Spanning Tree (STP) Feature Overview and Configuration Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

How to Set up IP Camera by Using a Macintosh Computer
EDIMAX COMPUTER INC. Edimax IP Camera series How to set up IP Camera by using a Macintosh computer 2011 Edimax Computer 3350 Scott Blvd., Building #15 Santa Clara, California 95054, USA Phone 408-496-1105 • Fax 408-980-1530 www.edimax.us How to setup Edimax IP Camera by a Macintosh computer Introduction The most important thing to setup IP Camera is to assign a static IP address so the camera can work with your network. So far the Edimax IP Cam Admin utility is Windows based only and the program can not work for Macintosh computers. Macintosh users can follow this guide to set up Edimax IP camera. Step 1. Understand the IP address used in your network. Have your Macintosh computer operate as usual. Go into System Preferences. In System Preferences, Go to Network. Select the adapter you are using. It could be an Airport card, a third- party Wireless card, or an Ethernet Adapter. Write down the IP address, subnet mask, Router, and DNS server address. We have a usb wireless card in this example. Its IP address 10.0.1.2 told us that the IP addresses used in the network are 10.0.1.x. All the devices in the network have the first three octets the same, but the last octet number must be different. We decide to give our new camera an IP address 10.0.1.100 because no other computer device use 10.0.1.100. We temporarily disconnect the wireless adapter. You can turn off your Airport adapter if you use it to get on Internet. -

Ieee 802.1 for Homenet
IEEE802.org/1 IEEE 802.1 FOR HOMENET March 14, 2013 IEEE 802.1 for Homenet 2 Authors IEEE 802.1 for Homenet 3 IEEE 802.1 Task Groups • Interworking (IWK, Stephen Haddock) • Internetworking among 802 LANs, MANs and other wide area networks • Time Sensitive Networks (TSN, Michael David Johas Teener) • Formerly called Audio Video Bridging (AVB) Task Group • Time-synchronized low latency streaming services through IEEE 802 networks • Data Center Bridging (DCB, Pat Thaler) • Enhancements to existing 802.1 bridge specifications to satisfy the requirements of protocols and applications in the data center, e.g. • Security (Mick Seaman) • Maintenance (Glenn Parsons) IEEE 802.1 for Homenet 4 Basic Principles • MAC addresses are “identifier” addresses, not “location” addresses • This is a major Layer 2 value, not a defect! • Bridge forwarding is based on • Destination MAC • VLAN ID (VID) • Frame filtering for only forwarding to proper outbound ports(s) • Frame is forwarded to every port (except for reception port) within the frame's VLAN if it is not known where to send it • Filter (unnecessary) ports if it is known where to send the frame (e.g. frame is only forwarded towards the destination) • Quality of Service (QoS) is implemented after the forwarding decision based on • Priority • Drop Eligibility • Time IEEE 802.1 for Homenet 5 Data Plane Today • 802.1Q today is 802.Q-2011 (Revision 2013 is ongoing) • Note that if the year is not given in the name of the standard, then it refers to the latest revision, e.g. today 802.1Q = 802.1Q-2011 and 802.1D -

IEEE 802.1Aq Standard, Is a Computer Networking Technology Intended to Simplify the Creation and Configuration of Networks, While Enabling Multipath Routing
Brought to you by: Brian Miller Yuri Spillman - Specified in the IEEE 802.1aq standard, is a computer networking technology intended to simplify the creation and configuration of networks, while enabling multipath routing. - Link State Protocol - Based on IS-IS -The standard is the replacement for the older spanning tree protocols such as IEEE 802.1D, IEEE 802.1w, and IEEE 802.1s. These blocked any redundant paths that could result in layer 2(Data Link Layer), whereas IEEE 802.1aq allows all paths to be active with multiple equal cost paths, and provides much larger layer 2 topologies. 802.1aq is an amendment to the "Virtual Bridge Local Area Networks“ and adds Shortest Path Bridging (SPB). Shortest path bridging, which is undergoing IEEE’s standardization process, is meant to replace the spanning tree protocol (STP). STP was created to prevent bridge loops by allowing only one path between network switches or ports. When a network segment goes down, an alternate path is chosen and this process can cause unacceptable delays in a data center network. The ability to use all available physical connectivity, because loop avoidance uses a Control Plane with a global view of network topology Fast restoration of connectivity after failure, again because of Link State routing's global view of network topology Under failure, the property that only directly affected traffic is impacted during restoration; all unaffected traffic just continues Ideas are rejected by IEEE 802.1. accepted by the IETF and the TRILL WG is formed. Whoops, there is a problem. They start 802.1aq for spanning tree based shortest path bridging Whoops, spanning tree doesn’t hack it. -

IEEE 802.11Be Multi-Link Operation: When the Best Could Be to Use Only a Single Interface
IEEE 802.11be Multi-Link Operation: When the Best Could Be to Use Only a Single Interface Alvaro´ L´opez-Ravent´os Boris Bellalta Dept. Information and Communication Technologies Dept. Information and Communication Technologies Universitat Pompeu Fabra (UPF) Universitat Pompeu Fabra (UPF) Barcelona, Spain Barcelona, Spain [email protected] [email protected] Abstract—The multi-link operation (MLO) is a new feature can find the most disruptive updates. We refer to the adoption proposed to be part of the IEEE 802.11be Extremely High of multi-link communications, which represents a paradigm Throughput (EHT) amendment. Through MLO, access points shift towards concurrent transmissions. Although under the and stations will be provided with the capabilities to transmit and receive data from the same traffic flow over multiple radio multi-link label we find the multi-AP coordination and the interfaces. However, the question on how traffic flows should be multi-band/multi-channel operation features, this article is distributed over the different interfaces to maximize the WLAN focused on the analysis of the latter one. performance is still unresolved. To that end, we evaluate in this Upon its current version, the IEEE 802.11 standard already article different traffic allocation policies, under a wide variety defines two MAC architectures for supporting the multi- of scenarios and traffic loads, in order to shed some light on that question. The obtained results confirm that congestion-aware band/multi-channel operation. However, both designs present policies outperform static ones. However, and more importantly, a common limitation: MAC service data units (MSDUs) the results also reveal that traffic flows become highly vulnerable belonging to the same traffic flow can not be transmitted to the activity of neighboring networks when they are distributed across different bands [4]. -

MR52 Datasheet
MR52 Datasheet MR52 Dual-band 802.11ac Wave 2 access point with separate radios dedicated to security, RF management, and Bluetooth High performance 802.11ac MR52 and Meraki cloud Wave 2 wireless management: A powerful The Cisco Meraki MR52 is a cloud-managed 4x4:4 802.11ac combo Wave 2 access point with MU-MIMO support. Designed for next- generation deployments in offices, schools, hospitals, shops, Management of the MR52 is through the Meraki cloud, with an and hotels, the MR52 offers high performance, enterprise-grade intuitive browser-based interface that enables rapid deployment security, and simple management. without time-consuming training or costly certifications. Since the MR52 is self-configuring and managed over the web, it can The MR52 provides a maximum of 2.5 Gbps* aggregate frame be deployed at a remote location in a matter of minutes, even rate with concurrent 2.4 GHz and 5 GHz radios. A dedicated without on-site IT staff. third radio provides real-time WIDS/WIPS with automated RF optimization, and a fourth integrated radio delivers Bluetooth 24x7 monitoring via the Meraki cloud delivers real-time alerts Low Energy (BLE) scanning and Beaconing. if the network encounters problems. Remote diagnostic tools enable immediate troubleshooting over the web so that With the combination of cloud management, high performance distributed networks can be managed with a minimum of hassle. hardware, multiple radios, and advanced software features, the MR52 makes an outstanding platform for the most demanding The MR52’s firmware is automatically kept up to date via the of uses - including high-density deployments and bandwidth or cloud. -

Introduction to Spanning Tree Protocol by George Thomas, Contemporary Controls
Volume6•Issue5 SEPTEMBER–OCTOBER 2005 © 2005 Contemporary Control Systems, Inc. Introduction to Spanning Tree Protocol By George Thomas, Contemporary Controls Introduction powered and its memory cleared (Bridge 2 will be added later). In an industrial automation application that relies heavily Station 1 sends a message to on the health of the Ethernet network that attaches all the station 11 followed by Station 2 controllers and computers together, a concern exists about sending a message to Station 11. what would happen if the network fails? Since cable failure is These messages will traverse the the most likely mishap, cable redundancy is suggested by bridge from one LAN to the configuring the network in either a ring or by carrying parallel other. This process is called branches. If one of the segments is lost, then communication “relaying” or “forwarding.” The will continue down a parallel path or around the unbroken database in the bridge will note portion of the ring. The problem with these approaches is the source addresses of Stations that Ethernet supports neither of these topologies without 1 and 2 as arriving on Port A. This special equipment. However, this issue is addressed in an process is called “learning.” When IEEE standard numbered 802.1D that covers bridges, and in Station 11 responds to either this standard the concept of the Spanning Tree Protocol Station 1 or 2, the database will (STP) is introduced. note that Station 11 is on Port B. IEEE 802.1D If Station 1 sends a message to Figure 1. The addition of Station 2, the bridge will do ANSI/IEEE Std 802.1D, 1998 edition addresses the Bridge 2 creates a loop. -
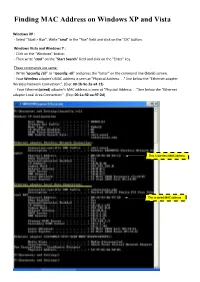
Finding MAC Address on Windows XP and Vista
Finding MAC Address on Windows XP and Vista Windows XP : - Select "Start > Run". Write "cmd" in the "Run" field and click on the "OK" button. Windows Vista and Windows 7 : - Click on the "Windows" button. - Then write "cmd" on the "Start Search" field and click on the "Enter" key. These commands are same: - Write "ipconfig /all" or "ipconfig -all" and press the "Enter" on the command line (blank) screen. - Your Wireless adapter’s MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Wireless Network Connection:”. (Exp: 00-1b-9e-2a-a4-13) - Your Ethernet(wired) adapter's MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Local Area Connection:”. (Exp: 00-1a-92-aa-97-2d) This is wireless MAC address This is wired MAC address Finding MAC Address on Linux root@test:/ > ifconfig –a eth0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:85 <----- This is wired MAC address inet addr:10.92.52.10 Bcast:10.92.255.255 Mask:255.255.248.0 inet6 addr: fe80::1:2ae:9a85/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a85/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 wlan0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:95 <----- This is wireless MAC address inet addr:10.80.2.94 Bcast:10.80.255.255 Mask:255.255.252.0 inet6 addr: fe80::1:2ae:9a95/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a95/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 Finding MAC Address on Macintosh OS 10.1 - 10.4 Please note: Wired and Wireless MAC addresses are different. -

Power Over Ethernet
How To | Power over Ethernet Introduction Power over Ethernet (PoE) is a technology allowing devices such as IP telephones to receive power over existing LAN cabling. This technical note is in four parts as follows: • PoE Technology • How PoE works • Allied Telesyn PoE implementation • Command Reference What information will you find in this document? The first two parts of this document describe the PoE technology, and the installation and management advantages that PoE can provide. This is followed by an overview of how PoE works, Power Device(PD) discovery, PD classification, and the delivery of power to PD data cables. The third part of this document focuses on Allied Telesyn’s implementation of PoE on the AT-8624PoE switch. The document concludes with a list of configuration and monitoring commands. Which product and software version does this information apply to? The information provided here applies to: • Products: AT8624PoE switch • Software version: 2.6.5 C613-16048-00 REV C www.alliedtelesyn.com PoE Technology Power over Ethernet is a mechanism for supplying power to network devices over the same cabling used to carry network traffic. PoE allows devices that require power, called Powered Devices (PDs), such as IP telephones, wireless LAN Access Points, and network cameras to receive power in addition to data, over existing infrastructure without needing to upgrade it. This feature can simplify network installation and maintenance by using the switch as a central power source for other network devices. A device that can source power such as an Ethernet switch is termed Power Sourcing Equipment (PSE). Power Sourcing Equipment can provide power, along with data, over existing LAN cabling to Powered Devices. -

Modular Embedded PC's with Intel® Atom™ E3800 Top Side The
QSys Modular Embedded PC’s with Intel® Atom™ E3800 The Qseven mainboard (carrier board) MB-Q7-2 in combination with The highlights: a standard Qseven 2.0 (x86) module forms an ultra compact hardware kit. By use of the new Intel® Atom™ family E3800 (BayTrail“) a very Based on Intel® Atom™ E3800 („BayTrail“) economical and extremely powerful embedded PC is available. The Optimized for ultra low power integrated Intel® HD Graphics Engine (Generation 7) raises the bar also Extended temperature in graphic intensive low power applications. High speed interfaces like Gigabit Ethernet, USB 3.0 and eSATAp The compact design with only 10 cm x 10 cm x 2,3 cm and the huge DisplayPort and LVDS amount of interfaces and functionalities allows the user to create high Extendable with 2x Mini PCIe incl. SIM card socket performant but passive cooled solutions like BoxPCs, PanelPCs and Onboard eMMC and mSATA socket custom specific devices in a very fast and convenient way. Integrated security features Audio with integrated amplifier Another key aspect is security which is supported by TPM 1.2/2.0, Ultra compact design (10cm x 10 cm x 2,3 cm) a Sentinel HL security controller and an integrated secure EEPROM Longevity support which allows the user to realize a very secure embedded device. Also usable as embedded alternative for Intel® NUC Standard boards (eNUC) Top side Bottom side Technical data hardware kit Performance/configurations Microprocessor (CPU module) With extended temperature support: CPU: Intel® Atom™ E3800 („BayTrail-I“) 5 variants from 1,46 GHz Single Core up to E3815: 1x 1,46 GHz, 512 KB L2-Cache, HD Gfx 400/400 MHz, 1,91 GHz Quad Core 5 W TDP, 2 GB Single-Ch. -

USB to Ethernet Adapter | QUICK SETUP GUIDE RF-PCC132
USB to Ethernet Adapter | QUICK SETUP GUIDE RF-PCC132 Thank you for purchasing this high quality Rocketfish USB to Ethernet Adapter. Use this adapter to instantly connect to a 10/100 Mbps network from the USB port on your desktop or laptop computer. 3 When the installation is complete, click Finish to restart your Package contents computer and finish the installation. • USB to Ethernet Adapter • Driver CD • Quick Setup Guide Setting up the adapter Note: The driver software must be installed before you connect the adapter. The adapter does not need to be connected for the software to install. To install on a Windows PC: 1 Insert the driver CD into the optical drive on your computer. The software should run automatically. The initial installation screen opens. Note: If the software does not run automatically, locate and double-click Run.exe on the driver CD. 4 Connect the USB connector on the adapter to an open USB port on 2 Click on your operating system, then follow on-screen instructions. your desktop or laptop computer. 5 Connect a network cable to the Ethernet port on the adapter. To install on a Mac: 1 Insert the driver CD into the optical drive of your computer. On the driver CD, locate and click AX88772.dmg. Click the DISK IMAGE icon. The driver setup driver setup dialog box opens. Note: If the computer has Windows 8, you do not need to install the driver from the disc. The drivers are installed automatically. 2 When the installer screen opens, click 4 When installation is complete, click Restart to FCC Information Continue to start the installation, then restart the computer and finish the installation. -

Ds-Ruckus-R710.Pdf
R710 Indoor 802.11ac Wave 2 4x4:4 Wi-Fi Access Point DATA SHEET Bandwidth-hungry voice and video applications. Internet of Things (IoT) connections. An explosion of new devices and content. With these kinds of demands, organizations in every industry need more from their Wi-Fi. But with hundreds of devices and nonstop wireless noise and interference, busy indoor spaces can make challenging wireless environments. The Ruckus R710 is a premier indoor access point, delivering industry-leading performance and reliability in the most demanding high-density locations. With BENEFITS data rates up to 800Mbps (2.4GHz) and 1.733Gbps (5GHz), the R710 delivers the highest available throughput for Wi-Fi clients. STUNNING WI-FI PERFORMANCE Provide a great user experience no matter The R710 delivers reliable, high-performance connectivity in schools, universities, how challenging the environment with public venues, hotels, conference centers, and other busy indoor spaces. The BeamFlex+™ adaptive antenna technology perfect choice for data-intensive streaming multimedia applications, it delivers and a library of 4K+ directional antenna picture-perfect HD-quality IP video, while supporting voice and data applications patterns. with stringent quality-of-service requirements. SERVE MORE DEVICES Connect more devices simultaneously with The R710 802.11ac Wave 2 Wi-Fi AP incorporates patented technologies found only four MU-MIMO spatial streams and in the Ruckus Wi-Fi portfolio. concurrent dual-band 2.4/5GHz radios while enhancing non-Wave 2 device • Extended coverage with patented BeamFlex+ utilizing multi-directional performance. antenna patterns. AUTOMATE OPTIMAL THROUGHPUT • Improve throughput with ChannelFly, which dynamically finds less congested ChannelFly™ dynamic channel technology Wi-Fi channels to use. -

A 24Port 10G Ethernet Switch
A 24-port 10G Ethernet Switch (with asynchronous circuitry) Andrew Lines 1 Agenda Product Information Technical Details Photos 2 Tahoe: First FocalPoint Family Member The lowest-latency feature-rich 10GE switch chip Tahoe · 10G Ethernet switch - 24 Ports · Line rate performance - 240Gb/s bandwidth SPI CPU JTAG LED - 360M frames/s - Full-speed multicast Frame Processor · Fully-integrated single chip (Scheduler) - 1MB frame memory - 16K MAC addresses ® ® · Lowest latency Ethernet ) 4) s s - -4 X X - 200ns with copper cables u u (C (C x x I I ™ U U e e · Rich Feature Set RapidArray A X XA N N (packet storage) - Extensive layer 2 features · Flexible SERDES interfaces - 10G XAUI (CX-4) - 1G SGMII Asynchronous Blocks 3 Tahoe Hardware Architecture Modular architecture, centralized control SPI CPU JTAG LED Interface Interface Interface Interface Management Frame Control LCI Lookup Handler Stats RX Port Logic Scheduler TX Port Logic P M M P Ser Ser C A A C Des Des S C C S Switch Element Data Path ® ® s s ™ u u x RapidArray x e (1MB Shared Memory) e N N RX Port Logic TX Port Logic P M M P Ser Ser C A A C Des Des S C C S 4 Tahoe Chip Plot Fabricated in TSMC 0.13um Ethernet Port Logic - SerDes RapidArray Memory - PCS - 1MB shared - MAC Nexus Crossbars - 1.5Tb/s total - 3ns latency Scheduler - Highly optimized - High event rate MAC Table - 16K addresses Management Frame Control - CPU interface - Frame handler - JTAG - Lookup - EEPROM interface - Statistics - LEDs 5 Bridge Features Robust set of layer-2 features · General Bridge Features · Security - 16K MAC entries - 802.1x; MAC Address Security - STP: multiple, rapid, standard · Monitoring - Learning and Ageing - Rich monitoring terms - Multicast GMRP and IGMPv3 · logical combination of terms · VLAN Tag (IEEE 802.1Q-2003) · Src Port, Dst Port, VLAN, - Add / Remove tags Traffic Type, Priority, Src - Per port association default MA, Dst MA, etc.