Get the Cutter Edge Free Vol
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Wal-Mart: a New Center of Gravity for Payments
News April 26, 2010 • Issue 10:04:02 Industry Update .......................................14 Job rebound in acquiring? ........................48 Processors press industry Wal-Mart: A new center for more standards ...............................49 Retailer wanted breach of gravity for payments connection hushed up ...........................51 Trade Association News The ETA, celebrating 20 years in style .....84 Features GS Advisory Board: Positive signs and actions – Part 3 ..........32 SellingPrepaid: Prepaid in Brief ....................................38 Consumers in the prepaid driver's seat .............................41 Security standard in store for stored-value ....................................42 Research Rundown...................................80 Views ACH grows, B2B payments plod along By Patti Murphy, The Takoma Group .......24 The cost of credit card processing – past and present By Jared Isaacman al-Mart Stores Inc. is unique in the payments industry. It is the United Bank Card Inc. ...........................26 only financial services provider that allows a customer to pay The 'Wal-Mart case' revisited bills electronically, transfer money to friends and relatives, and By Brandes Elitch, CrossCheck Inc. .........28 W purchase an affordable set of bath towels. That combination of discounted retail goods with equally inexpensive financial products has proven Education a formidable business model. Street SmartsSM Pundits may haggle over the degree of Wal-Mart's influence on the industry, but No ISO demise with niche markets an impact it has had – not only in driving down fees across the prepaid card sector, for example, but also in fostering a deeper relationship between service By Ken Musante ...................................60 providers and customers. And yet the Bentonville, Ark.-headquartered com- Contractual pricing pitfalls pany's role as a payments trendsetter (and its prominence generally) has been By Adam Atlas, Attorney at Law..............64 over 30 years in the making. -

Seduced by Success Seduced by Success Customer
LEADERSHIP OCTOBER 2007 ExcellenceTHE MAGAZINE OF LEADERSHIP DEVELOPMENT, MANAGERIAL EFFECTIVENESS, AND ORGANIZATIONAL PRODUCTIVITY Don’t You Be Seduced by Success Customer As Boss Why Develop Your Leaders? YouYou CanCan HaveHave MoreMore Pat Lencioni Leadership Coach SatisfactionSatisfaction “Leadership Excellence is an exceptional way to learn and then apply the best and latest ideas in the field of leadership.” —WARREN BENNIS, AUTHOR AND USC PROFESSOR OF MANAGEMENT w w w . L e a d e r E x c e l . c o m LEADERSHIP ™ THE MAGAZINE OF LEADERSHIP DEVELOPMENT, MANAGERIAL EFFECTIVENESS, AND ORGANIZATIONAL PRODUCTIVITY VOL.Excellence 24 NO. 10 OCTOBER 2007 On the Edge Today’s leader, like this mountain lion, stays poised to pounce on opportunity that presents itself in the market to gain and sustain a competitive advantage. HOWARD GARDNER Use an evidence- MICHAEL G. WINSTON DANIEL BURRUS Good Work based approach. .7 Why Develop Leaders? Seek Advantage Internalize the need This is your only Keeping up is SCOTT J. ALLEN to act responsibly. .3 competitive advantage. .12 a fool’s game. 16 Effective Leadership ILEEN IGHE ROBERT GALFORD Assess the effectiveness E T ROBERT L. DILENSCHNEIDER Positive Influence of your current Leadership Development Keep Up, Move Ahead leader development. .8 Think about your It won’t happen Don’t just imitate: leadership legacy. .4 on cruise control. .13 you must innovate. .17 RON MCMILLAN PATRICK LENCIONI MICHAEL HAMMER Master Influencers TOM KOLDITZ Satisfaction They ensure the Customer Economy In Extremis Leaders Yes, you can get more vital behaviors. .9 Attend to the agenda Can you and your of it at work. -

Doing Business in the Mobile Channel
News July 12, 2010 • Issue 10:07:01 Industry Update .......................................14 Security standards lifecycle extended .........42 Congress approves interchange Doing business in regulation amendment ..........................44 New ACH rules in step with Check 21 .......47 the mobile channel Trade Association News: ETA unveils new logo ............................76 By Patti Murphy MWAA to present strategies The Takoma Group for changing times ................................76 verything is mobile these days, and the business of payments is no Features exception: Juniper Research Ltd., a high-tech research firm based in the U.K., forecasts that nearly half of all mobile telephone users worldwide GS Advisory Board: E will be using mobile devices to initiate payments by 2014. Meanwhile, the online auction site eBay Inc. claims it handled $500 million in mobile pay- Merchant retention, taking ments in 2009; this year that number is expected to triple. the initiative – Part 1 .............................24 SellingPrepaid: At present, the bulk of mobile payments occur outside the United States. In Prepaid in brief ....................................33 Kenya, for example, M-Pesa, a mobile banking and payments product provided FinCEN seeks comprehensive by mobile operator Safaricom Ltd., managed to sign up 20 percent of Kenyans who just a few years ago were unbanked. AML framework....................................34 Prepaid largely spared in fi nal In Haiti, where 90 percent of adults had no bank accounts just last year, a Durbin Amendment ..............................38 project is underway to build a mobile money system for the entire nation. Views The U.S. Agency for International Development and the Bill & Melinda Gates Foundation kicked in money and expertise to create the system. -

Innovation in a Competitive World
2016 VOL. 7 Strategies for Transforming Your KNOW Business & Future WHAT’S NEXT by Daniel Burrus CEO of Burrus Research ͮ 10 Technology-Driven Hard Trends Shaping 2016 ͮ The Anticipatory Organization™ Model ͮ Be the Disruptor, not the Disrupted ͮ Increasing Your Sales with Helpful & Meaningful Content ͮ The Merits of Innovation in a Competitive World ͮ Are We Educating Students for a Future That Doesn’t Exist? ͮ What Mobile Trends Should You Be Getting Behind? ͮ Anticipatory Healthcare: Predict and Prevent ͮ Everyday Innovation Can Produce Big Results ͮ The Power of Certainty “ After reading Flash Foresight and applying the principles to our business, in less than a year we have been able to double our revenues and increase the value of our company by a factor of four, and we feel the biggest impact is yet to come.” — ARNIE BELLINI, CEO, CONNECTWISE HIGH PRAISE FOR FLASH FORESIGHT “I love this book! It’s as much fun to read as it is inspiring to learn from. Buy it, read it, and put it to use—in a flash!” — ALAN M. WEBBER, CO-FOUNDER, FAST COMPANY MAGAZINE “With the increasing pressure to innovate and gain competitive advantages, leaders from start-ups to multi-national organizations will find deep insights from the seven principles of Flash Foresight. It will change the way you think about your current obstacles and open your mind to limitless new opportunities.” — TERRY JONES, FOUNDER, TRAVELOCITY.COM AND FOUNDING CHAIRMAN OF KAYAK.COM “Full of provocative insights and powerful strategies from a veteran entrepreneur. The ‘Take Your Biggest Problem — and Skip It’ chapter alone is worth the price of admission.” HARDCOVER AND KINDLE VERSION — STEVE FORBES, EDITOR-IN-CHIEF OF FORBES AND CEO OF FORBES, INC. -

Brought to You by Burrus Research
2015 VOL. 6 Strategies for Transforming Your KNOW Business & Future WHAT’S NEXT by Daniel Burrus CEO of Burrus Research ͮ 25 Game-Changing Hard Trends That Will Create Both Disruption and Opportunity on a Global Level ͮ Forget Lean and Agile – It’s Time to be Anticipatory ͮ Essential Secrets to Retaining Your Best Employees ͮ Disruptive Technologies That Will Impact Us The Most in the Next Decade ͮ The New Golden Rule of Business ͮ Big Data: Do You Have a Plan? ͮ The Internet of Things Far Bigger Than Anyone Realizes ͮ Strategic Plans Are Obsolete! ͮ The Science and Art of Every Profession ͮ Are You Collaborating or Cooperating? The Answer Will Increasingly Influence Your Success “ After reading Flash Foresight and applying the principles to our business, in less than a year we have been able to double our revenues and increase the value of our company by a factor of four, and we feel the biggest impact is yet to come.” — ARNIE BELLINI, CEO, CONNECTWISE HIGH PRAISE FOR FLASH FORESIGHT “I love this book! It’s as much fun to read as it is inspiring to learn from. Buy it, read it, and put it to use—in a flash!” — ALAN M. WEBBER, CO-FOUNDER, FAST COMPANY MAGAZINE “With the increasing pressure to innovate and gain competitive advantages, leaders from start-ups to multi-national organizations will find deep insights from the seven principles of Flash Foresight. It will change the way you think about your current obstacles and open your mind to limitless new opportunities.” — TERRY JONES, FOUNDER TRAVELOCITY.COM AND CHAIRMAN OF KAYAK.COM “Full of provocative insights and powerful strategies from a veteran entrepreneur. -
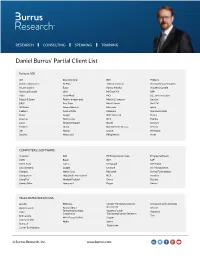
Daniel Burrus' Partial Client List
RESEARCH CONSULTING SPEAKING TRAINING Daniel Burrus’ Partial Client List Fortune 500 3M Dow Chemical IBM Pillsbury Abbott Laboratories DuPont Johnson Controls PricewaterhouseCoopers Alcatel-Lucent Eaton Konica Minolta Procter & Gamble American Express eBay McGraw Hill SAP AT&T ExxonMobil MCI S.C. Johnson & Sons Bausch & Lomb Fidelity Investments Merck & Company Sara Lee BASF First Data Merrill Lynch Shell Oil BP Global General Electric Microsoft Sprint Cadbury General Mills Motorola Starwood Hotels Chase Google NBC Universal Texaco Chevron Harris Corp. NCR Toshiba Cisco Hewlett Packard Nestle Unilever Citibank Hilton Northwestern Mutual Verizon Dell Honda Oracle Whirlpool Deloitte Honeywell Philip Morris Xerox COMPUTERS | SOFTWARE Autodesk Dell HP Enterprise Services Progress Software CDW Epson IBM SAP Check Point Fujitsu Intergraph SSA Global Cisco Systems Google Lexmark Sun Microsystems Compaq Harris Corp. Microsoft Symbol Technologies Compuware Help Desk International NCR Teradata CompTIA Hewlett Packard Oracle Toshiba ConnectWise Honeywell Paypal Unisys ! TELECOMMUNICATIONS ACUTA Motorola Oregon Telecommunications Univision Communications Association Alcatel Lucent National Rural Verizon Telecommunications Society of Cable AT&T Vodafone Cooperative Telecommunication Engineers Bell Canada Zain MTN Group Limited SingTel Comcast Cable Nokia Sprint InterCall Technicolor Lucent Technologies © Burrus Research, Inc. www.burrus.com RESEARCH CONSULTING SPEAKING TRAINING Daniel Burrus’ Partial Client List Continued FINANCIAL Accenture Deloitte -

About Daniel Burrus Global Futurist | Strategic Advisor | Best-Selling Author
ABOUT DANIEL BURRUS GLOBAL FUTURIST | STRATEGIC ADVISOR | BEST-SELLING AUTHOR Daniel Burrus is considered one of the World’s Leading Futurists on Global Trends and Disruptive Innovation. The New York Times has referred to him as one of the top three business gurus in the highest demand as a speaker. He has delivered over 3,000 keynote speeches worldwide and is a strategic advisor to executives from Fortune 500 companies, helping them to develop game-changing strategies based on his proven methodologies for capitalizing on technology innovations and their future impact. His client list includes Lockheed Martin, Verizon, Microsoft, VISA, Deloitte, Google, Procter & Gamble, KPMG, Honda, FedEx and the U.S. Department of Defense. He is the author of seven books, including the New York Times and Wall Street Journal bestseller Flash Foresight, and his latest book, The Anticipatory Organization, is an Amazon No. 1 bestseller. Burrus is also a featured writer with millions of monthly readers on the topics of disruptive innovation, exponential change and the future for a variety of publications, including CNBC, Huffington Post and Wired Magazine. He has been the featured subject of several PBS television specials and has appeared on programs such as CNN, Fox Business and Bloomberg. Burrus has been quoted in a variety of publications, including Harvard Business Review, The Wall Street Journal, Financial Times, Fortune and Forbes. Burrus is an innovative entrepreneur who has founded six businesses, four of which were U.S. national leaders in the first year. He is the CEO of Burrus Research, a research and consulting firm that monitors global advancements in technology-driven trends to help clients profit from technological, social and business forces that are converging to create enormous, untapped opportunities. -
By Daniel Burrus CEO of Burrus Research
VOLUME 9 Strategies for Transforming Your KNOW Business & Future WHAT’S NEXT by Daniel Burrus CEO of Burrus Research ͮ Daniel Burrus’ Top 20 Technology-Driven Hard Trends Shaping the Future ͮ What’s the Secret to the Next Big Thing? Anticipation ͮ Accelerate Growth Using Hard Trends ͮ 3 Steps to Build a Stronger Team ͮ Agility Levels the Playing Field Anticipation Changes the Game ͮ Change and Transformation—Knowing the Difference to Accelerate Growth ͮ Owning Innovation in Your Organization ͮ Is Your Organizational Futureview Aligned? ͮ Redefining Risk ͮ When It Comes to Trends, Know Which Ones Will Happen ͮ Certainty—The Ultimate Closing Tool ͮ Will Artificial Intelligence Replace Human Intelligence? TO GET YOUR COPY, VISIT WWW.THEAOBOOK.COM HIGH PRAISE FOR THE ANTICIPATORY ORGANIZATION “If you’re in business and you’re not thinking about disruption, you’re not paying attention. And if you haven’t read The Anticipatory Organization, you haven’t learned how to think about—and get ahead of—the disruption that’s headed your way. Read this book!” — ALAN M. WEBBER, CO-FOUNDER, FAST COMPANY MAGAZINE “The Anticipatory Organization provides critical insights into trends shaping the future of business. Daniel Burrus delivers a powerful vision for driving growth and innovation within a company. This is a must read for emerging digital leaders within industry.” — JUDE SCHRAMM, CIO OF GENERAL ELECTRIC COMPANY – AVIATION “The Anticipatory Organization provides a compelling methodology to enable each of us to identify future trends and meaningful opportunities HARDCOVER AND KINDLE VERSION in a time of hyper change. -

Alert!August 2010 | Vol
gfhgfhgfhgf Alert!August 2010 | Vol. 50 | No. 08 Emerging Technology Technology/Software Directory iPad for MR Social Media & Research MRA’s Alert! Magazine - August 2010 1 With so many information sources, attending industry events is no longer a given. But face to face meetings can be “incredibly productive when the program and people are important. MRA’s First Outlook Conference will be that kind of event. The workshop on mining social media will provide an in-depth look at how to fi nd and listen to online “conversations, and even help you build a social media monitoring dashboard. This is real quality. “ “ Join me in Orlando at the Walt “ Disney World Swan Resort, an exciting place “to develop relationships. Janet Baldi Vice President, Data Collection RTi Research MRA FIRST OUTLOOK CONFERENCE INSIGHTS & STRATEGIES FOR THE ENTIRE PROFESSION NOVEMBER 2-4 2010 ORLANDO MRA FIRST OUTLOOK CONFERENCE INSIGHTS & STRATEGIES FOR THE ENTIRE PROFESSION NOVEMBER 2-4 2010 ORLANDO www.mra-net.org/foc2 | 860.682.1000 MRA’sMRA’s Alert! Alert! Magazine Magazine - August - July 2010 August 2010 Alert!August 2010 | Vol. 50 | No. 08 With so many information sources, attending industry events is no longer a given. But face to face meetings can be “incredibly productive when the program and people are important. MRA’s 7 Social Media Research: First Outlook Conference will be that From Buzz to Biz kind of event. By Annie Pettit, Ph.D. Emerging Technology The iPad as a Data Technology/Software Directory The workshop on mining social media 16 Collection Device iPad for MR Social Media & Research will provide an in-depth look at By Jerry Arbittier how to fi nd and listen to online conversations, and even help you “ Don’t Forget Your “Place” When On This Month’s Cover build a social media monitoring 19 Creating a Customer Satisfaction dashboard. -

About Daniel Burrus Global Futurist | Strategic Advisor | Best-Selling Author
ABOUT DANIEL BURRUS GLOBAL FUTURIST | STRATEGIC ADVISOR | BEST-SELLING AUTHOR Daniel Burrus is considered one of the World’s Leading Futurists on Global Trends and Innovation. The New York Times has referred to him as one of the top three business gurus in the highest demand as a speaker. He has delivered over 2,800 keynote speeches worldwide, and is a strategic advisor to executives from Fortune 500 companies, helping them to develop game-changing strategies based on his proven methodologies for capitalizing on technology innovations and their future impact. His client list includes companies such as Microsoft, GE, American Express, Google, Deloitte, Procter & Gamble, Honda, and IBM. Burrus is also a featured writer with millions of monthly readers on the topics of innovation, change and the future for CNBC, Huffington Post, and Wired Magazine to name a few. He is the author of seven books, including the New York Times and Wall Street Journal best-seller Flash Foresight, as well as the international best-seller Technotrends. His latest book, The Anticipatory Organization: Turn Disruption and Change Into Opportunity and Advantage (2017), is an Amazon #1 Hot New Release for Business He has been the featured subject of several PBS television specials and has appeared on networks such as CNN, Fox Business, and Bloomberg, and is quoted in a variety of publications, including Harvard Business Review, The Wall Street Journal, Financial Times, Fortune, and Forbes. Burrus is an innovative entrepreneur who has founded six businesses, four of which were national leaders in the United States in the first year. He is the CEO of Burrus Research, a research and consulting firm that monitors global advancements in technology-driven trends to help clients profit from technological, social and business forces that are converging to create enormous, untapped opportunities. -

Daniel Burrus Onesheet
Delivered by One of the World’s Daniel Burrus has given over 2,800 keynote addresses that motivate and inspire audiences to take positive actions based on his breakthrough insights. Every talk he gives is customized to your industry and your Leading Technology Forecasters organization with content that is always extremely timely, motivating, actionable and focused on turning rapid change into competitive and Business Strategists advantages. Perhaps that’s why the majority of his clients invite him back to speak again and again. World-famous for his 30+ year record of accurately predicting the future of technological change and its direct impact on the business world. Author of six books, including The New York Times and Wall Street Journal best-seller Flash Foresight: How To See the Invisible and Do Recent Work The Impossible. Named by The New York Times as one of America’s top three business “gurus” in the highest demand as a speaker. When IBM launched IBM Global Business Services with their top 40 industry experts to plan a game-changing future for A strategic advisor to leaders from Fortune 500 companies including IBM, IBM, the only outside resource they used was Daniel Burrus. American Express, Toshiba and Disney. When Vodafone launched its Global Mobile Enterprise service A featured blogger on the topics of innovation, change and thefuture for to Fortune 200 companies, they chose Daniel Burrus to deliver CNBC, Huffington Post, Examiner and Wired Magazine. the message to C-level executives in multiple national events. When Deloitte gathered leaders from China and SE Asia for Best-Selling Author a major forecasting event, they chose Daniel Burrus. -

The Anticipatory Organization
VOLUME 10 Strategies for Transforming Your KNOW Business & Future WHAT’S NEXT by Daniel Burrus CEO of Burrus Research ͮ Digital Disruption and Your Workforce ͮ Innovation: Everyone’s Responsibility ͮ Will A.I. Disrupt Your Profession? ͮ The Power of Anticipatory Customer Service ͮ 5 Sales Strategies Not Found in How-to Books ͮ Elevate Your Success with Five Simple Steps ͮ Success in Manufacturing with Multigenerational Collaboration ͮ Hard Trends Are Easy to Find If You Know Where to Look ͮ Protecting Your Intellectual Property, Products and Brand ͮ 4 Questions of World-Class Entrepreneurs ͮ 12 Technology Categories That Will Transform Careers and Create New Opportunities TO GET YOUR COPY, VISIT WWW.THEAOBOOK.COM HIGH PRAISE FOR THE ANTICIPATORY ORGANIZATION “If you’re in business and you’re not thinking about disruption, you’re not paying attention. And if you haven’t read The Anticipatory Organization, you haven’t learned how to think about—and get ahead of—the disruption that’s headed your way. Read this book!” — ALAN M. WEBBER, CO-FOUNDER, FAST COMPANY MAGAZINE “The Anticipatory Organization provides critical insights into trends shaping the future of business. Daniel Burrus delivers a powerful vision for driving growth and innovation within a company. This is a must read for emerging digital leaders within industry.” — JUDE SCHRAMM, CIO OF GENERAL ELECTRIC COMPANY – AVIATION “The Anticipatory Organization provides a compelling methodology to enable each of us to identify future trends and meaningful opportunities HARDCOVER AND KINDLE VERSION in a time of hyper change. Simple in its approach, yet truly transformational in its results.” — JOEL DOHERTY, HEAD OF GLOBAL STRATEGY AND BUSINESS DEVELOPMENT, EPSON CLOUD/EPSON AMERICA AUDIO VERSION “The Anticipatory Organization teaches you how to accelerate growth by jumping ahead of the competition with low risk.