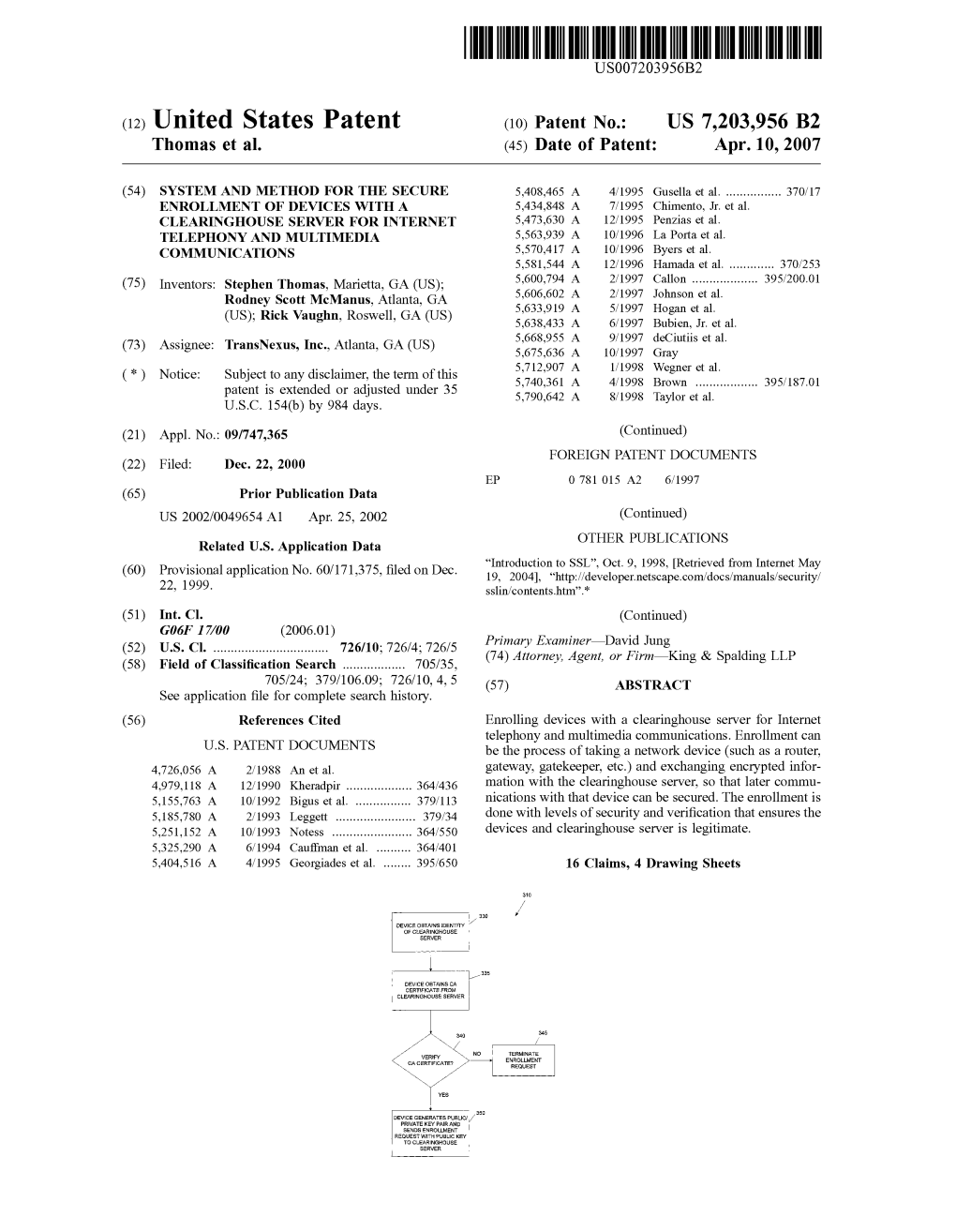
(12) United States Patent (10) Patent No.: US 7,203,956 B2 Thomas Et Al
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mobile Telemedicine and Wireless Remote Monitoring Applications
İSTANBUL TECHNICAL UNIVERSITY INSTITUTE OF SCIENCE AND TECHNOLOGY MOBILE TELEMEDICINE AND WIRELESS REMOTE MONITORING APPLICATIONS M.Sc. Thesis by Taner SOYUGENÇ, B.Sc. Department : Electronics and Communication Engineering Programme : Biomedical Engineering NOVEMBER 2006 PREFACE In this project, my main goal is to implement a mobile sample application by defining the related global standards for telemedicine. The work is focused on recommendations of technology associated with a feasibility study. First of all, I would like to thank Assoc. Prof. Dr. Selçuk PAKER for his valuable advice, support and encouragement to accomplish the project. Besides, I would like to thank my family who is always with me giving support at every step of my life. November 2006 Taner SOYUGENÇ iii CONTENTS ACRONYMS vi LIST OF TABLES viii LIST OF FIGURES ix SUMMARY xi ÖZET xii 1. INTRODUCTION 1 1.1. Technology Overview 2 1.1.1. Communication Infrastructure 5 1.1.2. Overview of GSM-GPRS 6 1.1.2.1. Brief History of GSM 8 1.1.2.2. GPRS 12 1.1.3. Mobile Solutions 14 1.1.4. Wireless Medical Sensors 15 1.2. Aim of the Project 16 2. WORLDWIDE APPLICATIONS, VENDORS AND STANDARDS 18 2.1. Available Products 19 2.1.1. ECG 19 2.1.2. Pulse Oximeter 20 2.1.3. Blood Pressure Sensor 23 2.1.4. Various Sensor Brands 24 2.1.5. Advanced Research 27 2.1.6. Home Care Monitoring Systems 31 2.2. Medical Information Standards and Organizations 35 2.2.1. ASTM 39 2.2.2. CEN/TC251 Health Informatics 39 2.2.3. -

Next Generation Web Scanning Presentation
Next generation web scanning New Zealand: A case study First presented at KIWICON III 2009 By Andrew Horton aka urbanadventurer NZ Web Recon Goal: To scan all of New Zealand's web-space to see what's there. Requirements: – Targets – Scanning – Analysis Sounds easy, right? urbanadventurer (Andrew Horton) www.morningstarsecurity.com Targets urbanadventurer (Andrew Horton) www.morningstarsecurity.com Targets What does 'NZ web-space' mean? It could mean: •Geographically within NZ regardless of the TLD •The .nz TLD hosted anywhere •All of the above For this scan it means, IPs geographically within NZ urbanadventurer (Andrew Horton) www.morningstarsecurity.com Finding Targets We need creative methods to find targets urbanadventurer (Andrew Horton) www.morningstarsecurity.com DNS Zone Transfer urbanadventurer (Andrew Horton) www.morningstarsecurity.com Find IP addresses on IRC and by resolving lots of NZ websites 58.*.*.* 60.*.*.* 65.*.*.* 91.*.*.* 110.*.*.* 111.*.*.* 113.*.*.* 114.*.*.* 115.*.*.* 116.*.*.* 117.*.*.* 118.*.*.* 119.*.*.* 120.*.*.* 121.*.*.* 122.*.*.* 123.*.*.* 124.*.*.* 125.*.*.* 130.*.*.* 131.*.*.* 132.*.*.* 138.*.*.* 139.*.*.* 143.*.*.* 144.*.*.* 146.*.*.* 150.*.*.* 153.*.*.* 156.*.*.* 161.*.*.* 162.*.*.* 163.*.*.* 165.*.*.* 166.*.*.* 167.*.*.* 192.*.*.* 198.*.*.* 202.*.*.* 203.*.*.* 210.*.*.* 218.*.*.* 219.*.*.* 222.*.*.* 729,580,500 IPs. More than we want to try. urbanadventurer (Andrew Horton) www.morningstarsecurity.com IP address blocks in the IANA IPv4 Address Space Registry Prefix Designation Date Whois Status [1] ----- -

Overview of PHP Where to Get PHP Installing and Configuring PHP
1 G Overview of PHP G Where to get PHP G Installing and configuring PHP on your web server Author: Tim Green What Is PHP? This chapter is a basic introduction to the workings of PHP and how it all began. We will briefly discover its origins as a programming language, looking at how it has evolved in earlier versions of Dreamweaver to its current implementation in Dreamweaver MX. As an introductory guide, we will take you through your first steps in working with PHP. We'll look at where you can obtain it, and discuss the various installation options that are available to you. We'll also cover, in detail, the necessary steps to install and configure PHP to work with your preferred web server. Summarizing this chapter we also include timely troubleshooting hints and tips should you encounter any problems or difficulties with your new PHP installation. What Is PHP and What Is It for? Put simply, PHP is a tool for creating dynamic web pages. Its presence is completely transparent to the end user. PHP is easy to learn, and most importantly, it's easy to implement. PHP in the Real World So, PHP creates dynamic web pages, but what exactly do we mean by dynamic? Today's web sites come in all shapes and sizes. Some provide rich user experiences using Flash animations; others provide interactive page elements created with JavaScript, or a combination of both (or other) technologies. These types of web site can be described as being dynamic as some part of them changes as a result of either a manual or automatic stimulus. -

Comparison of Web Server Software from Wikipedia, the Free Encyclopedia
Create account Log in Article Talk Read Edit ViewM ohrisetory Search Comparison of web server software From Wikipedia, the free encyclopedia Main page This article is a comparison of web server software. Contents Featured content Contents [hide] Current events 1 Overview Random article 2 Features Donate to Wikipedia 3 Operating system support Wikimedia Shop 4 See also Interaction 5 References Help 6 External links About Wikipedia Community portal Recent changes Overview [edit] Contact page Tools Server Developed by Software license Last stable version Latest release date What links here AOLserver NaviSoft Mozilla 4.5.2 2012-09-19 Related changes Apache HTTP Server Apache Software Foundation Apache 2.4.10 2014-07-21 Upload file Special pages Apache Tomcat Apache Software Foundation Apache 7.0.53 2014-03-30 Permanent link Boa Paul Phillips GPL 0.94.13 2002-07-30 Page information Caudium The Caudium Group GPL 1.4.18 2012-02-24 Wikidata item Cite this page Cherokee HTTP Server Álvaro López Ortega GPL 1.2.103 2013-04-21 Hiawatha HTTP Server Hugo Leisink GPLv2 9.6 2014-06-01 Print/export Create a book HFS Rejetto GPL 2.2f 2009-02-17 Download as PDF IBM HTTP Server IBM Non-free proprietary 8.5.5 2013-06-14 Printable version Internet Information Services Microsoft Non-free proprietary 8.5 2013-09-09 Languages Jetty Eclipse Foundation Apache 9.1.4 2014-04-01 Čeština Jexus Bing Liu Non-free proprietary 5.5.2 2014-04-27 Galego Nederlands lighttpd Jan Kneschke (Incremental) BSD variant 1.4.35 2014-03-12 Português LiteSpeed Web Server LiteSpeed Technologies Non-free proprietary 4.2.3 2013-05-22 Русский Mongoose Cesanta Software GPLv2 / commercial 5.5 2014-10-28 中文 Edit links Monkey HTTP Server Monkey Software LGPLv2 1.5.1 2014-06-10 NaviServer Various Mozilla 1.1 4.99.6 2014-06-29 NCSA HTTPd Robert McCool Non-free proprietary 1.5.2a 1996 Nginx NGINX, Inc. -

Download the Index
41_067232945x_index.qxd 10/5/07 1:09 PM Page 667 Index NUMBERS 3D video, 100-101 10BaseT Ethernet NIC (Network Interface Cards), 512 64-bit processors, 14 100BaseT Ethernet NIC (Network Interface Cards), 512 A A (Address) resource record, 555 AbiWord, 171-172 ac command, 414 ac patches, 498 access control, Apache web server file systems, 536 access times, disabling, 648 Accessibility module (GNOME), 116 ACPI (Advanced Configuration and Power Interface), 61-62 active content modules, dynamic website creation, 544 Add a New Local User screen, 44 add command (CVS), 583 address books, KAddressBook, 278 Administrator Mode button (KDE Control Center), 113 Adobe Reader, 133 AFPL Ghostscript, 123 41_067232945x_index.qxd 10/5/07 1:09 PM Page 668 668 aggregators aggregators, 309 antispam tools, 325 aKregator (Kontact), 336-337 KMail, 330-331 Blam!, 337 Procmail, 326, 329-330 Bloglines, 338 action line special characters, 328 Firefox web browser, 335 recipe flags, 326 Liferea, 337 special conditions, 327 Opera web browser, 335 antivirus tools, 331-332 RSSOwl, 338 AP (Access Points), wireless networks, 260, 514 aKregator webfeeder (Kontact), 278, 336-337 Apache web server, 529 album art, downloading to multimedia dynamic websites, creating players, 192 active content modules, 544 aliases, 79 CGI programming, 542-543 bash shell, 80 SSI, 543 CNAME (Canonical Name) resource file systems record, 555 access control, 536 local aliases, email server configuration, 325 authentication, 536-538 allow directive (Apache2/httpd.conf), 536 installing Almquist shells -

Patent (10) Patent N0.: US 7,398,551 B2 Thomas Et Al
US007398551B2 (12) Ulllted States Patent (10) Patent N0.: US 7,398,551 B2 Thomas et al. (45) Date of Patent: Jul. 8, 2008 (54) SYSTEM AND METHOD FOR THE SECURE 5,408,465 A 4/1995 Gusella et al. .............. .. 370/17 ENROLLMENT 0F DEVICES WITH A 5,434,848 A 7/1995 Chimento, Jr. et al. ¥€E€g§§ggggi§§€ig?gg?INTERNET 5,473,630 A 12/1995 PenZias et al. COMMUNICATIONS 5,563,939 A 10/1996 La Porta et al. 5,570,417 A 10/1996 Byers et al. (75) Inventors; Stephen Thomas’ Marietta’ GA (Us); 5,581,544 A 12/1996 Hamada et al. ........... .. 370/253 Rodney Scott McManus, Atlanta, GA 5,600,794 A 2/1997 Callon ................. .. 395/20001 (US); Rick Vaughn, Roswell, GA (US) 5,606,602 A 2/1997 Johnson et a1. (73) Assignee: TransNeXus, Inc., Atlanta, GA (U S) ( * ) Notice: Subject‘ to any disclaimer, the term of this (Continued) patent 15 extended or adjusted under 35 U.S.C. 154(b) by 0 days. FOREIGN PATENT DOCUMENTS (21) Appl. No.: 11/503,852 EP 0 781015 A2 6/1997 (22) Filed: Aug. 14, 2006 (65) Prior Publication Data (Continued) US 2007/0033644 A1 Feb. 8, 2007 OTHER PUBLICATIONS Related U_s_ Application Data Role-based access control with X509 attribute certi?cates _ _ _ _ Chadwick, D.; Otenko,A.; Ball, E.; Internet Computing, IEEE vol. 7, (63) Cont1nuat1on of appl1cat10n No. 09/747,365, ?led on Issue 2, Mar,-Apr, 2003 pp, 62-69,* Dec. 22, 2000, now Pat. No. 7,203,956. -

PERFORMANCE to Improve the Performance Many Things Must Be Considered
CHAPTER FIVE PERFORMANCE To improve the performance many things must be considered. The web portal must avoid the system downtimes. Different types of the web servers are available in the market. Selection of the web server must be done after considering the server limitations and the needs of the web portal. Most of the time some assumptions are made about the client machine, but to make the robust web portal all the Client side limitations (e.g., communication media limitations or availability of devices like printer, speaker, etc.) must be considered. The most important point about the performance is speed optimization which can be achieved by Task scheduling. Different types of tools are available in the market as per the reQuirements for the Load and Performance Measurement. 5 PERFORMANCE 5.1 Introduction The software products undergo several cycles of alpha and beta tests and receive feedback from the users before they are distributed as a final product. The alpha and beta versions are given to the users and users suggest changes, which are reflected in the final product. If the software is fully customized then different modules are prepared and these models are installed on the user machines and users are asked to use the modules. Dynamic Content Caching (Centralized or Distributed) is used to improve the performance. The End-Users may struggle in the identification and manipulation of variables. The Modelling Web Applications Compare the modelling components using non-object oriented languages, and Compare the modelling components using object-oriented languages. Most commonly used model components are Script, Mark up, Style Sheet, Schema, Data languages, and Object-Oriented languages. -

Installation and Configuration General Installation Considerations
Installation and Configuration General Installation Considerations Before starting the installation, first you need to know what do you want to use PHP for. There are three main fields you can use PHP, as described in the What can PHP do? section: • Websites and web applications (server-side scripting) • Command line scripting • Desktop (GUI) applications For the first and most common form, you need three things: PHP itself, a web server and a web browser. You probably already have a web browser, and depending on your operating system setup, you may also have a web server (e.g. Apache on Linux and MacOS X; IIS on Windows). You may also rent webspace at a company. This way, you don't need to set up anything on your own, only write your PHP scripts, upload it to the server you rent, and see the results in your browser. In case of setting up the server and PHP on your own, you have two choices for the method of connecting PHP to the server. For many servers PHP has a direct module interface (also called SAPI). These servers include Apache, Microsoft Internet Information Server, Netscape and iPlanet servers. Many other servers have support for ISAPI, the Microsoft module interface (OmniHTTPd for example). If PHP has no module support for your web server, you can always use it as a CGI or FastCGI processor. This means you set up your server to use the CGI executable of PHP to process all PHP file requests on the server. If you are also interested to use PHP for command line scripting (e.g. -

Fortiweb 4.0 MR4 CLI Reference, 1St Edition
CLI Reference for FortiWeb™ 4.0 MR4 Courtney Schwartz Contributors: George Csaba Martijn Duijm Patricia Siertsema Idan Soen Shiji Li Hao Xu Shiqiang Xu Forrest Zhang Contents Introduction ............................................................................................24 Scope ............................................................................................................................. 24 Conventions .................................................................................................................. 25 IP addresses............................................................................................................. 25 Cautions, notes, & tips.............................................................................................. 25 Typographic conventions.......................................................................................... 25 Command syntax...................................................................................................... 26 What’s new .............................................................................................28 Documentation changes .............................................................................................. 32 Using the CLI ..........................................................................................34 Connecting to the CLI................................................................................................... 34 Connecting to the CLI using a local console............................................................ -

Release 5.0.4 the Phpmyadmin Devel Team
phpMyAdmin Documentation Release 5.0.4 The phpMyAdmin devel team Jan 24, 2021 Contents 1 Introduction 3 1.1 Supported features............................................3 1.2 Shortcut keys...............................................4 1.3 A word about users............................................4 2 Requirements 5 2.1 Web server................................................5 2.2 PHP....................................................5 2.3 Database.................................................6 2.4 Web browser...............................................6 3 Installation 7 3.1 Linux distributions............................................7 3.2 Installing on Windows..........................................8 3.3 Installing from Git............................................8 3.4 Installing using Composer........................................9 3.5 Installing using Docker..........................................9 3.6 Quick Install............................................... 14 3.7 Verifying phpMyAdmin releases..................................... 16 3.8 phpMyAdmin configuration storage................................... 17 3.9 Upgrading from an older version..................................... 19 3.10 Using authentication modes....................................... 19 3.11 Securing your phpMyAdmin installation................................ 27 3.12 Using SSL for connection to database server.............................. 28 3.13 Known issues............................................... 28 4 Configuration 29 4.1 Basic -

Instituto Tecnológico Y De Estudios Superiores De Monterrey Campus Monterrey Programa De Graduados En Tecnologias De Información Y Electrónica
INSTITUTO TECNOLÓGICO Y DE ESTUDIOS SUPERIORES DE MONTERREY CAMPUS MONTERREY PROGRAMA DE GRADUADOS EN TECNOLOGIAS DE INFORMACIÓN Y ELECTRÓNICA ESTUDIO EXPLORATORIO: OPEN SOURCE COMO PLATAFORMA DE TECNOLOGÍA DE INFORMACIÓN EN LA PYME DE MONTERREY N.L. TESIS PRESENTADA COMO REQUISITO PARCIAL PARA OBTENER EL GRADO ACADÉMICO DE: MAESTRÍA EN ADMINISTRACIÓN DE TECNOLOGÍAS DE INFORMACIÓN POR DAVID HERNÁNDEZ ORTIZ MONTERREY, N. L. ABRIL 2006 INSTITUTO TECNOLÓGICO Y DE ESTUDIOS SUPERIORES DE MONTERREY CAMPUS MONTERREY PROGRAMA DE GRADUADOS EN TECNOLOGÍAS DE INFORMACIÓN Y ELECTRÓNICA ESTUDIO EXPLORATORIO: OPEN SOURCE COMO PLATAFORMA DE TECNOLOGÍA DE INFORMACIÓN EN LA PYME DE MONTERREY, N. L. TESIS PRESENTADA COMO REQUISITO PARCIAL PARA OBTENER EL GRADO ACADÉMICO DE: MAESTRÍA EN ADMINISTRACIÓN DE TECNOLOGÍAS DE INFORMACIÓN POR: DAVID HERNÁNDEZ ORTÍZ MONTERREY, NUEVO LEÓN MARZO 2006 INSTITUTO TECNOLÓGICO Y DE ESTUDIOS SUPERIORES DE MONTERREY CAMPUS MONTERREY PROGRAMA DE GRADUADOS EN TECNOLOGÍAS DE INFORMACIÓN Y ELECTRÓNICA ESTUDIO EXPLORATORIO: OPEN SOURCE COMO PLATAFORMA DE TECNOLOGÍA DE INFORMACIÓN EN LA PYME DE MONTERREY, N, L. TESIS PRESENTADA COMO REQUISITO PARCIAL PARA OBTENER EL GRADO ACADÉMICO DE: MAESTRÍA EN ADMINISTRACIÓN DE TECNOLOGÍAS DE INFORMACIÓN POR: DAVID HERNÁNDEZ ORTÍZ MONTERREY. NUEVO LEÓN MARZO 2006 ESTUDIO EXPLORATORIO: OPEN SOURCE, COMO PLATAFORMA DE TECNOLOGÍA DE INFORMACIÓN EN LA PYME DE MONTERREY, N. L. POR: DAVID HERNÁNDEZ ORTÍZ TESIS Presentada al Programa de Graduados en Tecnologías de Información y Electrónica Este trabajo es requisito para obtener el grado de Maestro en Administración de Tecnologías de Información INSTITUTO TECNOLÓGICO Y DE ESTUDIOS SUPERIORES DE MONTERREY MARZO DE 2006 Dedicatoria A Dios... Por permitirme vivir esta experiencia, por darme salud y la sabiduría para entender todo lo que ha sucedido durante esta tiempo, por seguirme apoyando a pensar de las cosas y sobre todo, por darme una familia que no tiene comparación.. -

Software Libre Vs Software Propietario Ventajas Y Desventajas
Software libre vs software propietario Ventajas y desventajas Culebro Ju´arez, Montserrat. G´omezHerrera, Wendy Guadalupe. Torres S´anchez, Susana. M´exico,Mayo 2006. ii ´Indice general Agradecimientos. VII Pr´ologo. IX Introducci´on. 1 1. Conceptos fundamentales sobre software. 3 1.1. Definici´onde software. 3 1.2. Definici´onde software libre. 3 1.3. Definici´onde software propietario. 4 1.3.1. Software propietario. 4 1.3.2. Objeciones al t´ermino “propietario”. 5 1.3.3. Software privativo. 5 1.3.4. Objeciones al t´ermino “privativo”. 5 1.3.5. Software no libre. 5 1.3.6. Objeciones al t´ermino “no libre”. 5 1.3.7. Software privado. 5 1.3.8. Objeciones al t´ermino “privado”. 6 1.3.9. Software con propietario. 6 1.3.10. Objeciones al t´ermino “con propietario”. 6 1.4. Software semilibre. 6 1.5. Freeware. 6 1.6. Shareware. 7 1.7. Abandonware. 7 1.8. Warez. 7 2. Visi´onhist´oricadel software. 9 2.1. La importancia del software. 9 2.2. Incursi´onde los hackers. 10 2.3. La cultura Unix. 10 2.4. GNU. 11 2.5. Libertad y costo. 12 2.6. Linux. 12 2.7. Open Source (c´odigoabierto). 14 2.8. El papel del software libre en el crecimiento de Internet. 14 2.9. Formatos abiertos. 15 2.10. Visi´onhist´oricadel Software propietario (Microsoft). 15 iii 3. Copyright, copyleft y patentes. 17 3.1. Copyright. 17 3.1.1. Derecho de autor y Copyright. 17 3.1.2. El contrato de copyright.