A Review Study of Interior and Exterior Gateway Protocols
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Comprehensive Study of Routing Protocols Performance with Topological Changes in the Networks Mohsin Masood Mohamed Abuhelala Prof
A comprehensive study of Routing Protocols Performance with Topological Changes in the Networks Mohsin Masood Mohamed Abuhelala Prof. Ivan Glesk Electronics & Electrical Electronics & Electrical Electronics & Electrical Engineering Department Engineering Department Engineering Department University of Strathclyde University of Strathclyde University of Strathclyde Glasgow, Scotland, UK Glasgow, Scotland, UK Glasgow, Scotland, UK mohsin.masood mohamed.abuhelala ivan.glesk @strath.ac.uk @strath.ac.uk @strath.ac.uk ABSTRACT different topologies and compare routing protocols, but no In the modern communication networks, where increasing work has been considered about the changing user demands and advance applications become a functionality of these routing protocols with the topology challenging task for handling user traffic. Routing with real-time network limitations. such as topological protocols have got a significant role not only to route user change, network congestions, and so on. Hence without data across the network but also to reduce congestion with considering the topology with different network scenarios less complexity. Dynamic routing protocols such as one cannot fully understand and make right comparison OSPF, RIP and EIGRP were introduced to handle among any routing protocols. different networks with various traffic environments. Each This paper will give a comprehensive literature review of of these protocols has its own routing process which each routing protocol. Such as how each protocol (OSPF, makes it different and versatile from the other. The paper RIP or EIGRP) does convergence activity with any change will focus on presenting the routing process of each in the network. Two experiments are conducted that are protocol and will compare its performance with the other. -

Configuring Static Routing
Configuring Static Routing This chapter contains the following sections: • Finding Feature Information, on page 1 • Information About Static Routing, on page 1 • Licensing Requirements for Static Routing, on page 4 • Prerequisites for Static Routing, on page 4 • Guidelines and Limitations for Static Routing, on page 4 • Default Settings for Static Routing Parameters, on page 4 • Configuring Static Routing, on page 4 • Verifying the Static Routing Configuration, on page 10 • Related Documents for Static Routing, on page 10 • Feature History for Static Routing, on page 10 Finding Feature Information Your software release might not support all the features documented in this module. For the latest caveats and feature information, see the Bug Search Tool at https://tools.cisco.com/bugsearch/ and the release notes for your software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the "New and Changed Information"chapter or the Feature History table in this chapter. Information About Static Routing Routers forward packets using either route information from route table entries that you manually configure or the route information that is calculated using dynamic routing algorithms. Static routes, which define explicit paths between two routers, cannot be automatically updated; you must manually reconfigure static routes when network changes occur. Static routes use less bandwidth than dynamic routes. No CPU cycles are used to calculate and analyze routing updates. You can supplement dynamic routes with static routes where appropriate. You can redistribute static routes into dynamic routing algorithms but you cannot redistribute routing information calculated by dynamic routing algorithms into the static routing table. -

Dynamic Routing: Routing Information Protocol
CS 356: Computer Network Architectures Lecture 12: Dynamic Routing: Routing Information Protocol Chap. 3.3.1, 3.3.2 Xiaowei Yang [email protected] Today • ICMP applications • Dynamic Routing – Routing Information Protocol ICMP applications • Ping – ping www.duke.edu • Traceroute – traceroute nytimes.com • MTU discovery Ping: Echo Request and Reply ICMP ECHO REQUEST Host Host or or Router router ICMP ECHO REPLY Type Code Checksum (= 8 or 0) (=0) identifier sequence number 32-bit sender timestamp Optional data • Pings are handled directly by the kernel • Each Ping is translated into an ICMP Echo Request • The Pinged host responds with an ICMP Echo Reply 4 Traceroute • xwy@linux20$ traceroute -n 18.26.0.1 – traceroute to 18.26.0.1 (18.26.0.1), 30 hops max, 60 byte packets – 1 152.3.141.250 4.968 ms 4.990 ms 5.058 ms – 2 152.3.234.195 1.479 ms 1.549 ms 1.615 ms – 3 152.3.234.196 1.157 ms 1.171 ms 1.238 ms – 4 128.109.70.13 1.905 ms 1.885 ms 1.943 ms – 5 128.109.70.138 4.011 ms 3.993 ms 4.045 ms – 6 128.109.70.102 10.551 ms 10.118 ms 10.079 ms – 7 18.3.3.1 28.715 ms 28.691 ms 28.619 ms – 8 18.168.0.23 27.945 ms 28.028 ms 28.080 ms – 9 18.4.7.65 28.037 ms 27.969 ms 27.966 ms – 10 128.30.0.246 27.941 ms * * Traceroute algorithm • Sends out three UDP packets with TTL=1,2,…,n, destined to a high port • Routers on the path send ICMP Time exceeded message with their IP addresses until n reaches the destination distance • Destination replies with port unreachable ICMP messages Path MTU discovery algorithm • Send packets with DF bit set • If receive an ICMP error message, reduce the packet size Today • ICMP applications • Dynamic Routing – Routing Information Protocol Dynamic Routing • There are two parts related to IP packet handling: 1. -

Improving the Convergence of IP Routing Protocols
Improving the Convergence of IP Routing Protocols Pierre Francois Thesis submitted in partial fulfillment of the requirements for the Degree of Doctor in Applied Sciences October 30, 2007 Département d’Ingénierie Informatique Faculté des Sciences Appliquées Université catholique de Louvain Louvain-la-Neuve Belgium Thesis Committee: Yves Deville (Chair) Université catholique de Louvain, BE Clarence Filsfils Cisco Systems Laurent Mathy Lancaster University, UK Jennifer Rexford Princeton University, USA Roch Guérin University of Pennsylvania, USA Guy Leduc Université de Liège, BE Olivier Bonaventure (Advisor) Université catholique de Louvain, BE Philippe Delsarte Université catholique de Louvain, BE Preamble The IP protocol suite has been initially designed to provide best effort reachability among the nodes of a network or an inter-network. The goal was to design a set of routing solutions that would allow routers to automatically provide end-to-end connectivity among hosts. Also, the solution was meant to recover the connectivity upon the failure of one or multiple devices supporting the service, without the need of manual, slow, and error-prone reconfigurations. In other words, the requirement was to have an Internet that "converges" on its own. Along with the "Internet Boom", network availability expectations increased, as e-business emerged and companies started to associate loss of Internet connec- tivity with loss of customers... and money. So, Internet Service Providers (ISPs) relied on best practice rules for the design and the configuration of their networks, in order to improve their Quality of Service. The same routing suite is now used by Internet Service Providers that have to cope with more and more stringent Service Level Agreements (SLAs). -

Chapter 4 Dynamic Routing
CHAPTER 4 DYNAMIC ROUTING In this chapter we cover the basic principles of dynamic routing algorithms that form the basis of the experiments in Lab 4. The chapter has six sections. Each section covers material that you need to run the lab exercises. The first section gives an overview of dynamic routing protocols and discusses the differences between the two major classes of routing algorithms: intra domain and inter domain. Sections 2, 3, 4, and 5 give an overview of the most common routing algorithms such , RIP, OSPF, BGP and IGRP. Section 6 presents the commands used to configure the hosts and the routers for dynamic routing. TABLE OF CONTENT 1 ROUTING PROTOCOLS ........................................................................................................................ 3 1.1 AUTONOMOUS SYSTEMS (AS)............................................................................................................ 3 1.2 INTRADOMAIN ROUTING VERSUS INTERDOMAIN ROUTING ............................................................... 4 1.3 DYNAMIC ROUTING ............................................................................................................................ 4 1.3.1 Distance Vector Algorithm ........................................................................................................... 4 2 RIP ............................................................................................................................................................... 5 3 OSPF........................................................................................................................................................... -

Reinforcement Learning for Routing in Communication Networks
Reinforcement Learning for Routing in Communication Networks Walter H. Andrag Thesis presented in partial fulfilment of the requirements for the degree of Master of Science at the University of Stellenbosch Supervisor: Prof Christian W. Omlin April 2003 Stellenbosch University http://scholar.sun.ac.za Declaration I, the undersigned, hereby declare that the work contained in this thesis is my own original work and has not previously in its entirety or in part been submitted at any university for a degree. Signature: Date: .~ Stellenbosch University http://scholar.sun.ac.za Abstract Routing policies for packet-switched communication networks must be able to adapt to changing traffic patterns and topologies. We study the feasibility of implementing an adaptive routing policy using the Q-Learning algorithm which learns sequences of actions from delayed rewards. The Q-Routing algorithm adapts a network's routing policy based on local information alone and converges toward an optimal solution. We demonstrate that Q-Routing is a viable alternative to other adaptive routing methods such as Bellman-Ford. We also study variations of Q-Routing designed to better explore possible routes and to take into consideration limited buffer size and optimize multiple objectives. 11 Stellenbosch University http://scholar.sun.ac.za Opsomming Die roetering in kommunikasienetwerke moet kan aanpas by veranderings in netwerk- topologie en verkeersverspreidings. Ons bestudeer die bruikbaarheid van 'n aanpasbare roeteringsalgoritme gebaseer op die "Q-Learning"-algoritme wat dit moontlik maak om 'n reeks besluite te kan neem gebaseer op vertraagde vergoedings. Die roeteringsalgo- ritme gebruik slegs nabygelee inligting om roeteringsbesluite te maak en konvergeer na 'n optimale oplossing. -

RIP: Routing Information Protocol a Routing Protocol Based on the Distance-Vector Algorithm
Laboratory 6 RIP: Routing Information Protocol A Routing Protocol Based on the Distance-Vector Algorithm Objective The objective of this lab is to configure and analyze the performance of the Routing Information Protocol (RIP) model. Overview A router in the network needs to be able to look at a packet’s destination address and then determine which of the output ports is the best choice to get the packet to that address. The router makes this decision by consulting a forwarding table. The fundamental problem of routing is: How do routers acquire the information in their forwarding tables? Routing algorithms are required to build the routing tables and hence forwarding tables. The basic problem of routing is to find the lowest-cost path between any two nodes, where the cost of a path equals the sum of the costs of all the edges that make up the path. Routing is achieved in most practical networks by running routing protocols among the nodes. The protocols provide a distributed, dynamic way to solve the problem of finding the lowest-cost path in the presence of link and node failures and changing edge costs. One of the main classes of routing algorithms is the distance-vector algorithm. Each node constructs a vector containing the distances (costs) to all other nodes and distributes that vector to its immediate neighbors. RIP is the canonical example of a routing protocol built on the distance-vector algorithm. Routers running RIP send their advertisements regularly (e.g., every 30 seconds). A router also sends an update message whenever a triggered update from another router causes it to change its routing table. -

WMM - Wireless Mesh Monitoring
WMM - Wireless Mesh Monitoring Ricardo Pinto [email protected] Instituto Superior T´ecnico Advisor: Professor Lu´ısRodrigues Abstract. Wireless Mesh Networks (WMN) have emerged as a poten- tial technology to quickly deploy a wireless infrastructure that is self- healing, self-configured, and self-organized. This report makes an in- troduction to WMNs, their protocols and some existing deployments. Then the problem of monitoring the operation of these networks, is ad- dressed by making a brief survey on some relevant network monitoring approaches and by pointing directions of future work in this area. 1 Introduction Within the short span of a decade, wireless networks have revolutionized the way we use our devices, bringing us cable-free mobility, always-on connectiv- ity, and reduced infrastructure costs. In the past few years, we have witnessed a tremendous growth of wireless LANs (WLANs) mainly due to their ease of deployment and maintenance. However, all wireless access points (APs) need to be connected to the wired backbone network and, therefore, WLANs still re- quire extensive infrastructure and careful planning in order to minimize their costs. Wireless Mesh Networks (WMNs) have emerged as a key technology to ease the deployment of wireless networks. Unlike traditional WiFi networks, in WMNs only a subset of APs are required to be connected to the wired network. As a result, only a subset of the nodes need wired infrastructure (these nodes serve as gateways) while the other mesh nodes have the ability to route mes- sages to the gateways, thus providing also access to the Internet. A WMN is a dynamically self-organized and self-configured network in which the nodes au- tomatically establish and maintain connectivity. -

Babel Routing Protocol for Omnet++ More Than Just a New Simulation Module for INET Framework
Babel Routing Protocol for OMNeT++ More than just a new simulation module for INET framework Vladimír Veselý, Vít Rek, Ondřej Ryšavý Department of Information Systems, Faculty of Information Technology Brno University of Technology Brno, Czech Republic {ivesely, rysavy}@fit.vutbr.cz; [email protected] Abstract—Routing and switching capabilities of computer Device discovery protocols such as Cisco Discovery networks seem as the closed environment containing a limited set Protocol (CDP) and Link Layer Discovery Protocol of deployed protocols, which nobody dares to change. The (LLDP), which verify data-link layer operation. majority of wired network designs are stuck with OSPF (guaranteeing dynamic routing exchange on network layer) and In this paper, we only focus on a Babel simulation model. RSTP (securing loop-free data-link layer topology). Recently, Babel is increasingly more popular seen as the open-source more use-case specific routing protocols, such as Babel, have alternative to Cisco’s Enhanced Interior Gateway Routing appeared. These technologies claim to have better characteristic Protocol (EIGRP). Babel is also considered a better routing than current industry standards. Babel is a fresh contribution to protocol for mobile networks comparing to Destination- the family of distance-vector routing protocols, which is gaining its Sequenced Distance-Vector (DSDV) or Ad hoc On-Demand momentum for small double-stack (IPv6 and IPv4) networks. This Distance-Vector (AODV) routing protocols. Babel is a hybrid paper briefly describes Babel behavior and provides details on its distance vector routing protocol. Although it stems from a implementation in OMNeT++ discrete event simulator. classical distributed Bellman-Ford algorithm, it also adopts certain features from link-state protocols, such as proactive Keywords—Babel, OMNeT++, INET, Routing, Protocols, IPv6, neighbor discovery. -
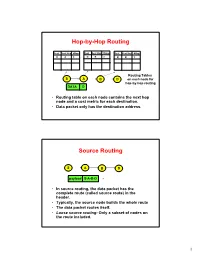
Hop-By-Hop Routing Source Routing
Hop-by-Hop Routing Dest. Next Hop #Hops Dest. Next Hop #Hops Dest. Next Hop #Hops D A 3 D B 2 D D 1 Routing Tables S A B D on each node for hop-by-hop routing DATA D • Routing table on each node contains the next hop node and a cost metric for each destination. • Data packet only has the destination address. Source Routing S A B D payload S-A-B-D • In source routing, the data packet has the complete route (called source route) in the header. • Typically, the source node builds the whole route • The data packet routes itself. • Loose source routing: Only a subset of nodes on the route included. 1 Static vs. Dynamic Routing • Static routing has fixed routes, set up by network administrators, for example. • Dynamic routing is network state- dependent. Routes may change dynamically depending on the “state” of the network. • State = link costs. Switch traffic from highly loaded links to less loaded links. Distributed, Dynamic Routing Protocols • Distributed because in a dynamic network, no single, centralized node “knows” the whole “state” of the network. • Dynamic because routing must respond to “state” changes in the network for efficiency. • Two class of protocols: Link State and Distance Vector. 2 Link State Protocol • Each node “floods” the network with link state packets (LSP) describing the cost of its own (outgoing) links. – Link cost metric = typically delay for traversing the link. – Every other node in the network gets the LSPs via the flooding mechanism. • Each node maintains a LSP database of all LSPs it received. -

Improving Convergence Time of Routing Protocols
Improving Convergence Time of Routing Protocols Gotz¨ Lichtwald, Uwe Walter and Martina Zitterbart Institute of Telematics University of Karlsruhe, Germany Email: {lichtwald, walter, zit}@tm.uka.de Abstract— One of the main design goals of the Internet is but normal routing protocol traffic takes this function and robustness against failures. Normally, this is accomplished by is used as regular alive beacon. redundancy and dynamic routing protocols that automatically In order to further limit resource consumption, rather adapt to failures: If a link is unavailable, data packets can gen- erally be sent via alternative paths. An essential requirement long time intervals between consecutive check messages for this is a fast mechanism for failure detection, since routing have been chosen. This also helps to reduce the number protocols can only start to reroute traffic around problems as of so-called false positives. Whenever a link is wrongly soon as they get aware of them. This paper proposes a novel declared to be broken, due to several short-time link noise design of a generic failure detection service to be utilized periods or temporarily router processor overload this is by routing protocols that aims at dramatically decreasing the detection times of today’s mechanisms. After the introduction called a false positive. of the concept and its evaluation, the integration of the new It is a permanent tradeoff that must be found between failure detection service into BGP is described. Furthermore, a delayed failure detection and too many false positives. an example for the adaption of a routing protocol using the If a link breakdown has occurred, but has not yet been proposed service is given. -

Achieving Sub-Second IGP Convergence in Large IP Networks∗
Achieving sub-second IGP convergence in large IP networks∗ Pierre Francois Clarence Filsfils and Olivier Bonaventure Dept CSE, Universite´ John Evans Dept CSE, Universite´ catholique de Louvain (UCL), Cisco Systems catholique de Louvain (UCL), Belgium Belgium fcf,[email protected] [email protected] [email protected] ABSTRACT 16]. Nowadays, following the widespread deployment of real time We describe and analyse in details the various factors that influence applications such as VoIP and the common use of Virtual Private the convergence time of intradomain link state routing protocols. Networks (VPN), much tighter Service Level Agreements (SLA) This convergence time reflects the time required by a network to are required, leading to LS IGP convergence requirements from react to the failure of a link or a router. To characterise the con- sub-3-second to sub-second. [11, 10]. vergence process, we first use detailed measurements to determine the time required to perform the various operations of a link state This paper shows that sub-second LS IGP convergence can be con- protocol on currently deployed routers. We then build a simulation servatively met on a SP network without any compromise on sta- model based on those measurements and use it to study the conver- bility. gence time in large networks. Our measurements and simulations indicate that sub-second link-state IGP convergence can be easily The paper is structured as follows: we firstly provide an overview met on an ISP network without any compromise on stability. of a typical IS-IS convergence. While for ease of reading we use the IS-IS terminology throughout the paper, the analysis equally Categories and Subject Descriptors applies to OSPF.