Zimbra Collaboration Administrator Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
CYRUS: BUILD YOUR TUTORIAL OWN EMAIL SERVER Don’T Trust Google? We’Ll Help You Navigate the Sea of JOHN LANE Acronyms to Build Your Own Mailserver
TUTORIAL MAILSERVER CYRUS: BUILD YOUR TUTORIAL OWN EMAIL SERVER Don’t trust Google? We’ll help you navigate the sea of JOHN LANE acronyms to build your own mailserver. ou can’t beat the convenience and ease of use access their mail by connecting to the server using WHY DO THIS? offered by Gmail. But unfortunately, all that any IMAP-capable email client application. • Take control of your Yfree storage comes at a price: your privacy. You will need a, preferably new, server for this email provision. Spam, intrusive adverts and snooping from unnamed project and you’ll need root access to it. Our examples • Stop outside agencies government agencies are the inevitable downside of use Arch Linux, and we created a new virtual server. from scanning the using someone else’s service for free. So why not Begin by installing Cyrus (build the Arch User content of your emails. build your own email server including anti-spam, Repository package first – see the boxout below-right): • Get webmail without advertising. anti-virus and webmail? $ pacman -U ~build/cyrus-imapd/cyrus-imapd-2.4.17-5-x86_64. You can use your own server to retrieve messages pkg.tar.xz from other mailservers, such as those provided by The default configuration writes data to /var/imap internet service providers, or other services like those and user mailboxes to /var/spool/imap. You can from Google and Yahoo. But you don’t need to rely on change this if you prefer another location; we’ll others if you have your own server. If you have a configure our server to use /srv/mail/cyrus to domain name that you control, and if you can give your illustrate this. -

Show Me the Money: Characterizing Spam-Advertised Revenue
Show Me the Money: Characterizing Spam-advertised Revenue Chris Kanich∗ Nicholas Weavery Damon McCoy∗ Tristan Halvorson∗ Christian Kreibichy Kirill Levchenko∗ Vern Paxsonyz Geoffrey M. Voelker∗ Stefan Savage∗ ∗ y Department of Computer Science and Engineering International Computer Science Institute University of California, San Diego Berkeley, CA z Computer Science Division University of California, Berkeley Abstract money at all [6]. This situation has the potential to distort Modern spam is ultimately driven by product sales: policy and investment decisions that are otherwise driven goods purchased by customers online. However, while by intuition rather than evidence. this model is easy to state in the abstract, our under- In this paper we make two contributions to improving standing of the concrete business environment—how this state of affairs using measurement-based methods to many orders, of what kind, from which customers, for estimate: how much—is poor at best. This situation is unsurpris- ing since such sellers typically operate under question- • Order volume. We describe a general technique— able legal footing, with “ground truth” data rarely avail- purchase pair—for estimating the number of orders able to the public. However, absent quantifiable empiri- received (and hence revenue) via on-line store order cal data, “guesstimates” operate unchecked and can dis- numbering. We use this approach to establish rough, tort both policy making and our choice of appropri- but well-founded, monthly order volume estimates ate interventions. In this paper, we describe two infer- for many of the leading “affiliate programs” selling ence techniques for peering inside the business opera- counterfeit pharmaceuticals and software. tions of spam-advertised enterprises: purchase pair and • Purchasing behavior. -

Respecting the Block Interface – Computational Storage Using Virtual Objects
Respecting the block interface – computational storage using virtual objects Ian F. Adams, John Keys, Michael P. Mesnier Intel Labs Abstract immediately obvious, and trade-offs need to be made. Unfor- tunately, this often means that the parallel bandwidth of all Computational storage has remained an elusive goal. Though drives within a storage server will not be available. The same minimizing data movement by placing computation close to problem exists within a single SSD, as the internal NAND storage has quantifiable benefits, many of the previous at- flash bandwidth often exceeds that of the storage controller. tempts failed to take root in industry. They either require a Enter computational storage, an oft-attempted approach to departure from the widespread block protocol to one that address the data movement problem. By keeping computa- is more computationally-friendly (e.g., file, object, or key- tion physically close to its data, we can avoid costly I/O. Var- value), or they introduce significant complexity (state) on top ious designs have been pursued, but the benefits have never of the block protocol. been enough to justify a new storage protocol. In looking We participated in many of these attempts and have since back at the decades of computational storage research, there concluded that neither a departure from nor a significant ad- is a common requirement that the block protocol be replaced dition to the block protocol is needed. Here we introduce a (or extended) with files, objects, or key-value pairs – all of block-compatible design based on virtual objects. Like a real which provide a convenient handle for performing computa- object (e.g., a file), a virtual object contains the metadata that tion. -

Zambia and Spam
ZAMNET COMMUNICATION SYSTEMS LTD (ZAMBIA) Spam – The Zambian Experience Submission to ITU WSIS Thematic meeting on countering Spam By: Annabel S Kangombe – Maseko June 2004 Table of Contents 1.0 Introduction 1 1.1 What is spam? 1 1.2 The nature of Spam 1 1.3 Statistics 2 2.0 Technical view 4 2.1 Main Sources of Spam 4 2.1.1 Harvesting 4 2.1.2 Dictionary Attacks 4 2.1.3 Open Relays 4 2.1.4 Email databases 4 2.1.5 Inadequacies in the SMTP protocol 4 2.2 Effects of Spam 5 2.3 The fight against spam 5 2.3.1 Blacklists 6 2.3.2 White lists 6 2.3.3 Dial‐up Lists (DUL) 6 2.3.4 Spam filtering programs 6 2.4 Challenges of fighting spam 7 3.0 Legal Framework 9 3.1 Laws against spam in Zambia 9 3.2 International Regulations or Laws 9 3.2.1 US State Laws 9 3.2.2 The USA’s CAN‐SPAM Act 10 4.0 The Way forward 11 4.1 A global effort 11 4.2 Collaboration between ISPs 11 4.3 Strengthening Anti‐spam regulation 11 4.4 User education 11 4.5 Source authentication 12 4.6 Rewriting the Internet Mail Exchange protocol 12 1.0 Introduction I get to the office in the morning, walk to my desk and switch on the computer. One of the first things I do after checking the status of the network devices is to check my email. -

Cyrus Mail Server 2 Table of Contents
Univention Corporate Server Cyrus mail server 2 Table of Contents 1. Introduction ........................................................................................................................ 4 2. Installation ......................................................................................................................... 5 3. Management of the mail server data ....................................................................................... 6 3.1. Management of mail domains ..................................................................................... 6 3.2. Assignment of e-mail addresses to users ........................................................................ 6 3.3. Management of mailing lists ....................................................................................... 7 3.4. Management of mail groups ........................................................................................ 7 3.5. Management of shared IMAP folders ........................................................................... 8 3.6. Mail quota ............................................................................................................... 9 4. Spam detection and filtering ................................................................................................ 10 5. Identification of viruses and malware .................................................................................... 11 6. Identification of Spam sources with DNS-based Blackhole Lists (DNSBL) ................................... -

Email Phishing for IT Providers How Phishing Emails Have Changed and How to Protect Your IT Clients
Email Phishing for IT Providers How phishing emails have changed and how to protect your IT clients 1 © 2016 Calyptix Security Corporation. All rights reserved. I [email protected] I (800) 650 – 8930 (800) 650-8930 I [email protected] Contents Introduction ............................................................................................ 2 Phishing overview .................................................................................. 3 Trends in phishing emails ...................................................................... 6 Email phishing tactics .......................................................................... 11 Steps for MSP & VARS .......................................................................... 24 Advice for your clients .......................................................................... 29 Sources .................................................................................................. 35 1 © 2016 Calyptix Security Corporation. All rights reserved. I [email protected] I (800) 650 – 8930 Introduction There are only so many ways to break into a bank. You can march through the door. You can climb through a window. You can tunnel through the floor. There is the service entrance, the employee entrance, and access on the roof. Criminals who want to rob a bank will probably use an open route – such as a side door. It’s easier than breaking down a wall. Criminals who want to break into your network face a similar challenge. They need to enter. They can look for a weakness in your -

CUB Guide to Fighting Robocalls
CitizensUtilityBoard.org 1-800-669-5556 Guide to Fighting Robocalls February 2021 The latest news on the robocall fi ght Robocalls are prerecorded messages from computer-generat- ed dialers, and Illinois is one of the nation’s hardest hit states. In early 2021, for example, the state received more than 153 million robocalls (about 57 per second) in the span of just one month. That ranked Illinois eighth in the country for these calls, according to the robocall-blocking fi rm YouMail. While there are helpful robocalls (alerting you to school closings or when a prescription is ready), YouMail estimates about 42 percent of the calls in Illinois were scams and another 22 percent were simply marketing pitches. Unwanted robocalls are annoying, and costly. The Federal Com- munications Commission (FCC) put the price tag at $3 billion a year just from lost time, not even counting any fraud. TechRe- One in 10 Americans public put the total annual loss for consumers at $9.5 billion. are scammed each year, While policymakers are fi nally starting to act against illegal robo- calls, don’t wait for federal law to catch up. Use the simple tips in resulting in an annual loss of this guide to protect yourself from unwanted calls. The law The Telephone Robocall Abuse Criminal Enforcement and $9.5 billion Deterrence (TRACED) Act became federal law in 2019. The act increases penalties and requires phone companies to validate Source: TechRepublic, calls before they reach you. This is to combat “spoofi ng,” October 2019 when a robocaller uses your area code and/or prefi x to ap- pear as if someone locally—maybe a friend or neighbor—is Note: In December 2020, the FCC ordered that organiza- trying to reach you. -

Toward an Automated Vulnerability Comparison of Open Source IMAP Servers Chaos Golubitsky – Carnegie Mellon University
Toward an Automated Vulnerability Comparison of Open Source IMAP Servers Chaos Golubitsky – Carnegie Mellon University ABSTRACT The attack surface concept provides a means of discussing the susceptibility of software to as-yet-unknown attacks. A system’s attack surface encompasses the methods the system makes available to an attacker, and the system resources which can be used to further an attack. A measurement of the size of the attack surface could be used to compare the security of multiple systems which perform the same function. The Internet Message Access Protocol (IMAP) has been in existence for over a decade. Relative to HTTP or SMTP, IMAP is a niche protocol, but IMAP servers are widely deployed nonetheless. There are three popular open source UNIX IMAP servers – UW-IMAP, Cyrus, and Courier-IMAP – and there has not been a formal security comparison between them. In this paper, I use attack surfaces to compare the relative security risks posed by these three products. I undertake this evaluation in service of two complementary goals: to provide an honest examination of the security postures and risks of the three servers, and to advance the study of attack surfaces by performing an automated attack surface measurement using a methodology based on counting entry and exit points in the code. Introduction Contributions and Roadmap System administrators frequently confront the The paper makes two major contributions. First, problem of selecting a software package to perform a I undertake an in-depth discussion of the relative secu- desired function. Many considerations affect this deci- rity postures of the three major open source IMAP sion, including functionality, ease of installation, soft- servers in use today. -

Comodo Antispam Gateway Software Version 1.5
Comodo Antispam Gateway Software Version 1.5 Administrator Guide Guide Version 1.5.082412 Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Comodo Antispam Gateway - Administrator Guide Table of Contents 1 Introduction to Comodo Antispam Gateway........................................................................................................................... 4 1.1 Release Notes............................................................................................................................................................. 5 1.2 Purchasing License .................................................................................................................................................... 6 1.3 Adding more Users, Domains or Time to your Account .................................................................................................6 1.4 License Information................................................................................................................................................... 10 2 Getting Started................................................................................................................................................................... 13 2.1 Incoming Filtering Configuration ................................................................................................................................ 13 2.1.1 Configuring Your Mail Server.................................................................................................................................. -

IDC Marketscape IDC Marketscape: Worldwide Object-Based Storage 2019 Vendor Assessment
IDC MarketScape IDC MarketScape: Worldwide Object-Based Storage 2019 Vendor Assessment Amita Potnis THIS IDC MARKETSCAPE EXCERPT FEATURES SCALITY IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide Object-Based Storage Vendor Assessment Source: IDC, 2019 December 2019, IDC #US45354219e Please see the Appendix for detailed methodology, market definition, and scoring criteria. IN THIS EXCERPT The content for this excerpt was taken directly from IDC MarketScape: Worldwide Object-Based Storage 2019 Vendor Assessment (Doc # US45354219). All or parts of the following sections are included in this excerpt: IDC Opinion, IDC MarketScape Vendor Inclusion Criteria, Essential Guidance, Vendor Summary Profile, Appendix and Learn More. Also included is Figure 1. IDC OPINION The storage market has come a long way in terms of understanding object-based storage (OBS) technology and actively adopting it. It is a common practice for OBS to be adopted for secondary and cold storage needs at scale. Over the recent years, OBS has proven its ability to scale to tens and hundreds of petabytes and is now maturing to support newer workloads such as unstructured data analytics, IoT, AI/ML/DL, and so forth. As the price of flash declines and the data sets continue to grow, the need for analyzing the data is on the rise. Moving data sets from an object store to a high- performance tier for analysis is a thing of the past. Many vendors are enhancing their object offerings to include a flash tier or are bringing all-flash array object storage offerings to the market today. In this IDC MarketScape, IDC assesses the present commercial OBS supplier (suppliers that deliver software-defined OBS solutions as software or appliances much like other storage platforms) landscape. -
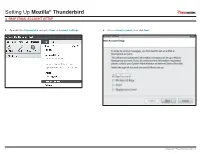
Setting up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP
Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP 1. Open Mozilla Thunderbird and go to Tools -> Account Settings. 2. Choose Email account; then click Next. 1 Copyright © EmailHosting.com LLC Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP (cont.) 3. In the Identity window type your name as you want it to appear on outgoing emails. 4. In the Server Information window select the radio button labeled IMAP. • Then, type your email address in the field labeled Email Address. • Enter imap.emailhosting.com in the field labeled Incoming Server. • Click Next to continue. • Enter smtp.emailhosting.com in the field labeled Outgoing Server. • Click Next to continue. John Smith imap.emailhosting.com [email protected] smtp.emailhosting.com Note: If you have already used Thunderbird in the past the Outgoing Server will not be listed. 2 Copyright © EmailHosting.com LLC Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP (cont.) 5. In the User Names window, the fields should already be filled out correctly. 6. Click Next on the Account Name page to accept the default Account Name. • Confirm that both fields match your EmailHosting username. • In the Congratulations window, verify that all information is correct. • Click Next to continue. • Then click Finish. [email protected] [email protected] [email protected] [email protected] 7. You will be prompted for your password. If you’d like to save your password, make sure Use Password Manager to remember this password is checked before clicking on OK to continue. Note: The field Outgoing Server is only visible during the setup of Mozilla Thunderbird’s first email account. -

Set up Mail Server Documentation 1.0
Set Up Mail Server Documentation 1.0 Nosy 2014 01 23 Contents 1 1 1.1......................................................1 1.2......................................................2 2 11 3 13 3.1...................................................... 13 3.2...................................................... 13 3.3...................................................... 13 4 15 5 17 5.1...................................................... 17 5.2...................................................... 17 5.3...................................................... 17 5.4...................................................... 18 6 19 6.1...................................................... 19 6.2...................................................... 28 6.3...................................................... 32 6.4 Webmail................................................. 36 6.5...................................................... 37 6.6...................................................... 38 7 39 7.1...................................................... 39 7.2 SQL.................................................... 41 8 43 8.1...................................................... 43 8.2 strategy.................................................. 43 8.3...................................................... 44 8.4...................................................... 45 8.5...................................................... 45 8.6 Telnet................................................... 46 8.7 Can postfix receive?..........................................