Hyper V Download Windows 10
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Effective Virtual CPU Configuration with QEMU and Libvirt
Effective Virtual CPU Configuration with QEMU and libvirt Kashyap Chamarthy <[email protected]> Open Source Summit Edinburgh, 2018 1 / 38 Timeline of recent CPU flaws, 2018 (a) Jan 03 • Spectre v1: Bounds Check Bypass Jan 03 • Spectre v2: Branch Target Injection Jan 03 • Meltdown: Rogue Data Cache Load May 21 • Spectre-NG: Speculative Store Bypass Jun 21 • TLBleed: Side-channel attack over shared TLBs 2 / 38 Timeline of recent CPU flaws, 2018 (b) Jun 29 • NetSpectre: Side-channel attack over local network Jul 10 • Spectre-NG: Bounds Check Bypass Store Aug 14 • L1TF: "L1 Terminal Fault" ... • ? 3 / 38 Related talks in the ‘References’ section Out of scope: Internals of various side-channel attacks How to exploit Meltdown & Spectre variants Details of performance implications What this talk is not about 4 / 38 Related talks in the ‘References’ section What this talk is not about Out of scope: Internals of various side-channel attacks How to exploit Meltdown & Spectre variants Details of performance implications 4 / 38 What this talk is not about Out of scope: Internals of various side-channel attacks How to exploit Meltdown & Spectre variants Details of performance implications Related talks in the ‘References’ section 4 / 38 OpenStack, et al. libguestfs Virt Driver (guestfish) libvirtd QMP QMP QEMU QEMU VM1 VM2 Custom Disk1 Disk2 Appliance ioctl() KVM-based virtualization components Linux with KVM 5 / 38 OpenStack, et al. libguestfs Virt Driver (guestfish) libvirtd QMP QMP Custom Appliance KVM-based virtualization components QEMU QEMU VM1 VM2 Disk1 Disk2 ioctl() Linux with KVM 5 / 38 OpenStack, et al. libguestfs Virt Driver (guestfish) Custom Appliance KVM-based virtualization components libvirtd QMP QMP QEMU QEMU VM1 VM2 Disk1 Disk2 ioctl() Linux with KVM 5 / 38 libguestfs (guestfish) Custom Appliance KVM-based virtualization components OpenStack, et al. -

The NTFS File System
The NTFS File System OVERVIEW: This lab is part of a series of lab exercises intended to support courseware for Forensics training. The development of this document is funded by the Department of Labor (DOL) Trade Adjustment Assistance Community College and Career Training (TAACCCT) Grant No. TC-22525-11-60-A-48. In this lab, students will enumerate hosts on the network using various tools. This lab includes the following tasks: 1 – Examining the NTFS File System 2 – Using a HEX Editor to explore an NTFS Partition 3 – Verifying and viewing the image details 4 – Analyzing an NTFS Partition With Autopsy Key TermDescription The acronym NTFS stands for New Technology File System. The NTFS File System was originally introduced with the Windows NT. NTFS is a journaling file system which means it keeps a log of changes being written to the disk. If a computer is shutdown improperly, it will have a better NTFS chance of recovery if it has a journaling file system. Files and folder access can be restricted with the security feature of NTFS. Starting with Windows 2000, Microsoft included the Encrypted File System, or EFS, as an NTFS feature. EFS allows users to encrypt files to protect against unauthorized access. A Feature of the NTFS File system that allows you to encrypt files and folders. The feature EFS became available on the NTFS File system starting with Windows 2000, and is still available today on Windows 10 and Server 2016. An Alternate Data Stream, or ADS, is a feature of the NTFS file system that allowed compatibility ADS with older versions of the Mac OS. -

Vmware Fusion 12 Vmware Fusion Pro 12 Using Vmware Fusion
Using VMware Fusion 8 SEP 2020 VMware Fusion 12 VMware Fusion Pro 12 Using VMware Fusion You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com © Copyright 2020 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 2 Contents Using VMware Fusion 9 1 Getting Started with Fusion 10 About VMware Fusion 10 About VMware Fusion Pro 11 System Requirements for Fusion 11 Install Fusion 12 Start Fusion 13 How-To Videos 13 Take Advantage of Fusion Online Resources 13 2 Understanding Fusion 15 Virtual Machines and What Fusion Can Do 15 What Is a Virtual Machine? 15 Fusion Capabilities 16 Supported Guest Operating Systems 16 Virtual Hardware Specifications 16 Navigating and Taking Action by Using the Fusion Interface 21 VMware Fusion Toolbar 21 Use the Fusion Toolbar to Access the Virtual-Machine Path 21 Default File Location of a Virtual Machine 22 Change the File Location of a Virtual Machine 22 Perform Actions on Your Virtual Machines from the Virtual Machine Library Window 23 Using the Home Pane to Create a Virtual Machine or Obtain One from Another Source 24 Using the Fusion Applications Menus 25 Using Different Views in the Fusion Interface 29 Resize the Virtual Machine Display to Fit 35 Using Multiple Displays 35 3 Configuring Fusion 37 Setting Fusion Preferences 37 Set General Preferences 37 Select a Keyboard and Mouse Profile 38 Set Key Mappings on the Keyboard and Mouse Preferences Pane 39 Set Mouse Shortcuts on the Keyboard and Mouse Preference Pane 40 Enable or Disable Mac Host Shortcuts on the Keyboard and Mouse Preference Pane 40 Enable Fusion Shortcuts on the Keyboard and Mouse Preference Pane 41 Set Fusion Display Resolution Preferences 41 VMware, Inc. -

Understanding Full Virtualization, Paravirtualization, and Hardware Assist
VMware Understanding Full Virtualization, Paravirtualization, and Hardware Assist Contents Introduction .................................................................................................................1 Overview of x86 Virtualization..................................................................................2 CPU Virtualization .......................................................................................................3 The Challenges of x86 Hardware Virtualization ...........................................................................................................3 Technique 1 - Full Virtualization using Binary Translation......................................................................................4 Technique 2 - OS Assisted Virtualization or Paravirtualization.............................................................................5 Technique 3 - Hardware Assisted Virtualization ..........................................................................................................6 Memory Virtualization................................................................................................6 Device and I/O Virtualization.....................................................................................7 Summarizing the Current State of x86 Virtualization Techniques......................8 Full Virtualization with Binary Translation is the Most Established Technology Today..........................8 Hardware Assist is the Future of Virtualization, but the Real Gains Have -

Introduction to Virtualization
z Systems Introduction to Virtualization SHARE Orlando Linux and VM Program Romney White, IBM [email protected] z Systems Architecture and Technology © 2015 IBM Corporation Agenda ° Introduction to Virtualization – Concept – Server Virtualization Approaches – Hypervisor Implementation Methods – Why Virtualization Matters ° Virtualization on z Systems – Logical Partitions – Virtual Machines 2 z Systems Virtualization Technology © 2015 IBM Corporation Virtualization Concept Virtual Resources Proxies for real resources: same interfaces/functions, different attributes May be part of a physical resource or multiple physical resources Virtualization Creates virtual resources and "maps" them to real resources Primarily accomplished with software or firmware Resources Components with architecturally-defined interfaces/functions May be centralized or distributed - usually physical Examples: memory, disk drives, networks, servers Separates presentation of resources to users from actual resources Aggregates pools of resources for allocation to users as virtual resources 3 z Systems Virtualization Technology © 2015 IBM Corporation Server Virtualization Approaches Hardware Partitioning Bare-metal Hypervisor Hosted Hypervisor Apps ... Apps Apps ... Apps Apps ... Apps OS OS OS OS OS OS Adjustable partitions Hypervisor Hypervisor Partition Controller Host OS SMP Server SMP Server SMP Server Server is subdivided into fractions Hypervisor provides fine-grained Hypervisor uses OS services to each of which can run an OS timesharing of all resources -

KVM Based Virtualization and Remote Management Srinath Reddy Pasunuru St
St. Cloud State University theRepository at St. Cloud State Culminating Projects in Information Assurance Department of Information Systems 5-2018 KVM Based Virtualization and Remote Management Srinath Reddy Pasunuru St. Cloud State University, [email protected] Follow this and additional works at: https://repository.stcloudstate.edu/msia_etds Recommended Citation Pasunuru, Srinath Reddy, "KVM Based Virtualization and Remote Management" (2018). Culminating Projects in Information Assurance. 53. https://repository.stcloudstate.edu/msia_etds/53 This Starred Paper is brought to you for free and open access by the Department of Information Systems at theRepository at St. Cloud State. It has been accepted for inclusion in Culminating Projects in Information Assurance by an authorized administrator of theRepository at St. Cloud State. For more information, please contact [email protected]. 1 KVM Based Virtualization and Remote Management by Srinath Reddy Pasunuru A Starred Paper Submitted to the Graduate Faculty of St. Cloud State University in Partial Fulfillment of the Requirements for the Degree Master of Science in Information Assurance May, 2018 Starred Paper Committee Susantha Herath, Chairperson Ezzat Kirmani Sneh Kalia 2 Abstract In the recent past, cloud computing is the most significant shifts and Kernel Virtual Machine (KVM) is the most commonly deployed hypervisor which are used in the IaaS layer of the cloud computing systems. The Hypervisor is the one which provides the complete virtualization environment which will intend to virtualize as much as hardware and systems which will include the CPUs, Memory, network interfaces and so on. Because of the virtualization technologies such as the KVM and others such as ESXi, there has been a significant decrease in the usage if the resources and decrease in the costs involved. -
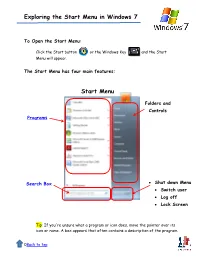
Exploring the Start Menu in Windows 7
Exploring the Start Menu in Windows 7 To Open the Start Menu: Click the Start button or the Windows Key and the Start Menu will appear. The Start Menu has four main features: Start Menu Folders and Controls Programs Shut down Menu Search Box Switch user Log off Lock Screen Tip: If you're unsure what a program or icon does, move the pointer over its icon or name. A box appears that often contains a description of the program. 0Back to top Exploring the Start Menu in Windows 7 Programs (Left Pane of the Start Menu) The programs list includes recently used programs and “Pinned” programs. Click once on a program icon to open it Jump List: If an entry has a black menu arrow, clicking on it will show a “Jump List” of recently opened and Pinned documents. Documents can be opened directly from this list. Jump List Left Click on “All Programs” to show a list of available programs and folders. Organize and move icons by left clicking, then dragging to the desired location. 0Back to top Exploring the Start Menu in Windows 7 Adding or Removing a Program on the Start Menu or Taskbar: Adding or “Pinning” a program on the Start Menu or Taskbar: 1. Find the program icon in the Start Menu, All Programs or Taskbar 2. Right click on the program icon 3. Select “Pin to Taskbar” and/or “Pin to Start Menu” 4. The icon will now be Pinned (stuck) to the selected area. 5. Icons can also be added to the Taskbar from the Start Menu by clicking on the icon in the Start Menu and dragging it to the Taskbar. -

Hypervisors Vs. Lightweight Virtualization: a Performance Comparison
2015 IEEE International Conference on Cloud Engineering Hypervisors vs. Lightweight Virtualization: a Performance Comparison Roberto Morabito, Jimmy Kjällman, and Miika Komu Ericsson Research, NomadicLab Jorvas, Finland [email protected], [email protected], [email protected] Abstract — Virtualization of operating systems provides a container and alternative solutions. The idea is to quantify the common way to run different services in the cloud. Recently, the level of overhead introduced by these platforms and the lightweight virtualization technologies claim to offer superior existing gap compared to a non-virtualized environment. performance. In this paper, we present a detailed performance The remainder of this paper is structured as follows: in comparison of traditional hypervisor based virtualization and Section II, literature review and a brief description of all the new lightweight solutions. In our measurements, we use several technologies and platforms evaluated is provided. The benchmarks tools in order to understand the strengths, methodology used to realize our performance comparison is weaknesses, and anomalies introduced by these different platforms in terms of processing, storage, memory and network. introduced in Section III. The benchmark results are presented Our results show that containers achieve generally better in Section IV. Finally, some concluding remarks and future performance when compared with traditional virtual machines work are provided in Section V. and other recent solutions. Albeit containers offer clearly more dense deployment of virtual machines, the performance II. BACKGROUND AND RELATED WORK difference with other technologies is in many cases relatively small. In this section, we provide an overview of the different technologies included in the performance comparison. -

Your Performance Task Summary Explanation
Lab Report: 11.2.5 Manage Files Your Performance Your Score: 0 of 3 (0%) Pass Status: Not Passed Elapsed Time: 6 seconds Required Score: 100% Task Summary Actions you were required to perform: In Compress the D:\Graphics folderHide Details Set the Compressed attribute Apply the changes to all folders and files In Hide the D:\Finances folder In Set Read-only on filesHide Details Set read-only on 2017report.xlsx Set read-only on 2018report.xlsx Do not set read-only for the 2019report.xlsx file Explanation In this lab, your task is to complete the following: Compress the D:\Graphics folder and all of its contents. Hide the D:\Finances folder. Make the following files Read-only: D:\Finances\2017report.xlsx D:\Finances\2018report.xlsx Complete this lab as follows: 1. Compress a folder as follows: a. From the taskbar, open File Explorer. b. Maximize the window for easier viewing. c. In the left pane, expand This PC. d. Select Data (D:). e. Right-click Graphics and select Properties. f. On the General tab, select Advanced. g. Select Compress contents to save disk space. h. Click OK. i. Click OK. j. Make sure Apply changes to this folder, subfolders and files is selected. k. Click OK. 2. Hide a folder as follows: a. Right-click Finances and select Properties. b. Select Hidden. c. Click OK. 3. Set files to Read-only as follows: a. Double-click Finances to view its contents. b. Right-click 2017report.xlsx and select Properties. c. Select Read-only. d. Click OK. e. -

Hortonworks Sandbox with Vmware Fusion
Hortonworks Sandbox with VMware Fusion Virtual Machine Overview The Hortonworks Sandbox is delivered as a virtual appliance. The virtual appliance (indicated by an .ovf or .ova extension in the filename) runs in the context of a virtual machine (VM), a piece of software that appears to be an application to the underlying (host) operating system (OS), but that looks like a bare machine, including CPU, storage, network adapters, and so forth, to the operating system and applications that run on it. To use the Hortonworks Sandbox, one of the supported virtual machine applications needs to installed on your host machine: • VirtualBox • VMware Fusion • Hyper-V This document describes importing the Hortonworks Sandbox virtual appliance into VMware Fusion. Prerequisites To use the Hortonworks Sandbox with VMware Fusion the following requirements need to be met: • VMware Fusion installed Version 5 or later (Version 7 recommended) You can download VMware Fusion here: https://my.vmware.com/web/vmware/info/slug/desktop_end_user_computi ng/vmware_fusion/7_0#product_downloads • Host Operating Systems: Host operating system refers to the operating system of your computer. The following link gives list of operating systems supported to run VMware Fusion https://www.vmware.com/support/fusion/faq/requirements • Hardware (The newer the hardware the better): • A 64-bit machine with a multi-core CPU that supports virtualization. Please look into your operating system’s documentation to verify if you are running a 64 bit OS. Mac OS X: https://support.apple.com/en-us/HT3696 Installation instructions – VMware on Mac OS 1 • BIOS that has been enabled for virtualization support. Please contact your specific computer vendor to determine how to enable/verify this feature in your machine’s BIOS. -

Attacker Chatbots for Randomised and Interactive Security Labs, Using Secgen and Ovirt
Hackerbot: Attacker Chatbots for Randomised and Interactive Security Labs, Using SecGen and oVirt Z. Cliffe Schreuders, Thomas Shaw, Aimée Mac Muireadhaigh, Paul Staniforth, Leeds Beckett University Abstract challenges, rewarding correct solutions with flags. We deployed an oVirt infrastructure to host the VMs, and Capture the flag (CTF) has been applied with success in leveraged the SecGen framework [6] to generate lab cybersecurity education, and works particularly well sheets, provision VMs, and provide randomisation when learning offensive techniques. However, between students. defensive security and incident response do not always naturally fit the existing approaches to CTF. We present 2. Related Literature Hackerbot, a unique approach for teaching computer Capture the flag (CTF) is a type of cyber security game security: students interact with a malicious attacker which involves collecting flags by solving security chatbot, who challenges them to complete a variety of challenges. CTF events give professionals, students, security tasks, including defensive and investigatory and enthusiasts an opportunity to test their security challenges. Challenges are randomised using SecGen, skills in competition. CTFs emerged out of the and deployed onto an oVirt infrastructure. DEFCON hacker conference [7] and remain common Evaluation data included system performance, mixed activities at cybersecurity conferences and online [8]. methods questionnaires (including the Instructional Some events target students with the goal of Materials Motivation Survey (IMMS) and the System encouraging interest in the field: for example, PicoCTF Usability Scale (SUS)), and group interviews/focus is an annual high school competition [9], and CSAW groups. Results were encouraging, finding the approach CTF is an annual competition for students in Higher convenient, engaging, fun, and interactive; while Education (HE) [10]. -

Ovirt and Openstack Storage (Present and Future)
oVirt and OpenStack Storage (present and future) Federico Simoncelli Principal Software Engineer, Red Hat January 2014 1 Federico Simoncelli – oVirt and OpenStack Storage (present and future) Agenda ● Introduction ● oVirt and OpenStack Overview ● Present ● oVirt and Glance Integration ● Importing and Exporting Glance Images ● Current Constraints and Limitations ● Future ● Glance Future Integration ● Keystone Authentication in oVirt ● oVirt and Cinder Integration 2 Federico Simoncelli – oVirt and OpenStack Storage (present and future) oVirt Overview ● oVirt is a virtualization management application ● manages hardware nodes, storage and network resources, in order to deploy and monitor virtual machines running in your data center ● Free open source software released under the terms of the Apache License 3 Federico Simoncelli – oVirt and OpenStack Storage (present and future) The oVirt Virtualization Architecture 4 Federico Simoncelli – oVirt and OpenStack Storage (present and future) OpenStack Overview ● Cloud computing project to provide an Infrastructure as a Service (IaaS) ● Controls large pools of compute, storage, and networking resources ● Free open source software released under the terms of the Apache License ● Project is managed by the OpenStack Foundation, a non-profit corporate entity established in September 2012 5 Federico Simoncelli – oVirt and OpenStack Storage (present and future) OpenStack Glance Service ● Provides services for discovering, registering, and retrieving virtual machine images ● RESTful API that allows querying