Pmview Pro User's Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tools and Prerequisites for Image Processing
Tools and Prerequisites for Image Processing EE4830 Digital Image Processing http://www.ee.columbia.edu/~xlx/ee4830/ Lecture 1, Jan 26 th , 2009 Part 2 by Lexing Xie -2- Outline Review and intro in MATLAB A light-weight review of linear algebra and probability An introduction to image processing toolbox A few demo applications Image formats in a nutshell Pointers to image processing software and programming packages -3- Matlab is … : a numerical computing environment and programming language. Created by The MathWorks, MATLAB allows easy matrix manipulation, plotting of functions and data, implementation of algorithms, creation of user interfaces, and interfacing with programs in other languages. Main Features: basic data structure is matrix optimized in speed and syntax for matrix computation Accessing Matlab on campus Student Version Matlab + Simulink $99 Image Processing Toolbox $59 Other relevant toolboxes $29~59 (signal processing, statistics, optimization, …) th CUNIX and EE lab (12 floor) has Matlab installed with CU site- license -4- Why MATLAB? Shorter code, faster computation Focus on ideas, not implementation C: #include <math.h> double x, f[500]; for( x=1.; x < 1000; x=x+2) f[(x-1)/2]=2*sin(pow(x,3.))/3+4.56; MATLAB: f=2*sin((1:2:1000).^3)/3+4.56; But: scripting language, interpreted, … … -5- MATLAB basic constructs M-files: functions scripts Language constructs Comment: % if .. else… for… while… end Help: help function_name, helpwin, helpdesk lookfor, demo -6- matrices … are rectangular “tables” of entries where the entries are numbers or abstract quantities … Some build-in matrix constructors a = rand(2), b = ones(2), c=eye(2), Addition and scalar product d = c*2; Dot product, dot-multiply and matrix multiplication c(:)’*a(:), d.*a, d*a Matrix inverse, dot divide, etc. -

OS/2 Warp Catalogue
The OS/2 Software Source: www.xeu.com/blueware/ The OS/2 Warp Catalogue The Hottest Java The Strongest Platform The OS/2 Warp Catalogue In This Catalogue Anti-virus .......................................... 4 Backup .............................................. 4 It’s Java Time CD-ROMs ........................................ 4 Communications ........................ 6 Just when you thought that OS/2 was on its way back, it is receiving a strong Database Management .......... 9 infusion from Java and the internet. Development Tools ................ 10 As Dr. Michael Cowpland, president and CEO of Corel Disk Compression .................. 14 Corporation put it: “This platform is indeed one of the Games & Entertainment ..... 19 OS/2 Warp: best operating system solutions in which to run The Hottest Corel Office for Java (http://officeforjava.corel.com/), Graphics & Multimedia ........ 20 a suite of applications that is setting the standard for The Operating System ......... 21 Java Around! Java-based office suites, and marks another milestone OS/2 Warp is developing in the evolution of Java as a whole.” Productivity ................................. 21 into a strong and speedy Programmer’s Editors .......... 23 foundation for Java. The OS/2 Warp 4.0 Java implementation was recently This perfect fit is nicely updated with a better Virtual Machine (VM) and a REXX Programming ................ 23 symbolized by “Carmen” speedy Just In Time (JIT) compiler. Also, even older OS/2 the two-sided coffee cup versions, including Warp 3.0, Warp Connect Utilities & Tools ........................ 24 by dutch ceramist Erik-Jan |and Warp Server are now fully able to suppport Java. Books ............................................. 28 Kwakkel on the cover page. But the great work does not end with that: you can Registration Service ............. -

Guidance for the Provision of ESI to Detainees
Guidance for the Provision of ESI to Detainees Joint Electronic Technology Working Group October 25, 2016 Contents Guidance ......................................................................................................................................... 1 I. An Approach to Providing e-Discovery to Federal Pretrial Detainees ................................... 1 II. Special Concerns in the Delivery of ESI to Detainees ........................................................... 2 A. Defense Concerns .............................................................................................................. 2 B. CJA and FDO Budgeting Concerns ................................................................................... 3 C. Court Concerns ................................................................................................................... 3 D. Facility Concerns ............................................................................................................... 3 E. U.S. Marshals Service Concerns ........................................................................................ 4 F. Government Concerns ........................................................................................................ 4 III. Practical Steps ....................................................................................................................... 4 A. Government, Defense, Facility and Judicial Points of Contact/Working Group ............... 4 B. Identify Facility e-Discovery Capabilities ........................................................................ -

Tugboat, Volume 11 (1990), No. 1 Typesetting Modern Greek
TUGboat, Volume 11 (1990), No. 1 ability of TEX is no different than that of any other Fonts word processing system. However, two particular aspects of T@ may exacerbate the perception of a graphics limitation: is implemented over a broad range of computer platforms, and T@ files Typesetting Modern Greek - An Update are explicitly processed in two distinct stages. Yannis Haralambous We maintain that TEX has an excellent intrin- I would like to announce that. as of March 1, sic graphics capability, which has largely been unex- version 1.1 of the reduced greek fonts and macros ploited. To demonstrate the graphics capability of (cf. TUGboat 10, no. 3 (1989), 354-359) is available. 'I)$,we have chosen the IBM PC and the HP Laser- New features include Jet as a natural configuration. Indeed, this article was produced using the PC/LaserJet combination, hyphenation patterns for modern greek follow- and includes graphics plots derived from several dif- ing the rules mentioned in op. czt., ferent sources. The caption of each plot explains some refinements of the fonts, how the graphics image was obtained. These fig- an italics font, ures were not "cut and pasted", rather they were 0 a new version of greekmacros . t ex. and finally included electronically on the device driver level. a BONUS: an extended logol0.mf file for After considering several possible methods for writing the METAFONT logo in greek! acquiring graphics, printer capture is selected be- This work has been done on a Mac Plus using cause the LaserJet PCL language is well standard- Ozwand MacMETAFONT. -
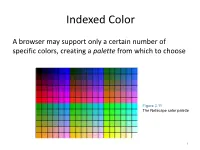
Indexed Color
Indexed Color A browser may support only a certain number of specific colors, creating a palette from which to choose Figure 3.11 The Netscape color palette 1 QUIZ How many bits are needed to represent this palette? Show your work. 2 How to digitize a picture • Sample it → Represent it as a collection of individual dots called pixels • Quantize it → Represent each pixel as one of 224 possible colors (TrueColor) Resolution = The # of pixels used to represent a picture 3 Digitized Images and Graphics Whole picture Figure 3.12 A digitized picture composed of many individual pixels 4 Digitized Images and Graphics Magnified portion of the picture See the pixels? Hands-on: paste the high-res image from the previous slide in Paint, then choose ZOOM = 800 Figure 3.12 A digitized picture composed of many individual pixels 5 QUIZ: Images A low-res image has 200 rows and 300 columns of pixels. • What is the resolution? • If the pixels are represented in True-Color, what is the size of the file? • Same question in High-Color 6 Two types of image formats • Raster Graphics = Storage on a pixel-by-pixel basis • Vector Graphics = Storage in vector (i.e. mathematical) form 7 Raster Graphics GIF format • Each image is made up of only 256 colors (indexed color – similar to palette!) • But they can be a different 256 for each image! • Supports animation! Example • Optimal for line art PNG format (“ping” = Portable Network Graphics) Like GIF but achieves greater compression with wider range of color depth No animations 8 Bitmap format Contains the pixel color -

Administering CRM 2015 for Online and On- Premises
Administering CRM 2015 for online and on- premises Version 7.1.1 This document is provided "as-is". Information and views expressed in this document, including URL and other Internet Web site references, may change without notice. Some examples depicted herein are provided for illustration only and are fictitious. No real association or connection is intended or should be inferred. This document does not provide you with any legal rights to any intellectual property in any Microsoft product. You may copy and use this document for your internal, reference purposes. The videos and eBooks might be in English only. Also, if you click the links, you may be redirected to a U.S. website whose content is in English. © 2015 Microsoft. All rights reserved. Microsoft, Active Directory, Azure, Bing, Excel, Internet Explorer, Microsoft Dynamics, Outlook, SharePoint, SQL Server, Windows, and Windows Server are trademarks of the Microsoft group of companies. All other trademarks are property of their respective owners. Contents Administering CRM 2015 ................................................................................................................. 9 What's new for administrators and customizers in Microsoft Dynamics CRM 2015 and CRM Online ........................................................................................................................................ 9 Getting started ............................................................................................................................ 22 64-bit supported -

A New Steganographic Method for Palette-Based Images
IS&T's 1999 PICS Conference A New Steganographic Method for Palette-Based Images Jiri Fridrich Center for Intelligent Systems, SUNY Binghamton, Binghamton, New York Abstract messages. The gaps in human visual and audio systems can be used for information hiding. In the case of images, the In this paper, we present a new steganographic technique human eye is relatively insensitive to high frequencies. This for embedding messages in palette-based images, such as fact has been utilized in many steganographic algorithms, GIF files. The new technique embeds one message bit into which modify the least significant bits of gray levels in one pixel (its pointer to the palette). The pixels for message digital images or digital sound tracks. Additional bits of embedding are chosen randomly using a pseudo-random information can also be inserted into coefficients of image number generator seeded with a secret key. For each pixel transforms, such as discrete cosine transform, Fourier at which one message bit is to be embedded, the palette is transform, etc. Transform techniques are typically more searched for closest colors. The closest color with the same robust with respect to common image processing operations parity as the message bit is then used instead of the original and lossy compression. color. This has the advantage that both the overall change The steganographer’s job is to make the secretly hidden due to message embedding and the maximal change in information difficult to detect given the complete colors of pixels is smaller than in methods that perturb the knowledge of the algorithm used to embed the information least significant bit of indices to a luminance-sorted palette, except the secret embedding key.* This so called such as EZ Stego.1 Indeed, numerical experiments indicate Kerckhoff’s principle is the golden rule of cryptography and that the new technique introduces approximately four times is often accepted for steganography as well. -

Understanding Image Formats and When to Use Them
Understanding Image Formats And When to Use Them Are you familiar with the extensions after your images? There are so many image formats that it’s so easy to get confused! File extensions like .jpeg, .bmp, .gif, and more can be seen after an image’s file name. Most of us disregard it, thinking there is no significance regarding these image formats. These are all different and not cross‐ compatible. These image formats have their own pros and cons. They were created for specific, yet different purposes. What’s the difference, and when is each format appropriate to use? Every graphic you see online is an image file. Most everything you see printed on paper, plastic or a t‐shirt came from an image file. These files come in a variety of formats, and each is optimized for a specific use. Using the right type for the right job means your design will come out picture perfect and just how you intended. The wrong format could mean a bad print or a poor web image, a giant download or a missing graphic in an email Most image files fit into one of two general categories—raster files and vector files—and each category has its own specific uses. This breakdown isn’t perfect. For example, certain formats can actually contain elements of both types. But this is a good place to start when thinking about which format to use for your projects. Raster Images Raster images are made up of a set grid of dots called pixels where each pixel is assigned a color. -

Gaussplot 8.0.Pdf
GAUSSplotTM Professional Graphics Aptech Systems, Inc. — Mathematical and Statistical System Information in this document is subject to change without notice and does not represent a commitment on the part of Aptech Systems, Inc. The software described in this document is furnished under a license agreement or nondisclosure agreement. The software may be used or copied only in accordance with the terms of the agreement. The purchaser may make one copy of the software for backup purposes. No part of this manual may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording, for any purpose other than the purchaser’s personal use without the written permission of Aptech Systems, Inc. c Copyright 2005-2006 by Aptech Systems, Inc., Maple Valley, WA. All Rights Reserved. ENCSA Hierarchical Data Format (HDF) Software Library and Utilities Copyright (C) 1988-1998 The Board of Trustees of the University of Illinois. All rights reserved. Contributors include National Center for Supercomputing Applications (NCSA) at the University of Illinois, Fortner Software (Windows and Mac), Unidata Program Center (netCDF), The Independent JPEG Group (JPEG), Jean-loup Gailly and Mark Adler (gzip). Bmptopnm, Netpbm Copyright (C) 1992 David W. Sanderson. Dlcompat Copyright (C) 2002 Jorge Acereda, additions and modifications by Peter O’Gorman. Ppmtopict Copyright (C) 1990 Ken Yap. GAUSSplot, GAUSS and GAUSS Engine are trademarks of Aptech Systems, Inc. Tecplot RS, Tecplot, Preplot, Framer and Amtec are registered trademarks or trade- marks of Amtec Engineering, Inc. Encapsulated PostScript, FrameMaker, PageMaker, PostScript, Premier–Adobe Sys- tems, Incorporated. Ghostscript–Aladdin Enterprises. Linotronic, Helvetica, Times– Allied Corporation. -

Sahara Slate PC I500 Tablet PC User's Guide
User’s Guide Sahara Slate PC® i500 12.1” Tablet PC Preface Preface This manual will help you get the most out of your new Sahara Slate PC® i500 Tablet PC. If you are a new computer user, or just new to Tablet PCs, read through this manual carefully be- fore first using your Sahara Slate PC. If after reading this manual you still have questions, visit us online at www.tabletkiosk.com for additional resources and information on using your Sahara Slate PC i500 Tablet PC. Copyright ©2011 Sand Dune Ventures, Inc. d/b/a TabletKiosk. All Rights Reserved. All product information is subject to change without notice. Sahara Slate PC, TabletKiosk and the TabletKiosk logo are registered trademarks or trademarks of TabletKiosk. in the United States and/or other countries. Microsoft Windows and the Windows logo are either registered trademarks or trademarks of Microsoft Corporation in the United States and/ or other countries. Intel, the Intel logo, Intel Core, and Intel Core Inside are trademarks of Intel Corporation in the U.S. and other countries. The Bluetooth word mark and logos are owned by the Bluetooth SIG, Inc. and any use of such marks by TabletKiosk is under license. openSUSE and SUSE are trademarks of Novell, Inc. in the United States and other countries. Linux is a registered trademark of Linus Torvalds. Preface i Disclaimer The specifications and information in this manual are subject to change without prior notice in order to improve reliability, design and/or function. In no way does this represent a commitment on the part of the manufacturer. -

Netpbm Format - Wikipedia, the Free Encyclopedia
Netpbm format - Wikipedia, the free encyclopedia http://en.wikipedia.org/wiki/Portable_anymap Netpbm format From Wikipedia, the free encyclopedia (Redirected from Portable anymap) The phrase Netpbm format commonly refers to any or all Portable pixmap of the members of a set of closely related graphics formats used and defined by the Netpbm project. The portable Filename .ppm, .pgm, .pbm, pixmap format (PPM), the portable graymap format extension .pnm (PGM) and the portable bitmap format (PBM) are image file formats designed to be easily exchanged between Internet image/x-portable- platforms. They are also sometimes referred to collectively media type pixmap, -graymap, [1] as the portable anymap format (PNM). -bitmap, -anymap all unofficial Developed Jef Poskanzer Contents by 1 History Type of Image file formats 2 File format description format 2.1 PBM example 2.2 PGM example 2.3 PPM example 3 16-bit extensions 4 See also 5 References 6 External links History The PBM format was invented by Jef Poskanzer in the 1980s as a format that allowed monochrome bitmaps to be transmitted within an email message as plain ASCII text, allowing it to survive any changes in text formatting. Poskanzer developed the first library of tools to handle the PBM format, Pbmplus, released in 1988. It mainly contained tools to convert between PBM and other graphics formats. By the end of 1988, Poskanzer had developed the PGM and PPM formats along with their associated tools and added them to Pbmplus. The final release of Pbmplus was December 10, 1991. In 1993, the Netpbm library was developed to replace the unmaintained Pbmplus. -

Paint 3D Download for Windows 10 Paint 3D
paint 3d download for windows 10 Paint 3D. Paint 3D is an updated version for Windows 10 with a series of features that simplify enormously the process of drawing and creating sketches on a PC. 1 2 3 4 5 6 7 8 9 10. Windows is full of legendary elements: the blue screen of death, the dog that searched for documents or the possibility to play Solitaire. But Paintbrush, also simply known as Paint, is probably one of the most mythical. Well, this app can be considered as the Paintbrush for Windows 10 as it has been developed by Microsoft and readapts the features of the classic drawing program to the peculiarities of the new operating system. A very easy-to-use drawing program. With dozens of new features, Paint 3D brings creation to another level. And it does so without needing complicated commands or complex functions : it's easy to feel like an artist with its tools that will help you to create extraordinary free-hand drawings. In other words, it recovers the simplicity of yesteryear's software. Paint 3d download for windows 10. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices.