A Private Cloud Architecture Designed for High Usability
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Archangel Gabriel Parish
ARCHANGEL GABRIEL PARISH THESECONDSUNDAYOFORDINARYTIME JANUARY 17, 2021 Mass and Confession Times SAINT MALACHY HOLY TRINITY SAINTMARY,HELPOF CHURCH CHURCH CHRISTIANSCHURCH 343 Forest Grove Rd 5718 Steubenville Pike 1011 Church Ave Coraopolis, PA 15108 Robinson Township, PA 15136 McKees Rocks, PA 15136 HOLY MASS HOLY MASS HOLY MASS Saturday — 4 PM Saturday — 5 PM Saturday — 6 PM Sunday — 8 AM, Sunday — 10 AM, 12:30 PM, 7 PM Sunday — 11 AM 10 AM (outdoor) Mon to Fri — 6:30 PM Mon to Wed — 9:30 AM Thurs to Sat — 8:30 AM RECONCILIATION RECONCILIATION RECONCILIATION SATURDAY, 11 AM - 12 PM MON-FRI,5:30PM-6:15PM SUNDAY,9:30AM-10:30AM Administrative Office: 412-787-2140 Website: www.archangelgabrielparish.org Email: [email protected] Sacramental emergencies: 412-787-2140 x2 WHAT YOU’LL FIND IN THIS WEEK’S BULLETIN Sunday, January 17, 2021 Table of contents, COVID Mass protocols.........................................Page 2 Sunday Mass worship aid..............................................................Pages 3-7 Message from Father Dave..............................................................Pages 8-9 This week’s Mass intentions...............................................................Page 10 This week’s calendar, Sunday Mass registration link.....................Page 11 Parish news, hymn history.................................................................Page 12 Faith Formation news, Baptism announcements............................Page 13 Intercessory prayer lists, Mass readings for the week...........................Page -

Based Services Using XRI-Based Apis for Enabling New E-Business
International Journal of E-Business Development May. 2013, Vol. 3 Iss. 2, PP. 64-74 An Approach for the Composition of Generic Cloud- Based Services Using XRI-Based APIs for Enabling New E-Business Antonio Celesti1, Francesco Tusa2, Massimo Villari3, Antonio Puliafito4 DICIEAMA, Università degli Studi di Messina Contrada Di Dio, S. Agata 98166, Messina, Italia [email protected]; [email protected]; [email protected]; [email protected] Abstract-Nowadays, cloud computing offers more and more business opportunities, and thanks to the concept of virtualization, different types of cost-effective Cloud-based services have been rising. Virtualization of computing, storage, and networking resources, and their interconnection is at the heart of cloud computing, hence enabling new E-Business scenarios. In such a context, APIs for enabling Cloud-based services are strongly required, nevertheless, methods, mechanisms and tools for exploiting virtualized resources and their utilization for developing anything as a service (*aaS) are still ad-hoc and/or proprietary in nature. In this paper, we discuss how to use an adaptive standard protocol, i.e., XRI, for enabling cloud service providers to arrange their own Cloud- based services, building them on top of the IaaS provided by other service providers. Keywords- Cloud Computing; Cloud Management; Federation; Service Composition; E-Business I. INTRODUCTION Today, cloud computing represents a tempting business opportunity for ICT operators of increasing their revenues [1,2]. The cloud ecosystem begins to be clearer and the role played by cloud service providers appears more defined than the past. Moreover, the number of new public, private, and hybrid clouds rising all over the world is continually growing [3]. -

Micah at a Glance
Scholars Crossing The Owner's Manual File Theological Studies 11-2017 Article 33: Micah at a Glance Harold Willmington Liberty University, [email protected] Follow this and additional works at: https://digitalcommons.liberty.edu/owners_manual Part of the Biblical Studies Commons, Christianity Commons, Practical Theology Commons, and the Religious Thought, Theology and Philosophy of Religion Commons Recommended Citation Willmington, Harold, "Article 33: Micah at a Glance" (2017). The Owner's Manual File. 13. https://digitalcommons.liberty.edu/owners_manual/13 This Article is brought to you for free and open access by the Theological Studies at Scholars Crossing. It has been accepted for inclusion in The Owner's Manual File by an authorized administrator of Scholars Crossing. For more information, please contact [email protected]. MICAH AT A GLANCE This book records some bad news and good news as predicted by Micah. The bad news is the ten northern tribes of Israel would be captured by the Assyrians and the two southern tribes would suffer the same fate at the hands of the Babylonians. The good news foretold of the Messiah’s birth in Bethlehem and the ultimate establishment of the millennial kingdom of God. BOTTOM LINE INTRODUCTION QUESTION (ASKED 4 B.C.): WHERE IS HE THAT IS BORN KING OF THE JEWS? (MT. 2:2) ANSWER (GIVEN 740 B.C.): “BUT THOU, BETHLEHEM EPHRATAH, THOUGH THOU BE LITTLE AMONG THE THOUSANDS OF JUDAH, YET OUT OF THEE SHALL HE COME FORTH” (Micah 5:2). The author of this book, Micah, was a contemporary with Isaiah. Micah was a country preacher, while Isaiah was a court preacher. -

Open House March 20 1:30-3:30Pm the Weekend of March 20-21 There Will Be an Open March 27 1:30-3:30Pm House for the New Addition
March 14, 2021 Fourth Sunday in Lent ST. GABRIEL THE ARCHANGEL CATHOLIC CHURCH PARISH OFFICE PARISH CLERGY EMAIL 8755 Scarborough Drive Pastor, Fr. Kirk Slattery: [email protected] Colorado Springs, CO 80920 Father Don Billiard, OFM: [email protected] www.saintgabriel.net Deacon Juan Cabrera: [email protected] Office Hours: Monday-Friday Deacon Dave Geislinger: [email protected] 9:00 am-5:00 pm Deacon André Mason: [email protected] Phone: (719) 528-8407 Deacon Mike McGrady: [email protected] Fax: (719) 598-1696 Email: [email protected] “Go to Joseph! Have recourse with special confidence to St. Joseph, for his protection is most powerful, as he is the patron of the universal Church.” Blessed Pope Pius IX Mass Schedule Please See Mass Schedule on page 2. Sacrament of Reconciliation Please see Reconciliation schedule on page 2 . First Friday: 8am to noon. Eucharistic Adoration: Wednesday 8am to 6pm. Baptism Please call the office to schedule the sacrament or to register for the Baptism class. Our Baptism class is offered on the Second Saturday of the month from 8:30am-12:30pm and are offered in both English and Spanish. Marriage Preparation sessions must begin twelve months prior to marriage date. Please contact the office before any arrangements are made regarding the wedding. Permission Letter If you are in need of a permission letter for a sacrament or to be a Godparent, call or come to the office. Submit permission letter request 1 week prior to pick up. Sick or Homebound If you are homebound and wish to receive Eucharist please call the office and you will be referred to our Communion to Homebound/Nursing Home Ministry. -

Solemnity of the Nativity of John the Baptist
Solemnity of the Nativity of John the Baptist OPENING SONG: YE WATCHERS AND YE HOLY ONES Reading 2 Acts 13:22-26 Ye watchers and ye holy ones, bright seraphs, cherubim, In those days, Paul said: and thrones, raise the glad strain, Alleluia! “God raised up David as king; of him God testified, Cry out, dominions, princedoms, powers, I have found David, son of Jesse, a man after my own heart; virtues, archangels, angels' choirs: he will carry out my every wish. From this man’s descendants God, according to his promise, Refrain: has brought to Israel a savior, Jesus. Alleluia! Alleluia! John heralded his coming by proclaiming a baptism of repent- Alleluia! Alleluia! Alleluia! ance to all the people of Israel; and as John was completing his course, he would say, O higher than the cherubim, more glorious than the ‘What do you suppose that I am? I am not he. seraphim, lead their praises, Alleluia! Behold, one is coming after me; Thou bearer of th' eternal Word, most gracious, I am not worthy to unfasten the sandals of his feet.’ magnify the Lord: [Refrain] “My brothers, sons of the family of Abraham, and those others among you who are God-fearing, Respond, ye souls in endless rest, ye patriarchs and to us this word of salvation has been sent.” prophets blest, Alleluia! Alleluia! Ye holy twelve, ye martyrs strong, all saints triumphant, The Word of the Lord raise the song: [Refrain] Thanks be to God O friends, in gladness let us sing, supernal anthems Alleluia echoing, Alleluia! Alleluia! R. -

Jonah for Yom Kippur Afternoon Who Am I? “And the Word Of
Jonah for Yom Kippur Afternoon Who Am I? “And the word of the Eternal came to Yonah ben Amittai.” (Jonah 1:1) 1. Then he sent out a dove to see if the water had receded from the surface of the ground. But the dove could find nowhere to perch because there was water over all the surface of the earth; so it returned to Noah in the ark. He reached out his hand and took the dove and brought it back to himself in the ark. He waited seven more days and again sent out the dove from the ark. When the dove returned to him in the evening, there in its beak was a freshly plucked olive leaf! Then Noah knew that the water had receded from the earth. (Genesis 8:8-11) 2. That the Eternal spoke through his servant Jonah ben Amitai from Gat-Hepher (I Kings 14:25) 3. Abarbanel And he said to her, “Give me your son.” And he took him from her arms and carried him up into the upper chamber where he lodged, and laid him on his own bed. And he cried to the Eternal, “O Eternal my God, have you brought calamity even upon the widow with whom I sojourn, by killing her son?” Then he stretched himself upon the child three times and cried to the Eternal, “O Eternal my God, let this child's life come into him again.” And the Eternal listened to the voice of Elijah. And the life of the child came into him again, and he revived. -

Automated System and Service Monitoring with Openqrm and Nagios
Name: Matthias Rechenburg Email: [email protected] Organization: the openQRM project Copyright (C) 2007 Matthias Rechenburg This document is released under the GNU/GPL Automated system and service monitoring with openQRM and Nagios The first step to make sure all systems and services in a data centers are running well is to monitor them. A well-known, proven and widely used monitoring tool is Nagios which is available for openQRM in the flavor of an additional plugin. The second, also essential, step is the automatic handling of errors, what openQRM is famous for. The combination of the enhanced monitoring utility Nagios and the automated error-handling, high-availability and fail-over features of the openQRM data center management platform creates a powerful and dynamic environment which reduces down-time of systems and services in a modern data center to the minimum. Common data center scenarios and their challenges In a common data center setup there are different server “islands” for specific purposes as databases, web-servers, infrastructure and communication systems, network-devices, storage-servers, etc. Also, often there is a separation between production-, QA- and development environment. Each section of the data center has its own specific setup, mostly a very special, static installation, maintained by one or more administrators. To make it worse, each section may have different service-level-agreements (SLA) which generates additional complexity for the service- and system-monitoring infra- structure. Also common for data centers is that new systems are added sequentially while other systems are fully underutilized, just consuming power and producing heat. Turning to fully automated system- and service monitoring With the increasing number of systems and the resulting complexity the goal is to reach a level of fully automated service- and system-monitoring which is easy to setup and maintain and which provides an automated error-handling to gain high-availability at system- and service-level for the complete data center environment. -

Paas Solutions Evaluation
PaaS solutions evaluation August 2014 Author: Sofia Danko Supervisors: Giacomo Tenaglia Artur Wiecek CERN openlab Summer Student Report 2014 CERN openlab Summer Student Report 2014 Project Specification OpenShift Origin is an open source software developed mainly by Red Hat to provide a multi- language PaaS. It is meant to allow developers to build and deploy their applications in a uniform way, reducing the configuration and management effort required on the administration side. The aim of the project is to investigate how to deploy OpenShift Origin at CERN, and to which extent it could be integrated with CERN "Middleware on Demand" service. The student will be exposed to modern cloud computing concepts such as PaaS, and will work closely with the IT middleware experts in order to evaluate how to address service needs with a focus on deployment in production. Some of the tools that are going to be heavily used are Puppet and Openstack to integrate with the IT infrastructure. CERN openlab Summer Student Report 2014 Abstract The report is a brief summary of Platform as a Service (PaaS) solutions evaluation including investigation the current situation at CERN and Services on Demand provision, homemade solutions, external market analysis and some information about PaaS deployment process. This first part of the report is devoted to the current status of the process of deployment OpenShift Origin at existing infrastructure at CERN, as well as specification of the common issues and restrictions that were found during this process using different machines for test. Furthermore, the following open source software solutions have been proposed for the investigation of possible PaaS provision at CERN: OpenShift Online; Cloud Foundry; Deis; Paasmaster; Cloudify; Stackato; WSO2 Stratos. -

Rites of Maymar of Archangel Michael ﻣﯾﻣر رﺋﯾس اﻟﻣﻼﺋﮐﺔ اﻟﺟﻟﯾل ﻣﯾﺧﺎﺋﯾل
Rites of Maymar of Archangel Michael ميمر رئيس المﻻئكة الجليل ميخائيل Fr. Jacob Nadian St. Bishoy Coptic Orthodox Church of Toronto Stouffville, ON Canada 1 H.H. Pope Tawadros, II Pope and Patriarch of the See of St. Mark, The Coptic Orthodox Church In Egypt and Abroad 2 Rites of Maymar of Archangel Michael طقس ميمر رئيس المﻻئكة الجليل ميخائيل Table of Contents Part 1: The Archangel Michael ....................................................................................................4 1. What is Maymar? .................................................................................................................... 4 2. The Meaning of the Name “Michael” ..................................................................................... 4 3. The Archangel Michael in the Holy Bible .............................................................................. 5 Part 2: Miracles of Archangel Michael ........................................................................................9 Part 3: Rites of Maymar of Archangel Michael ........................................................................10 The Prayer of Thanksgiving...................................................................................................... 11 Verses of Cymbals .................................................................................................................... 14 Adam Verses of Cymbals (Sunday to Tuesday) ................................................................... 14 Watos Verses of Cymbals (Wednesday to Saturday) -

AMOS 44 Prophet of Social Justice
AMOS 44 Prophet of Social Justice Introduction. With Amos, we are introduced to the proclamation of Amos’ judgment, but rather in the first of the “writings prophets.” They did not only social evils that demand such judgment. preach but also wrote down their sermons. Preaching prophets like Elijah and Elisha did not write down Style. Amos’ preaching style is blunt, confrontational their sermons. In some books of the Bible, Amos and and insulting. He calls the rich ladies at the local his contemporaries (Hosea, Isaiah, etc.), are country club in Samaria “cows of Basham” (4:1). sometimes called the “Latter Prophets” to distinguish With an agricultural background, he uses symbols he them from the “Former Prophets” (Joshua, Samuel, has experienced on the land: laden wagons, roaring Nathan, etc.). lions, flocks plundered by wild beasts. Historical Context. One of the problems we DIVISION OF CHAPTERS encounter when dealing with the so-called “Latter Prophets” is the lack of historical context for their PART ONE is a collection of oracles against ministry. Since little or nothing is written in the surrounding pagan nations. These oracles imply that historical books about any of the prophets, with the God’s moral law applies not only to his chosen ones exception of Isaiah, scholars have depended on the but to all nations. In this series of condemnations, text of each prophetic book to ascertain the historical Judah and Israel are not excluded (chs 1-2). background of each of the prophets. Some of the books provide very little historical information while PART TWO is a collection of words and woes against others give no clues at all. -

The Needs of Virtual Machines Implementation in Private Cloud Computing Environment
THE NEEDS OF VIRTUAL MACHINES IMPLEMENTATION IN PRIVATE CLOUD COMPUTING ENVIRONMENT Edy Kristianto Jurusan Teknik Informatika, Fakultas Teknik dan Ilmu Komputer, Universitas Kristen Krida Wacana Jl. Tanjung Duren Raya no. 4, Jakarta Barat, 11470 [email protected] ABSTRACT The Internet of Things (IOT) becomes the purpose of the development of information and communication technology. Cloud computing has a very important role in supporting the IOT, because cloud computing allows to provide services in the form of infrastructure (IaaS), platform (PaaS), and Software (SaaS) for its users. One of the fundamental services is infrastructure as a service (IaaS). This study analyzed the requirement that there must be based on a framework of NIST to realize infrastructure as a service in the form of a virtual machine to be built in a cloud computing environment. Keywords: cloud computing, virtual machine, virtualisation, iaas ABSTRAK The Internet of Things (IoT) menjadi tujuan perkembangan teknologi informasi dan komunikasi. Komputasi awan memiliki peranan yang sangat penting dalam mendukung terjadinya IoT, karena komputasi awan memungkinkan menyediakan layanan baik berupa infrastuktur (IaaS), platform (PaaS), dan perangkat lunak (SaaS) bagi para penggunanya. Salah satu layanan yang mendasar adalah infrastruktur sebagai layanan (IaaS). Penelitian ini menganalisa kebutuhan yang harus ada berdasarkan kerangka kerja dari NIST untuk mewujudkan infrastruktur sebagai layanan dalam bentuk mesin virtual yang akan dibangun dalam lingkungan komputasi awan. Kata kunci: komputasi awan, mesin virtual, virtualisasi, iaas The Needs of Virtual Machines.… (Edy Kristianto) 525 PENDAHULUAN Perkembangan teknologi informasi mengarah pada The Internet of Things (IoT) dengan meningkatnya penggunaan smartphone dalam kehidupan manusia untuk berkomunikasi dan akses internet. -
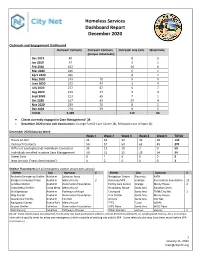
Homeless Services Dashboard Report December 2020
Homeless Services Dashboard Report December 2020 Outreach and Engagement Dashboard Outreach Contacts Outreach Contacts Outreach Line Calls Street Exits (unique individuals) Dec 2019 40 8 3 Jan 2020 97 2 1 Feb 2020 102 14 6 Mar 2020 226 6 1 April 2020 306 8 2 May 2020 243 70 9 9 June 2020 272 97 3 9 July 2020 277 67 5 7 Aug 2020 213 57 3 4 Sept 2020 213 65 7 1 Oct 2020 167 69 39 4 Nov 2020 239 70 8 1 Dec 2020 274 59 9 5 TOTAL 2,395 112 53 • Clients currently engaged in Case Managementi: 34 • December 2020 street exit destinations: Orange Family Care Center (4), Relocation out of state (1) December 2020 Data by Week Week 1 Week 2 Week 3 Week 4 Week 5 TOTAL Hours on Site 24 32 32 32 20 140 Outreach Contacts 50 57 60 62 45 274 Different (unduplicated) Individuals Contacted 35 12 10 2 0 59 Individuals enrolled in active Case Management 30 31 35 35 34 34 Street Exits 0 1 4 0 0 5 New Arrivals ("new client intakes") 1 2 0 0 0 3 Shelter Placements (of all emergency shelter street exits above) Shelter City Operator # Shelter City Operator # Anaheim Emergency Shelter Anaheim Salvation Army Navigation Center Placentia PATH Bridges at Kraemer Place Anaheim Mercy House 2 Roomkey/VPS multiple Illumination Foundation 23 La Mesa Shelter Anaheim Illumination Foundation Family Care Center Orange Mercy House 4 Costa Mesa Shelter Costa Mesa Mercy House Hospitality House Santa Ana Salvation Army Via Esperanza Anaheim Pathways of Hope Courtyard Santa Ana TMM/City Net 1 Way Shelter Anaheim Illumination Foundation Link Shelter Santa Ana Mercy House Quarantine Facility Anaheim City Net Armory Santa Ana City Net Navigation Center Buena Park Mercy House TTES Tustin OCRM Airport Shelter Fullerton Illumination Foundation SAFE Place Santa Ana WISE Place Safe Parking Fullerton Pathways of Hope Other Shelters various various 2 (Note: Some clients have documented community ties (last permanent address, school district enrollments, id, employment history, etc.) in multiple cities which qualify them for entry into emergency shelters outside of existing city and/or SPA.