University of Madras, computers (PCs) (Hoog, 2011) and digital cameras. Chepauk, Chennai – 600 005. In addition to the standard capabilities that exist in the iPhone, endless applications are also available for Abstract download to assist with finances or organization, or Prevalence and functionality of mobile devices are simply for entertainment. Recognizing these increasing. idevices such as smart phones, iphones advances and capabilities, it is conceivable that these and iPads are now being increasingly referred for devices could be used to commit or assist in criminal digital investigations, since these are being used by activities. Therefore they must be considered as terrorists, miscreants and contraband across borders viable sources of digital evidence and forensically and are also frequently used in prison despite being sound procedures should be available to support a prohibited. -
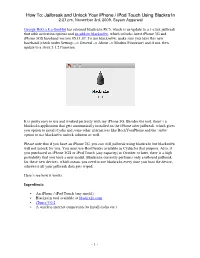
How To: Jailbreak and Unlock Your Iphone / Ipod Touch Using Blackra1n 2:27 Pm, November 3Rd, 2009, Sayam Aggarwal
How To: Jailbreak and Unlock Your iPhone / iPod Touch Using Blackra1n 2:27 pm, November 3rd, 2009, Sayam Aggarwal George Hotz a.k.a GeoHot has released blackra1n RC3, which is an update to a 1-click jailbreak that adds activation options and an add-on blacksn0w , which unlocks latest iPhone 3G and iPhone 3GS baseband version 05.11.07. To use blacksn0w, make sure you have this new baseband (check under Settings –> General –> About –> Modem Firmware) and if not, then update to a stock 3.1.2 firmware. It is pretty easy to use and worked perfectly with my iPhone 3G. Besides the tool, there’s a blackra1n application that gets automatically installed on the iPhone after jailbreak, which gives you option to install Cydia and some other alternatives like RockYourPhone and the ’sn0w’ option to use blacksn0w unlock solution as well. Please note that if you have an iPhone 2G, you can still jailbreak using blackra1n but blacksn0w will not unlock for you. You must use BootNeuter available in Cydia for that purpose. Also, if you purchased an iPhone 3GS or iPod Touch (any capacity) in October or later, there is a high probability that you have a new model. Blackra1n currently performs only a tethered jailbreak for these new devices, which means you need to use blackra1n every time you boot the device, otherwise all your jailbreak data gets wiped. Here’s see how it works. Ingredients: • An iPhone / iPod Touch (any model) • Blackra1n tool available at blackra1n.com • iTunes 9.0.2 • A wireless internet connection (to install cydia etc.) - 1 - How To: Jailbreak and Unlock Your iPhone / iPod Touch Using Blackra1n 2:27 pm, November 3rd, 2009, Sayam Aggarwal Now, let’s get started with the procedure : 1. -

Managing Jailbreak Threats on Ios Enterprise Mobile Security WHITE PAPER
WHITEPAPER Managing Jailbreak Threats on iOS Enterprise Mobile Security WHITE PAPER I. Introduction Apple strongly discourages iOS users from jailbreaking their devices and for good reason: the practice can impair Jailbreakers can easily avoid detection key device functionality, such as OS upgrades, and can also 3 introduce significant security risks, such as the using free tools such as xCon or ability to download and execute unvetted and potentially FLEX 4 that fool standard jailbreak malicious applications. detection tests. Nonetheless, many people ignore these risks and jailbreak their devices to unlock capabilities or content that Apple otherwise prohibits on iOS. A range of free tools and tutorials have made jailbreaking widely accessible, even to non-technical users. Consequently, an estimated 7.5% of all II. The Path to Jailbreaking iPhones, more than 30 million devices worldwide, are jailbroken. Jailbreaking is especially prevalent in China where Motivation an estimated 13% of all iPhones are jailbroken.1 A wide variety of Apple-restricted iOS customizations and content might incent a user to jailbreak their device, such as: Jailbreaking entails removing restrictions on iOS by modifying system kernels to allow read and write access to the file system. • Enabling app-multitasking with split-screen views This form of administrative privilege escalation permits custom • Locking individual apps with Touch ID software installation and device behavior modification. • Creating mobile wifi hotspots without paying While Apple diligently patches new jailbreak vulnerabilities, additional carrier charges it’s a constant game of Whac-A-Mole with the jailbreaking community racing to find new vulnerabilities whenever Apple • Unlocking the phone to use the device internationally or releases iOS upgrades. -

Perlindungan Hak Cipta Atas Adanya Metode Jailbreak Pada Aplikasi Ios Berbayar Dari Apple
PERLINDUNGAN HAK CIPTA ATAS ADANYA METODE JAILBREAK PADA APLIKASI IOS BERBAYAR DARI APPLE TESIS Oleh AMELIA ANGGRIANY SISWOYO 127011082 / M.Kn FAKULTAS HUKUM UNIVERSITAS SUMATERA UTARA MEDAN 2017 UNIVERSITAS SUMATERA UTARA PERLINDUNGAN HAK CIPTA ATAS ADANYA METODE JAILBREAK PADA APLIKASI IOS BERBAYAR DARI APPLE TESIS Diajukan Untuk Memperoleh Gelar Magister Kenotariatan Pada Program Studi Magister Kenotariatan Fakultas Hukum Universitas Sumatera Utara Oleh AMELIA ANGGRIANY SISWOYO 127011082 / M.Kn FAKULTAS HUKUM UNIVERSITAS SUMATERA UTARA MEDAN 2017 UNIVERSITAS SUMATERA UTARA UNIVERSITAS SUMATERA UTARA Telah diuji pada Tanggal : 28 November 2017 PANITIA PENGUJI TESIS Ketua : Dr. T. Kezerina Devi A, SH, CN, MHum Anggota : 1. Prof. Dr. Saidin, SH, MHum 2. Dr. Jelly Leviza, SH, MHum 3. Dr. Edy Ikhsan, SH, MHum 4. Dr. Rosnidar Sembiring, SH, MHum UNIVERSITAS SUMATERA UTARA SURAT PERNYATAAN Saya yang bertanda tangan dibawah ini : Nama : AMELIA ANGGRIANY SISWOYO Nim : 127011082 Program Studi : Magister Kenotariatan FH USU Judul Tesis : PERLINDUNGAN HAK CIPTA ATAS ADANYA METODE JAILBREAK PADA APLIKASI IOS BERBAYAR DARI APPLE Dengan ini menyatakan bahwa Tesis yang saya buat adalah asli karya saya sendiri bukan Plagiat, apabila dikemudian hari diketahui Tesis saya tersebut Plagiat karena kesalahan saya sendiri, maka saya bersedia diberi sanksi apapun oleh Program Studi Magister Kenotariatan FH USU dan saya tidak akan menuntut pihak manapun atas perbuatan saya tersebut. Demikianlah surat pernyataan ini saya buat dengan sebenarnya dan dalam keadaan sehat. Medan, Yang membuat Pernyataan Nama : AMELIA ANGGRIANY SISWOYO Nim : 127011082 UNIVERSITAS SUMATERA UTARA ABSTRAK Jailbreak adalah istilah yang umum digunakan bagi pengguna produk Apple yang bertujuan untuk membuka proteksi bawaan iDevice sehingga dapat memodifikasi sistem yang ada, karena dapat mengakses secara penuh maka pengguna dapat memasang aplikasi dari pihak ketiga yang tidak diverifikasi oleh Apple. -

DECLARATION of Ryan Bricker in Opposition to 103 Opposition
Sony Computer Entertainment America LLC v. Hotz et al Doc. 104 Att. 17 EXHIBIT Q DECLARATION OF RYAN BRICKER IN SUPPORT OF PLAINTIFF SONY COMPUTER ENTERTAINMENT AMERICA LLC’S OPPOSITION TO DEFENDANT GEORGE HOTZ’S MOTION TO DISMISS FOR LACK OF PERSONAL JURISDICTION AND IMPROPER VENUE Dockets.Justia.com geohot got sued: Legal Defense Fund Page 1 of 22 Report Abuse Next Blog» Create Blog Sign In GEOHOT GOT SUED SCEA VS HOTZ SATURDAY, FEBRUARY 19, 2011 ABOUT ME Legal Defense Fund GEORGE HOTZ I've done a little bit of hacking on Donations here are for legal defense ONLY the iPhone once. I checked with my lawyers before setting this up VIEW MY COMPLETE PROFILE See geohot.com (donations were big success, see this) PREVIOUS POSTS Found this while reading /b/ Wow, I'm impressed with the response, thanks so much! CFW bans Now I'm confident they won't win the win this war via attrition :-) SCEA has gone CRAZY I will discuss transparency of legal bills with my lawyers. Note to Sony POSTED BY GEORGE HOTZ AT 3:34 PM Townsend fights dirty In case you weren't one of the 1,000,000+ who's se... 306 COMMENTS: Three Facts 1 – 200 of 306 Newer› Newest» Mirko said... This is war... Yeah. I think this should be easy if everyone donated at least 1$. 100k people donating 1$ shouldnt be hard, and 1$ doesnt make you poor. It's just the number of people that donates that counts. Support this cause, why sue people who did nothing harmful to other people and let free people who kill, abuse childs, and stuff like that? FEBRUARY 19, 2011 3:45 PM Subscribe to hermann said..