User Guide 8.2.4
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Resolving Issues with Network Connectivity
Module 6: Resolving Issues with Network Connectivity Lab: Resolving Network Connectivity Issues (VMs: 10982D-LON-DC1, 10982D-LON-CL1) Exercise 1: Configuring Network Settings Task 1: Verify and configure network settings 1. Switch to LON-CL1. 2. Right-click Start, and then select Windows PowerShell (Admin). 3. At the Windows PowerShell (Admin) command prompt, type the following command, and then press Enter: test-connection LON-DC1 4. At the command prompt, type the following command, and then press Enter: netstat –n 5. If no connections appear, create a connection. To create a connection, in the Type here to search box, type \\LON-DC1 and then press Enter. 6. In File Explorer, double-click NETLOGON. 7. At the command prompt, type the following command, and then press Enter: netstat –n Note: If no connections are present, move on to the next step. 8. Click Start, type Control Panel and then press Enter. 9. In Control Panel, click Network and Internet, and then click Network and Sharing Center. 10. In Network and Sharing Center, click Ethernet. 11. In the Ethernet Status dialog box, click Properties. 12. Click Internet Protocol Version 4 (TCP/IPv4), and then click Properties. 13. In the Properties dialog box, click Obtain an IP address automatically. 14. Click Obtain DNS server address automatically. 15. Click OK to save the changes. 16. In the Ethernet Properties dialog box, click Close. 17. In the Ethernet Status dialog box, click Close. 18. At the Windows PowerShell command prompt, type the following command, and then press Enter: Get-NetIPAddress Task 2: Troubleshoot name resolution 1. -

Operating Procedures for TEM2 FEI Tecnai
Operating Procedures for TEM2 FEI Tecnai Note: Do not press the buttons on the TEM. This will turn the TEM off and will take hours to bring it back up. Please do not reboot the TEM computer. This will turn off the vacuum and the high tension. If you are having problems with the TEM, please find a SMIF staff member immediately. 1) Log usage into the SMIF web site. 2) Check to see if the camera boxes are on. a) The TIA camera box is the box behind the monitors. The switch will be lit green if on. b) The AMT camera box is on the floor under the Cryo holder. The green light above the switch should be on. c) If either of the cameras were off, please find a SMIF staff member to turn on. The cameras must cool down for 1hr before they can be used. 3) If needed, log into the TEM computer. User name is : TEM Users, Password is: tecnai 4) If needed, open the Tecnai User Interface and then open the TIA software. If the TIA software crashes, please find a SMIF staff member. 5) Place LN2 into the cold finger dewar. The LN2 needs to be topped off before each use. Turning on TEM Note: It is important to change the kV before ramping up the Heat to # when turning on the TEM. 1) There are tabs at the top left of the Tecnai software. Go to the Tune tab. Under the Control Pads box click on Fluorescent Background Light button. This turns on the lights on the control panels. -

1. Run Nslookup to Obtain the IP Address of a Web Server in Europe
1. Run nslookup to obtain the IP address of a Web server in Europe. frigate:Desktop drb$ nslookup home.web.cern.ch Server: 130.215.32.18 Address: 130.215.32.18#53 Non-authoritative answer: home.web.cern.ch canonical name = drupalprod.cern.ch. Name: drupalprod.cern.ch Address: 137.138.76.28 Note that the #53 denotes the DNS service is running on port 53. 2. Run nslookup to determine the authoritative DNS servers for a university in Asia. frigate:Desktop drb$ nslookup -type=NS tsinghua.edu.cn Server: 130.215.32.18 Address: 130.215.32.18#53 Non-authoritative answer: tsinghua.edu.cn nameserver = dns2.tsinghua.edu.cn. tsinghua.edu.cn nameserver = dns.tsinghua.edu.cn. tsinghua.edu.cn nameserver = dns2.edu.cn. tsinghua.edu.cn nameserver = ns2.cuhk.edu.hk. Authoritative answers can be found from: dns2.tsinghua.edu.cn internet address = 166.111.8.31 ns2.cuhk.edu.hk internet address = 137.189.6.21 ns2.cuhk.edu.hk has AAAA address 2405:3000:3:6::15 dns2.edu.cn internet address = 202.112.0.13 dns.tsinghua.edu.cn internet address = 166.111.8.30 Note that there can be multiple authoritative servers. The response we got back was from a cached record. To confirm the authoritative DNS servers, we perform the same DNS query of one of the servers that can provide authoritative answers. frigate:Desktop drb$ nslookup -type=NS tsinghua.edu.cn dns.tsinghua.edu.cn Server: dns.tsinghua.edu.cn Address: 166.111.8.30#53 tsinghua.edu.cn nameserver = dns2.edu.cn. -

VNC User Guide 7 About This Guide
VNC® User Guide Version 5.3 December 2015 Trademarks RealVNC, VNC and RFB are trademarks of RealVNC Limited and are protected by trademark registrations and/or pending trademark applications in the European Union, United States of America and other jursidictions. Other trademarks are the property of their respective owners. Protected by UK patent 2481870; US patent 8760366 Copyright Copyright © RealVNC Limited, 2002-2015. All rights reserved. No part of this documentation may be reproduced in any form or by any means or be used to make any derivative work (including translation, transformation or adaptation) without explicit written consent of RealVNC. Confidentiality All information contained in this document is provided in commercial confidence for the sole purpose of use by an authorized user in conjunction with RealVNC products. The pages of this document shall not be copied, published, or disclosed wholly or in part to any party without RealVNC’s prior permission in writing, and shall be held in safe custody. These obligations shall not apply to information which is published or becomes known legitimately from some source other than RealVNC. Contact RealVNC Limited Betjeman House 104 Hills Road Cambridge CB2 1LQ United Kingdom www.realvnc.com Contents About This Guide 7 Chapter 1: Introduction 9 Principles of VNC remote control 10 Getting two computers ready to use 11 Connectivity and feature matrix 13 What to read next 17 Chapter 2: Getting Connected 19 Step 1: Ensure VNC Server is running on the host computer 20 Step 2: Start VNC -

Software User Guide
Cycle Host User's Guide This guide is an evolving document. If you find sections that are unclear, or missing information, please let us know ([email protected]). Please check our website (www.wetlabs.com) periodically for updates. WET Labs, Inc. PO Box 518 Philomath, OR 97370 541-929-5650 fax: 541-929-5277 www.wetlabs.com 28 January 2010 Cycle Host User's Guide Revision 1.04 1/59 Cycle Host Installation The following sub-sections detail the steps necessary to install and run the Cycle Host program (also referred to as "the host") for the first time on a new computer. System Requirements Below are the recommended minimum requirements for a computer to be used to run the host program. Although Windows is currently the only supported operating system, future releases are planned to support Linux and MAC OS as well. Please let us know of your interest in these platforms via [email protected]. Feature Requirements Operating System Windows XP/Vista/2000/2003 (32 and 64 bit versions) Memory 128 Megabytes Disk Space 125 Megabytes (excludes data file storage) Data Port Serial port or USB to Serial adapter supporting 19200 baud Input Devices Keyboard (minimum) Mouse or other pointing device (recommended) Monitor Color, 1024 x 768 (minimum recommended) Table 1: Host Computer System Requirements The Java Runtime Environment The Cycle Host program is written in the JavaTM language developed by Sun Microsystems Inc. For this reason, execution of the host requires the installation of the Java Runtime Environment, or JRE. At the time of this release the current JRE is Version 6 Update 16. -

Command-Line IP Utilities This Document Lists Windows Command-Line Utilities That You Can Use to Obtain TCP/IP Configuration Information and Test IP Connectivity
Guide to TCP/IP: IPv6 and IPv4, 5th Edition, ISBN 978-13059-4695-8 Command-Line IP Utilities This document lists Windows command-line utilities that you can use to obtain TCP/IP configuration information and test IP connectivity. Command parameters and uses are listed for the following utilities in Tables 1 through 9: ■ Arp ■ Ipconfig ■ Netsh ■ Netstat ■ Pathping ■ Ping ■ Route ■ Tracert ARP The Arp utility reads and manipulates local ARP tables (data link address-to-IP address tables). Syntax arp -s inet_addr eth_addr [if_addr] arp -d inet_addr [if_addr] arp -a [inet_address] [-N if_addr] [-v] Table 1 ARP command parameters and uses Parameter Description -a or -g Displays current entries in the ARP cache. If inet_addr is specified, the IP and data link address of the specified computer appear. If more than one network interface uses ARP, entries for each ARP table appear. inet_addr Specifies an Internet address. -N if_addr Displays the ARP entries for the network interface specified by if_addr. -v Displays the ARP entries in verbose mode. -d Deletes the host specified by inet_addr. -s Adds the host and associates the Internet address inet_addr with the data link address eth_addr. The physical address is given as six hexadecimal bytes separated by hyphens. The entry is permanent. eth_addr Specifies physical address. if_addr If present, this specifies the Internet address of the interface whose address translation table should be modified. If not present, the first applicable interface will be used. Pyles, Carrell, and Tittel 1 Guide to TCP/IP: IPv6 and IPv4, 5th Edition, ISBN 978-13059-4695-8 IPCONFIG The Ipconfig utility displays and modifies IP address configuration information. -
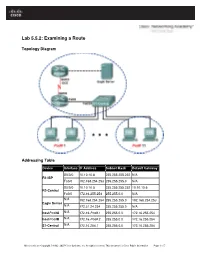
Lab 5.5.2: Examining a Route
Lab 5.5.2: Examining a Route Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway S0/0/0 10.10.10.6 255.255.255.252 N/A R1-ISP Fa0/0 192.168.254.253 255.255.255.0 N/A S0/0/0 10.10.10.5 255.255.255.252 10.10.10.6 R2-Central Fa0/0 172.16.255.254 255.255.0.0 N/A N/A 192.168.254.254 255.255.255.0 192.168.254.253 Eagle Server N/A 172.31.24.254 255.255.255.0 N/A host Pod# A N/A 172.16. Pod#.1 255.255.0.0 172.16.255.254 host Pod# B N/A 172.16. Pod#. 2 255.255.0.0 172.16.255.254 S1-Central N/A 172.16.254.1 255.255.0.0 172.16.255.254 All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 7 CCNA Exploration Network Fundamentals: OSI Network Layer Lab 5.5.1: Examining a Route Learning Objectives Upon completion of this lab, you will be able to: • Use the route command to modify a Windows computer routing table. • Use a Windows Telnet client command telnet to connect to a Cisco router. • Examine router routes using basic Cisco IOS commands. Background For packets to travel across a network, a device must know the route to the destination network. This lab will compare how routes are used in Windows computers and the Cisco router. -

Angel® Concentrated Platelet Rich Plasma (Cprp) System - Operator’S Manual
Angel® Concentrated Platelet Rich Plasma (cPRP) System - Operator’s Manual Software Version 1.20 DFU-0263-5 Revision 0 05/2020 This page intentionally left blank Table of Contents Before You Get Started Introduction .............................................................................................................................................. vii Indications for Use ................................................................................................................................... vii Contraindications for Use ......................................................................................................................... vii Warnings .................................................................................................................................................. vii Precautions ............................................................................................................................................... x Additional Information .............................................................................................................................. xii Symbols .................................................................................................................................................. xiii Requirements for the disposal of waste electrical and electronic equipment (WEEE) ........................... xiv Service Information ................................................................................................................................ -

Copyrighted Material
Index Numerics Address Resolution Protocol (ARP), 1052–1053 admin password, SOHO network, 16-bit Windows applications, 771–776, 985, 1011–1012 900, 902 Administrative Tools window, 1081–1083, 32-bit (x86) architecture, 124, 562, 769 1175–1176 64-bit (x64) architecture, 124, 562, 770–771 administrative tools, Windows, 610 administrator account, 1169–1170 A Administrators group, 1171 ADSL (Asynchronous Digital Subscriber Absolute Software LoJack feature, 206 Line), 1120 AC (alternating current), 40 Advanced Attributes window, NTFS AC adapters, 311–312, 461, 468–469 partitions, 692 Accelerated Graphics Port (AGP), 58 Advanced Computing Environment (ACE) accelerated video cards (graphics initiative, 724 accelerator cards), 388 Advanced Confi guration and Power access points, wireless, 996, 1121 Interface (ACPI) standard, 465 access time, hard drive, 226 Advanced Graphics Port (AGP) card, access tokens, 1146–1147 391–392 Account Operators group, 1172 Advanced Graphics Port (AGP) port, 105 ACE (Advanced Computing Environment) Advanced Host Controller Interface (AHCI), initiative, 724 212–213 ACPI (Advanced Confi guration and Power Advanced Micro Devices (AMD), 141–144 Interface) standard, 465 Advanced Packaging Tool (APT), 572 Action Center, 1191–1192 Advanced Power Management (APM) Active Directory Database, 1145–1146, 1183 standard, 465 active heat sink, 150 Advanced Programmable Interrupt active matrix display, LCD (thin-fi lm Controller (APIC), 374 transistor (TFT) display), 470 Advanced RISC Computing Specifi cation active partition, 267, -

Introduction to Computer Networking
www.PDHcenter.com PDH Course E175 www.PDHonline.org Introduction to Computer Networking Dale Callahan, Ph.D., P.E. MODULE 7: Fun Experiments 7.1 Introduction This chapter will introduce you to some networking experiments that will help you improve your understanding and concepts of networks. (The experiments assume you are using Windows, but Apple, Unix, and Linux systems will have similar commands.) These experiments can be performed on any computer that has Internet connectivity. The commands can be used from the command line using the command prompt window. The commands that can be used are ping, tracert, netstat, nslookup, ipconfig, route, ARP etc. 7.2 PING PING is a network tool that is used on TCP/IP based networks. It stands for Packet INternet Groper. The idea is to verify if a network host is reachable from the site where the PING command issued. The ping command uses the ICMP to verify if the network connections are intact. When a PING command is issued, a packet of 64 bytes is sent to the destination computer. The packet is composed of 8 bytes of ICMP header and 56 bytes of data. The computer then waits for a reply from the destination computer. The source computer receives a reply if the connection between the two computers is good. Apart from testing the connection, it also gives the round trip time for a packet to return to the source computer and the amount of packet loss [19]. In order to run the PING command, go to Start ! Run and in the box type “cmd”. -

User Manual ( Wins Version 5.26.99 )
Wins Scoring System User Manual ( Wins version 5.26.99 ) Srl STELTRONIC via Artigianale 34 • 25082 Botticino Sera (BS) – ITALY Tel. +39 030 2190811 • Fax + 39 030 2190798 http://www.steltronic.com STELTRONIC S.r.l. via Artigianale Botticino Sera (BS) ITALY - User manual [Wins ver 5.26] 2 Tel. +39 030 2190811 Fax +39 030 2190798 http://www.steltronic.com Thank you for choosing Steltronic. This user manual has been written for Wins version 5.26.99, it is also available in pdf format so that it can installed onto a computer. In order to make it easy to consult, the manual has been divided into chapters each covering different subjects: GENERAL Brief Hardware and Scoring System Architecture description. ------------------------------------------------------------------------------------------------------------------------------------ INITIAL USE OF WINDOWS, TURNING THE SYSTEM ON AND OFF Fast guide for ‘first time users’ of the PC and computer system. ------------------------------------------------------------------------------------------------------------------------ SETUP OF THE WINS PROGRAM Contains all the information relative to the program settings from selecting time zones to changing animations. ------------------------------------------------------------------------------------------------------------------------ USING THE SYSTEMS FUCTIONS Description of how to use the lane rental, time game, bar and other programs. ------------------------------------------------------------------------------------------------------------------------ -

Visual Language Features Supporting Human-Human and Human-Computer Communication
Visual Language Features Supporting Human-Human and Human-Computer Communication Jason E. Robbins1, David J. Morley2, David F. Redmiles1, Vadim Filatov3, Dima Kononov3 1 University of California, Irvine 2 Rockwell International 3RR-Gateway, AO Abstract relationships and then try to model them as closely as pos- sible while abstracting details that distract attention from Fundamental to the design of visual languages are the our main concerns. goals of facilitating communication between people and Currently, OBPE exists as a research prototype serving computers, and between people and other people. The to explore the concepts and features that are needed to Object Block Programming Environment (OBPE) is a visual design, programming, and simulation tool which allow effective visual programming in our domain. OBPE emphasizes support for both human-human and human- programs are composed of object blocks, ports, and arcs. computer communication. OBPE provides several features Object blocks use ports as their interface points to the rest to support effective communication: (1) multiple, of the system. Arcs are message passageways between coordinated views and aspects, (2) customizable graphics, ports. Object blocks (or simply, blocks) are visual abstract (3) the “machines with push-buttons” metaphor, and (4) data types [1] which encapsulate state, behavior, visualiza- the host/transient pattern. OBPE uses a diagram-based, tion of state and behavior, and user interface event process- visual object-oriented language that is intended for quickly ing. Furthermore, blocks are first class objects because they designing and programming visual simulations of are instances of normal Smalltalk classes.1 factories. Users interact with OBPE through browsers that allow direct manipulation of blocks and visualization of their 1.