The Shortcut Guide to Securing Automated File Transfers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -
![CERBERUS FTP SERVER 8.0] User Manual for Cerberus FTP Server 8.0](https://docslib.b-cdn.net/cover/6710/cerberus-ftp-server-8-0-user-manual-for-cerberus-ftp-server-8-0-266710.webp)
CERBERUS FTP SERVER 8.0] User Manual for Cerberus FTP Server 8.0
V.8 Cerberus, LLC Grant Averett [CERBERUS FTP SERVER 8.0] User manual for Cerberus FTP Server 8.0. It contains detailed steps and help on configuring Cerberus FTP Server. CONTENTS Introduction .............................................................................................................................................. 11 Description ........................................................................................................................................... 11 Guide .................................................................................................................................................... 11 Minimum System Requirements .............................................................................................................. 12 Hardware Requirements ...................................................................................................................... 12 Operating Systems ................................................................................................................................ 12 Cerberus FTP Server 5.0, 6.0, and 7.0 ............................................................................................... 12 Cerberus FTP Server 8.0 and higher ................................................................................................. 12 Installation ................................................................................................................................................ 13 Upgrading an Existing Installation ............................................................................................................ -

IT Acronyms.Docx
List of computing and IT abbreviations /.—Slashdot 1GL—First-Generation Programming Language 1NF—First Normal Form 10B2—10BASE-2 10B5—10BASE-5 10B-F—10BASE-F 10B-FB—10BASE-FB 10B-FL—10BASE-FL 10B-FP—10BASE-FP 10B-T—10BASE-T 100B-FX—100BASE-FX 100B-T—100BASE-T 100B-TX—100BASE-TX 100BVG—100BASE-VG 286—Intel 80286 processor 2B1Q—2 Binary 1 Quaternary 2GL—Second-Generation Programming Language 2NF—Second Normal Form 3GL—Third-Generation Programming Language 3NF—Third Normal Form 386—Intel 80386 processor 1 486—Intel 80486 processor 4B5BLF—4 Byte 5 Byte Local Fiber 4GL—Fourth-Generation Programming Language 4NF—Fourth Normal Form 5GL—Fifth-Generation Programming Language 5NF—Fifth Normal Form 6NF—Sixth Normal Form 8B10BLF—8 Byte 10 Byte Local Fiber A AAT—Average Access Time AA—Anti-Aliasing AAA—Authentication Authorization, Accounting AABB—Axis Aligned Bounding Box AAC—Advanced Audio Coding AAL—ATM Adaptation Layer AALC—ATM Adaptation Layer Connection AARP—AppleTalk Address Resolution Protocol ABCL—Actor-Based Concurrent Language ABI—Application Binary Interface ABM—Asynchronous Balanced Mode ABR—Area Border Router ABR—Auto Baud-Rate detection ABR—Available Bitrate 2 ABR—Average Bitrate AC—Acoustic Coupler AC—Alternating Current ACD—Automatic Call Distributor ACE—Advanced Computing Environment ACF NCP—Advanced Communications Function—Network Control Program ACID—Atomicity Consistency Isolation Durability ACK—ACKnowledgement ACK—Amsterdam Compiler Kit ACL—Access Control List ACL—Active Current -

Securing 7 Layers of Insecurity
Chapter 63 FTP and HTTP The Art of Serving Files and Content. D 7 eep L ay Se er s “And bring me a hard copy of c o the Internet so I can do some V f I i serious surfing.” e n nn sec a 2007 urity -- Scott Adams Copyright Information Some rights reserved / Einige Rechte vorbehalten Michael Kafka, René Pfeiffer, Sebastian Mayer C.a.T. Consulting and Trainings, Vienna, Austria You may freely use, distribute and modify this work under following D agreement: 7 eep Diese Arbeit darf frei genutzt, verbreitet und bearbeitet werden unter L folgenden Bedingungen: ay Se Authors must be referenced (also for modification) er s Autoren müssen genannt werden (auch bei Bearbeitung) c o V Only for non commercial use f I i Nur für nichtkommerzielle Nutzung e n nn Derivative work under same licence sec Derivative Arbeit unter selber Lizenz a 2007 urity http://www.creativecommons.com © November 2007 63 - FTP and HTTP Chapter 63 FTP and HTTP Agenda FTP Overview HTTP Overview D 7 eep HTTP Attacks L ay Se WebDAV er s c Tunneling o V f I i e n nn sec a 2007 urity © November 2007 63 - FTP and HTTP File Transfer Protocol (FTP) Historical File Transfers. D 7 eep L ay Se er s c o V f I i e n nn sec a 2007 urity © November 2007 63 - FTP and HTTP FTP Overview Born with RFC 114 in 1971, older than TCP FTP uses three modes active FTP, passive FTP and D 7 eep extended passive FTP L ay Se FTP uses two TCP connections er s c Command channel 21/TCP o V f I i Data channel 20/TCP, dynamic/TCP e n nn sec a 2007 urity © November 2007 63 - FTP and HTTP FTP -

ELFIQ APP OPTIMIZER White Paper V1.03 - May 2015 CONTENTS Introduction
ELFIQ APP OPTIMIZER White Paper V1.03 - May 2015 CONTENTS Introduction ...............................................................................................................................................................................3 Signature-Based Recognition vs. ACL’s ................................................................................................................3 Detection Engine ...................................................................................................................................................................3 Using Groups or Individual Applications .............................................................................................................3 Actions Once an Application is Detected ...........................................................................................................3 Appendix A: Application List ........................................................................................................................................ 4 martellotech.com elfiq.com 2 INTRODUCTION The Elfiq AppOptimizer is designed to give organizations full control over their existing and future bandwidth, guaranteeing key applications such as Citrix XenDesktop or Skype get priority treatment and undesirables such as peer-to-peer file transfers or games are limited or no longer permitted. It is an add-on-module that provides application-layer deep packet inspection (layer 7) classification and control, including Mobile, Social Networking, P2P, Instant Messaging, -

FTP and Beyond NASA
LINUX USER GFTP File Transfer with the Versatile GFTP FTP and Beyond NASA Whether you like your file transfers with a GUI or from a command prompt, GFTP has the right tool for every job.The GFTP client also supports advanced features such as secure file transfer with SSH. BY MARTIN STEIGERWALD FTP is a versatile and efficient installed automatically. See the box area shows the current action for a pro- File Transfer Protocol (FTP) labeled “Installing GFTP” for more on tocol. Gclient for Linux systems. GFTP, installing GFTP with Suse or Debian, as Enter the name of the FTP server to which was written by Brian Masney, per- well as details for building GFTP from which you wish to connect in the box forms all the standard chores associated source code. labeled Host at the top of the main win- with downloading and uploading files to dow. You can also enter an FTP FTP servers, and it also offers additional Working with GFTP username and password, and you can services, such as HTTP file transfer, SSH- GFTP launches a classical FTP-style split specify the port number to use for the based file transfer, and simultaneous window, with panels showing the local connection. The split window displays download from multiple servers. The and remote directories (see Figure 1). A the local directory structure on the left GFTP program provides several useful status area below provides information and the remote directories on the right. features that add efficiency to your FTP on the current transfers, and another When you find the file you wish to trans- sessions, such as drag and drop, intelli- gent prompting for existing files, direct Installing GFTP input for FTP commands, and direct If you have Suse Linux,you can run YaST | also means that the menu items created by transfer between two FTP servers. -
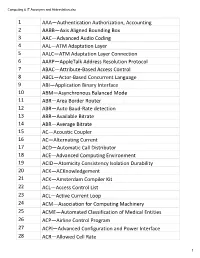
Computing & IT Acronyms and Abbreviation.Xlsx
Computing & IT Acronyms and Abbreviation.xlsx 1 AAA—Authentication Authorization, Accounting 2 AABB—Axis Aligned Bounding Box 3 AAC—Advanced Audio Coding 4 AAL—ATM Adaptation Layer 5 AALC—ATM Adaptation Layer Connection 6 AARP—AppleTalk Address Resolution Protocol 7 ABAC—Attribute-Based Access Control 8 ABCL—Actor-Based Concurrent Language 9 ABI—Application Binary Interface 10 ABM—Asynchronous Balanced Mode 11 ABR—Area Border Router 12 ABR—Auto Baud-Rate detection 13 ABR—Available Bitrate 14 ABR—Average Bitrate 15 AC—Acoustic Coupler 16 AC—Alternating Current 17 ACD—Automatic Call Distributor 18 ACE—Advanced Computing Environment 19 ACID—Atomicity Consistency Isolation Durability 20 ACK—ACKnowledgement 21 ACK—Amsterdam Compiler Kit 22 ACL—Access Control List 23 ACL—Active Current Loop 24 ACM—Association for Computing Machinery 25 ACME—Automated Classification of Medical Entities 26 ACP—Airline Control Program 27 ACPI—Advanced Configuration and Power Interface 28 ACR—Allowed Cell Rate 1 Computing & IT Acronyms and Abbreviation.xlsx 29 ACR—Attenuation to Crosstalk Ratio 30 AD—Active Directory 31 AD—Administrative Domain 32 ADC—Analog-to-Digital Converter 33 ADC—Apple Display Connector 34 ADB—Apple Desktop Bus 35 ADCCP—Advanced Data Communications Control Procedures 36 ADO—ActiveX Data Objects 37 ADSL—Asymmetric Digital Subscriber Line 38 ADT—Abstract Data Type 39 AE—Adaptive Equalizer 40 AES—Advanced Encryption Standard 41 AF—Anisotropic Filtering 42 AFP—Apple Filing Protocol 43 AGP—Accelerated Graphics Port 44 AH—Active Hub 45 AI—Artificial -

Open-E DATA STORAGE SERVER
Open-E DATA STORAGE SERVER Manual (Ver. 5.00 up49) November 19, 2008 2 1 Before you get started .............................................................................. 5 1.1 Contents of this package ..................................................................................... 5 1.2 System requirements ............................................................................................ 5 1.3 Supported clients ................................................................................................. 5 1.4 Supported network protocols ............................................................................... 6 1.5 Supported network file protocols ......................................................................... 6 1.6 Required tools ...................................................................................................... 6 1.7 Safety precautions ................................................................................................ 6 1.7.1 Personal safety ............................................................................................ 6 1.7.2 Safety for your data ..................................................................................... 6 1.7.3 ESD precautions .......................................................................................... 6 2 Features ..................................................................................................... 7 2.1 What is Open-E Data Storage Server .................................................................. -

E-Squads: a Novel Paradigm to Build Privacy-Preserving Ubiquitous Applications
E-squads : a novel paradigm to build privacy-preserving ubiquitous applications Adrien Luxey To cite this version: Adrien Luxey. E-squads : a novel paradigm to build privacy-preserving ubiquitous applications. Dis- tributed, Parallel, and Cluster Computing [cs.DC]. Université Rennes 1, 2019. English. NNT : 2019REN1S071. tel-02389297v2 HAL Id: tel-02389297 https://tel.archives-ouvertes.fr/tel-02389297v2 Submitted on 30 Mar 2020 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Thèse de doctorat de L’UNIVERSITÉ DE RENNES 1 Comue Université Bretagne Loire École Doctorale N° 601 Mathématiques et Sciences et Technologies de l’Information et de la Communication Spécialité : Informatique Par Adrien LUXEY Les e-squads : Un nouveau paradigme pour la conception d’applications ubiquitaires respectant le droit à la vie privée Thèse présentée et soutenue à Rennes (France), le 29 Novembre 2019 Unité de recherche : Irisa (UMR 6074) Rapporteurs avant soutenance : Romain ROUVOY Professeur des Universités Université de Lille Vivien QUÉMA Professeur des Universités Grenoble INP Composition du Jury : Présidente : Anne-Marie KERMARREC Directrice de recherche Univ Rennes, CNRS, Inria, IRISA Rapporteurs : Romain ROUVOY Professeur des Universités Université de Lille Vivien QUÉMA Professeur des Universités Grenoble INP Examinatrice : Sonia BEN MOKHTAR Directrice de recherche CNRS Lyon Dir. -

UD5 Instalación Y Administración De Servicios De Transferencia De Ficheros
2011- 2012 UD5 Instalación y administración de servicios de transferencia de ficheros José Jiménez Arias IES Gregorio Prieto 2011-2012 UD5 Instalación y administración de servicios de transferencia de ficheros 2011-2012 ÍNDICE 1. Funcionalidad del servicio de transferencia de archivos. - Características. Componentes y funcionamiento. - Protocolo FTP. - Tipos de usuarios y accesos al servicio: Acceso anónimo y acceso autorizado. - Configuración del servicio de transferencia de archivos. Permisos y cuotas. - Conexiones y modos: Conexión de control y conexión de datos. Modos activo y pasivo. - Tipos de transferencia de archivos: ASCII y Binario. - Clientes FTP: en línea de comandos, entornos “gráficos” y navegadores / exploradores. - Monitorización y registro del servicio de transferencia de archivos. - Seguridad en FTP. - FTPS (FTP/SSL): FTPS Implícito. FTPS Explícito (FTPES) - Protocolo FXP (File eXchange Protocol). 2. Servicio TFTP (Trivial File Transfer Protocol). 3. Servicios SFTP/SCP. 4. Transferencia o distribución de archivos entre iguales (peer- to-peer). - Características. Protocolos. Software. Configuración. Alumno: José Jiménez Arias Módulo: Servicios de Redes e Internet 2 UD5 Instalación y administración de servicios de transferencia de ficheros 2011-2012 1. Funcionalidad del servicio de transferencia de archivos. FTP File Transfer Protocol, 'Protocolo de Transferencia de Ficheros', es un protocolo de red para la transferencia de archivos entre sistemas conectados a una red TCP (Transmission Control Protocol), basado en la arquitectura cliente- servidor. Desde un equipo cliente se puede conectar a un servidor para descargar archivos desde él o para enviarle archivos, independientemente del sistema operativo utilizado en cada equipo. El servicio FTP es ofrecido por la capa de aplicación del modelo de capas de red TCP/IP al usuario, utilizando normalmente el puerto de red 20 y el 21. -

(12) United States Patent (10) Patent No.: US 8,863,298 B2 Akella Et Al
USOO886.3298B2 (12) United States Patent (10) Patent No.: US 8,863,298 B2 Akella et al. (45) Date of Patent: Oct. 14, 2014 (54) SECURE VIRTUAL FILE MANAGEMENT USPC ................................. 726/26, 28, 29; 713/189 SYSTEM See application file for complete search history. (71) Applicant: Mobile Iron, Inc., Mountain View, CA (56) References Cited (US) U.S. PATENT DOCUMENTS (72) Inventors: Venkata Sastry Akella, San Jose, CA 7,870,315 B2 1/2011 Moon (US); Rahul Sharma, San Jose, CA 2005, 0198061 A1 9, 2005 Robinson et al. (US); Sanjeev Krishnan, Bangalore 2007/0050620 A1 3/2007 Pham et al. (IN); Babu Srinivasan, Bangalore (IN) (Continued) (73) Assignee: Mobile Iron, Inc., Mountain View, CA OTHER PUBLICATIONS (US) Author Unknown, BackDoor. Generic 10. ACXS Info, Fix BackDoor. (*) Notice: Subject to any disclaimer, the term of this Generic 10. ACXS PC Errors, How to Guides to Fix Windows Errors patent is extended or adjusted under 35 Fix any PC Errors Fast and Easy Complete How-to PC Fix Guides, U.S.C. 154(b) by 0 days. p. 1-10, Aug. 2010, http://www. pcerrorsfix.org/howtofix/fix BackDoor. Generic 1 O.ACXS-error.html. (21) Appl. No.: 13/734,545 Primary Examiner — Edward Zee (22) Filed: Jan. 4, 2013 (74) Attorney, Agent, or Firm — Van Pelt, Yi & James LLP Prior Publication Data (65) (57) ABSTRACT US 2013/021917.6 A1 Aug. 22, 2013 A virtual file management system provides user access to Related U.S. Application Data managed content on mobile devices. The system comprises storage domains storing the managed content distributively (60) Provisional application No. -

Communications, 2002
A Direct-to-ground Architecture for Supporting Commercial Communications from the International Space Station Alex T. Nguyen, Xiangrong Zhou, Michael Hadjitheodosiou, John. S. Baras Center for Satellite & Hybrid Communication Networks, Institute for Systems Research, University of Maryland, College Park, MD 20742, USA Abstract—We outline the first steps of an effort to start 2. COMMUNICATION OPTIONS defining a communications architecture for supporting broadband data communications from the Figure 1 shows the possible options that a commercial user International Space Station. We focus on a direct-to- can use to transmit data ground architecture, which could serve as an intermediary solution to satisfy near term communications needs of commercial experiments and payloads on the ISS and overcome certain limitations of the current ISS communications infrastructure. We address three communications options and evaluate an architecture for the direct to ground option, focusing on a particular user’s requirements, communications links, and coverage availability. We also discuss system, mobility support and protocol issues that need to be addressed for this solution to be a feasible alternative. 1. INTRODUCTION The deployment of the International Space Station will provide a unique platform for tele-presence / tele-science in space, and generate a vast and diverse set of multimedia and data communication requirements. NASA is currently trying to upgrade the communication capability for Figure 1. Communications alternatives to/from the ISS commercial payloads on the ISS to enable broadband support of a variety of multimedia services. We are 2.1. Option 1: Using existing TDRSS investigating alternative long-term solutions for supporting communications from ISS payloads, including the use of This option is essentially the current communication commercial technology and commercial assets and infrastructure for the ISS, whereby an antenna on the ISS infrastructure in space and on the ground.