Internet Explorer 6.0
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

TRABAJO DE DIPLOMA Título: Diseño De La Página Web De Antenas
FACULTAD DE INGENIERÍA ELÉCTRICA Departamento de Telecomunicaciones y Electrónica TRABAJO DE DIPLOMA Título: Diseño de la Página Web de Antenas Autor: Alaín Hidalgo Burgos Tutor: Dr. Roberto Jiménez Hernández Santa Clara 2006 “Año de la Revolución Energética en Cuba” Universidad Central “Marta Abreu” de Las Villas FACULTAD DE INGENIERÍA ELÉCTRICA Departamento de Telecomunicaciones y Electrónica TTRRAABBAAJJOO DDEE DDIIPPLLOOMMAA Diseño de la Página Web de Antenas Autor: Alaín Hidalgo Burgos e-mail: [email protected] Tutor: Dr. Roberto Jiménez Hernández Prof. Dpto. de Telecomunicaciones y electrónica Facultad de Ing. Eléctrica. UCLV. e-mail: [email protected] Santa Clara Curso 2005-2006 “Año de la Revolución Energética en Cuba” Hago constar que el presente trabajo de diploma fue realizado en la Universidad Central “Marta Abreu” de Las Villas como parte de la culminación de estudios de la especialidad de Ingeniería en Telecomunicaciones y Electrónica, autorizando a que el mismo sea utilizado por la Institución, para los fines que estime conveniente, tanto de forma parcial como total y que además no podrá ser presentado en eventos, ni publicados sin autorización de la Universidad. Firma del Autor Los abajo firmantes certificamos que el presente trabajo ha sido realizado según acuerdo de la dirección de nuestro centro y el mismo cumple con los requisitos que debe tener un trabajo de esta envergadura referido a la temática señalada. Firma del Tutor Firma del Jefe de Departamento donde se defiende el trabajo Firma del Responsable de Información Científico-Técnica PENSAMIENTO “El néctar de la victoria se bebe en la copa del sacrificio” DEDICATORIA Dedico este trabajo a mis padres, a mí hermana y a mi novia por ser las personas más hermosas que existen y a las cuales les debo todo. -

IE 6.0 Download and Set-Up Downloading Internet Explorer
IE 6.0 Download and Set-up To use the Web Commerce e-commerce service, you need to: • Gain access to the Internet • Install Microsoft™ Internet Explorer 6.0™ • Configure Temporary Internet files in Internet Explorer. • Configure AutoComplete in Internet Explorer. • Enable JavaScript in Internet Explorer. This tutorial provides detailed instructions to help you download and configure Internet Explorer 6.0 for use with Web Commerce application. Downloading Internet Explorer 6.0 Only Microsoft Internet Explorer 6 has the security features required to use the Web Commerce services. If you already have Internet access, you can use any Internet browser to download and install the most current version of IE, Internet Explorer 6. To download IE 6 from the Microsoft web site: 1. Go to the Microsoft Download Search page at: • http://www.microsoft.com/downloads/search.asp 1. Select the latest version of Internet Explorer (e.g.: Internet Explorer 6) from the Product Name drop-down list. 2. Select the operating system installed on your computer (e.g.: Windows 98) from the Operating System drop-down list. 3. Click the Find It! Button. A list of downloadable files appears. 4. Click Internet Explorer 6 from the list of files. A new browser window opens, which will allow you to specify which language version of IE you want to download. Exelon 2 5. Choose your preferred language and click the GO button. The next Windows File Download screen appears: 7. Click Internet Explorer 6 under the Download heading. A download box will open, select the Open Button, and the download for Internet Explorer 6 will commence. -
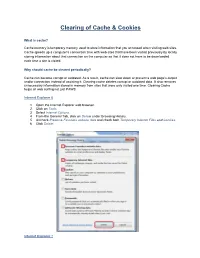
Clearing of Cache & Cookies
Clearing of Cache & Cookies What is cache? Cache memory is temporary memory used to store information that you accessed when visiting web sites. Cache speeds up a computer’s connection time with web sites that have been visited previously by locally storing information about that connection on the computer so that it does not have to be downloaded each time a site is visited. Why should cache be cleared periodically? Cache can become corrupt or outdated. As a result, cache can slow down or prevent a web page’s output and/or connection instead of assisting it. Clearing cache deletes corrupt or outdated data. It also removes unnecessary information stored in memory from sites that were only visited one time. Clearing Cache helps all web surfing not just PAWS. Internet Explorer 8 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Select Internet Options. 4. From the General Tab, click on Delete under Browsing History. 5. Uncheck Preserve Favorites website data and check both Temporary Internet Files and Cookies. 6. Click Delete. Internet Explorer 7 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Click on Internet Options. 4. Click on Delete under Browsing History. 5. Click Delete cookies. 6. When prompted, click Yes. 7. Click on Delete Internet Files. 8. When prompted, click Yes. 9. Click Close. 10. Click OK. 11. Close and reopen the browser for the changes to go into effect. Internet Explorer 6 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Click on Internet Options. 4. -

Browser Wars
Uppsala universitet Inst. för informationsvetenskap Browser Wars Kampen om webbläsarmarknaden Andreas Högström, Emil Pettersson Kurs: Examensarbete Nivå: C Termin: VT-10 Datum: 2010-06-07 Handledare: Anneli Edman "Anyone who slaps a 'this page is best viewed with Browser X' label on a Web page appears to be yearning for the bad old days, before the Web, when you had very little chance of read- ing a document written on another computer, another word processor, or another network" - Sir Timothy John Berners-Lee, grundare av World Wide Web Consortium, Technology Review juli 1996 Innehållsförteckning Abstract ...................................................................................................................................... 1 Sammanfattning ......................................................................................................................... 2 1 Inledning .................................................................................................................................. 3 1.1 Bakgrund .............................................................................................................................. 3 1.2 Syfte ..................................................................................................................................... 3 1.3 Frågeställningar .................................................................................................................... 3 1.4 Avgränsningar ..................................................................................................................... -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Spybot - Search & Destroy Can Detect and Remove Spyware of Different Kinds from Your Computer
Description Spybot - Search & Destroy can detect and remove spyware of different kinds from your computer. Spyware is a relatively new kind of threat that common anti-virus applications do not cover yet. If you see new toolbars in your Internet Explorer that you didn't intentionally install, if your browser crashes, or if you browser start page has changed without your knowing, you most probably have spyware. But even if you don't see anything, you may be infected, because more and more spyware is emerging that is silently tracking your surfing behaviour to create a marketing profile of you that will be sold to advertisement companies. Spybot-S&D; is free, so there's no harm in trying to see if something snooped into your computer, too :) Spybot-S&D; can also clean usage tracks, an interesting function if you share your computer with other users and don't want them to see what you worked on. And for professional users, it allows to fix some registry inconsistencies and offers some extended reporting features. License Spybot-S&D; comes under the Dedication Public License. Requirements Microsoft Windows 95, 98, ME, NT, 2000 or XP (32 and 64 bit), 2003, Vista. Compatible with bootable PE disks (e.g. BartPE) and Wine. Minimum of 10 MB free hard disk space, more recommended for updates and backups. Usage We recommend that you continue by reading the tutorial next. © 2000-2008 Safer Networking Ltd. All rights reserved. I. Freeware First of all, the reasons why Spybot-S&D; is free: I.a. Dedication Spybot-S&D; is dedicated to the most wonderful girl on earth :) I.b. -

Poradnik Nt. Migracji Na Wolne Oprogramowanie Na Serwerach I Desktopach
Poradnik nt. migracji na Wolne Oprogramowanie na serwerach i desktopach wersja 1.0 – lipiec 2003 r. OpenPoland.org 20 lipca 2004 1 Rzado˛ wy Urzad˛ Koordynacji i Doradztwa ds. Informatyzacji przy Ministerstwie Spraw We- wnetrzn˛ ych Republiki Federalnej Niemiec (KBSt) 2 Szanowni Panstw´ o! Niniejszy poradnik został przetłumaczony przez osoby wchodzace˛ w skład grupy OpenPoland.org. Pragniemy zaznaczyc,´ ze˙ nasza praca została wykonana nie na zlecenie, lecz za zgoda˛ BMI1. Jednoczesnie´ informujemy, ze˙ tekst niniejszego tłumaczenia udo- stepniamy˛ nieodpłatnie i nie wolno go sprzedawac´ w zadnej˙ postaci. Powyzsze˙ zasady zredagowane zostały w oparciu o uzgodnienia poczynione z BMI jeszcze przed rozpoczeciem˛ prac nad tłumaczeniem. Mamy nadzieje,˛ ze˙ rozwiazania˛ przedstawione w poradniku juz˙ niedługo zyskaja˛ wielu zwolenników, szczególnie wsród´ szerokiego grona osób odpowiedzialnych za funkcjonowanie infrastruktury informatycznej w naszym kraju. Zachecamy˛ Panstwa´ do współpracy nad rozwojem poradnika. Prosimy o zgłaszanie konstruktywnych, krytycznych uwag na adres: [email protected] . Na zakonczenie´ pragniemy podkresli´ c,´ ze˙ nie jestesmy´ organizacja˛ polityczna˛ i tym samym nie popieramy wykorzystywania naszej kampanii na rzecz Wolnego Opro- gramowania do współzawodnictwa politycznego. Zachecamy˛ do owocnej lektury! Grupa OpenPoland.org 1Niemiecki odpowiednik polskiego MSW. Spis tresci´ 1 Wprowadzenie 16 1.1 Geneza poradnika . 16 1.2 O poradniku . 17 1.3 Jak korzystac´ z poradnika? . 19 1.4 Wskazówki dla decydentów . 21 1.4.1 Podstawowe zalecenia . 21 1.4.2 Migracja kontynuacyjna i zastepuj˛ aca˛ . 22 1.4.3 Rózne˙ drogi migracji . 22 1.4.4 Porównanie alternatywnych rozwiaza˛ n´ . 23 1.4.5 Istotne zagadnienia przyszłoscio´ we . 24 1.4.6 Korzysci´ ekonomiczne . 26 2 Najwazniejsze˙ zagadnienia 28 2.1 Wazne˙ definicje . -

Webct Browser Tuneup 10.4.02
WebCT Browser Tune-up page 1 of 4 UMass Office of Informationoit Technologies WebCT Browser Tune-up 1. Supported Browsers: WebCT 3.8 2 2. Prepare Your Browser Settings for WebCT 2 • Use a Supported Browser 2 • If you use AOL... 2 • Enable Java 2 • Set Your Browser Cache to Always Reload a Page 3 • Turn off Anonymous Logon • Enable Cookies 3-4 3. How to Determine Browser and WebCT Versions 4 Academic Computing Office of Information Technologies Lederle Graduate Research Center University of Massachusetts Amherst Phone:(413) 577-0072 Fax: (413) 545-3203 http://www.umass.edu/acco/ OIT Academic Computing, Lederle Graduate Research Center, University of Massachusetts WebCT Browser Tune-up page 2 of 4 Supported Browsers: WebCT 3.8 If you need help determining your browser or WebCT version, read the instructions at the end of this document. • Netscape 4.76, 6.2.1, 6.2.2, and 6.2.3 (PC & Mac) • Internet Explorer 5.0 to 6.0, except 5.5 Service Pack 1 (PC) • Internet Explorer 5.0 and 5.1 (Mac OS 9.x) • Internet Explorer 5.1 (Mac OS 10.1) • AOL 7.0 (PC & Mac) Prepare Your Browser Settings for WebCT Review the following items to optimize your browser for WebCT: 1. Use a Supported Browser Make sure you are using a supported browser. Browers that are not listed are not supported. 2. If you use AOL... If you are using AOL 7.0 with WebCT 3.7 or higher, disregard this section. For best results with AOL: • Connect to the Internet using AOL version 4.0 or higher • Open a private chat within • AOL, which allows the AOL client to remain open without asking if you wish to disconnect while minimized • Minimize AOL • Launch a supported browser 3. -

Internet Explorer Users Are Required to Add the Portal URL to Trusted Sites
CLA Client Portal Browser and Silverlight FAQs 1. Question: I am receiving an “Error 500” when clicking the link to access the CLA Document Portal. Resolution: Verify with your IT department that the portal is not blocked by any internal monitoring or protection applications. 2. Question: How do I know if my computer has Microsoft Silverlight Installed? Resolution: The first time you try and login to the portal you will be prompted to install Silverlight from Microsoft’s website if you don’t have it already installed. The installation typically takes less than one minute and is completely safe. http://www.microsoft.com/getsilverlight/Get-Started/Install/Default.aspx If you cannot, or prefer not to, install Silverlight on your machine, a simplified version of the document portal that does not require Silverlight is available. Click on the Take me to the non- Silverlight login on the CLA Document Portal page (www.claconnect.com/docportal). 3. Question: I cannot access the CLA Document Portal. (Server error/Page not found) Resolution: Check that you are using a Microsoft Silverlight 4 compatible browser on all PC’s or MAC. A complete list of browsers and operating systems that support Silverlight 4 can be found at http://www.microsoft.com/getsilverlight/locale/en-us/html/installation-win-SL4.html Please note: Internet Explorer users are required to add the portal URL to Trusted Sites. Adding to Trusted Sites Internet Explorer settings 1. Open Internet Explorer and browse to https://portal.cchaxcess.com/Portal/. 2. In Internet Explorer, select Tools / Internet Options; then select the Security tab and click Trusted Sites and then Sites. -

U.S. V. Microsoft Corporation : Government Exhibit
l'roubteshooter: Solving problems lnsmlhng vr umnstalilng i.,;,c:mt::L tx.piorer ➔ .U Page I ot 2 ,. MICJ,OSOfl NlOfHJf T$ Sf t.llCH tfllBIII 'IIOP WAITf US Micros<Jlt· ,.__.....__,._,._.., _____.) Solving problems Installing or Uninstalling Internet Expl_ore~ 4~0 Can you uninstall Internet Explorer 4.0 using the Add/Remove Program! Control Panel? Note • You must have administrative privileges to install and uninstall this program in Windows NT. This inclu< administrative privileges the first time you start your computer after installing or uninstalling. To uninstall Internet Explorer 4.0 In Windows 95 and Windows NT 4.0 1. Click Start, point to Settings, click Control Panel, and then double-click Add/Remove Programs. 2. Click the Inatall/Uninstall tab. 3. In the 11st of Installed programs, click Microsoft Internet Explorer 4.0, and then click Add/Remove 4. In the Add/Remove Internet Explorer 4.0 dialog box, click Remove Internet Explorer 4,0 and t components selected below and click to select all the additional components you want to remove. v have selected all the components you want to remove, click OK. 5. When Setup starts, click Remove All. If you have any files in the Recycle Bin, you receive the following warning: Internet Explorer 4.0 has modified the format of the Recycle Bin. If you want to keep any of the items currently in the Recycle Bin, open the Recyc move the items to a different location. To permanently delete all items from the Recycle Bin and continue, click OK. 6. -

Ÿþh Y P E R I O N I N S T a L L a T I O N S T a R T H E R E R E L E a S E 9 . 3
Hyperion Installation Start Here RELEASE 9.3.3 Updated: June 2011 Hyperion Installation Start Here, 9.3.3 Copyright © 2007, 2011, Oracle and/or its affiliates. All rights reserved. Authors: EPM Information Development Team Oracle and Java are registered trademarks of Oracle and/or its affiliates. Other names may be trademarks of their respective owners This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS: Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms set forth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). -

Working with Html, Css, and Http
Chapter 2 WORKING WITH HTML, CSS, AND HTTP Working with HTML An essential aspect of running a website is creating HTML files. Even sites that rely heavily on page technologies other than static HTML, such as script-driven pages, inevitably keep many static HTML files on the site. Although Web authors can write HTML in any text editor, many have adopted specialized HTML editor programs to handle the job. Ideally, an HTML editor should manage the job of converting an authors writing into the structures defined by the HTML standard without requiring the author to know the details of that standard. As the job is accomplished, the editor program may carry out additional tasks, such as letting the author fine-tune the finished documents appearance or handling site management tasks such as uploading documents to a server and checking its links. The most widely used HTML editors handle these secondary tasks with great success. Over the years, however, many designers created their actual HTML code with an emphasis on appearance rather than structure. This so-called presentational markup achieved popularity with an older generation of browsers because no widely supported alternative to controlling an HTML documents appearance was available. Presentational HTML has drawbacks, though, and a growing number of Web authors are abandoning it in favor of HTML markup that describes a documents structure. Reasons for this choice include: Library Technology Reports Many aspects of presentational markup make assumptions about the users display environment (specifically, screen resolution and window width) that are increasingly unwarranted and may lead to accessibility problems.