Benefits and Barriers of Adopting Cloud Computing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Dispatch List Date 29-04-2021 & 30-04-2021
ANDHRA PRADESH PHARMACY COUNCIL--DISPATCH LIST DATE 29-04-2021 & 30-04-2021 S.NO DESTINATION PINCODE BARCODE CANDIDATE NAME ADDRESS REMARKS 1 Ananthapur 515822 RN712290012IN A Mounika Nimbagallu 25290 2 Visakhapatnam 531126 RN712290026IN Meka Pawan Kalyan Edatam 25889 3 Prakasam 523113 RN712290030IN U Harshitha Rani Sakhavaram 24922 4 Prakasam 523105 RN712290043IN Shaik Fouziya Kandukuru 24904 5 Guntur 522647 RN712290057IN M Chaitanya Vani Vinukonda 24854 6 Guntur 522663 RN712290065IN N Chaitanya Kumar Bandlamotlu 25410 7 Guntur 522101 RN712290074IN I Chandra Sekhar Bapatla 25511 8 Krishna 521227 RN712290088IN CH Venkata Sai A Konduru 25518 9 Kurnool 518001 RN712290091IN Mallela Sreelakshmi Kurnool 25365 10 Chittoor 517132 RN712290105IN Karanam Brundavani Thumminda 25360 11 Chittoor 517128 RN712290114IN Thimmapuram Bhargav Kukkallapalli 25355 12 Kurnool 518301 RN712290128IN Bandu Bai MD Sadiq NaveedAdoni 25399 13 Nellore 524201 RN712290131IN Guddeti Sasidhar Kavali 25369 14 Nellore 524228 RN712290145IN Late Sravani Venkatadripalem 25358 15 Kadapa 516228 RN712290159IN Velpula Anitha S Venkatramapuram 25359 16 Prakasam 523329 RN712290162IN D Satyanarayana Reddy Badekhanpeta 24789 17 Guntur 522268 RN712290176IN Kandepu jyothi Bellamvaripalem 24750 18 Guntur 522201 RN712290180IN Gude Sahithi Tenali 24749 19 Guntur 522309 RN712290193IN Kalepalli Manikanta Gullapalli 24783 20 Prakasam 523105 RN712290202IN Bapatla Prudhvi Raj Kandukuru 24760 21 Guntur 522403 RN712290216IN Sukavasi Pujitha Sattenapalli 24762 22 Prakasam 523225 RN712290220IN Seedarla -

Unclaimed Dividended -2007-2008
CIN L25200AP1985PLC005631 Company MOLD-TEK TECHNOLOGIES LIMITED Date Of 22-SEP-2012 AGM( DD- Sum of unpaid and unclaimed dividend 200636 Sum of interest on unpaid and unclaimed dividend 0 Sum of matured deposit 0 Sum of interest on matured deposit 0 Sum of matured debentures 0 Sum of interest on matured debentures 0 Sum of application money due for refund 0 Sum of interest on application money due for refund 0 Father/Husb Father/Husb Father/Husb Proposed Date of Middle Folio Number of Amount First Name Last Name and First and Middle and Last Address Country State District PINCode Investment Type transfer to IEPF Name Securities Due(in Rs.) Name Name Name (DD-MON-YYYY) Amount for unclaimed P N JAWALE NARAYAN TUKARAM JAWALE C/O ARAB BANKING CORP P O BOX 5698 MANAMA BAHRAIN NA NA 00001916 112.00 07-NOV-2015 and unpaid dividend Amount for unclaimed V S MAHESH V N SRINIVASAN P O BOX 26992 MANAMA BAHRAIN NA NA 00001914 112.00 07-NOV-2015 and unpaid dividend Amount for unclaimed TWENTY FIRST CENTURY Not Available 204/205 6-3-550 IIIFLR AKASH GANGA SOMAJIGUDA INDIA Andhra Pradesh Hyderabad 500482 00001543 56.00 07-NOV-2015 and unpaid dividend Amount for unclaimed A ANITHA M APPI REDDY EWS 194 K P H B COLONY INDIA Andhra Pradesh Hyderabad 500072 00001695 280.00 07-NOV-2015 and unpaid dividend Amount for unclaimed A ANURADHA A H R KRISHNA RAO 11-5-453, F-31 SRI SAI KRUPA APTS RED HILLS INDIA Andhra Pradesh Hyderabad 500004 00001823 168.00 07-NOV-2015 and unpaid dividend Amount for unclaimed A BALANAND TAMMAYYA STATE BANK OF INDIA MAKAVARAM PALEM -

ZPHS Karumanchi, Guntur(Dt)
Welcome to School Dossier Zilla Parishad High School, K a r u m a n c h i , G u n t u r district, Andhra Pradesh School Background A Zilla Parishad High School, the school provides secondary education for classes 6th to 10th. It is a government school located in Karumanchi village, Savalyapuram mandal of Guntur district of A.P. Key Data points : Location Zilla Parishad High School, Karumanchi, Savalyapuram, Guntur district, Andhra Pradesh Principal - Mr. C. S. Rangarao School Infrastructure • Number of Teachers - 14 • Number of Students - 272 • Number of Classrooms - 14 • Number of washrooms - 4 • Playground - Yes • Library Books – 1200 • No of computers - 11 • Library Infrastructure- No. Students Background Majority of the students come from very poor background. The parents of these students work as farmers, daily laborers, servant /maids or have small shops in the locality. Most of the parents are uneducated. Key Highlights : • Average Strength of the Class 20 • Girl : Boys Ratio 45% 55% • Teacher : Student Ratio 1:20 School in Pictures What is Food4Thought Foundation ? Food 4 Thought Foundation (www.food4thoughtfoundation.org). We are a Social Enterprise (Not for Profit) established in 2015, with a firm belief of ‘Connecting Idle Books to Hungry Minds’ and fulfilling every book lover wish & request – Just one more page please . Food 4 Thought Foundation believes and focuses on the 3 major sector of Education, Children and Arts & Publishing. The focus areas range from circulating idle books to building libraries (education) to encouraging reading habits (children) to saving endangered stories (arts & publishing) Focus Areas : Education • Build & Operate Library Food4Thought Foundation believes in building & operating libraries which are micro organisms i.e. -
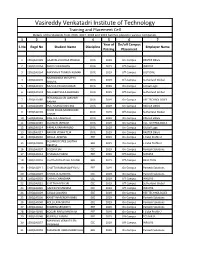
To Download Branch Wise Placement Data in Pdf Format
Vasireddy Venkatadri Institute of Technology Training and Placement Cell Details of the Students from 2016, 2017, 2018 and 2019 batches placed in various companies 1 2 3 4 5 6 7 Year of On/off Campus S.No Regd No Student Name Discipline Employer Name Passing Placement 1 15BQ1A0129 GAJAVALLI DURGA PRASAD CIVIL 2019 On-Campus RASTER ENGG 2 15BQ1A0154 MADA VISWANATH CIVIL 2019 Off-Campus INFOSYS 3 15BQ1A0164 MANNAVA THARUN KUMAR CIVIL 2019 Off-Campus JUST DIAL MUDIGONDA SRI SATYA 4 15BQ1A0170 CIVIL 2019 Off-Campus Sutherland Global SRAVYA 5 15BQ1A0172 MUVVA PAVAN KUMAR CIVIL 2019 On-Campus Global Logic 6 15BQ1A0174 NALLABOTHULA BHARGAV CIVIL 2019 Off-Campus Sutherland Global PERUMALLA SRI LAKSHMI 7 15BQ1A0185 CIVIL 2019 On-Campus VEE TECHNOLOGIES RAMYA 8 15BQ1A0193 PULI MURALI KRISHNA CIVIL 2019 On-Campus RASTER ENGG SHAIK KHAJA MOINUDDIN 9 15BQ1A0199 CIVIL 2019 Off-Campus Sutherland Global CHISTY 10 15BQ1A01A6 SWETHA TADEPALLI CIVIL 2019 On-Campus RASTER ENGG 11 15BQ1A01B7 VELINENI JAHNAVI CIVIL 2019 On-Campus VEE TECHNOLOGIES 12 16BQ5A0114 PARALA VARAPRASAD CIVIL 2019 On-Campus Global Logic 13 16BQ5A0117 RAVURI VISWA TEJA CIVIL 2019 On-Campus RASTER ENGG 14 15BQ1A0202 AKILLA. APARNA EEE 2019 On-Campus L Cube Profile 2 ALLAMUDI SREE LALITHA 15 15BQ1A0203 EEE 2019 On-Campus L Cube Profile 2 DEEPTHI 16 15BQ1A0207 B SESHA SAI EEE 2019 On-Campus Pantech Solutions 17 15BQ1A0214 CHAGALA HARINI EEE 2019 Off-Campus SONATA 18 15BQ1A0216 CHATHARASUPALLI.PAVANI EEE 2019 Off-Campus RSAC TECH 19 15BQ1A0217 CHATTU RAMANJANEYULU EEE 2019 On-Campus Pantech -

High Court of Andhra Pradesh: Amaravathi
HIGH COURT OF ANDHRA PRADESH: AMARAVATI CHIEF JUSTICE J.K. MAHESHWARI & JUSTICE NINALA JAYASURYA WRIT PETITION (PIL) No.183 of 2019 Dr. Srinivas Guntupalli, S/o Sambasiva Rao, aged about 40 years Occ:Assistant Professor General Medicine R/o F4 GRR Block ASRAM Medical College campus, Malkapuram, Eluru, West Godavari District 534005 … Petitioner Versus 1. The State of Andhra Pradesh, through its Principal Secretary, School Education Department, Secretariat Building at Velagapudi, Guntur District. 2. The Union of India, through its Principal Secretary, The Ministry of Human Resource Department. 3. The Commissioner of School Education, Andhra Pradesh, Amaravati. 4. The State Project Director, Sarva Sikha Abhiyan, High School Road, Patamata, Vijayawada. 5. The Director, SCERT, Sri Anjaneya Towers, D.No.7-104, B-Block, 2nd Floor, Vijayawada, Mylavaram Road, A.P. 6. Guntur District Aided Schools Management Association, Rep. by its District Secretary Bhatraju Chittranjan Das, Guntur. 7. Gorremuchu Venkata Narasimha Rao, S.o.Peda Rama Swamy, aged 42 years, R/o.H.No.77-54/1-15, Prakash Nagar, Vijayawada. 8. G.Sudheer Babu, S/o.Solomon, aged 39 years, R/o.6-1/5-21, Vandanam Street, Frizerpet, Chittinagar, Vijayawada. 9. Maddirala Mallikarjuna Rao, S/o.Balakotaiah, aged 48 years, R/o.Ravulakollu village, Ponnaluru Mandal, Prakasam District. HCJ & NJS,J 2 W.P. (PIL) Nos.183 & 185 of 2019 10. G. Madhu Babu, S/o.G.Venkaiah, aged 35 years, R/o.D.No.5-94, Prathuri village, Tadepalli Mandal, Polakampadu, Guntur District. 11. Dalitha Bahujan Front, rep. by its Secretary Sri M.Bhagya Rao, S/o.Venkateswarlu, aged about 48 years, Office at Arundelpet, 5/3, Guntur District. -

ANDHRA PRADESH PHARMACY COUNCIL--DISPATCH LIST Date
ANDHRA PRADESH PHARMACY COUNCIL--DISPATCH LIST Date-29-05-2020 S.NO DESTINATION PINCODE BARCODE CANDIDATE NAME ADDRESS REMARKS 1 Guntur 522002 RN794748301IN SK.Shakeela Begum Guntur 20978 2 Prakasam 523292 RN794748315IN Pakala Venkata Sreeja Ulavapadu 21166 3 Prakasam 523303 RN794748329IN Chennupalli Naga Jyothi Ballikurava 21410 4 Guntur 522503 RN794748332IN J Lakshmi Sai Velagapudi 21544 5 Prakasam 523214 RN794748346IN Shaik Shakilabi Tanguturu 21289 6 Guntur 522005 RN794748350IN M Lakshmi Prasanna Guntur 21026 7 Guntur 522306 RN794748363IN Gollapudi Naga Swetha Athota 21374 8 Guntur 522426 RN794748377IN Pattan Asma Macherla 21032 9 Prakasam 523357 RN794748385IN Chandragiri Vyshnavi Giddaluru 21495 10 Guntur 522414 RN794748394IN Palli Sarvani Takkellapadu 21218 11 Guntur 522002 RN794748403IN Eluri Venkata Prathyusha Guntur 21214 12 Prakasam 523169 RN794748417IN Kurakula Pravallika Cherukuru 21242 13 Prakasam 523346 RN794748425IN Inti Pavani Basinepalli 21572 14 Guntur 522646 RN794748434IN Telaprolu Chandana Karumanchi 21632 15 Prakasam 523305 RN794748448IN K Veerabrahmam Donakonda 21587 16 Krishna 521230 RN794748451IN Sandipamu Ajay Kumar Mylavaram 21841 17 Guntur 522201 RN794748465IN Korrapati Sai Krishna Tenali 20602 18 Krishna 521120 RN794748479IN Bhogadi Pavan Kalyan Bhavadevarapalli 21297 19 Kadapa 516360 RN794748482IN T Venkatesh Proddatur 22222 20 Kurnul 518594 RN794748496IN Mandla Nagaraju R.Nagulavaram 21928 21 Kurnul 518501 RN794748505IN S Shafi Nandyala 22155 22 Guntur 522410 RN794748519IN Naveen Bikki Atchampeta 19576 23 -

Sl. No. Name of Candidate Father's
FINAL LIST FOR AWARD OF ONGC MERITORIOUS SC/ST STUDENTS FOR THE YEAR 2018-19 (694) DISCIPLINE ENGG. SC BOYS(207) SL. NO. NAME OF CANDIDATE FATHER’S/ NAME OF INSTITUTION/UNIVERSITY PERCENTAGE OF NAME OF ZONE MOTHER'S/GUARDIAN'S MARKS IN QUALIFYING NAME EXAMINATION 1 BEJJAM NAVEEN BEJJAM RANGASWAMY CHAITANYA BHARATHI INSTITUTE OF 98.9 ZONE-5 KUMAR TECHNOLOGY, GANDIPET, HYDERABAD, TELANGANA 500 075 2 GADAGOTTI SAI GADAGOTTI JNTUH COLLEGE OF ENGINEERING 98.6 ZONE-5 KUMAR VENKATESWARLU JAGITYALA NACHUPALLY, KODIMYAL (M), JAGTIAR (DT), 505 501 3 DUBBA AKHIL KUMAR DUBBA SHYAM OSMANIA UNIVERSITY HYDERABAD, 98.5 ZONE-5 TELANGANA 500 007 4 UPPEY DHANUSH UPPEY MALLIKARJUNA NITW NATIONAL INSTITUTE OF 98.4 ZONE-5 VENKAT RAO TECHNOLOGY WARANGAL, 506 004 5 BANDELA DINAKAR B RAJESWARA RAO COLLEGE OF ENGINEERING GUIDY SARDHAR 98 ZONE-5 RAJEWDRA PRASAD PATEL ROAD, ANNA UNIVERSITY CHENNAI 600 025 6 CHINTA AVINASH CHINTA MICHAEL JAWAHARLAL NERHU TECHNOLOGY 98 ZONE-5 UNIVERSITY, KUKATPALLY, HYDERABAD, TELANGANA 500 085 7 MEKALA LAVAN MEKALA CHANDRAIAH JNTU COLLEGE OF ENGINEERING KALIKIRI, 97.9 ZONE-5 KUMAR KALIKIRI 517 234, CHITTOOR (DT), ANDHRA PRADESH 8 NATYALA PRAVEEN NATYALA ANIL KUMAR KU COLLEGE OF ENGINEERING & 97.9 ZONE-5 KUMAR TECHNOLOGY KAKATIYA UNIVERSITY CAMPUS, VIDYARANYAPURI, 506 001 9 LAKKEPOGU LAKKEPOGU KOTAIAH SARDAR VALLABHBHAI NATIONAL 97.7 ZONE-5 ANUDEEP BABU INSTITUTE OF TECHNOLOGY, ICHCHHANATH SURAT-7, GUJARAT 395 007 10 PITTALA ESHWAR PANAND VASAVI COLLEGE OF ENGINEERING (A), 97.6 ZONE-5 HYDERABAD, IBRAHIMBAGH 500 031 11 JOGGARI CHANDRA -

District Census Handbook, Prakasam, Part XII-A & B, Series-2
CENSUS OF INDIA 1991 SERIES 2 ANDHRA PRADESH DISTRICT CENSUS HANDBOOK PRAKASAM PARTS XII - A It B VILLAGE It TOWN DIRECTORY VILLAGE" TOWNWISE PRIMARY CENSUS ABSTRACT DIRECTORATE OF CENSUS OPERATIONS ANDHRA PRADESH PUBLISHED BY THE GOVERNMENT OF ANDHRA PRADESH 1995 iF 0 R EW 0 R D publication of the District Census Handbooks (DCHs) was initiated ,after the 1951 Census and is continuing since then with some innovations/modifications after each decennial Census. This is the most valuable district level publication brought out by the Census Organisation on behalf of each State Govt./ Uni~n Territory a~ministratio~. It Intc: al'ia. Provides data/information on some of the basIc demographiC and socia-economic characteristics and on the availability of certain important civic amenities/facilities in each village and town of the respective districts. This publication has thus proved to' be of immense utility to the planners., administrators, academicians and researchers. The scope of the DCH was initially confined to certain important census tables on population, economic and socio-cultural aspects as also the Primary Census Abstract (PCA) of each village and town (ward wise) of the district. The DCHs published after the 1961 Census contained a descriptive account of the district, administrative statistics, census tables and Village' and Town Directories including PCA. After the 1971 Census, two parts of the District Census Handbooks (Part-A comprising Village and Town Directories and Part-B comprising, Village and Town PCA) were released in all the States and Union Territories. The thnd Part (C) of the District Census Handbooks comprising administrative statistics and district census tables, which was also to be brought out, could not be published in many States/UTs due to considerable delay in compilation of relevant material. -
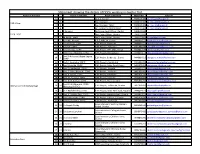
Statement Showing the Details of Ddos Working in Guntur Dist
Statement showing the details of DDOs working in Guntur Dist. Name of the Dept Name of the DDO Place of Working Mobile No email id 1 1 Dy.E.E, Guntur 9100121406 [email protected] 2 2 Exe. Engineer 9100121401 [email protected] R.W.S Dept 3 3 Exe. Engineer, Tenali 9100121403 [email protected] 4 4 Exe. Engineer, Narasaraopet 9100121402 [email protected] 1 K.Suhasini Dist.Coop.Audit Officer, Guntur 9100109186 Coop. Dept 2 Dist. Coop. Officer, Guntur 9100109185 5 3 M.Abdul Latieff Divl. Coop. Officer, Guntur 9985720889 [email protected]; 1 Kum.M.J.Nirmala P.D,D.W&C.W, Guntur 9440814511 [email protected] 6 2 S.V.Ramana, CDPO ICDS Project, Macherla 9440814512 [email protected] 7 3 J.Srivalli, CDPO ICDS Project, 75 Tyallur 9491051599 [email protected] 8 4 Smt.B.Sailaja, CDPO ICDS Project OPP: AMC, Tenali 9440814520 [email protected] 9 5 Smt.B.V.S.L.Bharathi, CDPO ICDS Project, Mangalagiri 9440814514 [email protected] Smt.Sk Ruksana Sultana Begum, 10 6 CDPO ICDS Project (Urban 1), , Guntur 9440814513 [email protected] 11 7 Smt.A. Anuradha, CDPO ICDS Project, Amruthalur 9491051598 [email protected] 12 8 Smt.B.Sujatha, CDPO ICDS Project, Main Road, Emani 9491051604 [email protected] 13 9 Smt.D.Geethanjali, CDPO ICDS Project, Bapatla 9440814516 [email protected] 14 10 Smt. G. Mary Bharathi, CDPO ICDS Project, Nallapdu 9491051601 [email protected] 15 11 Smt. B. Aruna, CDPO ICDS Project, Pallapatla 9491051597 [email protected] 16 12 Smt. -

NTR TRUST NEWS BULLETIN (No. 17)
NTR TRUST NEWS BULLETIN (No. 17) We are happy to share with you NTR Trust’s e-News Bulletin for the months of January and February 2018. We welcome your valuable feedback. Hon’ble Vice President of India Sri M. Venkaiah Naidu & Hon’ble Chief Minister of Andhra Pradesh Sri. Nara Chandra Babu Naidu garu along with other delegates in the Inaugural ceremony of Navyandhra Pustaka Sambaralu, Vijayawada HIGHLIGHTS 1. Hon'ble Vice President of India Sri M. Venkaiah Naidu & Hon'ble Chief Minister of Andhra Pradesh Sri Nara Chandrababu Naidu inaugurated Navyandhra Pusthaka Sambaralu (NPS) in Vijayawada. NPS is a travelling book, cultural and literary exhibition that will tour all the 13 districts of Andhra Pradesh. NTR Trust in partnership with VBFS and Dept. of Lang & Culture, GoAP are organizing NPS. WE WORK THE TALK! ntrtrust.org|1 2. NTR Trust's calendar event, Legendary Blood Donation Drive (LBD) 2018 was inaugurated by Smt. Nara Bhuvaneswari garu, Smt. Nara Brahmani garu & Smt. Hema Budaraju of Facebook at NTR Trust Bhavan, Hyderabad on 18 January. We are proud to have organized LBD at more than 300 locations across India and partnered with over 150 Blood Banks. 3. NTR Trust Managing Trustee Smt. Nara Bhuvaneswari visited Thimmapuram village of Guntur district. She took part in various village development activities and also interacted with the residents. 4. On the occasion of Padmashri, Kalatapaswi Sri Kasinathuni Vishwanath garu’s 88th Birthday, NTR Trust has organized a Voluntary Blood Donation camp in collaboration with Suvarnabhoomi Developers and Telugu Film Chamber. HEALTH Trustees Smt. Nara Bhuvaneswari & Smt. -

District Census Handbook, Guntur, Part XII-A & B, Series-2
CENSUS OF INDIA 1991 SERIES 2 ANDHRA PRADESH DISTRICT CENSUS HANDBOOK GUNTUR PARTS XII - A &. B VILLAGE &. TOWN DIRECTORY VILLAGE It TOWNWISE PRIMARY CENSUS ABSTRACT R.P.SINGH OF THE INDIAN ADMINISTRATIVE SERVICE DIRECTOR OF CENSUS OPERATIONS ANDHRA PRADESH PUBLISHED BY THE GOVERNMENT OF ANDHRA PRADESH 1995 FOREWORD Publication of the District Census Handbooks (DCHs) was initiated after the 1951 Census and is continuing since then with .some innovations/modifications after each decennial Census. This is the most valuable district level publication brought out by the Census Organisation on behalf of each State Govt./ Uni~n Territory a~ministratio~. It Inte: alia Provides data/information on· some of the baSIC demographic and soclo-economlc characteristics and on the availability of certain important civic amenities/facilities in each village and town of the respective ~i~tricts. This pub~i~ation has thus proved to be of immense utility to the pJanners., administrators, academiCians and researchers. The scope of the .DCH was initially confined to certain important census tables on population, economic and socia-cultural aspects as also the Primary Census Abstract (PCA) of each village and town (ward wise) of the district. The DCHs published after the 1961 Census contained a descriptive account of the district, administrative statistics, census tables and Village and Town Directories including PCA. After the 1971 Census, two parts of the District Census Handbooks (Part-A comprising Village and Town Directories and Part-B com~iSing Village and Town PCA) were released in all the States and Union Territories. Th ri art (C) of the District Census Handbooks comprising administrative statistics and distric census tables, which was also to be brought out, could not be published in many States/UTs due to considerable delay in compilation of relevant material. -

In-Operative Accounts
List of unclaimed/ in-operative accounts 1 SAI BALAJI HOUSING (P) LTD SAI BALAJI NIVAS, DNO 4-5-4/8/C, NAVABHARAT NAGAR, III LANE, GUNTUR 2 SHINE CERAMICS PVT LTD SRI KRISHNA ESTATES,PRAKASAM ROAD, VIJAYAWADA DNO29-19-21, MOTHER & CHILD HOSPITAL, DORNAKAL ROAD, 3 MOTHER & CHILD HOSPITAL SURYARAOPET,VIJAYAWADA 4 SRI SRINIVASA ENTERPRISES PROP:G SAMBA SIVA RAO ,AJITH SINGH NAGAR, VIJAYAWADA 5 SREE SAI DURGA CONSTRUCTION HNO60-25-3, ROAD NO-3,SBICOLONY SIDDARTHA NAGAR, VIJAYAWADA 6 GURUKRUPA E-SIBAR CABEL NET 26-17-75, SIBAR TOWERS, BESANT ROAD, VIJAYAWADA 7 OSHOTECH WEIGHING SYSTEMS 11-4-90/A, HUDDUSAHIB STREET, VIJAYAWADA VETAPALEM MAIN ROAD,NEAR ANKAMMA TEMPLE, UNADAVALLI,GUNTUR 8 GOGINENI VIJAYA CHAND DIST USHA COMPLEX, DUBAGUNTAVARI STREET, ELURU ROAD, 9 ANDHRA TRADE CENTRE VIJAYAWADA 10 SRINVASA ENTERPRISES PROP:JSRINIVASA RAO, KANCHIKACHERLA PO&MD, KRISHNA DIST DNO23-6-35, KOMMURUVARI STREET, SATYANARAYANA PURAM, 11 VUMA HOLIDAY INNS LIMITED VIJAYAWADA KRISHNA DIST 12 M/SRAMAKRISHNA POULTRY FARMS TUKKULURU (POST) (VILLAGE) ,KRISHNA DIST 13 M/S MURALI KRISHNA TRADERS P/O AMURALI MOHAN RAO,OPP BABU OPTICALS, NUZIVID 14 SRI RAMAKRISHNA CLAY PRODUCT ANNAVARAM (POST)(VILLAGE) NUZVID (MD) 15 MANIKANTA TRADERS AGIRIPALLI (VILLAGE) (MANDAL) KRISHNA (DIST) 16 HARITHA INFORMATICS PVT LTD KATRENIPADU POST, MUSUNURU MANDAL , KRISHNA DIST 17 SRI VENKATESWARA ENTERPRISES PVENKATESWARA RAO, SRI VENKATESWARA ENTERPRISES, TANUKU 18 SK NAGUL MEERA SAHEB S/O CHINNA MASTAN SHEB,MELLAMPUDI, TADEPALLI , GUNTUR DIST 19 MOHAMMAD SALEEMUDDIN D/NO 12-39 ,GANDHI