Logic Programming and Theorem Proving
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Youth Entertainment in Croatia: Behind the Scenes of Summer Music Festivals“ Master's Thesis Page - 1 - „ Content 1
Faculty of Humanites and Social Sciences Zagreb Ivana Lučića 3, 10 000 Zagreb, Croatia Department of Anthropology and Department of Pedagogy Mentors: doc.dr.sc.Caroline Hornstein Tomić and prof.dr.sc.Vedrana Spajić-Vrkaš Youth entertainment in Croatia: Behind the scenes of summer music festivals (Master’s thesis) Tia Šimanović Zagreb, July 21, 2015 To my mom, who is always there for me and my sisters. Who always knows how to give us just the right amount of support and help, not to make us feel impotent and incapable; who showers us with love and tenderness in just a right amount not to make us spoiled; who knows when to get angry at us and make us regret for what we have or have not done; who can perfectly balance when to push us a little if we start to fall apart and when to leave us on our own, to make us learn to cope with situations this life has prepared for us. To my mom, who is always somewhere near us, but leaves us alone to learn from our mistakes on our own; who lets us fall but always picks us up; who supports us endlessly and makes us feel as we can conquer the world if we just try hard enough; who makes us feel indestructible. For you mom, who instilled in us feelings of pride, ability, and self-respect; who gives us the power to act. You let us lead our own battles, but in times of trouble and darkness you are there to guide us and hold our hands and we always know you are here for us to turn to. -

M a R Y T Yler W H O R
I s s u e 1 J u l y 2 0 0 2 FREE! THE __ M a r y T y ler W h o r e s PLUS BAD RELIGION, RECORD REVIEWS, STUPID RANTS AND MORE! Why this is the most use the word mainstream, im portant thing you own: since punk is supposed to be an "underground" subculture, 1) I t 's fre e . but in essence, bands on Fat, 2) I wrote it. Epitaph, Lookout, Hopeless, 3) It'll be a collectible in BYO, Alternative Tentacles, 50 years. etc. are easily accessible and 4) Alright, it's really not people know who they are. So that great. as far as punk is concerned, they're in the mainstream. Anyway, here's something for Now, there are just not you wastoids to read when you enough bands playing and not have lost all hope for anything enough people coming out to exciting to ever happen in see those who do. It starts your life. It's also good to with you. That’s right. Get read while you're taking a off your lazy ass and start a shit, and it comes extra band - right now! And I don't handy when you've run out of mean any of that Blink or TP. Here's the deal. The New Found Glory pop/emo crippling south Florida Punk trash. What we need are Rock scene is in dire need of aggressive, powerful bands support. It needs a little that have something to say. boost. There are plenty of Tavern is cool enough to allow punks down here, but the you mongrels a chance to play scene is fucking deader than and hang out every Sunday dead. -

Ontology Design and Management for Ecare Services
Ontwerp en beheer van ontologieën voor elektronische zorgdiensten Ontology Design and Management for eCare Services Femke Ongenae Promotoren: prof. dr. ir. F. De Turck, prof. dr. ir. T. Dhaene Proefschrift ingediend tot het behalen van de graad van Doctor in de Ingenieurswetenschappen: Computerwetenschappen Vakgroep Informatietechnologie Voorzitter: prof. dr. ir. D. De Zutter Faculteit Ingenieurswetenschappen en Architectuur Academiejaar 2012 - 2013 ISBN 978-90-8578-621-4 NUR 984, 981 Wettelijk depot: D/2013/10.500/54 Universiteit Gent Faculteit Ingenieurswetenschappen en Architectuur Vakgroep Informatietechnologie Promotoren: prof. dr. ir. Filip De Turck prof. dr. ir. Tom Dhaene Universiteit Gent Faculteit Ingenieurswetenschappen en Architectuur Vakgroep Informatietechnologie Gaston Crommenlaan 8 bus 201, B-9050 Gent, Belgie¨ Tel.: +32-9-331.49.00 Fax.: +32-9-331.48.99 Dit werk kwam tot stand in het kader van een specialisatiebeurs van het IWT-Vlaanderen (Instituut voor de aanmoediging van Innovatie door Wetenschap en Technologie in Vlaanderen). Proefschrift tot het behalen van de graad van Doctor in de Ingenieurswetenschappen: Computerwetenschappen Academiejaar 2012-2013 Dankwoord Ik zie mezelf nog zitten in Auditorium A van de S9 tijdens de eerste les van het vak Computertechnologie, me luidop afvragend wat die CPU toch was waarover Prof. Hoffman het steeds had. Toen had ik nooit durven dromen dat ik hier vandaag zou staan. In die periode van 10 jaar, heb ik heel wat bijgeleerd, niet enkel op vlak van computerwetenschappen, maar ook op persoonlijk vlak. Zo heeft mijn doctoraat me duidelijk de meerwaarde van interdisciplinair en participatief onderzoek doen inzien. Vanaf die eerste dag heb ik steeds mensen gehad bij wie ik terecht kon voor steun, vragen, een levendige discussie, een aangename babbel, een wijze levensles of gewoon een leuk verzetje. -

Queer Youth and the Importance of Punk Rock
QUEERING PUNK: QUEER YOUTH AND THE IMPORTANCE OF PUNK ROCK DENISE SCOTT A THESIS SUBMITTED TO THE FACULTY OF GRADUATE STUDIES IN PARTIAL FULFILMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF ARTS GRADUATE PROGRAM IN INTERDISCIPLINARY STUDIES YORK UNIVERSITY TORONTO, ONTARIO DECEMBER 2011 Library and Archives Bibliotheque et Canada Archives Canada Published Heritage Direction du Branch Patrimoine de I'edition 395 Wellington Street 395, rue Wellington Ottawa ON K1A0N4 Ottawa ON K1A 0N4 Canada Canada Your file Votre reference ISBN: 978-0-494-90087-1 Our file Notre reference ISBN: 978-0-494-90087-1 NOTICE: AVIS: The author has granted a non L'auteur a accorde une licence non exclusive exclusive license allowing Library and permettant a la Bibliotheque et Archives Archives Canada to reproduce, Canada de reproduire, publier, archiver, publish, archive, preserve, conserve, sauvegarder, conserver, transmettre au public communicate to the public by par telecommunication ou par I'lnternet, preter, telecommunication or on the Internet, distribuer et vendre des theses partout dans le loan, distrbute and sell theses monde, a des fins commerciales ou autres, sur worldwide, for commercial or non support microforme, papier, electronique et/ou commercial purposes, in microform, autres formats. paper, electronic and/or any other formats. The author retains copyright L'auteur conserve la propriete du droit d'auteur ownership and moral rights in this et des droits moraux qui protege cette these. Ni thesis. Neither the thesis nor la these ni des extraits substantiels de celle-ci substantial extracts from it may be ne doivent etre imprimes ou autrement printed or otherwise reproduced reproduits sans son autorisation. -

Sexual Battery in Phelan Hall Reported
Scene: Hart's War—Page 13 Sports: Baseball Home Opener—Page 20 JJBMBBi San Francisco FOGHORN THE UNIVERSITY OF SAN FRANCISCO FEBRUARY 14,2002 WWW.FOGHORNONLINE.COM VOLUME 98, ISSUE 11 Sexual Battery in Phelan Hall Reported Victoria Leon Guerrero lowed her to her room and com the man, whom she met in front and they searched the entire area." ing me, so there are always mul FOGHORN STAFFWRITER mitted a sexual battery on her," of the hall, into her dorm room, JJ Thorp, director of the Office tiple people who will respond." A University of San Francisco stu said Wight. He explaine that sexual Wight said. of Residence Life, said this is the first Heidi Prestegard, senior, said dent reported that she was sexually battery is the unwanted touching The student's roommate reported incident of sexual assault she has always felt safe living in the battered in her Phelan Hall dorm of another person's private parts. showed up in time to prevent the occurring in a residence hall since residence halls. room two weeks ago, said Ted Wight, "There's some questions here as to sexual battery from escalating he became director seven years ago. "You have the people in the director of Public Safety. what really happened and how this and the man left. "This is a great example of why front desk that are always there, "We haven't really finished the transpired and we're still working "He just walked away," Wight it is important for people to sign in and definitely some people get by investigation and we're not really on that." said. -

Thesis June 12
Teaching Science for Social Justice: An Examination of Elementary Preservice Teachers’ Beliefs by James C. Eslinger A thesis submitted in conformity with the requirements for the degree of Doctor of Philosophy Department of Curriculum, Teaching and Learning Ontario Institute for Studies in Education University of Toronto © Copyright by James C. Eslinger (2013) TEACHING SCIENCE FOR SOCIAL JUSTICE: AN EXAMINATION OF ELEMENTARY PRESERVICE TEACHERS’ BELIEFS Doctor of Philosophy James C. Eslinger Department of Curriculum, Teaching and Learning Ontario Institute for Studies in Education of the University of Toronto 2013 ABSTRACT This qualitative study examines the beliefs and belief changes of eleven elementary preservice teachers about teaching science for social justice. Using constructivist grounded theory, it forwards a new theory of belief change about teaching science for social justice. The theory posits that three teaching and learning conditions may facilitate belief change: preservice teachers need to recognize (1) the relationship between science and society; (2) the relationship between individuals and society; and (3) the importance of taking action on socioscientific issues. This research responds to calls by critical scholars of teacher education who contend that beliefs in relation to equity, diversity, and multiculturalism need to be explored. They have found that many preservice teachers hold beliefs that are antithetical to social justice tenets. Since beliefs are generally considered to be precursors to actions, identifying and promoting change in beliefs are important to teaching science for social justice. Such a move may lead to the advancement of ii curricular and pedagogical efforts to promote the academic participation and success in elementary science of Aboriginal and racialized minority students. -
Brooks Wackerman, Brings a Most Assured Sense of Groove to BOB BERENSON Or (815) 732-5283
!350%2 #/,/33!, 7). 02):%0!#+!'% 41&$*"-%36..&3-&"%&3$%306/%61 &ROM'RETSCH 3ABIAN 'IBRALTAR ,0 4OCA AND0ROTECTION2ACKET 6ALUED AT/VER !UGUST 4HE7ORLDS$RUM-AGAZINE *.1307& :0635*.& *-"/36#*/ 3&13&4&/5*/(5)&/&8 %36..*/(3&(*.& 36'64i41&&%:w+0/&4 %6,&&--*/(50/4 53"(*$"$30#"5 #"%3&-*(*0/4 )*()"35 7"/%&3(3""'4 #300,4 16/,30$, (6:&7"/4130(03*(*/"- 8"$,&3."/ $".$0'03$0--&$5034 "-,"-*/&53*04%&3&,(3"/5(&"3*/(61 "-"/1"340/45)&130+&$50'3&$03%*/(%36.4 -ODERN$RUMMERCOM 3&7*&8&% :".")"$-6#$6450.(*(.",&3;*-%+*"/"48*4),/0$,&3;$)*/"4MM -13*$"3%$"+0/.*$4:45&..00/.*$4 Volume 35, Number 8 • Cover photo by Alex Solca CONTENTS Alex Solca Alex Solca 34 ILAN RUBIN 42 BROOKS He appeared in the Guinness record book, performed at the Modern Drummer Fest, and toured with Nine Inch Nails before he could legally buy a drink. MD checks in with the prodigious multi-instrumentalist, who recently released his WACKERMAN ambitious second solo album. After having served Infectious Grooves, the Vandals, Suicidal Tendencies, Tenacious D, and Korn with honor, he’s now celebrating a decade of bringing rare refinement to the pioneering punk of Bad Religion. Joe Del Tufo 12 Update NYC Jazzer MARK FERBER UFO’s ANDY PARKER Duff McKagan’s ISAAC CARPENTER Justin Bieber’s MELVIN BALDWIN Dropkick Murphys’ MATT KELLY Robert Caplin 30 A Different View Producer/Bandleader ALAN PARSONS 72 Portraits Avant/Rock Independent CHES SMITH 52 GUY EVANS 76 Woodshed Driven by its longtime drummer’s galvanizing performances, Drummer/Producer BOBBY MACINTYRE’s Studio 71 the iconic British prog band Van der Graaf Generator is as intense and unpredictable as ever. -

Episode #19 - Bad Religion Exposé
Episode #19 - Bad Religion Exposé Intro Welcome to Point Radio Cast. Who am I, why I'm doing this. Support Click through the site! pointradiocast.com/music.html Contact Info [email protected] Show intro - Theme Bad Religion: Through the Decades Exposé. They've been at it since 1979. Formed in LA in November or December, 1979. Greg Graffin and Brett Gurewitz have been there the whole time. They went from garage punk rock, to the punk/hardcore combo sound of today. Still at it, and still making great music! They're sort of nerd punk, and they've always had a left political angle. 1982 How Could Hell Be Any Worse? 6 Latch Key Kids Voice of God is Government Fu*k Armageddon… This is Hell, In the Night, Damned to be Free, White Trash 1983 Into the Unknown 4 Chasing the Wild Goose Losing Generation 1988 Suffer 6 Best for You Do What You Want You Are (The Government), Give You Nothing, Suffer 1989 No Control 8 Change of Ideas You No Control, I Want to Conquer the World, Anxiety, Automatic Man 1990 Against the Grain 9 Flat Earth Society Walk Away Modern Man, The Positive Aspect of Negative Thinking, Anesthesia, Faith Alone, Against the Grain, 21st Century (Digital Boy), Unacceptable 1992 Generator 8 Generator Too Much To Ask Heaven is Falling, Atomic Garden, The Answer, Fertile Cresent, Chimaera 1993 Recipe for Hate 7 American Jesus Don't Pray on Me Struck a Nerve, My Poor Friend Me, Skyscraper 1994 Stranger Than Fiction 7 Stranger Than Fiction Hooray for Me… Incomplete, Better Off Dead 1996 The Gray Race 9 Punk Rock Song Drunk Sincerity -

Festival Di Majano 2020 Bad Religion
COMUNICATO STAMPA Zenit srl in collaborazione con Pro Majano, Regione Friuli Venezia Giulia, PromoTurismo FVG e Vertigo, nell’ambito della 60° edizione del Festival di Majano presenta FESTIVAL DI MAJANO 2020 ANNUNCIATO IL PRIMO GRANDE CONCERTO DELLA 60° EDIZIONE IL GRUPPO CALIFORNIANO FESTEGGIA SUL PALCO I 40 ANNI DI ATTIVITÁ AUTENTICI SIMBOLI DEL PUNK MONDIALE, TERRANNO A MAJANO L’UNICO CONCERTO NEL NORDEST DI SOLO DUE DATE ITALIANE HANNO FIRMATO ALBUM MEMORABILI COME “SUFFER”, “NO CONTROL”, “RECIPE FOR HATE” E SONO DA SEMPRE AMATI PER I TESTI IMPEGNATI E LA QUALITÁ DELLE ESIBIZIONI LIVE IL FESTIVAL DI MAJANO COMPIE 60 ANNI, DA SEMPRE PUNTO DI RIFERIMENTO PER LA GRANDE MUSICA LIVE ITALIANA E INTERNAZIONALE #FestivalMajano60 BAD RELIGION “40th Anniversary Tour” 12 agosto 2020, inizio ore 21.30 MAJANO (UDINE), AREA CONCERTI FESTIVAL Biglietti in vendita online su Ticketone.it dalle ore 10.00 di venerdì 20 dicembre e in tutti i punti autorizzati dalle 10.00 di lunedì 23 dicembre. Info e punti vendita autorizzati su www.azalea.it Il Festival di Majano, storica rassegna musicale, culturale e enogastronomica del Friuli Venezia Giulia, festeggia nel 2020 i suoi 60° anni attestandosi come una delle manifestazioni più longeve e di successo dell’estate. Un’edizione importante la prossima, che vede oggi annunciato il primo grande ospite musicale internazionale. Saranno i Bad Religion, hardcore punk band californiana, autentico simbolo mondiale di questo genere, che festeggerà sul palco i 40 anni di attività con una tournée europea che vedrà in Italia solo due date, l’unica delle quali nel Nordest proprio al Festival di Majano, il prossimo 12 agosto 2020. -
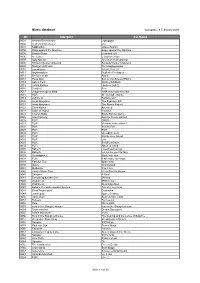
Music Database Nr Interpret CD-Name
Music database last update: 8 Febrauary 2009 Nr Interpret CD-Name 0001 Herbert Grönemeyer unplugged 0002 Herbert Grönemeyer Live 0003 Siddhartha Cruise Atlantic 0004 Rage against the Machine Rage against the Machine 0005 Beastie Boys Licensed to ill 0006 Ice Cube Lethal Incection 0007 Ugly Kid Joe American least wanted 0008 Schauorchester Ungelenk Schauorchester Ungelenk 0009 Rüdiger Hoffmann Der Hauptgewinner 0010 Liquid Bass In full Effect EP 0011 Nightcrawlers Push the Feeling on 0012 Recycle or die Rod 4 0013 Pizza Man Sex on the Streets RMX´s 0014 Aphex Twin Donkey Rhubarb 0015 Celvin Rotane I believe (uuh!) 0016 Cenith X Feel 0017 Judgement gone blind 1994 new hope-new fear 0018 PUR Sie sieht die Sonne 0019 Johnny O. Fantasy Girl 0020 Acrid Abeyance The Exposure EP 0021 Acrid Abeyance The Remix Project 0022 Earth Nation Alienated 0023 State of House Invasion 0024 Cosmic Baby Blade Runner part1 0025 Alien Factory Get the Future started 0026 PUR OPUS I 0027 PUR Vorsicht zerbrechlich ! 0028 PUR Wie im Film 0029 PUR PUR 0030 PUR Unendlich mehr 0031 PUR Nichts ohne Grund 0032 PUR Live 0033 PUR Seiltänzertraum 0034 PUR Abenteuerland 0035 Baby D I need your loving 0036 Baby D Let me be your fantasy 0037 Soundgarden Black hole sun 0038 Felix It will make my crazy 0039 Babylon Zoo Spaceman 0040 Oasis Wonderwall 0041 Madonna You´ll see 0042 Cherry Moon Trax In my Electric House 0043 Sampler E-Beat 0044 Everything but the Girl Missing 0045 Wolfsheim 55578 / Live 0046 Wolfsheim Dreaming Apes 0047 Bobo in the white wooden houses Travel in my mind 0048 Blind Passengers´ Destroyka 0049 Jamiroquai Space Cowboy 0050 Anne Clark Best of Anne Clark 0051 Fugees Fu-Gee-La 0052 Pulp Disco 2000 0053 Fury in the Slaughterhouse Fury in the Slaughterhouse 0054 Trancemaster Dream Structures 0055 Alanis Morissette Ironic 0056 Fury in the Slaughterhouse The hearing and the sense of Balance 0057 Deep Blue Something Breakfast at Tiffany´s 0058 Sampler 9000-Ohm 0059 Paul van Dyk Seven Ways 0060 Faithless Insomia 0061 Emmanuel Top & B.B.E. -

L F Kennedy Thesis FINAL
THE UNIVERSITY OF HULL Functions of Genre in Metal and Hardcore Music being a Thesis submitted for the Degree of PhD in Music in the University of Hull by Lewis F. Kennedy (MMus, BA) September 2017 Table of Contents List of Figures ........................................................................................................ iv List of Tables .......................................................................................................... v Acknowledgements ............................................................................................... vi Abstract .............................................................................................................. viii Introduction ........................................................................................................... 1 Chapter Outline ...................................................................................................... 3 Chapter One – Metal, Hardcore, and Discourse ...................................................... 6 Forging Metal Studies ..................................................................................................... 7 Early Metal Studies (1990s) .............................................................................................. 8 Metal Studies Expands (21st Century) ............................................................................. 11 Hardcore and/or Punk Studies ....................................................................................... 16 Metal Studies, Hardcore -

UNIVERSAL MUSIC • Esperanza Spalding – Emily's D+Evolution
• Esperanza Spalding – Emily’s D+Evolution • Donovan Woods – Hard Settle, Ain’t Troubled • The Lovelocks – Born to Love New Releases From Classics And Jazz Inside!!! And more… UNI16-08 UNIVERSAL MUSIC 2450 Victoria Park Ave., Suite 1, Willowdale, Ontario M2J 5H3 Phone: (416) 718.4000 *Artwork shown may not be final UNIVERSAL MUSIC CANADA NEW RELEASE Artist/Title: The 1975/ I like it when you sleep, for you are so beautiful yet so unaware (CD) Cat. #: B002433202 Price Code: JSP th Order Due: January 28th Release Date: February 26 2016 6 02547 67739 6 File: Alternative Genre Code: 2 Box Lot: 25 Track List: 1. The 1975 10. Somebody Else 2. Love Me 11. Loving Someone 3. UGH! 12. I like it when you sleep, for you 4. A Change Of Heart are so beautiful yet so unaware 5. She’s American 13. The Sound 6. if I Believe You 14. This Must Be A Dream 7. Please Be Naked 15. Paris 8. Lostmyhead 16. Nana 9. The Ballad of Me and My Brain 17. She Lays Down Artist/Title: The 1975/ I like it when you sleep, for you are so beautiful yet so unaware (LP) *Vinyl Is One Way Sale* 6 02547 73937 7 Cat. #: B002448301 Price Code: BD th Order Due: January 28th Release Date: February 26 2016 File: Alternative Genre Code: 2 Box Lot: Key Points: I like it when you sleep, for you are so beautiful yet so unaware of it, the eagerly awaited new album from the UK art-pop quartet THE 1975 will be released February 26 via Dirty Hit/ Interscope Records.