Flexible Updates of Embedded Systems Using Containers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Enabling the Use of Low Power Mobile and Embedded Technologies For
Enabling the Use of Embedded and Mobile Technologies for High-Performance Computing Author: Advisor: Nikola Rajovic´ Alex Ramirez A THESIS SUBMITTED IN FULFILMENT OF THE REQUIREMENTS FOR THE DEGREE OF Doctor per la Universitat Polit`ecnicade Catalunya Departament d’Arquitectura de Computadors Barcelona, Spring 2017 To my family . Моjоj породици . Acknowledgements During my PhD studies I received help and support from many people - it would be strange if I did not. Thus I would like to thank professors Mateo Valero and Veljko Milutinovi´cfor recognizing my interest in HPC and introducing me to my advisor, professor Alex Ramirez. I would like to thank him for trusting in me and giving me an opportunity to be a pioneer of HPC on mobile ARM platforms, for guiding and shaping my work last five years, for helping me understand what real priorities are, and for being pushy when it was really needed. In addition, thank you Carlos and Puzo for helping me to have a smooth start of my PhD and for filling the gap when Alex was too busy. Last two years of my PhD I have been working with Alex remotely, and I would like to thank the local crew who helped me: professor Eduard Ayguade for providing me with some very hard-to-get manuscripts and accepting to be my "ponente" at the University; professor Jesus Labarta for thorough dis- cussions about parallel performance issues and know-how lessons on demand; Alex Rico for helping me deliver work for the Mont-Blanc project and for friendly advices every so little; Filippo Mantovani for making sure I could use the prototypes without outages and for filtering-out internal bureaucracy issues. -

Cubietruck – Mini PC
SPRZĘT Cubietruck – mini PC Rynek komputerków jednopłytkowych opartych o procesory ARM zapoczątkowany przez Raspberry Pi rozwija się doskonale. Może nie jak grzyby po deszczu, ale systematycznie pojawiają się nowe rozwiązania: BeagleBoard, Marsboard, Cubieboard, Olinuxino itp. Różnią się one wyposażeniem, wydajnością, dostępnością dokumentacji oraz wsparciem technicznym. Ciekawie rozwija się propozycja Cubieboard. mocujących. Niby nic, ale te trzy kawałki two- org, zapoczątkowana płytką Cubieboard A10 rzywa i paczka tulejek umożliwiają poskładanie Fotografi a 3. Obudowa Cubietruck (opisaną w EP06/2013) i Cubieboard2 zgod- samodzielnego systemu mini-PC wyposażo- ną mechanicznie, ale zbudowaną w oparciu nego w dysk HDD 2,5”, wystarczająco zabez- rolę domowego centrum multimedialnego lub o nowszy, dwurdzeniowy procesor A20, zwięk- pieczając mechanicznie jego elementy. Osłony Linuxowego komputera PC. Jedyne zastrzeżenie szający wydajność Cubie i paletę jej zastosowań w odpowiednich miejscach mają wyfrezowane można mieć do kilku różnokolorowych LED, (fotografi a 1). Najnowsza propozycja to Cubie- otwory umożliwiające korzystanie z GPIO bez bezlitośnie informujących nasze oczy o stanie truck (Cubieboard3), oparty podobnie jak Cu- zdejmowania obudowy. pracy Cubie. bieboard2 (fotografi a 2) o procesor Allwinner Ciekawą propozycją dla osób wykorzy- Cubieboard3 oparty jest o SoC w architektu- A20, lecz mający znacznie bogatsze wyposaże- stujących Cubieboard3 w roli samodzielnego rze ARM7 – Allwinner A20, który w połączeniu nie, co niestety wiąże się z wyższą ceną. Porów- mini-PC, jest pełna obudowa pokazana na fo- ze sporej wielkości dyskiem NAND Flash oraz nanie parametrów poszczególnych komputer- tografi i 3. W swoim wnętrzu mieści swobodnie zwiększoną pamięcią RAM bezproblemowo ków Cubieboard umieszczono w tabeli 1. płytkę Cubieboard3, dysk HDD 2,5” (fotogra- sprawdza się w roli komputera PC pracującego Podobnie jak w przypadku poprzednich fi a 4) i przewody połączeniowe. -

Monitoring Dan Kontrol Sistem Irigasi Berbasis Iot Menggunakan Banana Pi
JURNAL TEKNIK ITS Vol. 7, No. 2, (2018) ISSN: 2337-3539 (2301-9271 Print) A288 Monitoring dan Kontrol Sistem Irigasi Berbasis IoT Menggunakan Banana Pi Andrie Wijaya, dan Muhammad Rivai Departemen Teknik Elektro, Fakultas Teknologi Elektro, Institut Teknologi Sepuluh Nopember (ITS) e-mail: [email protected] Abstrak— Saat ini metode pengaliran air atau irigasi dilakukan memperhatikan kondisi kelembaban tanah juga mengakibatkan secara manual. Petani harus menyiram tanaman satu persatu penggunaan air yang tidak tepat. Penggunaan air yang sehingga tidak efisien dalam hal energi, waktu, dan ketersediaan berlebihan akan mempengaruhi ketersediaan sumber air yang air sehingga dapat menurukan hasil panen. Internet of Things semakin menurun. merupakan konsep dan metode untuk kontrol jarak jauh, Tugas akhir ini bertujuan untuk menciptakan sistem monitoring, pengiriman data, dan berbagai tugas lainnya. IoT terhubung dengan suatu jaringan sehingga dapat di akses di irigasi berbasis internet of things [2][3], dan [4]. Pada sistem mana saja yang dapat mempermudah berbagai hal. IoT dapat ini petani dapat memonitoring kondisi kelembaban tanah dan dimanfaatkan di berbagai bidang, salah satunya adalah bidang mengkontrol debit air yang akan disiram pada tanaman pertanian. Pada bidang ini IoT dapat digunakan untuk memantau Sehingga meningkatkan hasil panen dan mengoptimalkan dan mengatur berbagai hal untuk menunjang pertanian. Pada penggunaan air. penelitian ini akan dibuat suatu peralatan yang digunakan untuk Sistem ini menggunakan sensor kelembaban tanah atau monitoring dan kontrol sistem irigasi berbasis IOT. Single Board higrometer [5][6]yang akan di proses di Single Board Computer Banana Pi digunakan sebagai prosesor utama yang Computer (SBC) Banana Pi [7]. SBC yang terhubung dengan terhubung dengan jaringan internet yang mengirim data dari sensor ke pengguna. -

A 1024-Core 70GFLOPS/W Floating Point Manycore Microprocessor
A 1024-core 70GFLOPS/W Floating Point Manycore Microprocessor Andreas Olofsson, Roman Trogan, Oleg Raikhman Adapteva, Lexington, MA The Past, Present, & Future of Computing SIMD MIMD PE PE PE PE MINI MINI MINI CPU CPU CPU PE PE PE PE MINI MINI MINI CPU CPU CPU PE PE PE PE MINI MINI MINI CPU CPU CPU MINI MINI MINI BIG BIG CPU CPU CPU CPU CPU BIG BIG BIG BIG CPU CPU CPU CPU PAST PRESENT FUTURE 2 Adapteva’s Manycore Architecture C/C++ Programmable Incredibly Scalable 70 GFLOPS/W 3 Routing Architecture 4 E64G400 Specifications (Jan-2012) • 64-Core Microprocessor • 100 GFLOPS performance • 800 MHz Operation • 8GB/sec IO bandwidth • 1.6 TB/sec on chip memory BW • 0.8 TB/sec network on chip BW • 64 Billion Messages/sec IO Pads Core • 2 Watt total chip power • 2MB on chip memory Link Logic • 10 mm2 total silicon area • 324 ball 15x15mm plastic BGA 5 Lab Measurements 80 Energy Efficiency 70 60 50 GFLOPS/W 40 30 20 10 0 0 200 400 600 800 1000 1200 MHz ENERGY EFFICIENCY ENERGY EFFICIENCY (28nm) 6 Epiphany Performance Scaling 16,384 G 4,096 F 1,024 L 256 O 64 4096 P 1024 S 16 256 64 4 16 1 # Cores On‐demand scaling from 0.25W to 64 Watt 7 Hold on...the title said 1024 cores! • We can build it any time! • Waiting for customer • LEGO approach to design • No global timinga paths • Guaranteed by design • Generate any array in 1 day • ~130 mm2 silicon area 1024 Cores 1Core 8 What about 64-bit Floating Point? Single Precision Double Precision 2 FLOPS/CYCLE 2 FLOPS/CYCLE 64KB SRAM 64KB SRAM 0.215mm^2 0.237mm^2 700MHz 600MHz 9 Epiphany Latency Specifications -
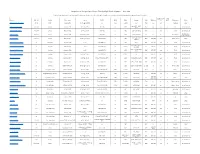
Comparison of 116 Open Spec, Hacker Friendly Single Board Computers -- June 2018
Comparison of 116 Open Spec, Hacker Friendly Single Board Computers -- June 2018 Click on the product names to get more product information. In most cases these links go to LinuxGizmos.com articles with detailed product descriptions plus market analysis. HDMI or DP- USB Product Price ($) Vendor Processor Cores 3D GPU MCU RAM Storage LAN Wireless out ports Expansion OSes 86Duino Zero / Zero Plus 39, 54 DMP Vortex86EX 1x x86 @ 300MHz no no2 128MB no3 Fast no4 no5 1 headers Linux Opt. 4GB eMMC; A20-OLinuXino-Lime2 53 or 65 Olimex Allwinner A20 2x A7 @ 1GHz Mali-400 no 1GB Fast no yes 3 other Linux, Android SATA A20-OLinuXino-Micro 65 or 77 Olimex Allwinner A20 2x A7 @ 1GHz Mali-400 no 1GB opt. 4GB NAND Fast no yes 3 other Linux, Android Debian Linux A33-OLinuXino 42 or 52 Olimex Allwinner A33 4x A7 @ 1.2GHz Mali-400 no 1GB opt. 4GB NAND no no no 1 dual 40-pin 3.4.39, Android 4.4 4GB (opt. 16GB A64-OLinuXino 47 to 88 Olimex Allwinner A64 4x A53 @ 1.2GHz Mali-400 MP2 no 1GB GbE WiFi, BT yes 1 40-pin custom Linux eMMC) Banana Pi BPI-M2 Berry 36 SinoVoip Allwinner V40 4x A7 Mali-400 MP2 no 1GB SATA GbE WiFi, BT yes 4 Pi 40 Linux, Android 8GB eMMC (opt. up Banana Pi BPI-M2 Magic 21 SinoVoip Allwinner A33 4x A7 Mali-400 MP2 no 512MB no Wifi, BT no 2 Pi 40 Linux, Android to 64GB) 8GB to 64GB eMMC; Banana Pi BPI-M2 Ultra 56 SinoVoip Allwinner R40 4x A7 Mali-400 MP2 no 2GB GbE WiFi, BT yes 4 Pi 40 Linux, Android SATA Banana Pi BPI-M2 Zero 21 SinoVoip Allwinner H2+ 4x A7 @ 1.2GHz Mali-400 MP2 no 512MB no no WiFi, BT yes 1 Pi 40 Linux, Android Banana -

LAB-Manual Iot for Intel Edison
Evaluation of Intel Architecture An Experimental Manual for Computer Architecture, Advanced Microprocessor, System On Chip (SoC) and Compiler Design In association with Intel Collaboration Program Designed by: Zeenat Shareef, MTech (Mobile and Pervasive Computing) Under the guidance of: Dr. S.R.N Reddy, HOD and Associate Professor, CSE Mr. Naveen , Mr. Sumit Verma, Intel Department of Computer Science Indira Gandhi Delhi Technical University for Women Kashmere Gate, Delhi-110006 LIST OF EXPERIMENTS EXP. No Description of Experiment 1. To familiarize with Intel Edison. 2. Write the steps to install the drivers and IDE for Intel Edison 3. Write the steps to configure Intel Edison and enable the WIFI module 4. To enable the Bluetooth module in Intel Edison and connect with a device. 5. Write the steps to blink the LED on the Intel Edison using Eclipse CDT remote explorer(WiFi). EXPERIMENT 1 AIM: To familiarize with Intel Edison. INTEL EDISON- A SOC based on Intel Atom The Intel Edison compute module is designed to lower the barriers to entry for anyone prototyping and producing IoT and wearable computing products. Intel Edison contains the core system processing and connectivity elements: processor, PMIC, RAM, eMMC, and Wi- Fi/BT. Intel Edison is a module that interfaces with end-user systems via a 70-pin connector. The Intel Edison compute module does not include any video input or output interfaces (MIPI CSI, MIPI DSI, HDMI, etc.). Internal image processing and graphics processing cores are disabled (ISP, PowerVR, VED, VEC, VSP, etc.). Intel Edison relies on the end-user support of input power. -

Intel Edison Workshop
Note: This presentation was made and provided by Intel during the Intel Embedded Education & Research Summit in March 2015 Intel Edison Workshop Setting up Edison Step by Step Our Workshop Goal: 1.Unbox Edison 2.Learn how to connect and configure Edison board: Serial connecton Name /WiFi set up/Password 3. Install drivers (New Windows Installer amd manual install) 4. Intel Development IoT Kit 5. Install IDEs 6. Run example code Intel® Edison Arduino Expansion Board Assembly https://software.intel.com/en‐us/articles/intel‐edison‐arduino‐expansion‐board‐assembly Microswitch and USB Ports Details The slider switches between USB host mode and USB device mode. Device mode: The switch is toggled down and a micro‐USB cable can be used to turn the Intel® Edison into a computer peripheral. Device mode allows you to do such things as: program the board over USB, or mount the onboard flash memory like a disk drive. Host mode: The switch is toggled up and USB peripherals with a standard‐sized USB cable (such as mice, keyboards, etc) can be plugged into the Intel® Edison. USB host mode requires the use of an external power adapter. The Intel Edison board has three USB ports: The middle port (Micro A type) is used for the following: •Power through USB •Ethernet over USB •Uploading Arduino sketches •Updating the firmware by using the board as a storage device, like a flash drive The edge port (Micro A type) is used to create a terminal connection by serial over USB only. Power Through DC Plug If you are going to use more power intensive features such as Wi‐Fi, a servo motor, or an Arduino shield, use a DC power supply in addition to the device mode micro‐USB cable. -

Development Boards This Product Is Rohs Compliant
Development Boards This product is RoHS compliant. PANDABOARD DEVELOPMENT PLATFORM Features: • Core Logic: OMAP4460 applications Processor • Interface: (1) General Purpose Expansion Header • Wireless Connectivity: 802.11 b/g/n (WiLink™ 6.0) • Memory: 1GB DDR2 RAM (I2C, GPMC, USB, MMC, DSS, ETM) • Debug options: JTAG, UART/RS-232, 1 GPIO button NTL • Full Size SD/MMC card port • Camera Expansion Header • Graphics APIs: OpenGL ES v2.0, OpenGL ES v1.1, • 10/100 Ethernet • Display Connectors: HDMI v1.3, DVI-D. LCD Expansion OpenVGv1.1, and EGL v1.3 • USB: (1) USB 2.0 OTG port, (2) USB 2.0 High-speed port • Audio Connectors: 3.5" In/Out, HDMI audio out For quantities greater than listed, call for quote. MOUSER Pandaboard Price Description STOCK NO. Part No. Each 595-PANDABOARD UEVM4430G-01-00-00 Pandaboard ARM Cortex-A9 MPCore 1GHz OMAP4430 SoC Platform 179.00 595-PANDABOARD-ES UEVM4460G-02-01-00 Pandaboard ARM Cortex-A9 MPCore 1GHz OMAP4460 SoC Platform 185.00 Embedded Modules Embedded BEAGLEBOARD SOC PLATFORMS BeagleBoard.org develops low-cost, fan-less single-board computers based on low-power Texas Instruments processors featuring the ARM Cortex-A8 core with all of the expandability of today's desktop machines, but without the bulk, expense, or noise. BeagleBoard.org provides an open source development platform for A B the creation of high-performance embedded designs. Beagleboard C4 Features: Beagleboard xM Features: Beaglebone Features: • Over 1,200 Dhrystone MIPS using the superscalar • Over 2,000 Dhrystone MIPS using the Super-scalar -

Improving the Beaglebone Board with Embedded Ubuntu, Enhanced GPMC Driver and Python for Communication and Graphical Prototypes
Final Master Thesis Improving the BeagleBone board with embedded Ubuntu, enhanced GPMC driver and Python for communication and graphical prototypes By RUBÉN GONZÁLEZ MUÑOZ Directed by MANUEL M. DOMINGUEZ PUMAR FINAL MASTER THESIS 30 ECTS, JULY 2015, ELECTRICAL AND ELECTRONICS ENGINEERING Abstract Abstract BeagleBone is a low price, small size Linux embedded microcomputer with a full set of I/O pins and processing power for real-time applications, also expandable with cape pluggable boards. The current work has been focused on improving the performance of this board. In this case, the BeagleBone comes with a pre-installed Angstrom OS and with a cape board using a particular software “overlay” and applications. Due to a lack of support, this pre-installed OS has been replaced by Ubuntu. As a consequence, the cape software and applications need to be adapted. Another necessity that emerges from the stated changes is to improve the communications through a GPMC interface. The depicted driver has been built for the new system as well as synchronous variants, also developed and tested. Finally, a set of applications in Python using the cape functionalities has been developed. Some extra graphical features have been included as example. Contents Contents Abstract ..................................................................................................................................................................................... 5 List of figures ......................................................................................................................................................................... -

User Manual - S.USV Solutions Compatible with Raspberry Pi, up Board and Tinker Board Revision 2.2 | Date 07.06.2018
User Manual - S.USV solutions Compatible with Raspberry Pi, UP Board and Tinker Board Revision 2.2 | Date 07.06.2018 User Manual - S.USV solutions / Revision 2.0 Table of Contents 1 Functions .............................................................................................................................................. 3 2 Technical Specification ........................................................................................................................ 4 2.1 Overview ....................................................................................................................................... 5 2.2 Performance .................................................................................................................................. 6 2.3 Lighting Indicators ......................................................................................................................... 6 3 Installation Guide................................................................................................................................. 7 3.1 Hardware ...................................................................................................................................... 7 3.1.1 Commissioning S.USV ............................................................................................................ 7 3.1.2 Connecting the battery .......................................................................................................... 8 3.1.3 Connecting the external power supply ................................................................................. -

Gerard Manley Hopkins and Old English Poetry: a Stylistic Analysis
Gerard Manley Hopkins and Old English poetry: a stylistic analysis Item Type text; Dissertation-Reproduction (electronic) Authors Li, Leshi Publisher The University of Arizona. Rights Copyright © is held by the author. Digital access to this material is made possible by the University Libraries, University of Arizona. Further transmission, reproduction or presentation (such as public display or performance) of protected items is prohibited except with permission of the author. Download date 23/09/2021 14:04:44 Link to Item http://hdl.handle.net/10150/565498 GERARD MANLEY HOPKINS AND OLD ENGLISH POETRY: A STYLISTIC ANALYSIS by Rebecca Lee A Dissertation Submitted to the Faculty of the DEPARTMENT OF ENGLISH In Partial Fulfillment of the Requirements For the Degree of DOCTOR OF PHILOSOPHY WITH A MAJOR IN ENGLISH LITERATURE . In the Graduate College THE UNIVERSITY OF ARIZONA 19 8 1 THE UNIVERSITY OF ARIZONA GRADUATE COLLEGE As members of the Final Examination Committee, we certify that we have read the dissertation prepared by Rebecca Lee_________________________________ entitled GERARD MANLEY HOPKINS AND OLD ENGLISH POETRY:___________________ A STYLISTIC ANALYSIS and recommend that it be accepted as fulfilling the dissertation requirement for the Degree of Doctor of Philosophy Date Date Final approval and acceptance of this dissertation is contingent upon the candidate's submission of the final copy of the dissertation to the Graduate College. I hereby certify that I have read this dissertation prepared under my direction and recommend that it be accepted as fulfilling the dissertation requirement. * / ■ ? ■ / Dissertation Director Date / STATEMENT BY AUTHOR This dissertation has been submitted in partial fulfillment of requirements for an advanced degree at The University of Arizona and is deposited in the University Library to be made available to borrowers under rules of the Library» Brief quotations from this dissertation are allowable without special permission5 provided that accurate acknowledgment of source is made. -

A Highly Modular Router Microarchitecture for Networks-On-Chip
A Highly Modular Router Microarchitecture for Networks-on-Chip Item Type text; Electronic Dissertation Authors Wu, Wo-Tak Publisher The University of Arizona. Rights Copyright © is held by the author. Digital access to this material is made possible by the University Libraries, University of Arizona. Further transmission, reproduction, presentation (such as public display or performance) of protected items is prohibited except with permission of the author. Download date 01/10/2021 08:12:16 Link to Item http://hdl.handle.net/10150/631277 A HIGHLY MODULAR ROUTER MICROARCHITECTURE FOR NETWORKS-ON-CHIP by Wo-Tak Wu Copyright c Wo-Tak Wu 2019 A Dissertation Submitted to the Faculty of the DEPARTMENT OF ELECTRICAL AND COMPUTER ENGINEERING In Partial Fulfillment of the Requirements For the Degree of DOCTOR OF PHILOSOPHY In the Graduate College THE UNIVERSITY OF ARIZONA 2019 THE UNIVERSITY OF ARIZONA GRADUATE COLLEGE As members of the Dissertation Committee, we certify that we have read the dissertation prepared by Wo-Tak Wu, titled A HIGHLY MODULAR ROUTER MICROARCHITECTURE FOR NETWORKS-ON-CHIP and recommend that it be accepted as fulfilling the dissertation requirement for the Degree of Doctor of Philosophy. Dr. Linda Powers --~-__:::::____ ---?---- _________ Date: August 7, 2018 Dr. Roman Lysecky Final approval and acceptance of this dissertation is contingent upon the candidate's submission of the final copies of the dissertation to the Graduate College. I hereby certify that I have read this dissertation prepared under my direction and recommend that it be accepted as fulfilling the dissertation requirement. _____(/2 __·...... ~"--------\;-~=--------- · __ Date: August 7, 2018 Dissertation Director: Dr.