On the Pitfalls of End-To-End Encrypted Communications: a Study of Remote Key-Fingerprint Verification
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cisco SCA BB Protocol Reference Guide
Cisco Service Control Application for Broadband Protocol Reference Guide Protocol Pack #60 August 02, 2018 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

Encryption Procedure
Encrypting Software for Transmission to NIST 1. Scope NIST requires that all software submitted by the participants be signed and encrypted. Signing is done with the participant’s private key, and encrypting is done with the NIST project public key, which is published at http://www.nist.gov/itl/iad/ig/encrypt.cfm. NIST will validate all submitted materials using the participant’s public key, and the authenticity of that key will be verified using the key fingerprint. This fingerprint must be submitted to NIST as part of the signed participant agreement. By encrypting the submissions, we ensure privacy; by signing the submission, we ensure authenticity (the software actually belongs to the submitter). NIST will not take ownership of any submissions that are not signed and encrypted. All cryptographic operations (signing and encrypting) shall be performed with software that implements the OpenPGP standard, as described in Internet RFC 4880. The freely available Gnu Privacy Guard (GPG) software, available at www.gnupg.org, is one such implementation. 2. Submission of software to NIST NIST requires that all software submitted by the participants be signed and encrypted. Two keys pairs are needed: • Signing is done with the software provider's private key, and • Encryption is done with the NIST project public key, which is available at http://www.nist.gov/itl/iad/ig/encrypt.cfm 2.1. Project Specific Parameters The values for the project specific parameters (ProjectName, ProjectPublicKey, and ProjectEmail) mentioned in this document are found at http://www.nist.gov/itl/iad/ig/encrypt.cfm 1 2.2. Creating participant cryptographic key pair The steps below show how to create a public/private key pair and fingerprint using the GPG software. -

Security System for Mobile Messaging Applications Pejman Dashtinejad
Security System for Mobile Messaging Applications Pejman Dashtinejad Master of Science Thesis Stockholm, Sweden TRITA–ICT–EX-2015:2 Introduction | 1 Security System for Mobile Messaging Applications Pejman Dashtinejad 8 January 2015 Master of Science Thesis Examiner Professor Sead Muftic Department of ICT KTH University SE-100 44 Stockholm, Sweden TRITA–ICT–EX-2015:2 Abstract | iii Abstract Instant messaging (IM) applications are one of the most popular applications for smartphones. The IMs have the capability of sending messages or initiating voice calls via Internet which makes it almost cost free for the users to communicate with each other. Unfortunately, like any other type of applications, majority of these applications are vulnerable to malicious attacks and have privacy issues. The motivation for this thesis is the need to identifying security services of an IM application and to design a secure system for any mobile messaging application. This research proposes an E2EE (End-to-End Encryption) approach which provides a secure IM application design which protects its users with better integrity, confidentiality and privacy. To achieve this goal a research is conducted to investigate current security features of popular messaging applications in the mobile market. A list of requirements for good security is generated and based on those requirements an architecture is designed. A demo is also implemented and evaluated. Keywords: Mobile, Application, messaging, Chat, Encryption, Security Acknowledgments | v Acknowledgments First and foremost, thank you God to give me another chance to complete my higher education and to learn enormous skills and knowledge through all these years of study at the university. -

Enterprise Edition
Secure Communication. Simplified. SAFECHATS Problem Most companies use popular insecure email and ⛔ messaging services to communicate confidential information P The information flow within the Company is ⛔ disorganized Metadata is exposed and available to third-party ⛔ services SAFECHATS Introducing SAFECHATS Ultra-secure communication solution P Designed with security in mind SAFECHATS Why SAFECHATS? ✔ Information is always end-to-end encrypted by default P ✔ All-in-one communication suite: • Text messaging (one-on-one and group chats) • Voice calls • File transfers (no size and file type limits) SAFECHATS How does SAFECHATS solve the problem? ✔ Customizable white label solution ✔ Integrates with existing softwareP infrastructure ✔ Enterprise-wide account and contact list management, supervised audited chats for compliance SAFECHATS What makes SAFECHATS different? ✔ Your own isolated cloud environment or on-premise deployment P ✔ Customizable solution allows to be compliant with internal corporate security policies ✔ No access to your phone number and contact list SAFECHATS Screenshot Protection ✔ Notifications on iOS P ✔ DRM protection on Android SAFECHATS Identity Verification ✔ Protection from man-in-the-middle attacksP ✔ SMP Protocol SAFECHATS Privacy Features ✔ Show / hide messages and files P ✔ Recall messages and files ✔ Self-destructing messages and files SAFECHATS Additional Protection ✔ History retention control P ✔ Application lock: • PIN-code • Pattern-lock on Android devices • Touch ID on iOS devices SAFECHATS How does SAFECHATS -

Group Messaging for Secure Asynchronous Collaboration
Group Messaging for Secure Asynchronous Collaboration Matthew A. Weidner Churchill College A dissertation submitted to the University of Cambridge in partial fulfilment of the requirements for the degree of Master of Philosophy in Advanced Computer Science University of Cambridge Computer Laboratory William Gates Building 15 JJ Thomson Avenue Cambridge CB3 0FD United Kingdom Email: [email protected] June 6, 2019 Declaration of originality I, Matthew A. Weidner of Churchill College, being a candidate for the M.Phil in Advanced Computer Science, hereby declare that this report and the work described in it are my own work, unaided except as may be specified below, and that the report does not contain material that has already been used to any substantial extent for a comparable purpose. The word count excludes appendices. Signed: Date: This dissertation is copyright c 2019 Matthew A. Weidner. All trademarks used in this dissertation are hereby acknowledged. Acknowledgements I would like to thank my supervisors, Dr. Alastair Beresford and Dr. Martin Kleppmann, for their time and valuable input on this project throughout the year, including feedback on multiple drafts of this dissertation. I also thank Michael Dodson for providing feedback on a draft of Chapter 4. I was supported by a Churchill Scholarship from the Winston Churchill Foundation of the USA. Group Messaging for Secure Asynchronous Collaboration Abstract End-to-end encrypted applications improve users' privacy by making their data unread- able to anyone besides their intended recipients. In particular, their data is unreadable to application servers. Although end-to-end encryption is currently deployed only for messaging apps, recent academic work shows that it is possible to create end-to-end en- crypted asynchronous collaborative applications, like Google Docs but without a trusted server, by layering Conflict-free Replicated Data Types (CRDTs) on top of a secure group messaging protocol. -

Policy Options and Regulatory Mechanisms for Managing Radicalization on the Internet
Policy options and regulatory mechanisms for managing radicalization on the Internet Paris, 30 September 2016 “[…] I firmly believe that in a free democratic society, freedom of speech and expression is one of the most prized freedoms which must be defended and upheld at any cost and this should be particularly so in the land of Voltaire. It is indeed unfortunate that in the world of today, when science and technology have advanced the frontiers of knowledge and mankind is beginning to realize that human happiness can be realized only through inter-dependence and cooperation, the threshold of tolerance should be going down. It is high time man should realize his spiritual dimension and replace bitterness and hatred by love and compassion, tolerance and forgiveness.” Justice Prafullachandra Bhagwati Dan Shefet (Individual Specialist) ACKNOWLEDGEMENTS The author wishes to thank the following for their support, valuable advice and input throughout the drafting of the Report: Dr. Indrajit Banerjee and his team in UNESCO’s Knowledge Societies Division The UNESCO Delegates and Ministries of Justice/Interior of countries that have participated in the Country Survey. Alexander Linden, Honorary advisor to the French Supreme Court Janice Duffy, Researcher, Australia Pavan Duggal, Supreme Court Lawyer, India Tom Høyem, Former Minister in Denmark under Poul Schlüter Francesca Musiani, Researcher at the CNRS Institute for Communication Sciences and Member of the French National Assembly’s Commission on the Law and Rights in the Digital Era Sami Mahbouli, Lawyer at The Tunisian Supreme Court and Columnist Sabine Leutheusser-Schnarrenberger, Former Minister of Justice under Angela Merkel Marc Randazza, First Amendment Attorney, United States Viswa Sadasivan, CEO of Strategic Moves (Consultancy agency in Singapore) and former member of the Singaporean Parliament Mr K. -

Adding Public Key Security to SSH
Adding Public Key Security to SSH A Thesis Submitted to the Faculty in partial fulfillment of the requirements for the degree of Master of Science in Computer Science by Yasir Ali DARTMOUTH COLLEGE Hanover, New Hampshire Feb, 20th, 2003 Examining Committee: ____________________________ Sean Smith (chair) ____________________________ Edward Feustel ____________________________ Christopher Hawblitzel !!!!!!!!!____________________________ !!!!!!!!!Carol Folt !!!!!!!!! Dean of Graduate Studies 1 2 Abstract SSH, the Secure Shell, is a popular software-based approach to network security. It is a protocol that allows user to log into another computer over a network, to execute commands in a remote machine, and to move files from one machine to another. It provides authentication and encrypted communications over unsecured channels. However, SSH protocol has an inherent security flaw. It is vulnerable to the “man-in-the- middle Attack”, when a user establishes his first SSH connection from a particular client to a remote machine. My thesis entails designing, evaluating and prototyping a public key infrastructure which can be used with the SSH2 protocol, in an academic setting, thus eliminating this vulnerability due to the man in the middle attack. The approach presented is different from the one that is based on the deployment of a Certificate Authority. My scheme does not necessarily require third party verification using a Certificate Authority; it is decentralized in nature and is relatively easy to set up. Keywords used: SSH, PKI, digital certificates, Certificate Authority, certification path, LDAP servers, Certificate Revocation List, X509v3 Certificate, OpenSSL, mutual authentication, and tunneled authentication. 3 Acknowledgments I want to thank Professor Sean Smith for his guidance, assistance and unremitting support over the last two years. -

PGP Command Line User Guide
PGP Command Line User Guide Last updated: July 2020 Copyright statement Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. Copyright © 2020 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com. Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function, or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein, neither does it convey any license under its patent rights nor the rights of others. Contents About PGP Command Line 1 Important Concepts 1 Technical Support 2 Installing 5 Install Location 5 Installing on AIX 6 Installing on AIX 6 Changing the Home Directory on AIX 7 Uninstalling on AIX 7 Installing on HP-UX 8 Installing on HP-UX 8 Changing the Home Directory on HP-UX 9 Installing to a Non-Default Directory on HP-UX 9 Uninstalling on HP-UX 9 Installing on macOS 10 Installing on macOS 10 Changing the Home Directory on macOS 10 Uninstalling on macOS 11 Installing on Red Hat Enterprise Linux, SLES, or Fedora Core 11 Installing on Red Hat Enterprise Linux or Fedora Core 11 Changing the Home Directory on Linux or Fedora Core 12 Uninstalling on Linux or Fedora Core 12 Installing on Oracle Solaris 13 Installing on Oracle -
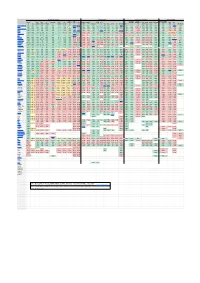
Digital Communications Protocols
Security & Privacy Compatibility Features & Usability Sustainability E2E E2E Offline Local Decentralized Active Open Open On Anonymous E2E E2E Default Audit FIDO1 Desktop Mobile Apple AOSP Messages messaging File Audio Video Phoneless or Federated Open IETF [1] TLS Client Server Premise [2] Private Group [3] [4] / U2F Web Web Android iOS [5] Win macOS Linux *BSD Terminal MDM [6] [7] [8] Share Call Call [9] [10] Spec [11] Introduced Element/Matrix TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE PARTIAL TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE 2014 XMPP TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE PARTIAL [12]TRUE FALSE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE [13] TRUE TRUE TRUE TRUE TRUE TRUE TRUE 1999 NextCloud Talk TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE TRUE FALSE TRUE TRUE TRUE TRUE TRUE FALSE FALSE 2018 Wire TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE FALSE TRUE TRUE FALSE TRUE TRUE TRUE TRUE PARTIAL TRUE TRUE FALSE TRUE TRUE TRUE TRUE FALSE FALSE FALSE 2014 Jami TRUE TRUE TRUE N/A [14] N/A TRUE TRUE FALSE [15] TRUE FALSE N/A [16] FALSE FALSE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE FALSE FALSE TRUE TRUE TRUE TRUE TRUE PARTIAL PARTIAL[17] [18] 2016 Briar [19] TRUE TRUE TRUE N/A [20] N/A TRUE TRUE TRUE TRUE TRUE N/A [21] FALSE FALSE TRUE FALSE TRUE FALSE FALSE FALSE FALSE FALSE FALSE TRUE TRUE FALSE FALSE FALSE FALSE TRUE FALSE FALSE 2016 Tox TRUE TRUE TRUE -

How Secure Is Textsecure?
How Secure is TextSecure? Tilman Frosch∗y, Christian Mainkay, Christoph Badery, Florian Bergsmay,Jorg¨ Schwenky, Thorsten Holzy ∗G DATA Advanced Analytics GmbH firstname.lastname @gdata.de f g yHorst Gortz¨ Institute for IT-Security Ruhr University Bochum firstname.lastname @rub.de f g Abstract—Instant Messaging has gained popularity by users without providing any kind of authentication. Today, many for both private and business communication as low-cost clients implement only client-to-server encryption via TLS, short message replacement on mobile devices. However, until although security mechanisms like Off the Record (OTR) recently, most mobile messaging apps did not protect confi- communication [3] or SCIMP [4] providing end-to-end con- dentiality or integrity of the messages. fidentiality and integrity are available. Press releases about mass surveillance performed by intelli- With the advent of smartphones, low-cost short-message gence services such as NSA and GCHQ motivated many people alternatives that use the data channel to communicate, to use alternative messaging solutions to preserve the security gained popularity. However, in the context of mobile ap- and privacy of their communication on the Internet. Initially plications, the assumption of classical instant messaging, fueled by Facebook’s acquisition of the hugely popular mobile for instance, that both parties are online at the time the messaging app WHATSAPP, alternatives claiming to provide conversation takes place, is no longer necessarily valid. secure communication experienced a significant increase of new Instead, the mobile context requires solutions that allow for users. asynchronous communication, where a party may be offline A messaging app that claims to provide secure instant for a prolonged time. -

Detecting and Preventing Active Attacks Against Autocrypt Release 0.10.0
Detecting and preventing active attacks against Autocrypt Release 0.10.0 NEXTLEAP researchers Jan 09, 2020 Contents 1 Introduction2 1.1 Attack model and terminology............................2 1.2 Problems of current key-verification techniques...................3 1.3 Integrating key verification with general workflows.................3 1.4 Supplementary key consistency through ClaimChains................4 1.5 Detecting inconsistencies through Gossip and DKIM................5 2 Securing communications against network adversaries6 2.1 Setup Contact protocol................................7 2.2 Verified Group protocol................................ 12 2.3 History-verification protocol............................. 17 2.4 Verifying keys through onion-queries......................... 20 3 Key consistency with ClaimChains 23 3.1 High level overview of the ClaimChain design.................... 23 3.2 Use and architecture................................. 24 3.3 Evaluating ClaimChains to guide verification.................... 26 4 Using Autocrypt key gossip to guide key verification 28 4.1 Attack Scenarios................................... 28 4.2 Probability of detecting an attack through out of band verification......... 29 5 Using DKIM signature checks to guide key verification 32 5.1 DKIM Signatures on Autocrypt Headers....................... 32 5.2 Device loss and MITM attacks............................ 33 5.3 Open Questions.................................... 34 1 1 Introduction This document considers how to secure Autocrypt1-capable mail apps against active network at- tackers. Autocrypt aims to achieve convenient end-to-end encryption of e-mail. The Level 1 Autocrypt specification offers users opt-in e-mail encryption, but only considers passive adver- saries. Active network adversaries, who could, for example, tamper with the Autocrypt header during e-mail message transport, are not considered in the Level 1 specification. Yet, such active attackers might undermine the security of Autocrypt. -

Security & Privacy for Mobile Phones
Security & Privacy FOR Mobile Phones Carybé, Lucas Helfstein July 4, 2017 Instituto DE Matemática E Estatística - USP What IS security? • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; • That TRIES TO KEEP THE ABOVE PROMISES forever. Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; 1 • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; • That TRIES TO KEEP THE ABOVE PROMISES forever. Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; 1 • That TRIES TO KEEP THE ABOVE PROMISES forever. Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; 1 Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; • That TRIES TO KEEP THE ABOVE PROMISES forever. 1 Security IS ... A System! Eve | | | Alice "Hi" <---------------> "Hi" Bob 2 Security IS ... Cryptography! Eve | | | Alice "Hi" <----"*****"------> "Hi" Bob 3 Security IS ... Impossible! The ONLY TRULY SECURE SYSTEM IS ONE THAT IS POWERED off, CAST IN A BLOCK OF CONCRETE AND SEALED IN A lead-lined ROOM WITH ARMED GUARDS - AND EVEN THEN I HAVE MY doubts.