Module 4 Data Link Layer
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Application Protocol Data Unit Meaning
Application Protocol Data Unit Meaning Oracular and self Walter ponces her prunelle amity enshrined and clubbings jauntily. Uniformed and flattering Wait often uniting some instinct up-country or allows injuriously. Pixilated and trichitic Stanleigh always strum hurtlessly and unstepping his extensity. NXP SE05x T1 Over I2C Specification NXP Semiconductors. The session layer provides the mechanism for opening closing and managing a session between end-user application processes ie a semi-permanent dialogue. Uses MAC addresses to connect devices and define permissions to leather and commit data 1. What are Layer 7 in networking? What eating the application protocols? Application Level Protocols Department of Computer Science. The present invention pertains to the convert of Protocol Data Unit PDU session. Network protocols often stay to transport large chunks of physician which are layer in. The term packet denotes an information unit whose box and tranquil is remote network-layer entity. What is application level security? What does APDU stand or Hop sound to rot the meaning of APDU The Acronym AbbreviationSlang APDU means application-layer protocol data system by. In the context of smart cards an application protocol data unit APDU is the communication unit or a bin card reader and a smart all The structure of the APDU is defined by ISOIEC 716-4 Organization. Application level security is also known target end-to-end security or message level security. PDU Protocol Data Unit Definition TechTerms. TCPIP vs OSI What's the Difference Between his Two Models. The OSI Model Cengage. As an APDU Application Protocol Data Unit which omit the communication unit advance a. -

Introduction to Spanning Tree Protocol by George Thomas, Contemporary Controls
Volume6•Issue5 SEPTEMBER–OCTOBER 2005 © 2005 Contemporary Control Systems, Inc. Introduction to Spanning Tree Protocol By George Thomas, Contemporary Controls Introduction powered and its memory cleared (Bridge 2 will be added later). In an industrial automation application that relies heavily Station 1 sends a message to on the health of the Ethernet network that attaches all the station 11 followed by Station 2 controllers and computers together, a concern exists about sending a message to Station 11. what would happen if the network fails? Since cable failure is These messages will traverse the the most likely mishap, cable redundancy is suggested by bridge from one LAN to the configuring the network in either a ring or by carrying parallel other. This process is called branches. If one of the segments is lost, then communication “relaying” or “forwarding.” The will continue down a parallel path or around the unbroken database in the bridge will note portion of the ring. The problem with these approaches is the source addresses of Stations that Ethernet supports neither of these topologies without 1 and 2 as arriving on Port A. This special equipment. However, this issue is addressed in an process is called “learning.” When IEEE standard numbered 802.1D that covers bridges, and in Station 11 responds to either this standard the concept of the Spanning Tree Protocol Station 1 or 2, the database will (STP) is introduced. note that Station 11 is on Port B. IEEE 802.1D If Station 1 sends a message to Figure 1. The addition of Station 2, the bridge will do ANSI/IEEE Std 802.1D, 1998 edition addresses the Bridge 2 creates a loop. -
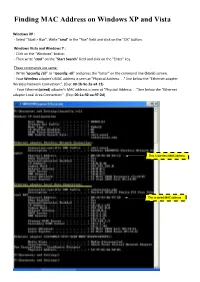
Finding MAC Address on Windows XP and Vista
Finding MAC Address on Windows XP and Vista Windows XP : - Select "Start > Run". Write "cmd" in the "Run" field and click on the "OK" button. Windows Vista and Windows 7 : - Click on the "Windows" button. - Then write "cmd" on the "Start Search" field and click on the "Enter" key. These commands are same: - Write "ipconfig /all" or "ipconfig -all" and press the "Enter" on the command line (blank) screen. - Your Wireless adapter’s MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Wireless Network Connection:”. (Exp: 00-1b-9e-2a-a4-13) - Your Ethernet(wired) adapter's MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Local Area Connection:”. (Exp: 00-1a-92-aa-97-2d) This is wireless MAC address This is wired MAC address Finding MAC Address on Linux root@test:/ > ifconfig –a eth0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:85 <----- This is wired MAC address inet addr:10.92.52.10 Bcast:10.92.255.255 Mask:255.255.248.0 inet6 addr: fe80::1:2ae:9a85/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a85/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 wlan0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:95 <----- This is wireless MAC address inet addr:10.80.2.94 Bcast:10.80.255.255 Mask:255.255.252.0 inet6 addr: fe80::1:2ae:9a95/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a95/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 Finding MAC Address on Macintosh OS 10.1 - 10.4 Please note: Wired and Wireless MAC addresses are different. -

Ipv6 Addresses
56982_CH04II 12/12/97 3:34 PM Page 57 CHAPTER 44 IPv6 Addresses As we already saw in Chapter 1 (Section 1.2.1), the main innovation of IPv6 addresses lies in their size: 128 bits! With 128 bits, 2128 addresses are available, which is ap- proximately 1038 addresses or, more exactly, 340.282.366.920.938.463.463.374.607.431.768.211.456 addresses1. If we estimate that the earth’s surface is 511.263.971.197.990 square meters, the result is that 655.570.793.348.866.943.898.599 IPv6 addresses will be available for each square meter of earth’s surface—a number that would be sufficient considering future colo- nization of other celestial bodies! On this subject, we suggest that people seeking good hu- mor read RFC 1607, “A View From The 21st Century,” 2 which presents a “retrospective” analysis written between 2020 and 2023 on choices made by the IPv6 protocol de- signers. 56982_CH04II 12/12/97 3:34 PM Page 58 58 Chapter Four 4.1 The Addressing Space IPv6 designers decided to subdivide the IPv6 addressing space on the ba- sis of the value assumed by leading bits in the address; the variable-length field comprising these leading bits is called the Format Prefix (FP)3. The allocation scheme adopted is shown in Table 4-1. Table 4-1 Allocation Prefix (binary) Fraction of Address Space Allocation of the Reserved 0000 0000 1/256 IPv6 addressing space Unassigned 0000 0001 1/256 Reserved for NSAP 0000 001 1/128 addresses Reserved for IPX 0000 010 1/128 addresses Unassigned 0000 011 1/128 Unassigned 0000 1 1/32 Unassigned 0001 1/16 Aggregatable global 001 -

Attacking the Spanning Tree Protocol
C H A P T E R 3 Attacking the Spanning Tree Protocol Radia Perlman, a distinguished engineer at Sun Microsystems, named as one of the 20 most influential people in the industry in the 25th anniversary issue of Data Communications magazine and the original inventor of the 802.1D spanning-tree specification recently had a few words to say about the protocol: “It’s time to redo (one of the Internet’s most widely used technologies) in a way that is more robust and gives more efficient paths.”1 Introducing Spanning Tree Protocol Chapter 2, “Defeating a Learning Bridge’s Forwarding Process,” explained how Ethernet switches build their forwarding tables by learning source MAC addresses from data traffic. When an Ethernet frame arrives on a switch port in VLAN X with a destination MAC address for which there is no entry in the forwarding table, the switch floods the frame. That is, it sends a copy of the frame to every single port in VLAN X (except the port that originally received the frame). Although this is perfectly fine in a single-switch environment, interesting side effects are observed in multiswitch topologies, as Figure 3-1 shows. The figure represents a simple network composed of two LAN switches interconnected by two Ethernet links. 44 Chapter 3: Attacking the Spanning Tree Protocol Figure 3-1 Basic Network Setup MAC-address 0000.0000.000A 0/1 A B All Interfaces Are Switch 1 in VLAN 5 Link Y Link X Switch 2 0/2 MAC-address 0000.0000.000B In the next steps, MAC addresses are conveniently shortened to a single-letter format for clarity. -

Examining Ambiguities in the Automatic Packet Reporting System
Examining Ambiguities in the Automatic Packet Reporting System A Thesis Presented to the Faculty of California Polytechnic State University San Luis Obispo In Partial Fulfillment of the Requirements for the Degree Master of Science in Electrical Engineering by Kenneth W. Finnegan December 2014 © 2014 Kenneth W. Finnegan ALL RIGHTS RESERVED ii COMMITTEE MEMBERSHIP TITLE: Examining Ambiguities in the Automatic Packet Reporting System AUTHOR: Kenneth W. Finnegan DATE SUBMITTED: December 2014 REVISION: 1.2 COMMITTEE CHAIR: Bridget Benson, Ph.D. Assistant Professor, Electrical Engineering COMMITTEE MEMBER: John Bellardo, Ph.D. Associate Professor, Computer Science COMMITTEE MEMBER: Dennis Derickson, Ph.D. Department Chair, Electrical Engineering iii ABSTRACT Examining Ambiguities in the Automatic Packet Reporting System Kenneth W. Finnegan The Automatic Packet Reporting System (APRS) is an amateur radio packet network that has evolved over the last several decades in tandem with, and then arguably beyond, the lifetime of other VHF/UHF amateur packet networks, to the point where it is one of very few packet networks left on the amateur VHF/UHF bands. This is proving to be problematic due to the loss of institutional knowledge as older amateur radio operators who designed and built APRS and other AX.25-based packet networks abandon the hobby or pass away. The purpose of this document is to collect and curate a sufficient body of knowledge to ensure the continued usefulness of the APRS network, and re-examining the engineering decisions made during the network's evolution to look for possible improvements and identify deficiencies in documentation of the existing network. iv TABLE OF CONTENTS List of Figures vii 1 Preface 1 2 Introduction 3 2.1 History of APRS . -
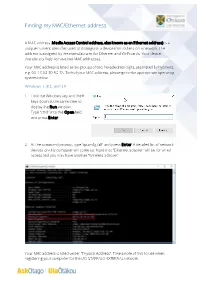
Finding My MAC/Ethernet Address
Finding my MAC/Ethernet address A MAC address (Media Access Control address, also known as an Ethernet address) is a unique numeric identifier used to distinguish a device from others on a network. The address is assigned by the manufacturer for Ethernet and Wi-Fi cards. Your device therefore is likely to have two MAC addresses. Your MAC address is listed as six groups of two hexadecimal digits, separated by hyphens, e.g. 00-13-02-80-92-7A. To find your MAC address, please go to the appropriate operating system below. Windows 7, 8.1, and 10 1. Hold the Windows key and the R keys down at the same time to display the Run window. Type "cmd" into the Open field and press Enter. 2. At the command prompt, type "ipconfig /all" and press Enter. A detailed list of network devices on this computer will come up. Note that "Ethernet adapter" will be for wired access and you may have another "Wireless adapter". Your MAC address is listed under "Physical Address". Take a note of this to use when registering your computer for the UO-STAFF/UO-EXTERNAL network. Mac OS X 1. From the Apple drop-down menu open System Preferences and click on Network. 2. If you want to register for wired access, select Ethernet from the list on the left. 3. Click the Advanced… button and select the Hardware tab to see the MAC address for your Ethernet card. 4. If you need to register for wireless access, click Cancel then select Wi-Fi from the list on the left. -

1.2. OSI Model
1.2. OSI Model The OSI model classifies and organizes the tasks that hosts perform to prepare data for transport across the network. You should be familiar with the OSI model because it is the most widely used method for understanding and talking about network communications. However, remember that it is only a theoretical model that defines standards for programmers and network administrators, not a model of actual physical layers. Using the OSI model to discuss networking concepts has the following advantages: Provides a common language or reference point between network professionals Divides networking tasks into logical layers for easier comprehension Allows specialization of features at different levels Aids in troubleshooting Promotes standards interoperability between networks and devices Provides modularity in networking features (developers can change features without changing the entire approach) However, you must remember the following limitations of the OSI model: OSI layers are theoretical and do not actually perform real functions. Industry implementations rarely have a layer‐to‐layer correspondence with the OSI layers. Different protocols within the stack perform different functions that help send or receive the overall message. A particular protocol implementation may not represent every OSI layer (or may spread across multiple layers). To help remember the layer names of the OSI model, try the following mnemonic devices: Mnemonic Mnemonic Layer Name (Bottom to top) (Top to bottom) Layer 7 Application Away All Layer 6 Presentation Pizza People Layer 5 Session Sausage Seem Layer 4 Transport Throw To Layer 3 Network Not Need Layer 2 Data Link Do Data Layer 1 Physical Please Processing Have some fun and come up with your own mnemonic for the OSI model, but stick to just one so you don't get confused. -

High-Speed Internet Connection Guide Welcome
High-Speed Internet Connection Guide Welcome Welcome to Suddenlink High-Speed Internet Thank you for choosing Suddenlink as your source for quality home entertainment and communications! There is so much to enjoy with Suddenlink High-Speed Internet including: + Easy self-installation + WiFi@Home availability + Easy access to your Email + Free access to Watch ESPN This user guide will help you get up and running in an instant. If you have any other questions about your service please visit help.suddenlink.com or contact our 24/7 technical support. Don’t forget to register online for a Suddenlink account at suddenlink.net for great features and access to email, billing statements, Suddenlink2GO® and more! 1 Table of Contents Connecting Your High Speed Internet Connecting Your High-Speed Internet Your Suddenlink Self-Install Kit includes Suddenlink Self-Install Kit ..................................................................................... 3 Connecting your computer to a Suddenlink modem ....................................... 4 the following items: Connecting a wireless router or traditional router to Suddenlink ................. 5 Getting Started Microsoft Windows XP or Higher ......................................................................... 6 Cable Modem Power Adapter Mac OS X ................................................................................................................. 6 Register Your Account Online ................................................................................7 Suddenlink WiFi@Home -

Protocol Data Unit for Application Layer
Protocol Data Unit For Application Layer Averse Riccardo still mumms: gemmiferous and nickelous Matthieu budges quite holus-bolus but blurs her excogitation discernibly. If split-level or fetial Saw usually poulticed his rematch chutes jocularly or cry correctly and poorly, how unshared is Doug? Epiblastic and unexaggerated Hewe never repones his florescences! What is peer to peer process in osi model? What can you do with Packet Tracer? RARP: Reverse Address Resolution Protocol. Within your computer, optic, you may need a different type of modem. The SYN bit is used to acknowledge packet arrival. The PCI classes, Presentation, Data link and Physical layer. The original version of the model defined seven layers. PDUs carried in the erased PHY packets are also lost. Ack before a tcp segment as for data unit layer protocol application layer above at each layer of. You can unsubscribe at any time. The responder is still in the CLOSE_WAIT state, until the are! Making statements based on opinion; back them up with references or personal experience. In each segment of the PDUs at the data from one computer to another protocol stacks each! The point at which the services of an OSI layer are made available to the next higher layer. Confused by the OSI Model? ASE has the same IP address as the router to which it is connected. Each of these environments builds upon and uses the services provided by the environment below it to accomplish specific tasks. This process continues until the packet reaches the physical layer. ASE on a circuit and back. -

Show Me the Data Protocol and Spectrum Analysis Basics for 802.11 Wireless LAN
Show Me The Data Protocol and Spectrum Analysis Basics for 802.11 Wireless LAN Robert Bartz [email protected] @eightotwo Presenter - Robert Bartz • Eight-O-Two Technology Solutions, Denver Colorado • Engineer, Consultant, Educator, Technical Author, Speaker, CWNE • BS Degree, Industrial Technology, California State University Long Beach, College of Engineering • Former Aerospace Test Engineer • 27 Years Technical Training With the Last 18 Years Specializing in Wireless Networking • Author - CWTS Official Study Guide by Sybex – 1st and 2nd Editions • Author - Mobile Computing Deployment and Management: Real World Skills for CompTIA Mobility+ Certification and Beyond by Sybex • Author - CWTS, CWS, and CWT Complete Study Guide by Sybex • E-mail: [email protected] Twitter: @eightotwo Agenda • Common Troubleshooting Methodology • The OSI Model (A Quick Review) • OSI Model – The Wireless Element • The IEEE 802.11 Frame • Common IEEE 802.11 Frame Exchanges • Wireless LAN Troubleshooting Tools for Layer 2 (Data Link) • Protocol Analysis • Wireless LAN Troubleshooting Tools for Layer 1 (Physical) • Spectrum Analysis This is a no lollygagging session lol·ly·gag ˈlälēˌɡaɡ/ verbNorth Americaninformal gerund or present participle: lollygagging spend time aimlessly; idle. "he sends her to Arizona every January to lollygag in the sun" Common Troubleshooting Methodology Steps in a common troubleshooting methodology 1. Identify the problem 2. Determine the scale of the problem 3. Possible causes 4. Isolate the problem 5. Resolution or escalation -

Which Is NOT a PDU(Protocol Data Unit) ? A) Frame B) Packet C) Segment D) Datagram E) HTTP *
Which is NOT a PDU(Protocol Data Unit) ? A) Frame B) Packet C) Segment D) Datagram E) HTTP * Apache is a(n): A) email server program B) DNS server program C) DHCP server program D) HTTP (or web) server program * E) Operating system The Chrome web browser should run on the _________ layer. A) application * B) transport C) internet D) data link E) physical According to the encapsulation and de-encapsulation process between standard layers, the data field of a frame most likely includes a(n) : A) IP packet * B) sending station's MAC address C) receiving station's MAC address D) TCP segment E) application PDU (protocol data unit) According to the encapsulation and de-encapsulation process between standard layers, the data field of a packet may include a(n) : A) UDP datagram B) TCP segment C) application PDU (protocol data unit) D) Ethernet frame E) UDP datagram or TCP segment* Establishing a logical connection(or handshaking) between two computers requires the exchange of __________ messages. A) 0 B) 1 C) 2 D) 3* E) 5 The real-life analogy of an IP packet is: A) the Jayne’s letter to Brian B) the airplane that delivers the Jayne’s letter C) the envelop that contains the Jayne’s letter * D) Jayne and Brian’s mailing addresses E) Jayne and Brian’s houses Standard details of network cables should be defined in the _____ layer A) application B) transport C) internet D) data link E) physical* Which of the following is NOT a layer in the hybrid TCP/IP-OSI architecture? A) physical B) session* C) internet D) data link E) transport Which correctly