GSI Local Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

10 Keyboard/Keypad Page (0X07) This Section Is the Usagepage for Key Codes to Be Used in Implementing a USB Keyboard
54 Universal Serial Bus HID Usage Tables 10 Keyboard/Keypad Page (0x07) This section is the UsagePage for key codes to be used in implementing a USB keyboard. A Boot Keyboard (84-, 101- or 104-key) should at a minimum support all associated usage codes as indicated in the “Boot” column below. The usage type of all key codes is Selectors (Sel), except for the modifier keys Keyboard Left Control (0x224) to Keyboard Right GUI (0x231) which are Dynamic Flags (DV). Note A general note on Usages and languages: Due to the variation of keyboards from language to language, it is not feasible to specify exact key mappings for every language. Where this list is not specific for a key function in a language, the closest equivalent key position should be used, so that a keyboard may be modified for a different language by simply printing different keycaps. One example is the Y key on a North American keyboard. In Germany this is typically Z. Rather than changing the keyboard firmware to put the Z Usage into that place in the descriptor list, the vendor should use the Y Usage on both the North American and German keyboards. This continues to be the existing practice in the industry, in order to minimize the number of changes to the electronics to accommodate other languages. Table 12: Keyboard/Keypad Page Ref: Typical AT-101 Usage ID Usage ID Usage Name Position PC- MacUNI Boot (Dec) (Hex) AT X 0 00 Reserved (no event indicated)9 N/A 4/101/104 1 01 Keyboard ErrorRollOver9 N/A 4/101/104 2 02 Keyboard POSTFail9 N/A 4/101/104 3 03 Keyboard ErrorUndefined9 -

IBM Power® Systems for SAS® Empowers Advanced Analytics Harry Seifert, Laurent Montaron, IBM Corporation
Paper 4695-2020 IBM Power® Systems for SAS® Empowers Advanced Analytics Harry Seifert, Laurent Montaron, IBM Corporation ABSTRACT For over 40+ years of partnership between IBM and SAS®, clients have been benefiting from the added value brought by IBM’s infrastructure platforms to deploy SAS analytics, and now SAS Viya’s evolution of modern analytics. IBM Power® Systems and IBM Storage empower SAS environments with infrastructure that does not make tradeoffs among performance, cost, and reliability. The unified solution stack, comprising server, storage, and services, reduces the compute time, controls costs, and maximizes resilience of SAS environment with ultra-high bandwidth and highest availability. INTRODUCTION We will explore how to deploy SAS on IBM Power Systems platforms and unleash the full potential of the infrastructure, to reduce deployment risk, maximize flexibility and accelerate insights. We will start by reviewing IBM and SAS’s technology relationship and the current state of SAS products on IBM Power Systems. Then we will look at some of the infrastructure options to deploy SAS 9.4 on IBM Power Systems and IBM Storage, while maximizing resiliency & throughput by leveraging best practices. Next, we will look at SAS Viya, which introduces changes to the underlying infrastructure requirements while remaining able to be deployed alongside a traditional SAS 9.4 operation. We’ll explore the various deployment modes available. Finally, we’ll look at tuning practices and reference materials available for a deeper dive in deploying SAS on IBM platforms. SAS: 40 YEARS OF PARTNERSHIP WITH IBM IBM and SAS have been partners since the founding of SAS. -

POWER® Processor-Based Systems
IBM® Power® Systems RAS Introduction to IBM® Power® Reliability, Availability, and Serviceability for POWER9® processor-based systems using IBM PowerVM™ With Updates covering the latest 4+ Socket Power10 processor-based systems IBM Systems Group Daniel Henderson, Irving Baysah Trademarks, Copyrights, Notices and Acknowledgements Trademarks IBM, the IBM logo, and ibm.com are trademarks or registered trademarks of International Business Machines Corporation in the United States, other countries, or both. These and other IBM trademarked terms are marked on their first occurrence in this information with the appropriate symbol (® or ™), indicating US registered or common law trademarks owned by IBM at the time this information was published. Such trademarks may also be registered or common law trademarks in other countries. A current list of IBM trademarks is available on the Web at http://www.ibm.com/legal/copytrade.shtml The following terms are trademarks of the International Business Machines Corporation in the United States, other countries, or both: Active AIX® POWER® POWER Power Power Systems Memory™ Hypervisor™ Systems™ Software™ Power® POWER POWER7 POWER8™ POWER® PowerLinux™ 7® +™ POWER® PowerHA® POWER6 ® PowerVM System System PowerVC™ POWER Power Architecture™ ® x® z® Hypervisor™ Additional Trademarks may be identified in the body of this document. Other company, product, or service names may be trademarks or service marks of others. Notices The last page of this document contains copyright information, important notices, and other information. Acknowledgements While this whitepaper has two principal authors/editors it is the culmination of the work of a number of different subject matter experts within IBM who contributed ideas, detailed technical information, and the occasional photograph and section of description. -

IBM AIX Version 6.1 Differences Guide
Front cover IBM AIX Version 6.1 Differences Guide AIX - The industrial strength UNIX operating system AIX Version 6.1 enhancements explained An expert’s guide to the new release Roman Aleksic Ismael "Numi" Castillo Rosa Fernandez Armin Röll Nobuhiko Watanabe ibm.com/redbooks International Technical Support Organization IBM AIX Version 6.1 Differences Guide March 2008 SG24-7559-00 Note: Before using this information and the product it supports, read the information in “Notices” on page xvii. First Edition (March 2008) This edition applies to AIX Version 6.1, program number 5765-G62. © Copyright International Business Machines Corporation 2007, 2008. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures . xi Tables . xiii Notices . xvii Trademarks . xviii Preface . xix The team that wrote this book . xix Become a published author . xxi Comments welcome. xxi Chapter 1. Application development and system debug. 1 1.1 Transport independent RPC library. 2 1.2 AIX tracing facilities review . 3 1.3 POSIX threads tracing. 5 1.3.1 POSIX tracing overview . 6 1.3.2 Trace event definition . 8 1.3.3 Trace stream definition . 13 1.3.4 AIX implementation overview . 20 1.4 ProbeVue . 21 1.4.1 ProbeVue terminology. 23 1.4.2 Vue programming language . 24 1.4.3 The probevue command . 25 1.4.4 The probevctrl command . 25 1.4.5 Vue: an overview. 25 1.4.6 ProbeVue dynamic tracing example . 31 Chapter 2. File systems and storage. 35 2.1 Disabling JFS2 logging . -

The Linux Users' Guide
The Linux Users' Guide Copyright c 1993, 1994, 1996 Larry Greenfield All you need to know to start using Linux, a free Unix clone. This manual covers the basic Unix commands, as well as the more specific Linux ones. This manual is intended for the beginning Unix user, although it may be useful for more experienced users for reference purposes. i UNIX is a trademark of X/Open MS-DOS and Microsoft Windows are trademarks of Microsoft Corporation OS/2 and Operating System/2 are trademarks of IBM X Window System is a trademark of X Consortium, Inc. Motif is a trademark of the Open Software Foundation Linux is not a trademark, and has no connection to UNIX, Unix System Labratories, or to X/Open. Please bring all unacknowledged trademarks to the attention of the author. Copyright c Larry Greenfield 427 Harrison Avenue Highland Park, NJ 08904 [email protected] Permission is granted to make and distribute verbatim copes of this manual provided the copyright notice and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this manual under the conditions for verbatim copying, provided also that the sections that reprint \The GNU General Public License", \The GNU Library General Public License", and other clearly marked sections held under seperate copyright are reproduced under the conditions given within them, and provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this manual into another language under the conditions for modified versions. -

Raiffeisenbank Speeds Data Warehouse, Cuts Costs with Red Hat Enterprise Linux
CUSTOMER CASE STUDY RAIFFEISENBANK SPEEDS DATA WAREHOUSE, CUTS COSTS WITH RED HAT ENTERPRISE LINUX Raiffeisenbank, a banking institution that provides a wide range of services to private and corporate clients in the Czech Republic, needed to replace the aging hardware and IBM AIX operating system that supported its data warehouse. By migrating to Red Hat Enterprise Linux running on cost-effective Hitachi servers with Intel processors, the bank has tripled system performance speed and maintained stability — while cutting total cost SOFTWARE AND of ownership (TCO) by 50%. SERVICES Red Hat® Enterprise Linux® HARDWARE Hitachi Unified Compute Platform for Oracle Database Hitachi Compute Blade 2500 Prague, Czech Republic FINANCIAL SERVICES (CB 2500) Hitachi Virtual Storage HEADQUARTERS 3,000 EMPLOYEES Platform G600 (VSP G600) 120 BRANCHES PARTNER “There are many benefits to using Red Hat MHM computer a.s. and Oracle solutions together, and also BENEFITS from moving from IBM to Intel. We feel • Achieved three times faster a combination of Red Hat and Oracle on system performance an Intel platform is a preferred solution • Anticipates 50% decrease for any company.” in total cost of ownership over five years JIŘÍ KOUTNÍK HEAD OF SYSTEM ADMINISTRATION, • Gained greater flexibility by RAIFFEISENBANK eliminating vendor lock-in facebook.com/redhatinc @redhatnews linkedin.com/company/red-hat redhat.com AGING UNIX SYSTEM TOO SLOW FOR MODERN BUSINESS Raiffeisenbank a.s. provides a wide range of banking services to private and corporate clients in the Czech Republic at more than 120 branches and business client centers. The bank offers corpo- rate and personal finance products and services related to savings, insurance, and leasing, including specialized mortgage centers and business advisors. -

Softwindows™ 95 for UNIX User's Guide (Version 5 of Softwindows
SoftWindows™ 95 for UNIX User’s Guide (Version 5 of SoftWindows 95) Document Number 007-3113-007 CONTRIBUTORS Edited by Karin Borda and Douglas B. O’Morain Production by Carlos Miqueo © 1998, Silicon Graphics, Inc.— All Rights Reserved The contents of this document may not be copied or duplicated in any form, in whole or in part, without the prior written permission of Silicon Graphics, Inc. RESTRICTED RIGHTS LEGEND Use, duplication, or disclosure of the technical data contained in this document by the Government is subject to restrictions as set forth in subdivision (c) (1) (ii) of the Rights in Technical Data and Computer Software clause at DFARS 52.227-7013 and/or in similar or successor clauses in the FAR, or in the DOD or NASA FAR Supplement. Unpublished rights reserved under the Copyright Laws of the United States. Contractor/manufacturer is Silicon Graphics, Inc., 2011 N. Shoreline Blvd., Mountain View, CA 94043-1389. TurboStart and SoftNode are registered trademarks of Insignia Solutions. SoftWindows is a trademark used under license. Silicon Graphics, the Silicon Graphics logo and IRIX are registered trademarks, and Indy, O2, and IRIS InSight are trademarks of Silicon Graphics, Inc. R5000 and R10000 are registered trademarks of MIPS Technologies, Inc. Apple and Macintosh are registered trademarks of Apple Computer, Inc. DEC is a trademark of Digital Equipment Corporation. WinPost is a trademark of Eastern Mountain Software. FLEXlm is a trademark of Globetrotter Software Inc. IBM is a registered trademark and IBM PC and IBM PC/AT are trademarks of International Business Machines Corp. Intel and Pentium are registered trademarks of Intel Corporation. -

Summary Keyboard Mapping
Technical Bulletin Product: RUMBA OFFICE 2.0 RUMBA for UNIX RUMBA for the VAX Version #: See above Host: UNIX, VAX Summary If you find that one or more of the keys you press in RUMBA for the VAX or RUMBA for UNIX doesn't produce the effect you expect, it may be that there is a mismatch between how the keyboard is mapped in RUMBA software and how the keys are mapped on the host. By remapping the characters that a key sends, RUMBA software can emulate most keyboards and be made to work with almost any application. When a key is pressed one of two things can happen. If the key defines a "local function," RUMBA software performs that function and nothing is sent to the host. One local function is the F2 or PrintScreen key. This function does not require host interaction. RUMBA software simply copies the information from the screen to the printer. If the key does not define a local function then RUMBA will send either a single character or a string of characters to the host. This document describes how to change the character or string of characters sent by RUMBA software when a key is pressed. It also covers some basic ways to determine what the host or application expects. To effectively fix key mapping problems, you will need to talk with your system administrator and possibly with the vendor of the host application you are using. Keyboard Mapping Host applications are written for a specific host keyboard. In the case of DEC and UNIX applications, this keyboard is usually a VT keyboard. -

Keyboard Scan Code Specification
Windows Platform Design Notes Designing Hardware for the Microsoft® Windows® Family of Operating Systems Keyboard Scan Code Specification Abstract: This specification details the PS/2 Scan Codes and USB Usage Tables that are validated for compliance to the Microsoft® Windows® Logo Program testing standard. This document details the alternative make and break PS/2 scan code and USB code response for the Windows Logo Key and Application Keys, plus Advanced Configuration and Power Interface (ACPI) power controls. This specification was previous published, with the same content, as “Windows Hardware Quality Labs Keyboard Specification” and also referred to as “Windows Keys Specification” and “New Keys Specification.” Revision 1.3a — March 16, 2000 Disclaimer: The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DOCUMENT. Microsoft Corporation may have patents or pending patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. The furnishing of this document does not give you any license to the patents, trademarks, copyrights, or other intellectual property rights except as expressly provided in any written license agreement from Microsoft Corporation. Microsoft does not make any representation or warranty regarding specifications in this document or any product or item developed based on these specifications. -

Programming the Cell Broadband Engine Examples and Best Practices
Front cover Draft Document for Review February 15, 2008 4:59 pm SG24-7575-00 Programming the Cell Broadband Engine Examples and Best Practices Practical code development and porting examples included Make the most of SDK 3.0 debug and performance tools Understand and apply different programming models and strategies Abraham Arevalo Ricardo M. Matinata Maharaja Pandian Eitan Peri Kurtis Ruby Francois Thomas Chris Almond ibm.com/redbooks Draft Document for Review February 15, 2008 4:59 pm 7575edno.fm International Technical Support Organization Programming the Cell Broadband Engine: Examples and Best Practices December 2007 SG24-7575-00 7575edno.fm Draft Document for Review February 15, 2008 4:59 pm Note: Before using this information and the product it supports, read the information in “Notices” on page xvii. First Edition (December 2007) This edition applies to Version 3.0 of the IBM Cell Broadband Engine SDK, and the IBM BladeCenter QS-21 platform. © Copyright International Business Machines Corporation 2007. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Draft Document for Review February 15, 2008 4:59 pm 7575TOC.fm Contents Preface . xi The team that wrote this book . xi Acknowledgements . xiii Become a published author . xiv Comments welcome. xv Notices . xvii Trademarks . xviii Part 1. Introduction to the Cell Broadband Engine . 1 Chapter 1. Cell Broadband Engine Overview . 3 1.1 Motivation . 4 1.2 Scaling the three performance-limiting walls. 6 1.2.1 Scaling the power-limitation wall . 6 1.2.2 Scaling the memory-limitation wall . -

Xterm Control Sequences
Xterm Control Sequences EdwardMoy University of California, Berkeley Revised by Stephen Gildea XConsortium (1994) Thomas Dickey XFree86 Project (1996-2003) Definitions c The literal character c. C Asingle (required) character. Ps Asingle (usually optional) numeric parameter,composed of one of more digits. Pm Amultiple numeric parameter composed of anynumber of single numeric parameters, separated by ;char- acter(s). Individual values for the parameters are listed with Ps . Pt Atextparameter composed of printable characters. C1 (8-Bit) Control Characters The xterm program recognizes both 8-bit and 7-bit control characters. It generates 7-bit controls (by default) or 8-bit if S8C1T is enabled. The following pairs of 7-bit and 8-bit control characters are equivalent: ESC D Index(IND is 0x84) ESC E Next Line ( NEL is 0x85) ESC H TabSet ( HTS is 0x88) ESC M Reverse Index( RI is 0x8d) ESC N Single Shift Select of G2 Character Set ( SS2 is 0x8e): affects next character only ESC O Single Shift Select of G3 Character Set ( SS3 is 0x8f): affects next character only ESC P Device Control String ( DCS is 0x90) ESC V Start of Guarded Area ( SPA is 0x96) Xterm Control Sequences C1 (8-Bit) Control Characters ESC W End of Guarded Area ( EPA is 0x97) ESC X Start of String ( SOS is 0x98) ESC Z Return Terminal ID (DECID is 0x9a). Obsolete form of CSI c(DA). ESC [ Control Sequence Introducer ( CSI is 0x9b) ESC \ String Terminator ( ST is 0x9c) ESC ] Operating System Command ( OSC is 0x9d) ESC ^ Privacy Message ( PM is 0x9e) ESC _ Application Program Command ( APC is 0x9f) These control characters are used in the vtXXX emulation. -
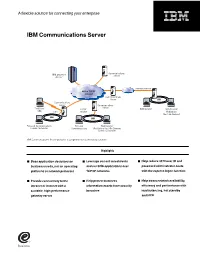
IBM Communications Server
A flexible solution for connecting your enterprise IBM Communications Server ^ Communications IBM Server zSeriesTM Internet/extranet SNA or TCP/IP intranet Communications Server LAN Communications Server Communications Server Traditional TCP/IP Web browser Web browser SNA SNA intranet WebSphere Host On-Demand LAN LAN Personal Communications Personal Web browser Screen Customizer Communications WebSphere Host On-Demand Screen Customizer IBM Communications Server provides a comprehensive connectivity solution. Highlights ■ Base application decisions on ■ Leverage current investments ■ Help reduce 3270 user ID and business needs, not on operating and run SNA applications over password administrator costs platforms or network protocols TCP/IP networks with the express logon function ■ Provide connectivity to the ■ Help protect business ■ Help boost network availability, intranet or Internet with a information assets from security efficiency and performance with scalable, high-performance breaches load balancing, hot standby gateway server and HPR As your business needs grow, place, while making the transition at applications over existing SNA chances are, so will your network. your own pace. IBM Communications networks without adding a separate Explosive growth and constant change Server can connect your employees, TCP/IP network. And you can extend in the information management and customers and trading partners to SNA applications to TCP/IP users delivery arena call for versatile the information and applications they without the addition of a separate technologies to meet your company’s need, independent of the underlying SNA network. growing needs. IBM Communications network. Designed to meet your Server meets the challenge—offering company’s growing e-business needs, Reliability and flexibility a comprehensive package of IBM Communications Server provides IBM Communications Server also enterprise networking solutions to fast, efficient ways to extend data to works as a Telnet server, providing effectively connect your employees, Web users.