Future of Identity in the Information Society Summary
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Technology Options for the European Electronic Toll Service
DIRECTORATE GENERAL FOR INTERNAL POLICIES POLICY DEPARTMENT B: STRUCTURAL AND COHESION POLICIES TRANSPORT AND TOURISM TECHNOLOGY OPTIONS FOR THE EUROPEAN ELECTRONIC TOLL SERVICE STUDY This document was requested by the European Parliament's Committee on Transport and Tourism. AUTHORS Steer Davies Gleave - Francesco Dionori, Lucia Manzi, Roberta Frisoni Universidad Politécnica de Madrid - José Manuel Vassallo, Juan Gómez Sánchez, Leticia Orozco Rendueles José Luis Pérez Iturriaga – Senior Consultant Nick Patchett - Pillar Strategy RESPONSIBLE ADMINISTRATOR Marc Thomas Policy Department Structural and Cohesion Policies European Parliament B-1047 Brussels E-mail: [email protected] EDITORIAL ASSISTANCE Nóra Révész LINGUISTIC VERSIONS Original: EN ABOUT THE PUBLISHER To contact the Policy Department or to subscribe to its monthly newsletter please write to: [email protected] Manuscript completed in April 2014. © European Union, 2014. This document is available on the Internet at: http://www.europarl.europa.eu/studies DISCLAIMER The opinions expressed in this document are the sole responsibility of the author and do not necessarily represent the official position of the European Parliament. Reproduction and translation for non-commercial purposes are authorised, provided the source is acknowledged and the publisher is given prior notice and sent a copy. DIRECTORATE GENERAL FOR INTERNAL POLICIES POLICY DEPARTMENT B: STRUCTURAL AND COHESION POLICIES TRANSPORT AND TOURISM TECHNOLOGY OPTIONS FOR THE EUROPEAN ELECTRONIC TOLL SERVICE STUDY Abstract This study has been prepared to review current and future technological options for the European Electronic Toll Service. It discusses the strengths and weaknesses of each of the six technologies currently in existence. It also assesses on-going technological developments and the way forward for the European Union. -

Alternative Ways of Funding Public Transport
Alternative Ways of Funding Public Transport A Case Study Assessment Barry Ubbels1, Peter Nijkamp1, Erik Verhoef1, Steve Potter2, Marcus Enoch2 1 Department of Spatial Economics, Free University Amsterdam, The Netherlands 2 Faculty of Technology, The Open University, Walton Hall, Milton Keynes, United Kingdom EJTIR, 1, no.1 (2001), pp. 73 - 89 Received: July 2000 Accepted: August 2000 Public transport traditionally has been, and still is, heavily subsidised by local or national governments, which have been motivated by declining average cost arguments, social considerations, and the desire to offer an alternative to private car use. Conventional sources for funding, including general taxes on labour, in many occasions have become harder to sustain for various reasons. This paper explores alternative, increasingly implemented, sources of funding, i.e., local charges or taxes that are hypothecated to support (urban) public transport (such as local sales taxes, parking charges etc.). Based on an overview of several case-studies all over the world, it is found that there is a large potential for applying unconventional charging mechanisms. Not only as means of raising financial support for public transport systems, but also as a method of sending appropriate (from a sustainable point of view) pricing signals to transport use. 1. Introduction Public transport refers to a collective transport system, which is made available, usually against payment, for any person who wishes to use it. Public transportation services can be provided at various scale levels and can take different forms. Common in many cities is the public bus and to a lesser extent the tram. Fewer countries have underground services or rapid rail. -

Autopista Central, S.A. the Valuation of a Toll Road Project in Chile
The Fuqua School of Business at Duke University FUQ-04-2010 Rev. April 30, 2010 Autopista Central, S.A. The Valuation of a Toll Road Project in Chile Manuel Flores arrived to his office in Madrid on Monday after a relaxing weekend spent with his family. It was mid-November 2007 and Flores, senior vice-president of Business Development for the Spanish construction and services company ACS, had spent the last three weeks visiting ACS project sites in Latin America. Upon his return to Spain, he had had gone to a three-day infrastructure and project finance conference in Majorca where many of the most important players in the industry had been in attendance. At the conference Flores was approached by Juan Albán from the toll-road and airport operator Abertis and Sergio Sandoval from the private equity arm of Santander Bank who had an interesting proposition for him. Specifically, Albán and Sandoval expressed considerable interest in jointly buying ACS’ stake in a 61 kilometer toll-road that the firm had constructed and was now co- operating in the Chilean capital of Santiago. ACS had a 48% equity stake in this venture known in Chile as Autopista Central or “Central Highway” which had received investment of more than USD 800 million by 2007. Although some had recently begun to speculate that world asset prices had reached a peak, companies like Abertis and Santander still had appetite for infrastructure projects that they viewed as being relatively safe investments. Flores, Albán, and Sandoval had had a series of informal meetings regarding Autopista Central at the conference in which the group decided that Flores would discuss the idea of a sale of ACS’ stake with the firm’s CEO, Florentino Pérez, as soon as possible. -

Corredor Sur Trust
OFFERING MEMORANDUM US$150,000,000 CORREDOR SUR TRUST 6.95% Notes due 2025 The Issuer, BG Trust, Inc., not in its individual capacity, but solely as trustee of the Corredor Sur Trust, formed under Law 1 of 1984 of the Republic of Panama, pursuant to an irrevocable trust agreement to be entered into with ICA Panama, S.A., as settlor and secondary beneficiary, will issue the notes. The Issuer will pay interest and principal on the notes on the 25th day of each May, August, November and February of each year, commencing on August 25, 2005 in the case of interest and on August 25, 2008 in the case of principal. The notes will mature on May 25, 2025. The Issuer may, at its option, redeem some or all of the notes at any time after the third anniversary of the date of issuance of the notes at the redemption prices described in this offering memorandum. The Issuer may also redeem the notes at any time in the event of certain tax law changes requiring payment of additional amounts as described in this offering memorandum. The notes will be senior secured obligations of the Issuer and will rank equally without any preference among themselves. The notes will be secured by a first priority lien on substantially all of the assets of the Issuer. The primary beneficiary under the trust agreement will be The Bank of New York, as trustee under the indenture governing the notes. Under an assignment agreement, ICA Panama, S.A. will assign to the Issuer certain of its rights, including its rights to receive tolls generated by the Corredor Sur toll road in Panama City under a concession granted by the Panamanian government, proceeds from certain ancillary service agreements, and certain payments from the Panamanian government, in each case as more fully described herein. -

Mfg Investment Fund Plc
MFG INVESTMENT FUND PLC (An open-ended umbrella investment company with segregated liability between sub-funds) Annual Report and Audited Financial Statements For the financial year ended 31 March 2020 Company Registration No. 525177 MFG INVESTMENT FUND PLC Annual Report and Audited Financial Statements For the financial year ended 31 March 2020 CONTENTS Page General Information 2 Background to the Company 3 Investment Manager’s Report 5 Directors’ Report 8 Depositary’s Report 11 Independent Auditor’s Report 12 Statement of Comprehensive Income 15 Statement of Financial Position 17 Statement of Changes in Net Assets Attributable to Holders of Redeemable Participating Shares 19 Statement of Cash Flows 21 Notes to the Financial Statements 23 Schedule of Investments 38 Schedule of Significant Portfolio Changes (unaudited) 48 Risk Item (unaudited) 53 UCITS Remuneration Disclosure (unaudited) 54 Appendix I - Securities Financing Transactions Regulation (unaudited) 55 Appendix II - CRS Data Protection Information Notice (unaudited) 56 1 MFG INVESTMENT FUND PLC Annual Report and Audited Financial Statements For the financial year ended 31 March 2020 GENERAL INFORMATION Directors Registered Office of the Company Bronwyn Wright* (Irish) 32 Molesworth Street Jim Cleary* (Irish) Dublin 2 Craig Wright (Australian) Ireland Investment Manager and Distributor Company Secretary MFG Asset Management MFD Secretaries Limited MLC Centre, Level 36 32 Molesworth Street 19 Martin Place Dublin 2 Sydney Ireland NSW 2000 Australia Depositary Northern Trust Fiduciary Administrator & Registrar Service (Ireland) Limited Northern Trust International Fund Administration Georges Court Services (Ireland) Limited 54-62 Townsend Street Georges Court Dublin 2 54-62 Townsend Street Ireland Dublin 2 Ireland Legal Advisers Maples and Calder Independent Auditor 75 St. -

Unconventional Funding of Urban Public Transport
Transportation Research Part D 7 (2002) 317–329 www.elsevier.com/locate/trd Unconventional funding of urban public transport Barry Ubbels *, Peter Nijkamp Department of Regional Economics, Free University, De Boelelaan 1105, 1081 HV Amsterdam, Netherlands Abstract In the past decade public authorities have developed a wealth of creative funding mechanisms to support transit systems. This paper offers a taxonomy of various unconventional funding mechanisms (i.e. outside the domain of charges for transit passengers or general taxation schemes), based on a review of financial arrangements for public transport. The paper identifies which classes of funding are particularly successful for the financing of transit systems. This cross-sectional analysis uses a type of artificial intelligence method, viz. rough set analysis. It appears that the nature of the funding scheme and the degree of public accept- ability are mainly responsible for the success of unconventional funding mechanisms. Ó 2002 Elsevier Science Ltd. All rights reserved. 1. Introduction Urban public transport––defined as publicly provided mass transit systems in cities––is often regarded as a less environmentally damaging mode of transport and in many countries generates much, sometimes uncritical, policy support. As a consequence, deficits in this sector are not charged to the user, but to the taxpayer. The awareness is growing, however, that alterna- tive sources of revenue may be necessary to keep transit systems intact or to finance new in- vestments. In the past, public transport companies have been supported primarily by federal, state and local funds and revenues from fares. Governments are involved in the financing and operation of this activity, because urban public transportation is an unprofitable business. -

Road Pricing in Theory and Practice: a Canadian Perspective
The Peter A. Allard School of Law Allard Research Commons Faculty Publications Allard Faculty Publications 2005 Road Pricing in Theory and Practice: A Canadian Perspective David G. Duff Allard School of Law at the University of British Columbia, [email protected] Carl Irvine Follow this and additional works at: https://commons.allard.ubc.ca/fac_pubs Part of the Tax Law Commons Citation Details David G Duff & Carl Irvine, "Road Pricing in Theory and Practice: A Canadian Perspective" (2005) U Toronto, Legal Studies Research Paper No. 05-07. This Research Paper is brought to you for free and open access by the Allard Faculty Publications at Allard Research Commons. It has been accepted for inclusion in Faculty Publications by an authorized administrator of Allard Research Commons. Road Pricing in Theory and Practice: A Canadian Perspective David G. Duff* and Carl Irvine+ I. Introduction Like other developed countries, Canada experienced massive increases in road transportation since the end of the Second World War, with substantial growth in the number of registered vehicles,1 annual per capita distances traveled by automobile,2 and the volume of goods transported by truck.3 At first, Canadian governments attempted to match the growing demand for road transportation by improving the quality and capacity of roads and highways – significantly increasing the extent of paved roadways and introducing a national highway system supported by federal shared-cost funding.4 Throughout this period, the cost of constructing and maintaining Canada’s road network was financed mostly from consolidated revenue funds and municipal property taxes, though federal and municipal governments levied taxes on automotive fuels and provincial governments collected vehicle registration fees that also contributed to these revenues.5 Since the 1970s, Canadian governments have been less willing to invest in roads and highways,6 as growing environmental concerns lessened public enthusiasm for * Associate Professor, Faculty of Law, University of Toronto ([email protected]). -

The Future Impact of ICT on Environmental Sustainability
Institute for Futures Studies and Technology Assessment (IZT) Swiss Federal Laboratories for Materials Testing and Research Sustainable Information Technology Unit (EMPA-SIT) Forum for the Future International Institute for Industrial Environmental Economics at Lund University (IIIEE) The future impact of ICT on environmental sustainability Second Interim Report “Script” Lorenz Erdmann (IZT) Siegfried Behrendt (IZT) submitted to Institute for Prospective Technological Studies (IPTS), Sevilla Berlin, May 2003 Chapter 1 Legal notice Neither the European Commission nor any person acting on behalf of the Commission is responsible for the use which might be made of the following information. © European Communities, 2003. Reproduction is authorized provided the source is acknowledged. 2 Executive Summary EXECUTIVE SUMMARY In the script the following ten key trends in ICT with low uncertainty have been identified: 1. Moore’s law continues for 10-15 years 2. Increasing context sensitivity 3. Wireless and mobile networks spread and converge 4. Widespread broadband access 5. Embedded computing and extension of networks into daily appliances 6. Growth of ICT markets 7. Ongoing built-up of ICT infrastructure 8. Parallel development of licensed and free software 9. Improved reliability of authentification systems 10. Improvement of existing ICT services and new location based services The scope of the investigation covers the following 10 fields and 7 indicators: freight passenger modal energy Share of GHG Daily transport transport split consumpt -

Electronic Toll Collection for Efficient Traffic Control
>> Electronic toll collection for efficient traffic control www.thalesgroup.com / transport Summary P. Introduction 3 Development of electronic toll collection in different countries 4 Benefits of electronic toll collection 4 Interoperable toll systems and the European dimension 5 Electronic toll collection and urban traffic control 6 Electronic toll collection as an instrument of road transport policy 7 Electronic toll collection and the legal issues 8 Electronic Road Tolling – looking ahead 8 Pan-European Road Tolling Scheme – A Reality? 8 Tailored solutions from Thales 9 Thales references in conventional and electronic toll collection 9 Electronic toll collection technologies 10 2 In many countries, road tolling has developed rapidly since motorway construction began in the early 1960s. In France, for example, tolls collected between 1995 and 2003 paid for 7,600 kilometres of new motorway – 80% of the entire network. Tolls also finance major investments in existing networks, improving user safety and comfort and even environmental quality. They provide part of the financing for large projects such as bridges and tunnels, which give motorways some of their key advantages over other roads, be it safety or efficiency. The Millau Viaduct is one example. Since the world’s highest roadway opened in December 2004, motorists have had a more direct route to the Mediterranean coast, avoiding the summer traffic that can bring other roads to a standstill. The functional concept of a basic toll system is simple: the motorist takes a ticket at the entrance to the motorway and presents it at the tollbooth at the exit. Ticketing and toll barriers can also be placed on each section of motorway. -

Cohesion Policy and Sustainable Development
COHESION POLICY AND SUSTAINABLE DEVELOPMENT Supporting Paper 3 Role of non-Cohesion Policy Instruments Institute for European Environmental Policy (IEEP) Together with CEE Bankwatch Network BIO Intelligence Service S.A.S. (BIO) GHK Institute for Ecological Economy Research (IÖW) Matrix Insight Netherlands Environmental Assessment Agency (PBL) December 2010 TABLE OF CONTENTS 1 INTRODUCTION ................................................................................................................................. 1 1.1 BACKGROUND ..................................................................................................................................... 1 1.2 APPROACH AND STRUCTURE ................................................................................................................ 2 PART I: SYNTHESIS REPORT ................................................................................................................... 6 2 DELIVERING WIN-WINS BY NON-INVESTMENT POLICY INSTRUMENTS ............................ 7 3 THE POTENTIAL FOR CROWDING OUT OF PRIVATE INVESTMENT .................................... 9 4 SUMMARY OF SHORT-LISTED INSTRUMENTS ......................................................................... 11 4.1 REGULATORY BASIS/CURRENT LEGISLATIVE FRAMEWORK .................................................................. 11 4.2 CURRENT DEPLOYMENT IN THE EU, AND TRENDS IN DEPLOYMENT ...................................................... 12 4.3 TYPE/SCALE OF INVESTMENT THAT MIGHT BE INFLUENCED ................................................................ -

SHOULD GOVERNMENTS LEASE THEIR TOLL ROADS? by Robert W
SHOULD GOVERNMENTS LEASE THEIR TOLL ROADS? by Robert W. Poole, Jr. August 2020 Reason Foundation’s mission is to advance a free society by developing, applying and promoting libertarian principles, including individual liberty, free markets and the rule of law. We use journalism and public policy research to influence the frameworks and actions of policymakers, journalists and opinion leaders. Reason Foundation’s nonpartisan public policy research promotes choice, competition and a dynamic market economy as the foundation for human dignity and progress. Reason produces rigorous, peer- reviewed research and directly engages the policy process, seeking strategies that emphasize cooperation, flexibility, local knowledge and results. Through practical and innovative approaches to complex problems, Reason seeks to change the way people think about issues, and promote policies that allow and encourage individuals and voluntary institutions to flourish. Reason Foundation is a tax-exempt research and education organization as defined under IRS code 501(c)(3). Reason Foundation is supported by voluntary contributions from individuals, foundations and corporations. The views are those of the author, not necessarily those of Reason Foundation or its trustees. SHOULD GOVERNMENTS LEASE THEIR TOLL ROADS? i EXECUTIVE SUMMARY The Covid-19 recession is putting large fiscal stress on state governments, including major negative impacts on their transportation budgets and under-funded pension systems. One tool that may help is called asset monetization, sometimes referred to as infrastructure asset recycling. As practiced in Australia and several other countries, the concept is for a government to sell or lease revenue-producing assets, unlocking their asset values to be used for other high-priority public purposes. -
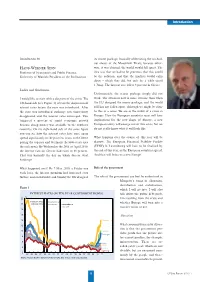
9 Introduction
Introduction Introduction by its rescue package, basically obliterating the no-bail- out clause of the Maastricht Treaty, because other- HANS-WERNER SINN wise, it was claimed, the world would fall apart. The Professor of Economics and Public Finance, idea was that we had to be generous, that this would University of Munich; President of the Ifo Institute be the solution, and that the markets would calm down – which they did, but only for a while (until 1 June). The interest rate fell to 8 percent in Greece. Ladies and Gentlemen, Unfortunately, the rescue package simply did not I would like to start with a diagram of the crisis. The work. The situation now is more extreme than when left-hand side (see Figure 1) reveals the dispersion of the EU designed the rescue package; and the world interest rates before the euro was introduced. After still has not fallen apart, although we might be close the euro was introduced exchange rate uncertainty to this in a sense. We are in the midst of a crisis in disappeared and the interest rates converged. This Europe. How the European countries react will have triggered a process of rapid economic growth implications for the new shape of Europe; a new because cheap money was available to the southern European entity will emerge out of this crisis, but we countries. On the right-hand side of the same figure do not really know what it will look like. you can see how the interest rates have once again spread significantly in the past few years, with Greece What happens over the course of this year will be paying the top rate and Germany the lowest rate (see decisive.