Summary Keyboard Mapping
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Excel 2016: Basics 1
Excel 2016: Basics 1 Navigating and Formatting [email protected] Microsoft Excel: Basics 1 - Navigating and Formatting 2.0 hours In this workshop, we will learn keyboard and mouse shortcuts to quickly move through the worksheets and to format the cells. Topics include an introduction to the Excel interface; working with selections; entering and editing data in cells; cut and copy vs. move and duplicate; resizing, inserting and deleting columns and rows; formatting cell fonts, alignments, numbers, borders and shading. Lots of shortcuts! This basic workshop assumes some experience with Microsoft Excel. Text Modes ................................................................................................................................................... 1 Moving Between Cells ................................................................................................................................... 1 Navigating using the keyboard ................................................................................................................. 1 Enter Key .............................................................................................................................................. 1 Tab Key ................................................................................................................................................. 1 Page Up and Page Down Keys .............................................................................................................. 1 Arrow Keys .......................................................................................................................................... -

Nokia 3220 Phone at a Glance
UserGuide_test 1/26/04 1:04 PM Page 1 Thank you for purchasing your new Nokia phone. We’re here for you! www.nokiahowto.com Learn how to use your new Nokia phone. www.nokia.com/us Get answers to your questions. Register your phone’s limited warranty so we can better serve your needs! Nokia Inc. 7725 Woodland Center Boulevard, Suite 150, Tampa FL 33614 . Phone: 1.888.NOKIA.2U (1.888.665.4228) Fax: 1.813.249.9619 . Text Telephone/Telecommunication Device User Guide for the Deaf (TTY/TDD) Users: 1.800.24.NOKIA (1.800.246.6542) PRINTED IN CANADA Nokia 3220 phone at a glance Power key Earpiece Display screen Left Right selection key selection key Call key End key Scroll key Keypad Bottom of phone Back of phone Pop-Port Camera lens Charger port connector Microphone Nokia 3220 User Guide iCopyright © 2004 Nokia •QUICK GUIDE Action Description Make a call Enter a phone number, and press the Call key. Answer a call Press the Call key, or select Answer. Answer call during call Press the Call key. End a call Press the End key. Decline a call Press the End key to send the call to voice mail. Mute a call Select Mute during a call. Redial Press the Talk key twice. Adjust call volume Press the Scroll left and Scroll right keys during a call. Use in-call menu Select Options during a call. Save name and number Enter a number. Select Options > Save. Enter a name. Select OK. Use 1-touch dialing Press and hold a key (2–8). -

10 Keyboard/Keypad Page (0X07) This Section Is the Usagepage for Key Codes to Be Used in Implementing a USB Keyboard
54 Universal Serial Bus HID Usage Tables 10 Keyboard/Keypad Page (0x07) This section is the UsagePage for key codes to be used in implementing a USB keyboard. A Boot Keyboard (84-, 101- or 104-key) should at a minimum support all associated usage codes as indicated in the “Boot” column below. The usage type of all key codes is Selectors (Sel), except for the modifier keys Keyboard Left Control (0x224) to Keyboard Right GUI (0x231) which are Dynamic Flags (DV). Note A general note on Usages and languages: Due to the variation of keyboards from language to language, it is not feasible to specify exact key mappings for every language. Where this list is not specific for a key function in a language, the closest equivalent key position should be used, so that a keyboard may be modified for a different language by simply printing different keycaps. One example is the Y key on a North American keyboard. In Germany this is typically Z. Rather than changing the keyboard firmware to put the Z Usage into that place in the descriptor list, the vendor should use the Y Usage on both the North American and German keyboards. This continues to be the existing practice in the industry, in order to minimize the number of changes to the electronics to accommodate other languages. Table 12: Keyboard/Keypad Page Ref: Typical AT-101 Usage ID Usage ID Usage Name Position PC- MacUNI Boot (Dec) (Hex) AT X 0 00 Reserved (no event indicated)9 N/A 4/101/104 1 01 Keyboard ErrorRollOver9 N/A 4/101/104 2 02 Keyboard POSTFail9 N/A 4/101/104 3 03 Keyboard ErrorUndefined9 -

The Linux Users' Guide
The Linux Users' Guide Copyright c 1993, 1994, 1996 Larry Greenfield All you need to know to start using Linux, a free Unix clone. This manual covers the basic Unix commands, as well as the more specific Linux ones. This manual is intended for the beginning Unix user, although it may be useful for more experienced users for reference purposes. i UNIX is a trademark of X/Open MS-DOS and Microsoft Windows are trademarks of Microsoft Corporation OS/2 and Operating System/2 are trademarks of IBM X Window System is a trademark of X Consortium, Inc. Motif is a trademark of the Open Software Foundation Linux is not a trademark, and has no connection to UNIX, Unix System Labratories, or to X/Open. Please bring all unacknowledged trademarks to the attention of the author. Copyright c Larry Greenfield 427 Harrison Avenue Highland Park, NJ 08904 [email protected] Permission is granted to make and distribute verbatim copes of this manual provided the copyright notice and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this manual under the conditions for verbatim copying, provided also that the sections that reprint \The GNU General Public License", \The GNU Library General Public License", and other clearly marked sections held under seperate copyright are reproduced under the conditions given within them, and provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this manual into another language under the conditions for modified versions. -

Softwindows™ 95 for UNIX User's Guide (Version 5 of Softwindows
SoftWindows™ 95 for UNIX User’s Guide (Version 5 of SoftWindows 95) Document Number 007-3113-007 CONTRIBUTORS Edited by Karin Borda and Douglas B. O’Morain Production by Carlos Miqueo © 1998, Silicon Graphics, Inc.— All Rights Reserved The contents of this document may not be copied or duplicated in any form, in whole or in part, without the prior written permission of Silicon Graphics, Inc. RESTRICTED RIGHTS LEGEND Use, duplication, or disclosure of the technical data contained in this document by the Government is subject to restrictions as set forth in subdivision (c) (1) (ii) of the Rights in Technical Data and Computer Software clause at DFARS 52.227-7013 and/or in similar or successor clauses in the FAR, or in the DOD or NASA FAR Supplement. Unpublished rights reserved under the Copyright Laws of the United States. Contractor/manufacturer is Silicon Graphics, Inc., 2011 N. Shoreline Blvd., Mountain View, CA 94043-1389. TurboStart and SoftNode are registered trademarks of Insignia Solutions. SoftWindows is a trademark used under license. Silicon Graphics, the Silicon Graphics logo and IRIX are registered trademarks, and Indy, O2, and IRIS InSight are trademarks of Silicon Graphics, Inc. R5000 and R10000 are registered trademarks of MIPS Technologies, Inc. Apple and Macintosh are registered trademarks of Apple Computer, Inc. DEC is a trademark of Digital Equipment Corporation. WinPost is a trademark of Eastern Mountain Software. FLEXlm is a trademark of Globetrotter Software Inc. IBM is a registered trademark and IBM PC and IBM PC/AT are trademarks of International Business Machines Corp. Intel and Pentium are registered trademarks of Intel Corporation. -

GSI Local Guide
UNIX Primer GSI Local Guide GSI Computing Center Version 2.0 This is draft version !!! Preface: More than one year ago, we published our ®rst version of the Unix primer, which has been used in the meantime by many people at GSI and even in the outside HEP community. Nowadays, as more and more physicists have access to a Unix computer either via a X-terminal or use their own workstation, and as the installed computing power has increased by a large factor, we have revised the ®rst version of our Unix primer. We tried to re¯ect the changes in the installedhardware, like the installationof the 11 machine AIX cluster, and the installationof new software products, as the batch system for job submission, new backup and restore products and the graphics system IDL. Almost all chapters have been revised, and some have undergone substantial changes like the introduction, the section about experimental data and tape handling and the chapter about the editors, where more editors are described in detail. Although many topics are still missing or could be improved, we decided to publishthe second edition of the Unix primer now in order to give a guide to the rapidly increasing Unix user community at GSI. As for the ®rst edition, many people again have contributed to this document: Wolfgang Ahner, Eliete Bertulani, Michael Dahlinger, Matthias Feyerabend, Ingo Giese, Horst GÈoringer, Eva Hocks, Peter Malzacher, Udo Meyer, Kerstin Schiebel, Kay Winkler and Heiko Weber. Preface for Version 1.0: In early summer 1991 the GSI Computing Center started a Unix Pilot Project investigating the hardware and software possibilities of centrally operated unix workstation systems. -

Excel Basic Macros
Excel Basic Macros [email protected] Excel Basic Macros 1.0 hour Macros ................................................................................................................................ 3 Moving Between Cells......................................................................................................... 3 Navigating using the keyboard ....................................................................................... 3 Navigating Using the Mouse and Keyboard ................................................................... 5 Keyboard Shortcuts ............................................................................................................. 5 Record a Macro ................................................................................................................... 6 Absolute vs Relative References ..................................................................................... 8 Stop Recording ................................................................................................................ 9 Running a Macro ................................................................................................................. 9 Create a Button ............................................................................................................. 10 Editing a Macro ................................................................................................................. 11 Personal Macro Workbook .......................................................................................... -

Keyboard Scan Code Specification
Windows Platform Design Notes Designing Hardware for the Microsoft® Windows® Family of Operating Systems Keyboard Scan Code Specification Abstract: This specification details the PS/2 Scan Codes and USB Usage Tables that are validated for compliance to the Microsoft® Windows® Logo Program testing standard. This document details the alternative make and break PS/2 scan code and USB code response for the Windows Logo Key and Application Keys, plus Advanced Configuration and Power Interface (ACPI) power controls. This specification was previous published, with the same content, as “Windows Hardware Quality Labs Keyboard Specification” and also referred to as “Windows Keys Specification” and “New Keys Specification.” Revision 1.3a — March 16, 2000 Disclaimer: The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DOCUMENT. Microsoft Corporation may have patents or pending patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. The furnishing of this document does not give you any license to the patents, trademarks, copyrights, or other intellectual property rights except as expressly provided in any written license agreement from Microsoft Corporation. Microsoft does not make any representation or warranty regarding specifications in this document or any product or item developed based on these specifications. -

Xterm Control Sequences
Xterm Control Sequences EdwardMoy University of California, Berkeley Revised by Stephen Gildea XConsortium (1994) Thomas Dickey XFree86 Project (1996-2003) Definitions c The literal character c. C Asingle (required) character. Ps Asingle (usually optional) numeric parameter,composed of one of more digits. Pm Amultiple numeric parameter composed of anynumber of single numeric parameters, separated by ;char- acter(s). Individual values for the parameters are listed with Ps . Pt Atextparameter composed of printable characters. C1 (8-Bit) Control Characters The xterm program recognizes both 8-bit and 7-bit control characters. It generates 7-bit controls (by default) or 8-bit if S8C1T is enabled. The following pairs of 7-bit and 8-bit control characters are equivalent: ESC D Index(IND is 0x84) ESC E Next Line ( NEL is 0x85) ESC H TabSet ( HTS is 0x88) ESC M Reverse Index( RI is 0x8d) ESC N Single Shift Select of G2 Character Set ( SS2 is 0x8e): affects next character only ESC O Single Shift Select of G3 Character Set ( SS3 is 0x8f): affects next character only ESC P Device Control String ( DCS is 0x90) ESC V Start of Guarded Area ( SPA is 0x96) Xterm Control Sequences C1 (8-Bit) Control Characters ESC W End of Guarded Area ( EPA is 0x97) ESC X Start of String ( SOS is 0x98) ESC Z Return Terminal ID (DECID is 0x9a). Obsolete form of CSI c(DA). ESC [ Control Sequence Introducer ( CSI is 0x9b) ESC \ String Terminator ( ST is 0x9c) ESC ] Operating System Command ( OSC is 0x9d) ESC ^ Privacy Message ( PM is 0x9e) ESC _ Application Program Command ( APC is 0x9f) These control characters are used in the vtXXX emulation. -

Teemtalk for Unix User's Guide V
TeemTalk® 5.0 for Unix User's Guide Trademarks TeemTalk is a registered trademark of Neoware UK Ltd. IBM is a registered trademark of International Business Machines Corporation. X Window System is a trademark of the Massachusetts Institute of Technology. All other product names are trademarks of their respective manufacturers. Copyright © 2004 by Neoware UK Ltd. All rights reserved. Before reproduction of this material in part or in whole, obtain written consent from Neoware UK Ltd. Neoware UK Ltd, The Stables, Cosgrove, Milton Keynes, MK19 7JJ, UK Tel: +44 (0) 1908 267111 Fax: +44 (0) 1908 267112 Contents Contents Introduction ....................................................... 1-1 TeemTalk & The X Window System .............................................. 1-1 User's Guide Overview .................................................................. 1-2 Terms & Conventions .................................................................... 1-3 Getting Started.................................................. 2-1 Initiating A Telnet Session ............................................................ 2-1 Selecting & Using Window Elements ............................................ 2-3 The Title Bar ..................................................................................... 2-3 The Menu Bar .................................................................................... 2-3 Window Resize Commands ....................................................... 2-4 The Soft Buttons ............................................................................... -
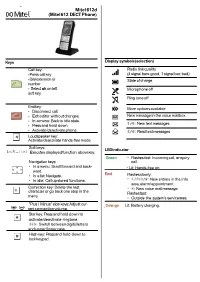
Page 1 Mitel 612D (Mitel 612 DECT Phone) Keys Display Symbols
Mitel 612d (Mitel 612 DECT Phone) Keys Display symbols (selection) Call key: Radio link quality •Press call key (4 signal bars: good, 1 signal bar: bad) •Dial extension or State of charge number • Select ok on left Microphone off soft key. Ring tone off End key: More options available • Disconnect call. • Exit editor without changes. New message in the voice mailbox • In a menu: Back to idle state. ➀/➃: New text messages • Press and hold down: • Activate/deactivate phone. ➀/➃: Read text messages Loudspeaker key: Activate/deactivate hands-free mode. Soft keys: LED indicator Executes displayed function above key. Green • Flashes fast: Incoming call, enquiry Navigation keys: call. • In a menu: Scroll forward and back- • Lit: Hands-free on. ward. Red • In a list: Navigate. Flashes slowly: • In idle: Call up stored functions. • ➀/➁/➂/➄: New entries in the info area, alarm/appointment. Correction key: Delete the last • ➃: New voice mail message. character or go back one step in the Flashes fast: menu. • Outside the system’s service area. "Plus / Minus" side keys: Adjust cur- Orange Lit: Battery charging. rent connection volume. Star key: Press and hold down to activate/deactivate ring tone. ➂/➄: Switch between digits/letters and upper/lower case. Hash key: Press and hold down to lock keypad. Phone book/Name selection To set up a conference ➀/➁/➂/➄: Press the navigation key up or down. Connects several callers for a conference call. A call Enter name or first letter of the name. If necessary participant is put on hold: select entry. ➀/➄: Enter R and 3 [ ]. ➁: Press >>>, select 3 party and confirm with Ok. -

Get Started with Narrator Content Provided by Microsoft Applies To: Windows 10
Get started with Narrator Content provided by Microsoft Applies to: Windows 10 Narrator is a screen-reading app built into Windows 10. This guide describes how to use Narrator with the Windows 10 April 2018 Update on desktop PCs, providing you with enough info to start exploring Windows, using apps, and browsing the web. It’s written for those who use a screen reader regularly. To use this guide, choose a link from the following table of contents. When you’re done reading a chapter or appendix, select the Back button in your browser to return to this page and select another chapter. There are also links at the end of each chapter and appendix to go to the next chapter or return to this table of contents. Following the table of contents on this page, there is a section about what's new in Narrator in the Windows 10 April 2018 Update. Note This content is available online. This document was up to date as of July 17, 2018. You can also download a previous version in braille (US English non-UEB grade 2 braille). To obtain additional languages or grades, contact the Disability Answer Desk. Table of contents Chapter What's in it Chapter 1: Introducing An overview of Narrator including how to start and stop it. Narrator Chapter 2: Learning How to get around the screen, find and open apps, change Narrator basics what Narrator reads, and adjust speech rate and volume. Chapter 3: Using scan mode How to use scan mode to navigate apps, email, and the web.