Music Cryptography Based on Carnatic Music
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Towards Automatic Audio Segmentation of Indian Carnatic Music
Friedrich-Alexander-Universit¨at Erlangen-Nurnberg¨ Master Thesis Towards Automatic Audio Segmentation of Indian Carnatic Music submitted by Venkatesh Kulkarni submitted July 29, 2014 Supervisor / Advisor Dr. Balaji Thoshkahna Prof. Dr. Meinard Muller¨ Reviewers Prof. Dr. Meinard Muller¨ International Audio Laboratories Erlangen A Joint Institution of the Friedrich-Alexander-Universit¨at Erlangen-N¨urnberg (FAU) and Fraunhofer Institute for Integrated Circuits IIS ERKLARUNG¨ Erkl¨arung Hiermit versichere ich an Eides statt, dass ich die vorliegende Arbeit selbstst¨andig und ohne Benutzung anderer als der angegebenen Hilfsmittel angefertigt habe. Die aus anderen Quellen oder indirekt ubernommenen¨ Daten und Konzepte sind unter Angabe der Quelle gekennzeichnet. Die Arbeit wurde bisher weder im In- noch im Ausland in gleicher oder ¨ahnlicher Form in einem Verfahren zur Erlangung eines akademischen Grades vorgelegt. Erlangen, July 29, 2014 Venkatesh Kulkarni i Master Thesis, Venkatesh Kulkarni ACKNOWLEDGEMENTS Acknowledgements I would like to express my gratitude to my supervisor, Dr. Balaji Thoshkahna, whose expertise, understanding and patience added considerably to my learning experience. I appreciate his vast knowledge and skill in many areas (e.g., signal processing, Carnatic music, ethics and interaction with participants).He provided me with direction, technical support and became more of a friend, than a supervisor. A very special thanks goes out to my Prof. Dr. Meinard M¨uller,without whose motivation and encouragement, I would not have considered a graduate career in music signal analysis research. Prof. Dr. Meinard M¨ulleris the one professor/teacher who truly made a difference in my life. He was always there to give his valuable and inspiring ideas during my thesis which motivated me to think like a researcher. -

Syllabus for Post Graduate Programme in Music
1 Appendix to U.O.No.Acad/C1/13058/2020, dated 10.12.2020 KANNUR UNIVERSITY SYLLABUS FOR POST GRADUATE PROGRAMME IN MUSIC UNDER CHOICE BASED CREDIT SEMESTER SYSTEM FROM 2020 ADMISSION NAME OF THE DEPARTMENT: DEPARTMENT OF MUSIC NAME OF THE PROGRAMME: MA MUSIC DEPARTMENT OF MUSIC KANNUR UNIVERSITY SWAMI ANANDA THEERTHA CAMPUS EDAT PO, PAYYANUR PIN: 670327 2 SYLLABUS FOR POST GRADUATE PROGRAMME IN MUSIC UNDER CHOICE BASED CREDIT SEMESTER SYSTEM FROM 2020 ADMISSION NAME OF THE DEPARTMENT: DEPARTMENT OF MUSIC NAME OF THE PROGRAMME: M A (MUSIC) ABOUT THE DEPARTMENT. The Department of Music, Kannur University was established in 2002. Department offers MA Music programme and PhD. So far 17 batches of students have passed out from this Department. This Department is the only institution offering PG programme in Music in Malabar area of Kerala. The Department is functioning at Swami Ananda Theertha Campus, Kannur University, Edat, Payyanur. The Department has a well-equipped library with more than 1800 books and subscription to over 10 Journals on Music. We have gooddigital collection of recordings of well-known musicians. The Department also possesses variety of musical instruments such as Tambura, Veena, Violin, Mridangam, Key board, Harmonium etc. The Department is active in the research of various facets of music. So far 7 scholars have been awarded Ph D and two Ph D thesis are under evaluation. Department of Music conducts Seminars, Lecture programmes and Music concerts. Department of Music has conducted seminars and workshops in collaboration with Indira Gandhi National Centre for the Arts-New Delhi, All India Radio, Zonal Cultural Centre under the Ministry of Culture, Government of India, and Folklore Academy, Kannur. -

Fusion Without Confusion Raga Basics Indian
Fusion Without Confusion Raga Basics Indian Rhythm Basics Solkattu, also known as konnakol is the art of performing percussion syllables vocally. It comes from the Carnatic music tradition of South India and is mostly used in conjunction with instrumental music and dance instruction, although it has been widely adopted throughout the world as a modern composition and performance tool. Similarly, the music of North India has its own system of rhythm vocalization that is based on Bols, which are the vocalization of specific sounds that correspond to specific sounds that are made on the drums of North India, most notably the Tabla drums. Like in the south, the bols are used in musical training, as well as composition and performance. In addition, solkattu sounds are often referred to as bols, and the practice of reciting bols in the north is sometimes referred to as solkattu, so the distinction between the two practices is blurred a bit. The exercises and compositions we will discuss contain bols that are found in both North and South India, however they come from the tradition of the North Indian tabla drums. Furthermore, the theoretical aspect of the compositions is distinctly from the Hindustani, (north Indian) tradition. Hence, for the purpose of this presentation, the use of the term Solkattu refers to the broader, more general practice of Indian rhythmic language. South Indian Percussion Mridangam Dolak Kanjira Gattam North Indian Percussion Tabla Baya (a.k.a. Tabla) Pakhawaj Indian Rhythm Terms Tal (also tala, taal, or taala) – The Indian system of rhythm. Tal literally means "clap". -
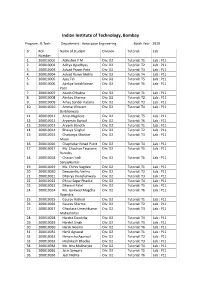
Rolllist Btech DD Bs2020batch
Indian Institute of Technology, Bombay Program : B.Tech. Department : Aerospace Engineering Batch Year : 2020 Sr. Roll Name of Student Division Tutorial Lab Number 1. 200010001 Abhishek P M Div: D2 Tutorial: T1 Lab : P11 2. 200010002 Aditya Upadhyay Div: D2 Tutorial: T2 Lab : P11 3. 200010003 Advait Pravin Pote Div: D2 Tutorial: T3 Lab : P11 4. 200010004 Advait Ranvir Mehla Div: D2 Tutorial: T4 Lab : P11 5. 200010005 Ajay Tak Div: D2 Tutorial: T5 Lab : P11 6. 200010006 Ajinkya Satishkumar Div: D2 Tutorial: T6 Lab : P11 Patil 7. 200010007 Akash Chhabra Div: D2 Tutorial: T1 Lab : P11 8. 200010008 Akshay Sharma Div: D2 Tutorial: T2 Lab : P11 9. 200010009 Amay Sunder Kataria Div: D2 Tutorial: T3 Lab : P11 10. 200010010 Ammar Khozem Div: D2 Tutorial: T4 Lab : P11 Barbhaiwala 11. 200010011 Anup Nagdeve Div: D2 Tutorial: T5 Lab : P11 12. 200010012 Aryaman Bansal Div: D2 Tutorial: T6 Lab : P11 13. 200010013 Aryank Banoth Div: D2 Tutorial: T1 Lab : P11 14. 200010014 Bhavya Singhal Div: D2 Tutorial: T2 Lab : P11 15. 200010015 Chaitanya Shankar Div: D2 Tutorial: T3 Lab : P11 Moon 16. 200010016 Chaphekar Ninad Punit Div: D2 Tutorial: T4 Lab : P11 17. 200010017 Ms. Chauhan Tejaswini Div: D2 Tutorial: T5 Lab : P11 Ramdas 18. 200010018 Chavan Yash Div: D2 Tutorial: T6 Lab : P11 Sanjaykumar 19. 200010019 Ms. Chinni Vagdevi Div: D2 Tutorial: T1 Lab : P11 20. 200010020 Deepanshu Verma Div: D2 Tutorial: T2 Lab : P11 21. 200010021 Dhairya Jhunjhunwala Div: D2 Tutorial: T3 Lab : P11 22. 200010022 Dhruv Sagar Phadke Div: D2 Tutorial: T4 Lab : P11 23. 200010023 Dhwanil Patel Div: D2 Tutorial: T5 Lab : P11 24. -

M.A-Music-Vocal-Syllabus.Pdf
BANGALORE UNIVERSITY NAAC ACCREDITED WITH ‘A’ GRADE P.G. DEPARTMENT OF PERFORMING ARTS JNANABHARATHI, BANGALORE-560056 MUSIC SYLLABUS – M.A KARNATAKA MUSIC VOCAL AND INSTRUMENTAL (VEENA, VIOLIN AND FLUTE) CBCS SYSTEM- 2014 Dr. B.M. Jayashree. Professor of Music Chairperson, BOS (PG) M.A. KARNATAKA MUSIC VOCAL AND INSTRUMENTAL (VEENA, VIOLIN AND FLUTE) Semester scheme syllabus CBCS Scheme of Examination, continuous Evaluation and other Requirements: 1. ELIGIBILITY: A Degree with music vocal/instrumental as one of the optional subject with at least 50% in the concerned optional subject an merit internal among these applicant Of A Graduate with minimum of 50% marks secured in the senior grade examination in music (vocal/instrumental) conducted by secondary education board of Karnataka OR a graduate with a minimum of 50% marks secured in PG Diploma or 2 years diploma or 4 year certificate course in vocal/instrumental music conducted either by any recognized Universities of any state out side Karnataka or central institution/Universities Any degree with: a) Any certificate course in music b) All India Radio/Doordarshan gradation c) Any diploma in music or five years of learning certificate by any veteran musician d) Entrance test (practical) is compulsory for admission. 2. M.A. MUSIC course consists of four semesters. 3. First semester will have three theory paper (core), three practical papers (core) and one practical paper (soft core). 4. Second semester will have three theory papers (core), two practical papers (core), one is project work/Dissertation practical paper and one is practical paper (soft core) 5. Third semester will have two theory papers (core), three practical papers (core) and one is open Elective Practical paper 6. -

CARNATIC MUSIC (CODE – 032) CLASS – X (Melodic Instrument) 2020 – 21 Marking Scheme
CARNATIC MUSIC (CODE – 032) CLASS – X (Melodic Instrument) 2020 – 21 Marking Scheme Time - 2 hrs. Max. Marks : 30 Part A Multiple Choice Questions: Attempts any of 15 Question all are of Equal Marks : 1. Raga Abhogi is Janya of a) Karaharapriya 2. 72 Melakarta Scheme has c) 12 Chakras 3. Identify AbhyasaGhanam form the following d) Gitam 4. Idenfity the VarjyaSwaras in Raga SuddoSaveri b) GhanDharam – NishanDham 5. Raga Harikambhoji is a d) Sampoorna Raga 6. Identify popular vidilist from the following b) M. S. Gopala Krishnan 7. Find out the string instrument which has frets d) Veena 8. Raga Mohanam is an d) Audava – Audava Raga 9. Alankaras are set to d) 7 Talas 10 Mela Number of Raga Maya MalawaGoula d) 15 11. Identify the famous flutist d) T R. Mahalingam 12. RupakaTala has AksharaKals b) 6 13. Indentify composer of Navagrehakritis c) MuthuswaniDikshitan 14. Essential angas of kriti are a) Pallavi-Anuppallavi- Charanam b) Pallavi –multifplecharanma c) Pallavi – MukkyiSwaram d) Pallavi – Charanam 15. Raga SuddaDeven is Janya of a) Sankarabharanam 16. Composer of Famous GhanePanchartnaKritis – identify a) Thyagaraja 17. Find out most important accompanying instrument for a vocal concert b) Mridangam 18. A musical form set to different ragas c) Ragamalika 19. Identify dance from of music b) Tillana 20. Raga Sri Ranjani is Janya of a) Karahara Priya 21. Find out the popular Vena artist d) S. Bala Chander Part B Answer any five questions. All questions carry equal marks 5X3 = 15 1. Gitam : Gitam are the simplest musical form. The term “Gita” means song it is melodic extension of raga in which it is composed. -
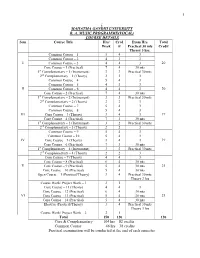
1 ; Mahatma Gandhi University B. A. Music Programme(Vocal
1 ; MAHATMA GANDHI UNIVERSITY B. A. MUSIC PROGRAMME(VOCAL) COURSE DETAILS Sem Course Title Hrs/ Cred Exam Hrs. Total Week it Practical 30 mts Credit Theory 3 hrs. Common Course – 1 5 4 3 Common Course – 2 4 3 3 I Common Course – 3 4 4 3 20 Core Course – 1 (Practical) 7 4 30 mts 1st Complementary – 1 (Instrument) 3 3 Practical 30 mts 2nd Complementary – 1 (Theory) 2 2 3 Common Course – 4 5 4 3 Common Course – 5 4 3 3 II Common Course – 6 4 4 3 20 Core Course – 2 (Practical) 7 4 30 mts 1st Complementary – 2 (Instrument) 3 3 Practical 30 mts 2nd Complementary – 2 (Theory) 2 2 3 Common Course – 7 5 4 3 Common Course – 8 5 4 3 III Core Course – 3 (Theory) 3 4 3 19 Core Course – 4 (Practical) 7 3 30 mts 1st Complementary – 3 (Instrument) 3 2 Practical 30 mts 2nd Complementary – 3 (Theory) 2 2 3 Common Course – 9 5 4 3 Common Course – 10 5 4 3 IV Core Course – 5 (Theory) 3 4 3 19 Core Course – 6 (Practical) 7 3 30 mts 1st Complementary – 4 (Instrument) 3 2 Practical 30 mts 2nd Complementary – 4 (Theory) 2 2 3 Core Course – 7 (Theory) 4 4 3 Core Course – 8 (Practical) 6 4 30 mts V Core Course – 9 (Practical) 5 4 30 mts 21 Core Course – 10 (Practical) 5 4 30 mts Open Course – 1 (Practical/Theory) 3 4 Practical 30 mts Theory 3 hrs Course Work/ Project Work – 1 2 1 Core Course – 11 (Theory) 4 4 3 Core Course – 12 (Practical) 6 4 30 mts VI Core Course – 13 (Practical) 5 4 30 mts 21 Core Course – 14 (Practical) 5 4 30 mts Elective (Practical/Theory) 3 4 Practical 30 mts Theory 3 hrs Course Work/ Project Work – 2 2 1 Total 150 120 120 Core & Complementary 104 hrs 82 credits Common Course 46 hrs 38 credits Practical examination will be conducted at the end of each semester 2 MAHATMA GANDHI UNIVERSITY B. -

Carnatic Music (Melodic Instrumental) (Code No
(B) CARNATIC MUSIC (MELODIC INSTRUMENTAL) (CODE NO. 032) CLASS–XI: (THEORY)(2019-20) One theory paper Total Marks: 100 2 Hours Marks : 30 Theory: A. History and Theory of Indian Music 1. (a) An outline knowledge of the following Lakshana Grandhas Silappadikaram, Natyasastra, Sangita Ratnakara and Chaturdandi Prakasika. (b) Short life sketch and contributions of the following:- Veena Dhanammal, flute Saraba Sastry, Rajamanikkam Pillai, Tirukkodi Kaval Krishna lyer (violin) Rajaratnam Pillai (Nagasvaram), Thyagaraja, Syamasastry, Muthuswamy Deekshitar, Veena Seshanna. (c) Brief study of the musical forms: Geetam and its varieties; Varnam – Padavarnam – Daruvarna Svarajati, Kriti/Kirtana and Padam 2. Definition and explanation of the following terms: Nada, Sruti, Svara, Vadi, Vivadi:, Samvadi, Anuvadi, Amsa & Nyasa, Jaati, Raga, Tala, Jati, Yati, Suladisapta talas, Nadai, Arohana, Avarohana. 3. Candidates should be able to write in notation the Varnam in the prescribed ragas. 4. Lakshanas of the ragas prescribed. 5. Talas Prescribed: Adi, Roopaka, Misra Chapu and Khanda Chapu. A brief study of Suladi Saptatalas. 6. A brief introduction to Manodhama Sangitam CLASS–XI (PRACTICAL) One Practical Paper Marks: 70 B. Practical Activities 1. Ragas Prescribed: Mayamalavagowla, Sankarabharana, Kharaharapriya, Kalyani, Kambhoji, Madhyamavati, Arabhi, Pantuvarali Kedaragaula, Vasanta, Anandabharavi, Kanada, Dhanyasi. 2. Varnams (atleast three) in Aditala in two degree of speed. 3. Kriti/Kirtana in each of the prescribed ragas, covering the main Talas Adi, Rupakam and Chapu. 4. Brief alapana of the ragas prescribed. 5. Technique of playing niraval and kalpana svaras in Adi, and Rupaka talas in two degrees of speed. 6. The candidate should be able to produce all the gamakas pertaining to the chosen instrument. -

Tillana Raaga: Bageshri; Taala: Aadi; Composer
Tillana Raaga: Bageshri; Taala: Aadi; Composer: Lalgudi G. Jayaraman Aarohana: Sa Ga2 Ma1 Dha2 Ni2 Sa Avarohana: Sa Ni2 Dha2 Ma1 Pa Dha2 Ga2 Ma1 Ga2 Ri2 Sa SaNiDhaMa .MaPaDha | Ga. .Ma | RiRiSa . || DhaNiSaGa .SaGaMa | Dha. MaDha| NiRi Sa . || DhaNiSaMa .GaRiSa |Ri. NiDha | NiRi Sa . || SaRiNiDha .MaPaDha |Ga . Ma . | RiNiSa . || Sa ..Ni .Dha Ma . |Sa..Ma .Ga | RiNiSa . || Sa ..Ni .Dha Ma~~ . |Sa..Ma .Ga | RiNiSa . || Pallavi tom dhru dhru dheem tadara | tadheem dheem ta na || dhim . dhira | na dhira na Dhridhru| (dhirana: DhaMaNi .. dhirana.: DhaMaGa .) tom dhru dhru dheem tadara | tadheem dheem ta na || dhim . dhira | na dhira na Dhridhru|| (dhirana: MaDha NiSa.. dhirana:DhaMa Ga..) tom dhru dhru dheem tadara | tadheem dheem ta na || (ta:DhaNi na:NiGaRi) dhim . dhira | na dhira na Dhridhru|| (dhirana:NiGaSaSaNi. Dhirana:DhaSaNiNiDha .) tom dhru dhru dheem tadara | tadheem dheem ta na || dhim . dhira | na dhira na Dhridhru|| (dhira:GaMaDhaNi na:GaGaRiSa dhira:NiDha na:Ga..) tom dhru dhru dheem tadana | tadheem dheem ta na || dhim.... Anupallavi SaMa .Ga MaNi . Dha| NiGa .Ri | NiDhaSa . || GaRi .Sa NiMa .Pa | Dha Ga..Ma | RiNi Sa . || naadhru daani tomdhru dhim | ^ta- ka-jha | Nuta dhim || … naadhru daani tomdhru dhim | (Naadru:MaGa, daani:DhaMa, tomdhru:NiDha, dhim: Sa) ^ta- ka-jha | Nuta dhim || (NiDha SaNi RiSa) taJha-Nu~ta dhim jhaNu | (tajha:SaSa Nu~ta: NiSaRiSa dhim:Ni; jha~Nu:MaDhaNi. tadhim . na | ta dhim ta || (tadhim:Dha Ga..;nata dhimta: MNiDha Sa.Sa) tanadheem .tatana dheemta tanadheem |(tanadheemta: DhaNi Ri ..Sa tanadheem: NiRiSa. .Sa tanadheem: NiDhaNi . ) .dheem dheemta | tom dhru dheem (dheem: Sa deemta:Ga.Ma tomdhrudeem:Ri..Ri Sa) .dheem dheem dheemta ton-| (dheem:Dha. -

Some Questions Concerning the Ugc Course in Astrology
SOME QUESTIONS CONCERNING THE UGC COURSE IN ASTROLOGY Kushal Siddhanta 18 AUGUST 2001. Dr. Murali Manohar cient Indian astronomer Varahamihira who Joshi, the present Union HRD Minister and in the sixth century AD spoke about the a former professor of physics in the Alla- earth's rotation.” Citing another fact in sup- habad University, was invited to the IIT, port of introducing astrology as a university Kharagpur, as the chief guest at an open- course, he said, 16 universities of the coun- ing function organized on the occasion of try had already been offering astrology as its fiftieth foundation anniversary. The a subject in various forms. So his govern- West Bengal Chief Minister Mr. Buddhadeb ment is doing nothing new. People should Bhattacharya was another guest. not oppose the astrology and other courses only on political reasons. There may be de- As expected, Mr. Bhattacharya in his bates and arguments over the issue. The speech indirectly criticized the policy of the Government, he assured all, was ready to Union Government to introduce worn out hear. So on and so forth. subjects like astrology, paurohitya, vas- tushastra, yoga and human consciousness, It all had started when the UGC issued a etc., in the universities through the Univer- circular on 23 February 2001 with a pro- sity Grant Commission (UGC). Dr. Joshi posal to all the universities of the country in his address, however, did not go into to introduce UG and PG courses as well the trouble of explaining why his depart- as doctoral researches in Vedic Astrology ment was so keen on funding these anti- which it later renamed in parenthesis as quated subjects in the universities in spite Jyotirvigyan (astronomy). -

Rāga Recognition Based on Pitch Distribution Methods
Rāga Recognition based on Pitch Distribution Methods Gopala K. Koduria, Sankalp Gulatia, Preeti Raob, Xavier Serraa aMusic Technology Group, Universitat Pompeu Fabra, Barcelona, Spain. bDepartment of Electrical Engg., Indian Institute of Technology Bombay, Mumbai, India. Abstract Rāga forms the melodic framework for most of the music of the Indian subcontinent. us automatic rāga recognition is a fundamental step in the computational modeling of the Indian art-music traditions. In this work, we investigate the properties of rāga and the natural processes by which people identify it. We bring together and discuss the previous computational approaches to rāga recognition correlating them with human techniques, in both Karṇāṭak (south Indian) and Hindustānī (north Indian) music traditions. e approaches which are based on first-order pitch distributions are further evaluated on a large com- prehensive dataset to understand their merits and limitations. We outline the possible short and mid-term future directions in this line of work. Keywords: Indian art music, Rāga recognition, Pitch-distribution analysis 1. Introduction ere are two prominent art-music traditions in the Indian subcontinent: Karṇāṭak in the Indian peninsular and Hindustānī in north India, Pakistan and Bangladesh. Both are orally transmied from one generation to another, and are heterophonic in nature (Viswanathan & Allen (2004)). Rāga and tāla are their fundamental melodic and rhythmic frameworks respectively. However, there are ample differ- ences between the two traditions in their conceptualization (See (Narmada (2001)) for a comparative study of rāgas). ere is an abundance of musicological resources that thoroughly discuss the melodic and rhythmic concepts (Viswanathan & Allen (2004); Clayton (2000); Sambamoorthy (1998); Bagchee (1998)). -
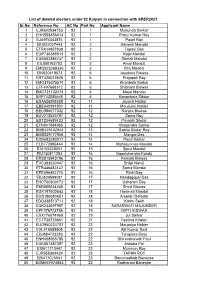
Sr.No Reference No AC No Part No Applicant Name 1 EJR602534753
List of deleted electors under 92 Kalyani in connection with SRER2021 Sr.No Reference No AC No Part No Applicant Name 1 EJR602534753 92 1 Mukunda Sarkar 2 EHH558456014 92 1 Pratul Kumar Roy 3 EJA974343874 92 1 Payel Roy 4 EIU002027443 92 2 Ganesh Mandal 5 ETR614857838 92 2 Tapasi Das 6 EGP736388513 92 2 Kajal Mandal 7 EUB502386747 92 2 Shefali Mandal 8 EIL050163793 92 2 Amal Mandal 9 EMQ923268336 92 2 Rita Mondal 10 EIN820419573 92 6 Joyatsna Biswas 11 ERT425012526 92 6 Prajapati Roy 12 EMO375375574 92 6 Kiranbala Sarkar 13 EFF497668312 92 6 Shibnath Biswas 14 EMC721102474 92 6 Maya Mondal 15 EYF742085668 92 6 Kananbala Sikdar 16 ESA626393528 92 11 Jayanti Haldar 17 EBE640991801 92 11 Mousumi Halder 18 EEU986577332 92 12 Ranjita Biswas 19 EUV212535787 92 12 Soma Roy 20 EST234689433 92 12 Priyashi Sikdar 21 EFN841884965 92 12 Khagendra Sarkar 22 EME449402944 92 13 Sabita Sikdar Roy 23 EMS829177866 92 14 Mangal Das 24 ECN693282011 92 14 Parul Sarkar 25 ELB772896444 92 14 Maharunnisa Mandal 26 EAI105328251 92 15 Sipra Mandal 27 EIU150811283 92 16 Gopalchandra Kundu 28 ERS815943196 92 16 Kamala Biswas 29 EVC383532447 92 16 Shilpi Nandi 30 ETR446483147 92 16 Soma Mondal 31 EPE596482775 92 16 Rinki Bag 32 EBJ839599081 92 17 Nandagopal Das 33 EHC700803173 92 17 Usharani Dey 34 EKB685034245 92 17 Shiuli Biswas 35 EGK197602643 92 18 Harimati Mondal 36 EGS186680651 92 18 Ameran Dafadar 37 EDQ338513711 92 18 Karim Sekh 38 EUK233697997 92 18 SARASWATI MAJUMDER 39 EPF076723786 92 19 DIPTI BISWAS 40 EXX176074968 92 19 Jui Sarkar 41 ECT730729861 92