ANTONY ANTONIOU (OSINT Security Analyst)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Conference Programme Europe’S Premier Microwave, Rf, Wireless and Radar Event
SIX DAYS THREE CONFERENCES THREE FORUMS ONE EXHIBITION EUROPEAN MICROWAVE WEEK 2020 JAARBEURS CONVENTION CENTRE UTRECHT – THE NETHERLANDS 10 – 15 JANUARY 2021 10-15 JANUARY 2021 EUROPEAN MICROWAVE WEEK 2020 CONFERENCE PROGRAMME EUROPE’S PREMIER MICROWAVE, RF, WIRELESS AND RADAR EVENT THE ART OF MICROWAVES Register online at: www.eumweek.com 2 – WWW.EUMWEEK.COM SPONSORS TABLE OF CONTENTS WWW.EUMWEEK.COM – 3 Promoting Table of Contents European Microwaves WELCOME MESSAGES STUDENT ACTIVITIES AND WiM Welcome to the 23rd European Microwave Week · · · · · 5 Welcome from the Student Activities Chair · · · · · · 38 Welcome from the President of the European Student Design Competitions · · · · · · · · · · · · 39 Microwave Association ·· · · · · · · · · · · · · · 6 Women in Microwaves · · · · · · · · · · · · · · 39 Welcome to the 15th European Microwave Integrated Career Platform · · · · · · · · · · · · · · · · · 40 Circuits Conference · · · · · · · · · · · · · · · · 7 5th European Microwave Student School · · · · · · · 42 Archiving through Editing the International Journal Welcome to the 50th European Microwave Conference · · 8 Tom Brazil Doctoral School of Microwaves · · · · · · · 43 the Knowledge Centre of Microwave and Wireless Welcome to the 17th European Radar Conference · · · · · 9 Welcome from the General TPC Chair · · · · · · · · ·10 Records papers written by the best Technologies CONFERENCE PROGRAMME international scientists in our secure database. The Journal solicits original and review Sunday 10th January 2021 · · · · · · · · · · · -

Antonis Antoniou · Kkismettin · Ajabu!
JULY 2021 Antonis Antoniou · Kkismettin · Ajabu! 2. Canzoniere Grecanico Salentino (CGS) · Meridiana · 22. Apo Sahagian · Ler Mer · Chimichanga (-) Ponderosa Music (1) 23. Katerina Papadopoulou & Anastatica · Anastasis · 3. Toumani Diabaté and The London Symphony Orchestra · Saphrane (19) Kôrôlén · World Circuit (10) 24. BLK JKS · Abantu / Before Humans · Glitterbeat (-) 4. Ballaké Sissoko · Djourou · Nø Førmat! (2) 25. Davide Ambrogio · Evocazioni e Invocazioni · Catalea 5. Ben Aylon · Xalam · Riverboat / World Music Network (6) (-) 6. Dobet Gnahoré · Couleur · Cumbancha (-) 26. Saucējas · Dabā · Lauska / CPL-Music (31) 7. Balkan Taksim · Disko Telegraf · Buda Musique (5) 27. V.A. · Hanin: Field Recordings In Syria 2008/2009 · 8. V.A. · Henna: Young Female Voices from Palestine · Kirkelig Worlds Within Worlds (-) Kulturverksted (-) 28. Juana Molina · Segundo (Remastered) · Crammed Discs 9. Samba Touré · Binga · Glitterbeat (3) (-) 10. Jupiter & Okwess · Na Kozonga · Zamora Label (7) 29. Bagga Khan · Bhajan · Amarrass (15) 11. Kasai Allstars · Black Ants Always Fly Together, One Bangle 30. Alena Murang · Sky Songs · Wind Music International Makes No Sound · Crammed Discs (12) Corporation (-) 12. Sofía Rei · Umbral · Cascabelera (-) 31. Oumar Ndiaye · Soutoura · Smokey Hormel (-) 13. Hamdi Benani, Mehdi Haddab & Speed Caravan · Nuba 32. Xurxo Fernandes · Levaino! · Xurxo Fernandes (29) Nova · Buda Musique (27) 33. Omar Sosa · An East African Journey · Otá (24) 14. Comorian · We Are an Island, but We're Not Alone · 34. San Salvador · La Grande Folie · La Grande Folie / Glitterbeat (17) Pagans / MDC (11) 15. Dagadana · Tobie · Agora Muzyka (18) 35. Helsinki-Cotonou Ensemble · Helsinki-Cotonou 16. Luís Peixoto · Geodesia · Groove Punch Studios (20) Ensemble · flowfish.music (-) 17. Femi Kuti & Made Kuti · Legacy + · Partisan (30) 36. -

Intelligence Community Programs, Management, and Enduring Issues
Intelligence Community Programs, Management, and Enduring Issues (name redacted) Analyst in Intelligence and National Security Policy November 8, 2016 Congressional Research Service 7-.... www.crs.gov R44681 Intelligence Community Programs, Management, and Enduring Issues Summary Congress’s and the American public’s ability to oversee and understand how intelligence dollars are spent is limited by the secrecy that surrounds the intelligence budget process. Yet, total spending on the Intelligence Community (IC) programs discussed in this report equates to approximately $70 billion dollars—roughly 10% of national defense spending. This report is designed to shed light on the IC budget—in terms of its programs, management, and enduring issues—using unclassified materials available in the public domain. This report focuses those IC programs, grouped, for the most part, under two labels: (1) the National Intelligence Program (NIP), and (2) the Military Intelligence Program (MIP). Nevertheless, the combined NIP and MIP budgets do not encompass the total of U.S. intelligence- related spending. Intelligence-related programs that are not part of the IC include, for example, the large Office of Intelligence within the Department of Homeland Security’s (DHS’s) Immigration and Customs Enforcement (ICE) division. The ICE Office of Intelligence is not included in the IC because, theoretically, ICE activities primarily support the DHS mission to protect the homeland. This report explains the management structure for the NIP and MIP to include their two separate budget processes and the roles of the Director of National Intelligence and the Under Secretary of Defense (Intelligence). The concluding section of this report considers the ability of the U.S. -

False Dilemma Wikipedia Contents
False dilemma Wikipedia Contents 1 False dilemma 1 1.1 Examples ............................................... 1 1.1.1 Morton's fork ......................................... 1 1.1.2 False choice .......................................... 2 1.1.3 Black-and-white thinking ................................... 2 1.2 See also ................................................ 2 1.3 References ............................................... 3 1.4 External links ............................................. 3 2 Affirmative action 4 2.1 Origins ................................................. 4 2.2 Women ................................................ 4 2.3 Quotas ................................................. 5 2.4 National approaches .......................................... 5 2.4.1 Africa ............................................ 5 2.4.2 Asia .............................................. 7 2.4.3 Europe ............................................ 8 2.4.4 North America ........................................ 10 2.4.5 Oceania ............................................ 11 2.4.6 South America ........................................ 11 2.5 International organizations ...................................... 11 2.5.1 United Nations ........................................ 12 2.6 Support ................................................ 12 2.6.1 Polls .............................................. 12 2.7 Criticism ............................................... 12 2.7.1 Mismatching ......................................... 13 2.8 See also -

0.1 Problems
0.1. PROBLEMS 1 0.1 Problems 1. Among the fundamental challenges in information security are confi- dentiality, integrity, and availability, or CIA. a. Define each of these terms: confidentiality, integrity, availability. b. Give a concrete example where confidentiality is more important than integrity. c. Give a concrete example where integrity is more important than confidentiality. d. Give a concrete example where availability is the overriding con- cern. 2. From a bank's perspective, which is usually more important, the in- tegrity of its customer's data or the confidentiality of the data? From the perspective of the bank's customers, which is more important? 3. Instead of an online bank, suppose that Alice provides an online chess playing service known as Alice's Online Chess (AOC). Players, who pay a monthly fee, log into AOC where they are matched with another player of comparable ability. a. Where (and why) is confidentiality important for AOC and its customers? b. Why is integrity necessary? c. Why is availability an important concern? 4. Instead of an online bank, suppose that Alice provides an online chess playing service known as Alice's Online Chess (AOC). Players, who pay a monthly fee, log into AOC where they are matched with another player of comparable ability. a. Where should cryptography be used in AOC? b. Where should access control used? c. Where would security protocols be used? d. Is software security a concern for AOC? Why or why not? 5. Some authors distinguish between secrecy, privacy, and confidential- ity. In this usage, secrecy is equivalent to our use of the term con- fidentiality, whereas privacy is secrecy applied to personal data, and 2 confidentiality (in this misguided sense) refers to an obligation not to divulge certain information. -

Open Source Intelligence (OSINT)
ATP 2-22.9 Open-Source Intelligence July 2012 DISTRIBUTION RESTRICTION: Unlimited Distribution Headquarters, Department of the Army *ATP 2-22.9 Army Techniques Publication Headquarters No. 2-22.9 (FMI 2-22.9) Department of the Army Washington, DC, 10 July 2012 Open-Source Intelligence Contents Page PREFACE.............................................................................................................. iv INTRODUCTION .................................................................................................... v Chapter 1 OPEN-SOURCE INTELLIGENCE (OSINT) FUNDAMENTALS ........................ 1-1 Definition and Terms .......................................................................................... 1-1 Characteristics .................................................................................................... 1-1 The Intelligence Warfighting Function ................................................................ 1-2 The Intelligence Process .................................................................................... 1-3 The Planning Requirements and Assessing Collection Process ........................ 1-4 The Military Decisionmaking Process ................................................................ 1-4 Intelligence Preparation of the Battlefield ........................................................... 1-5 Chapter 2 PLANNING AND PREPARATION OF THE OSINT MISSION ............................. 2-1 Section I – Planning OSINT Activities ........................................................... -

Remittance Economy Migration-Underdevelopment in Sri Lanka
REMITTANCE ECONOMY MIGRATION-UNDERDEVELOPMENT IN SRI LANKA Matt Withers A thesis submitted in fulfilment of requirements for the degree of Doctor of Philosophy. Faculty of Arts and Social Sciences Department of Political Economy The University of Sydney 2017 “Ceylon ate the fruit before growing the tree” - Joan Robinson (Wilson 1977) (Parren as 2005) (Eelens and Speckmann 1992) (Aneez 2016b) (International Monetary Fund (IMF) 1993; International Monetary Fund (IMF) 2009) (Central Bank of Sri Lanka (CBSL) 2004) (United Nations Population Division 2009) Acknowledgements Thanks are due to a great number of people who have offered support and lent guidance throughout the course of my research. I would like to extend my appreciation foremost to my wonderful supervisors, Elizabeth Hill and Stuart Rosewarne, whose encouragement and criticism have been (in equal measure) invaluable in shaping this thesis. I must similarly offer heartfelt thanks to my academic mentors, Nicola Piper and Janaka Biyanwila, both of whom have unfailingly offered their time, interest and wisdom as my work has progressed. Gratitude is also reserved for my colleagues Magdalena Cubas and Rosie Hancock, who have readily guided me through the more challenging stages of thesis writing with insights and lessons from their own research. A special mention must be made for the Centre for Poverty Analysis in Colombo, without whose assistance my research would simply not have been possible. I would like to thank Priyanthi Fernando for her willingness to accommodate me, Mohamed Munas for helping to make fieldwork arrangements, and to Vagisha Gunasekara for her friendship and willingness to answer my incessant questions about Sri Lanka. -

NISCOM Publication Espionage 1989
COMMENTS ................................... ........................................ 1 INTRODUCTION ... ... .... ........................................................ ... 2 SIGNIFICANT CASES ........ ...................................... ...............3 Michael Hahn Allen ...................................................................... 5 Stephen Anthony Baba ................................. ............................... 6 Robert Ernest Cordrey ..................................................................7 Nelson Cornelious Drummond ..................................................... 8 Wilfredo Garcia ............................................................................ 9 Stephen Dwayne Hawkins ...........................................................10 Brian Patrick Horton ....................................................................11 Clayton John Lonetree ................................................ ......... ...... 12 Samuel Lori ng Morison ............................................................. ..14 Jeffery Loring Pickerlng ......................................... .....................15 Jonathan Jay Pollard .................................................................. 16 Brian Everett Slavens .................................................................17 Michael Timothy Tobias .............................................................. 18 John Anthony Walker, Jr.... ............................................... ......... 19 Michael Lance Walker ............................................................... -

Alleged Spy Mid Twice for Security Rating
Michael Walker was arrested two top-secret access while they were on weeks ago while on active duty active duty." said a statement from aboard the aircraft carrier USS Ni- the office of Michael I. Burch, chief mitz. Pentagon spokesman. His father, John Anthony Walker. "Of the three with top-secret Jr., the alleged leader of the spy ring, clearance, it appears that only Whit- served almost 21 years In the Navy worth had been the subject of a re- before retiring in 1976. John Walk- investigation. with the first conduct- er's brother, Arthur, served 20 years ed In 1969 followed by one in 1978." before retiring in 1973. Mr. Whit- worth, who is not related to the See SECURITY, 14A, Col. 6 Walkers, served 21 years on active duty before retiring in 1983. The FBI, when it arrested Mr. Whitworth earlier this week, charged he had been providing classified in- formation to the Soviets through John Walker, a long-time friend. Both Mr. Whitworth and John Walker worked in sensitive radio communications posts before their retirement. Arthur Walker, who re- tired as a Secret clearance while on active duty. He held a top secret clearance at the time of his arrest be- cause he was working for a Virginia ASSOCIATED PRESS defense contractor. JERRY A. WHITWORTH Pentagon and Navy officials were Held "top secret" clerarance unable to say yesterday when the four men first received their clear- ances. In court papers filed yesterday in Alleged spy U.S. District Court in Baltimore, John Walker's federal public defend- Mid twice for er argued that he should be allowed to continue representing Mr. -

DNI Open Source Conference 2008 Transcripts
Office of the Director of National Intelligence Transcripts from the DNI Open Source Conference 2008 Washington, DC September 11, 2008 – September 12, 2008 The links below will forward you to the appropriate transcripts: 1) Mr. Glenn Gaffney Deputy Director of National Intelligence for Collection 2) Mr. Michael V. Hayden Director of the Central Intelligence Agency 3) Ms. Christine McKeown Office of the Under Secretary of Defense for Intelligence 4) Mr. Doug Naquin Director of the Open Source Center 5) Mr. Charles E. Allen DHS Under Secretary for Intelligence & Analysis 6) Panel: Managing the Balance Between Privacy & National Security 1 Remarks and Q&A by the Deputy Director of National Intelligence for Collection Mr. Glenn A. Gaffney DNI Open Source Conference 2008 Washington, DC MS. SABRA HORNE (ODNI Senior Advisor for Open Source/Outreach): Good morning. Welcome ladies and gentlemen and welcome to the Second Annual DNI Open Source Conference. We’re thrilled to have you here. I’m Sabra Horne, Senior Advisor for Outreach and the organizer for this event. We see many familiar faces here, a lot of the wonderful folks we’ve worked with over the past few years as well as those of you who were able to attend the conference last year. But in this last year, we’ve added many, many, many new faces to our friends and family list – those of you who know that using open source is vital in ensuring that we protect our national security. Our list of friends and family has grown, and grown, and grown. You recognize that open source information is critical in transcending the confines of the traditional Intelligence Community. -

Espionage Against the United States by American Citizens 1947-2001
Technical Report 02-5 July 2002 Espionage Against the United States by American Citizens 1947-2001 Katherine L. Herbig Martin F. Wiskoff TRW Systems Released by James A. Riedel Director Defense Personnel Security Research Center 99 Pacific Street, Building 455-E Monterey, CA 93940-2497 REPORT DOCUMENTATION PAGE Form Approved OMB No. 0704-0188 The public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instructions, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing the burden, to Department of Defense, Washington Headquarters Services, Directorate for Information Operations and Reports (0704- 0188), 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202-4302. Respondents should be aware that notwithstanding any other provision of law, no person shall be subject to any penalty for failing to comply with a collection of information if it does not display a currently valid OMB control number. PLEASE DO NOT RETURN YOUR FORM TO THE ABOVE ADDRESS. 1. REPORT DATE (DDMMYYYY) 2. REPORT TYPE 3. DATES COVERED (From – To) July 2002 Technical 1947 - 2001 4. TITLE AND SUBTITLE 5a. CONTRACT NUMBER 5b. GRANT NUMBER Espionage Against the United States by American Citizens 1947-2001 5c. PROGRAM ELEMENT NUMBER 6. AUTHOR(S) 5d. PROJECT NUMBER Katherine L. Herbig, Ph.D. Martin F. Wiskoff, Ph.D. 5e. TASK NUMBER 5f. WORK UNIT NUMBER 7. PERFORMING ORGANIZATION NAME(S) AND ADDRESS(ES) 8. -
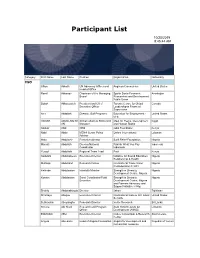
Participant List
Participant List 10/20/2019 8:45:44 AM Category First Name Last Name Position Organization Nationality CSO Jillian Abballe UN Advocacy Officer and Anglican Communion United States Head of Office Ramil Abbasov Chariman of the Managing Spektr Socio-Economic Azerbaijan Board Researches and Development Public Union Babak Abbaszadeh President and Chief Toronto Centre for Global Canada Executive Officer Leadership in Financial Supervision Amr Abdallah Director, Gulf Programs Educaiton for Employment - United States EFE HAGAR ABDELRAHM African affairs & SDGs Unit Maat for Peace, Development Egypt AN Manager and Human Rights Abukar Abdi CEO Juba Foundation Kenya Nabil Abdo MENA Senior Policy Oxfam International Lebanon Advisor Mala Abdulaziz Executive director Swift Relief Foundation Nigeria Maryati Abdullah Director/National Publish What You Pay Indonesia Coordinator Indonesia Yussuf Abdullahi Regional Team Lead Pact Kenya Abdulahi Abdulraheem Executive Director Initiative for Sound Education Nigeria Relationship & Health Muttaqa Abdulra'uf Research Fellow International Trade Union Nigeria Confederation (ITUC) Kehinde Abdulsalam Interfaith Minister Strength in Diversity Nigeria Development Centre, Nigeria Kassim Abdulsalam Zonal Coordinator/Field Strength in Diversity Nigeria Executive Development Centre, Nigeria and Farmers Advocacy and Support Initiative in Nig Shahlo Abdunabizoda Director Jahon Tajikistan Shontaye Abegaz Executive Director International Insitute for Human United States Security Subhashini Abeysinghe Research Director Verite