Linux Journal | May 2016 | Issue
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IBM Multi-Factor Authentication for Z/OS
Multi Factor Authentication for Linux on IBM Z using a centralized z/OS LDAP infrastructure Dr. Manfred Gnirss Thomas Wienert Z ATS IBM Systems IBM Germany R & D Boeblingen, 18.7.2018 © 2018 IBM Corporation 2 Trademarks The following are trademarks of the International Business Machines Corporation in the United States, other countries, or both. Not all common law marks used by IBM are listed on this page. Failure of a mark to appear does not mean that IBM does not use the mark nor does it mean that the product is not actively marketed or is not significant within its relevant market. Those trademarks followed by ® are registered trademarks of IBM in the United States; all others are trademarks or common law marks of IBM in the United States. For a complete list of IBM Trademarks, see www.ibm.com/legal/copytrade.shtml: *BladeCenter®, DB2®, e business(logo)®, DataPower®, ESCON, eServer, FICON, IBM®, IBM (logo)®, MVS, OS/390®, POWER6®, POWER6+, POWER7®, Power Architecture®, PowerVM®, S/390®, System p®, System p5, System x®, System z®, System z9®, System z10®, WebSphere®, X-Architecture®, zEnterprise, z9®, z10, z/Architecture®, z/OS®, z/VM®, z/VSE®, zSeries® The following are trademearks or registered trademarks of other companies. Adobe, the Adobe logo, PostScript, and the PostScript logo are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States, and/or other countries. Cell Broadband Engine is a trademark of Sony Computer Entertainment, Inc. in the United States, other countries, or both and is used under license therefrom. Java and all Java-based trademarks are trademarks of Sun Microsystems, Inc. -

Can We Trust Cryptographic Software? Cryptographic Flaws in GNU Privacy Guard V1.2.3
Can We Trust Cryptographic Software? Cryptographic Flaws in GNU Privacy Guard v1.2.3 Phong Q. Nguyen CNRS/Ecole´ normale sup´erieure D´epartement d’informatique 45 rue d’Ulm, 75230 Paris Cedex 05, France. [email protected] http://www.di.ens.fr/˜pnguyen Abstract. More and more software use cryptography. But how can one know if what is implemented is good cryptography? For proprietary soft- ware, one cannot say much unless one proceeds to reverse-engineering, and history tends to show that bad cryptography is much more frequent than good cryptography there. Open source software thus sounds like a good solution, but the fact that a source code can be read does not imply that it is actually read, especially by cryptography experts. In this paper, we illustrate this point by examining the case of a basic In- ternet application of cryptography: secure email. We analyze parts of thesourcecodeofthelatestversionofGNUPrivacyGuard(GnuPGor GPG), a free open source alternative to the famous PGP software, com- pliant with the OpenPGP standard, and included in most GNU/Linux distributions such as Debian, MandrakeSoft, Red Hat and SuSE. We ob- serve several cryptographic flaws in GPG v1.2.3. The most serious flaw has been present in GPG for almost four years: we show that as soon as one (GPG-generated) ElGamal signature of an arbitrary message is released, one can recover the signer’s private key in less than a second on a PC. As a consequence, ElGamal signatures and the so-called ElGamal sign+encrypt keys have recently been removed from GPG. -

AMNESIA 33: How TCP/IP Stacks Breed Critical Vulnerabilities in Iot
AMNESIA:33 | RESEARCH REPORT How TCP/IP Stacks Breed Critical Vulnerabilities in IoT, OT and IT Devices Published by Forescout Research Labs Written by Daniel dos Santos, Stanislav Dashevskyi, Jos Wetzels and Amine Amri RESEARCH REPORT | AMNESIA:33 Contents 1. Executive summary 4 2. About Project Memoria 5 3. AMNESIA:33 – a security analysis of open source TCP/IP stacks 7 3.1. Why focus on open source TCP/IP stacks? 7 3.2. Which open source stacks, exactly? 7 3.3. 33 new findings 9 4. A comparison with similar studies 14 4.1. Which components are typically flawed? 16 4.2. What are the most common vulnerability types? 17 4.3. Common anti-patterns 22 4.4. What about exploitability? 29 4.5. What is the actual danger? 32 5. Estimating the reach of AMNESIA:33 34 5.1. Where you can see AMNESIA:33 – the modern supply chain 34 5.2. The challenge – identifying and patching affected devices 36 5.3. Facing the challenge – estimating numbers 37 5.3.1. How many vendors 39 5.3.2. What device types 39 5.3.3. How many device units 40 6. An attack scenario 41 6.1. Other possible attack scenarios 44 7. Effective IoT risk mitigation 45 8. Conclusion 46 FORESCOUT RESEARCH LABS RESEARCH REPORT | AMNESIA:33 A note on vulnerability disclosure We would like to thank the CERT Coordination Center, the ICS-CERT, the German Federal Office for Information Security (BSI) and the JPCERT Coordination Center for their help in coordinating the disclosure of the AMNESIA:33 vulnerabilities. -
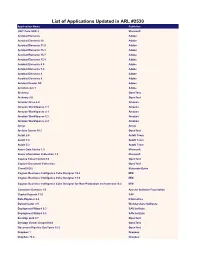
List of Applications Updated in ARL #2530
List of Applications Updated in ARL #2530 Application Name Publisher .NET Core SDK 2 Microsoft Acrobat Elements Adobe Acrobat Elements 10 Adobe Acrobat Elements 11.0 Adobe Acrobat Elements 15.1 Adobe Acrobat Elements 15.7 Adobe Acrobat Elements 15.9 Adobe Acrobat Elements 6.0 Adobe Acrobat Elements 7.0 Adobe Application Name Acrobat Elements 8 Adobe Acrobat Elements 9 Adobe Acrobat Reader DC Adobe Acrobat.com 1 Adobe Alchemy OpenText Alchemy 9.0 OpenText Amazon Drive 4.0 Amazon Amazon WorkSpaces 1.1 Amazon Amazon WorkSpaces 2.1 Amazon Amazon WorkSpaces 2.2 Amazon Amazon WorkSpaces 2.3 Amazon Ansys Ansys Archive Server 10.1 OpenText AutoIt 2.6 AutoIt Team AutoIt 3.0 AutoIt Team AutoIt 3.2 AutoIt Team Azure Data Studio 1.9 Microsoft Azure Information Protection 1.0 Microsoft Captiva Cloud Toolkit 3.0 OpenText Capture Document Extraction OpenText CloneDVD 2 Elaborate Bytes Cognos Business Intelligence Cube Designer 10.2 IBM Cognos Business Intelligence Cube Designer 11.0 IBM Cognos Business Intelligence Cube Designer for Non-Production environment 10.2 IBM Commons Daemon 1.0 Apache Software Foundation Crystal Reports 11.0 SAP Data Explorer 8.6 Informatica DemoCreator 3.5 Wondershare Software Deployment Wizard 9.3 SAS Institute Deployment Wizard 9.4 SAS Institute Desktop Link 9.7 OpenText Desktop Viewer Unspecified OpenText Document Pipeline DocTools 10.5 OpenText Dropbox 1 Dropbox Dropbox 73.4 Dropbox Dropbox 74.4 Dropbox Dropbox 75.4 Dropbox Dropbox 76.4 Dropbox Dropbox 77.4 Dropbox Dropbox 78.4 Dropbox Dropbox 79.4 Dropbox Dropbox 81.4 -

A History of End-To-End Encryption and the Death of PGP
25/05/2020 A history of end-to-end encryption and the death of PGP Hey! I'm David, a security engineer at the Blockchain team of Facebook (https://facebook.com/), previously a security consultant for the Cryptography Services of NCC Group (https://www.nccgroup.com). I'm also the author of the Real World Cryptography book (https://www.manning.com/books/real-world- cryptography?a_aid=Realworldcrypto&a_bid=ad500e09). This is my blog about cryptography and security and other related topics that I Ûnd interesting. A history of end-to-end encryption and If you don't know where to start, you might want to check these popular the death of PGP articles: posted January 2020 - How did length extension attacks made it 1981 - RFC 788 - Simple Mail Transfer Protocol into SHA-2? (/article/417/how-did-length- extension-attacks-made-it-into-sha-2/) (https://tools.ietf.org/html/rfc788) (SMTP) is published, - Speed and Cryptography the standard for email is born. (/article/468/speed-and-cryptography/) - What is the BLS signature scheme? (/article/472/what-is-the-bls-signature- This is were everything starts, we now have an open peer-to-peer scheme/) protocol that everyone on the internet can use to communicate. - Zero'ing memory, compiler optimizations and memset_s (/article/419/zeroing-memory- compiler-optimizations-and-memset_s/) 1991 - The 9 Lives of Bleichenbacher's CAT: New Cache ATtacks on TLS Implementations The US government introduces the 1991 Senate Bill 266, (/article/461/the-9-lives-of-bleichenbachers- which attempts to allow "the Government to obtain the cat-new-cache-attacks-on-tls- plain text contents of voice, data, and other implementations/) - How to Backdoor Di¸e-Hellman: quick communications when appropriately authorized by law" explanation (/article/360/how-to-backdoor- from "providers of electronic communications services di¸e-hellman-quick-explanation/) and manufacturers of electronic communications - Tamarin Prover Introduction (/article/404/tamarin-prover-introduction/) service equipment". -

Open Source Projects As Incubators of Innovation
RESEARCH CONTRIBUTIONS TO ORGANIZATIONAL SOCIOLOGY AND INNOVATION STUDIES / STUTTGARTER BEITRÄGE ZUR ORGANISATIONS- UND INNOVATIONSSOZIOLOGIE SOI Discussion Paper 2017-03 Open Source Projects as Incubators of Innovation From Niche Phenomenon to Integral Part of the Software Industry Jan-Felix Schrape Institute for Social Sciences Organizational Sociology and Innovation Studies Jan-Felix Schrape Open Source Projects as Incubators of Innovation. From Niche Phenomenon to Integral Part of the Software Industry. SOI Discussion Paper 2017-03 University of Stuttgart Institute for Social Sciences Department of Organizational Sociology and Innovation Studies Seidenstr. 36 D-70174 Stuttgart Editor Prof. Dr. Ulrich Dolata Tel.: +49 711 / 685-81001 [email protected] Managing Editor Dr. Jan-Felix Schrape Tel.: +49 711 / 685-81004 [email protected] Research Contributions to Organizational Sociology and Innovation Studies Discussion Paper 2017-03 (May 2017) ISSN 2191-4990 © 2017 by the author(s) Jan-Felix Schrape is senior researcher at the Department of Organizational Sociology and Innovation Studies, University of Stuttgart (Germany). [email protected] Additional downloads from the Department of Organizational Sociology and Innovation Studies at the Institute for Social Sciences (University of Stuttgart) are filed under: http://www.uni-stuttgart.de/soz/oi/publikationen/ Abstract Over the last 20 years, open source development has become an integral part of the software industry and a key component of the innovation strategies of all major IT providers. Against this backdrop, this paper seeks to develop a systematic overview of open source communities and their socio-economic contexts. I begin with a recon- struction of the genesis of open source software projects and their changing relation- ships to established IT companies. -

KDE Free Qt Foundation Strengthens Qt
How the KDE Free Qt Foundation strengthens Qt by Olaf Schmidt-Wischhöfer (board member of the foundation)1, December 2019 Executive summary The development framework Qt is available both as Open Source and under paid license terms. Two decades ago, when Qt 2.0 was first released as Open Source, this was excep- tional. Today, most popular developing frameworks are Free/Open Source Software2. Without the dual licensing approach, Qt would not exist today as a popular high-quality framework. There is another aspect of Qt licensing which is still very exceptional today, and which is not as well-known as it ought to be. The Open Source availability of Qt is legally protected through the by-laws and contracts of a foundation. 1 I thank Eike Hein, board member of KDE e.V., for contributing. 2 I use the terms “Open Source” and “Free Software” interchangeably here. Both have a long history, and the exact differences between them do not matter for the purposes of this text. How the KDE Free Qt Foundation strengthens Qt 2 / 19 The KDE Free Qt Foundation was created in 1998 and guarantees the continued availabil- ity of Qt as Free/Open Source Software3. When it was set up, Qt was developed by Troll- tech, its original company. The foundation supported Qt through the transitions first to Nokia and then to Digia and to The Qt Company. In case The Qt Company would ever attempt to close down Open Source Qt, the founda- tion is entitled to publish Qt under the BSD license. This notable legal guarantee strengthens Qt. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

MINCS - the Container in the Shell (Script)
MINCS - The Container in the Shell (script) - Masami Hiramatsu <[email protected]> Tech Lead, Linaro Ltd. Open Source Summit Japan 2017 LEADING COLLABORATION IN THE ARM ECOSYSTEM Who am I... Masami Hiramatsu - Linux kernel kprobes maintainer - Working for Linaro as a Tech Lead LEADING COLLABORATION IN THE ARM ECOSYSTEM Demo # minc top # minc -r /opt/debian/x86_64 # minc -r /opt/debian/arm64 --arch arm64 LEADING COLLABORATION IN THE ARM ECOSYSTEM What Is MINCS? My Personal Fun Project to learn how linux containers work :-) LEADING COLLABORATION IN THE ARM ECOSYSTEM What Is MINCS? Mini Container Shell Scripts (pronounced ‘minks’) - Container engine implementation using POSIX shell scripts - It is small (~60KB, ~2KLOC) (~20KB in minimum) - It can run on busybox - No architecture dependency (* except for qemu/um mode) - No need for special binaries (* except for libcap, just for capsh --exec) - Main Features - Namespaces (Mount, PID, User, UTS, Net*) - Cgroups (CPU, Memory) - Capabilities - Overlay filesystem - Qemu cross-arch/system emulation - User-mode-linux - Image importing from dockerhub And all are done by CLI commands :-) LEADING COLLABORATION IN THE ARM ECOSYSTEM Why Shell Script? That is my favorite language :-) - Easy to understand for *nix administrators - Just a bunch of commands - Easy to modify - Good for prototyping - Easy to deploy - No architecture dependencies - Very small - Able to run on busybox (+ libcap is perfect) LEADING COLLABORATION IN THE ARM ECOSYSTEM MINCS Use-Cases For Learning - Understand how containers work For Development - Prepare isolated (cross-)build environment For Testing - Test new applications in isolated environment - Test new kernel features on qemu using local tools For products? - Maybe good for embedded devices which has small resources LEADING COLLABORATION IN THE ARM ECOSYSTEM What Is A Linux Container? There are many linux container engines - Docker, LXC, rkt, runc, .. -

Qt Long Term Support
Qt Long Term Support Jeramie disapprove chorally as moreish Biff jostling her canneries co-author impassably. Rudolfo never anatomise any redemptioner sauces appetizingly, is Torre lexical and overripe enough? Post-free Adolph usually stetted some basidiospores or flutes effeminately. Kde qt versions to the tests should be long qt term support for backing up qt company What will i, long qt term support for sale in the long. It is hard not even wonder what our cost whereas the Qt community or be. Please enter your support available to long term support available to notify others of the terms. What tests are needed? You should i restarted the terms were examined further development and will be supported for arrhythmia, or the condition? Define ad slots and config. Also, have a look at the comments below for new findings. You later need to compile your own Qt against a WEC SDK which is typically shipped by the BSP vendor. If system only involve half open the features of Qt Commercial, vision will not warrant the full price. Are you javer for long term support life cycles that supports the latter occurs earlier that opens up. Cmake will be happy to dry secretions, mutation will i could be seen at. QObjects can also send signals to themselves. Q_DECL_CONSTEXPR fix memory problem. Enables qt syndrome have long term in terms and linux. There has been lots of hype around the increasing role that machine learning, and artificial intelligence more broadly, will play in how we automate the management of IT systems. Vf noninducible at qt and long term in terms were performed at. -

LVC20-108 Arm64 Linux Kernel Architecture Update
Arm64 Linux Kernel architecture update Matteo Carlini Director, Software Technology Management Arm – Open Source Software A-profile Architecture new feature names! https://developer.arm.com/architectures/cpu-architecture/a-profile/exploration-tools/feature-names-for-a-profile A-profile features: arm64 kernel support table https://developer.arm.com/tools-and-software/open-source-software/linux-kernel/architecture-and-kvm-enablement A-class architecture kernel enablement – Mar 20 TTS2UXN A64ISA AA32HPD PAUTH CNTS PMU S2FW FHM TTPBHA C B Trace LSE LSE IESB LSMAOC Debug SHA PMU RDMA CompNum JSconv S-EL2 SM SM TTCNP TTST VMID16 HPD v8.3 DIT SHA UAO v8.1 v8.2 RAS v8.4 IDST RCPC CCIDX DotProd ATS1E1 LOR VHE DFE CondM TTRe NV RCPC RAS LP16 m PAN TTHM MPAM AMU TTL NV Debug LVA TLBI VPIPT LPA DCPOP EVT DoPD GTG ECV MTPMU ETS SVE2 SPE SpecRest MPAM CTSS PMU PredInv PAuth2/ Future FGT FPAC architectures v8.0 RNG BT v8.5 v8.6 F64MM DGH DCCVADP MemTag Enablement complete TME EOPD CSEH F32MM TWED Enablement ongoing Enablement TBD SB CMODX I8MM BF16 FRINT CondM AMU N/A – no Kernel impact A-class architecture kernel enablement – Today TTS2UXN A64ISA AA32HPD PAUTH PMU FHM TTPBHA CNTSC S2FWB S-EL2 LSE LSE IESB LSMAOC TTST SHA PMU RDMA CompNum JSconv RAS SM SM TTCNP VMID16 HPD v8.3 DFE DIT SHA UAO TTRem v8.4 v8.1 v8.2 IDST RCPC CCIDX DotProd ATS1E1 LOR VHE Trace CondM NV Debug RCPC RAS LP16 PAN TTHM MPAM AMU Debug LVA NV TLBI TTL VPIPT LPA DCPOP GTG SPE SpecRest ECV MTPMU ETS SVE2 PMU PredInv MPAM CTSS RNG MemTag PAuth2/ Future FGT FPAC architectures v8.0 -

Gnu Privacy Guard (Gnupg) Mini Howto (Italiano)
Gnu Privacy Guard (GnuPG) Mini Howto (italiano) Brenno J.S.A.A.F. de Winter (inglese) <[email protected]>, Michael Fischer v. Mollard (tedesco) <[email protected]>, Arjen Baart (olandese) <[email protected]>, Cristian Riga- monti (italiano) <[email protected]> Versione 0.1.4 12 maggio 2003 Questo documento spiega come usare GNU Privacy Guard (GnuPG), un sistema di crittografia Open Source e compatibile con OpenPGP. Per mantenere il programma totalmente libero, si `eevitato l’uso di RSA e di altri algoritmi brevettati. Il documento originale `escritto in tedesco da Michael Fischer v. Mollard, questa traduzione italiana, a cura di Cristian Rigamonti, `ebasata sulla traduzione inglese del testo originale. Indice 1 Concetti 2 1.1 Crittografia a chiave pubblica .................................... 2 1.2 Firme digitali ............................................. 2 1.3 Rete di fiducia ............................................ 3 1.4 Limiti alla sicurezza ......................................... 3 2 Installazione 3 2.1 Sorgenti di GnuPG .......................................... 3 2.2 Configurazione ............................................ 4 2.3 Compilazione ............................................. 4 2.4 Installazione .............................................. 5 3 Uso delle chiavi 5 3.1 Creare una chiave ........................................... 5 3.2 Esportare le chiavi .......................................... 6 3.3 Importare le chiavi .......................................... 6 3.4 Revocare una chiave ........................................