Lecture 3 Graphs and Modeling
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Practical Parallel Hypergraph Algorithms
Practical Parallel Hypergraph Algorithms Julian Shun [email protected] MIT CSAIL Abstract v While there has been signicant work on parallel graph pro- 0 cessing, there has been very surprisingly little work on high- e0 performance hypergraph processing. This paper presents v0 v1 v1 a collection of ecient parallel algorithms for hypergraph processing, including algorithms for betweenness central- e1 ity, maximal independent set, k-core decomposition, hyper- v2 trees, hyperpaths, connected components, PageRank, and v2 v3 e single-source shortest paths. For these problems, we either 2 provide new parallel algorithms or more ecient implemen- v3 tations than prior work. Furthermore, our algorithms are theoretically-ecient in terms of work and depth. To imple- (a) Hypergraph (b) Bipartite representation ment our algorithms, we extend the Ligra graph processing Figure 1. An example hypergraph representing the groups framework to support hypergraphs, and our implementa- , , , , , , and , , and its bipartite repre- { 0 1 2} { 1 2 3} { 0 3} tions benet from graph optimizations including switching sentation. between sparse and dense traversals based on the frontier size, edge-aware parallelization, using buckets to prioritize processing of vertices, and compression. Our experiments represented as hyperedges, can contain an arbitrary number on a 72-core machine and show that our algorithms obtain of vertices. Hyperedges correspond to group relationships excellent parallel speedups, and are signicantly faster than among vertices (e.g., a community in a social network). An algorithms in existing hypergraph processing frameworks. example of a hypergraph is shown in Figure 1a. CCS Concepts • Computing methodologies → Paral- Hypergraphs have been shown to enable richer analy- lel algorithms; Shared memory algorithms. -

On the Archimedean Or Semiregular Polyhedra
ON THE ARCHIMEDEAN OR SEMIREGULAR POLYHEDRA Mark B. Villarino Depto. de Matem´atica, Universidad de Costa Rica, 2060 San Jos´e, Costa Rica May 11, 2005 Abstract We prove that there are thirteen Archimedean/semiregular polyhedra by using Euler’s polyhedral formula. Contents 1 Introduction 2 1.1 RegularPolyhedra .............................. 2 1.2 Archimedean/semiregular polyhedra . ..... 2 2 Proof techniques 3 2.1 Euclid’s proof for regular polyhedra . ..... 3 2.2 Euler’s polyhedral formula for regular polyhedra . ......... 4 2.3 ProofsofArchimedes’theorem. .. 4 3 Three lemmas 5 3.1 Lemma1.................................... 5 3.2 Lemma2.................................... 6 3.3 Lemma3.................................... 7 4 Topological Proof of Archimedes’ theorem 8 arXiv:math/0505488v1 [math.GT] 24 May 2005 4.1 Case1: fivefacesmeetatavertex: r=5. .. 8 4.1.1 At least one face is a triangle: p1 =3................ 8 4.1.2 All faces have at least four sides: p1 > 4 .............. 9 4.2 Case2: fourfacesmeetatavertex: r=4 . .. 10 4.2.1 At least one face is a triangle: p1 =3................ 10 4.2.2 All faces have at least four sides: p1 > 4 .............. 11 4.3 Case3: threefacesmeetatavertes: r=3 . ... 11 4.3.1 At least one face is a triangle: p1 =3................ 11 4.3.2 All faces have at least four sides and one exactly four sides: p1 =4 6 p2 6 p3. 12 4.3.3 All faces have at least five sides and one exactly five sides: p1 =5 6 p2 6 p3 13 1 5 Summary of our results 13 6 Final remarks 14 1 Introduction 1.1 Regular Polyhedra A polyhedron may be intuitively conceived as a “solid figure” bounded by plane faces and straight line edges so arranged that every edge joins exactly two (no more, no less) vertices and is a common side of two faces. -

Graph Theory
1 Graph Theory “Begin at the beginning,” the King said, gravely, “and go on till you come to the end; then stop.” — Lewis Carroll, Alice in Wonderland The Pregolya River passes through a city once known as K¨onigsberg. In the 1700s seven bridges were situated across this river in a manner similar to what you see in Figure 1.1. The city’s residents enjoyed strolling on these bridges, but, as hard as they tried, no residentof the city was ever able to walk a route that crossed each of these bridges exactly once. The Swiss mathematician Leonhard Euler learned of this frustrating phenomenon, and in 1736 he wrote an article [98] about it. His work on the “K¨onigsberg Bridge Problem” is considered by many to be the beginning of the field of graph theory. FIGURE 1.1. The bridges in K¨onigsberg. J.M. Harris et al., Combinatorics and Graph Theory , DOI: 10.1007/978-0-387-79711-3 1, °c Springer Science+Business Media, LLC 2008 2 1. Graph Theory At first, the usefulness of Euler’s ideas and of “graph theory” itself was found only in solving puzzles and in analyzing games and other recreations. In the mid 1800s, however, people began to realize that graphs could be used to model many things that were of interest in society. For instance, the “Four Color Map Conjec- ture,” introduced by DeMorgan in 1852, was a famous problem that was seem- ingly unrelated to graph theory. The conjecture stated that four is the maximum number of colors required to color any map where bordering regions are colored differently. -

Archimedean Solids
University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln MAT Exam Expository Papers Math in the Middle Institute Partnership 7-2008 Archimedean Solids Anna Anderson University of Nebraska-Lincoln Follow this and additional works at: https://digitalcommons.unl.edu/mathmidexppap Part of the Science and Mathematics Education Commons Anderson, Anna, "Archimedean Solids" (2008). MAT Exam Expository Papers. 4. https://digitalcommons.unl.edu/mathmidexppap/4 This Article is brought to you for free and open access by the Math in the Middle Institute Partnership at DigitalCommons@University of Nebraska - Lincoln. It has been accepted for inclusion in MAT Exam Expository Papers by an authorized administrator of DigitalCommons@University of Nebraska - Lincoln. Archimedean Solids Anna Anderson In partial fulfillment of the requirements for the Master of Arts in Teaching with a Specialization in the Teaching of Middle Level Mathematics in the Department of Mathematics. Jim Lewis, Advisor July 2008 2 Archimedean Solids A polygon is a simple, closed, planar figure with sides formed by joining line segments, where each line segment intersects exactly two others. If all of the sides have the same length and all of the angles are congruent, the polygon is called regular. The sum of the angles of a regular polygon with n sides, where n is 3 or more, is 180° x (n – 2) degrees. If a regular polygon were connected with other regular polygons in three dimensional space, a polyhedron could be created. In geometry, a polyhedron is a three- dimensional solid which consists of a collection of polygons joined at their edges. The word polyhedron is derived from the Greek word poly (many) and the Indo-European term hedron (seat). -

Practical Parallel Hypergraph Algorithms
Practical Parallel Hypergraph Algorithms Julian Shun [email protected] MIT CSAIL Abstract v0 While there has been significant work on parallel graph pro- e0 cessing, there has been very surprisingly little work on high- v0 v1 v1 performance hypergraph processing. This paper presents a e collection of efficient parallel algorithms for hypergraph pro- 1 v2 cessing, including algorithms for computing hypertrees, hy- v v 2 3 e perpaths, betweenness centrality, maximal independent sets, 2 v k-core decomposition, connected components, PageRank, 3 and single-source shortest paths. For these problems, we ei- (a) Hypergraph (b) Bipartite representation ther provide new parallel algorithms or more efficient imple- mentations than prior work. Furthermore, our algorithms are Figure 1. An example hypergraph representing the groups theoretically-efficient in terms of work and depth. To imple- fv0;v1;v2g, fv1;v2;v3g, and fv0;v3g, and its bipartite repre- ment our algorithms, we extend the Ligra graph processing sentation. framework to support hypergraphs, and our implementations benefit from graph optimizations including switching between improved compared to using a graph representation. Unfor- sparse and dense traversals based on the frontier size, edge- tunately, there is been little research on parallel hypergraph aware parallelization, using buckets to prioritize processing processing. of vertices, and compression. Our experiments on a 72-core The main contribution of this paper is a suite of efficient machine and show that our algorithms obtain excellent paral- parallel hypergraph algorithms, including algorithms for hy- lel speedups, and are significantly faster than algorithms in pertrees, hyperpaths, betweenness centrality, maximal inde- existing hypergraph processing frameworks. -

Graph Mining: Social Network Analysis and Information Diffusion
Graph Mining: Social network analysis and Information Diffusion Davide Mottin, Konstantina Lazaridou Hasso Plattner Institute Graph Mining course Winter Semester 2016 Lecture road Introduction to social networks Real word networks’ characteristics Information diffusion GRAPH MINING WS 2016 2 Paper presentations ▪ Link to form: https://goo.gl/ivRhKO ▪ Choose the date(s) you are available ▪ Choose three papers according to preference (there are three lists) ▪ Choose at least one paper for each course part ▪ Register to the mailing list: https://lists.hpi.uni-potsdam.de/listinfo/graphmining-ws1617 GRAPH MINING WS 2016 3 What is a social network? ▪Oxford dictionary A social network is a network of social interactions and personal relationships GRAPH MINING WS 2016 4 What is an online social network? ▪ Oxford dictionary An online social network (OSN) is a dedicated website or other application, which enables users to communicate with each other by posting information, comments, messages, images, etc. ▪ Computer science : A network that consists of a finite number of users (nodes) that interact with each other (edges) by sharing information (labels, signs, edge directions etc.) GRAPH MINING WS 2016 5 Definitions ▪Vertex/Node : a user of the social network (Twitter user, an author in a co-authorship network, an actor etc.) ▪Edge/Link/Tie : the connection between two vertices referring to their relationship or interaction (friend-of relationship, re-tweeting activity, etc.) Graph G=(V,E) symbols meaning V users E connections deg(u) node degree: -

Adjacency Matrix
CSE 373 Graphs 3: Implementation reading: Weiss Ch. 9 slides created by Marty Stepp http://www.cs.washington.edu/373/ © University of Washington, all rights reserved. 1 Implementing a graph • If we wanted to program an actual data structure to represent a graph, what information would we need to store? for each vertex? for each edge? 1 2 3 • What kinds of questions would we want to be able to answer quickly: 4 5 6 about a vertex? about edges / neighbors? 7 about paths? about what edges exist in the graph? • We'll explore three common graph implementation strategies: edge list , adjacency list , adjacency matrix 2 Edge list • edge list : An unordered list of all edges in the graph. an array, array list, or linked list • advantages : 1 2 3 easy to loop/iterate over all edges 4 5 6 • disadvantages : hard to quickly tell if an edge 7 exists from vertex A to B hard to quickly find the degree of a vertex (how many edges touch it) 0 1 2 3 4 56 7 8 (1, 2) (1, 4) (1, 7) (2, 3) 2, 5) (3, 6)(4, 7) (5, 6) (6, 7) 3 Graph operations • Using an edge list, how would you find: all neighbors of a given vertex? the degree of a given vertex? whether there is an edge from A to B? 1 2 3 whether there are any loops (self-edges)? • What is the Big-Oh of each operation? 4 5 6 7 0 1 2 3 4 56 7 8 (1, 2) (1, 4) (1, 7) (2, 3) 2, 5) (3, 6)(4, 7) (5, 6) (6, 7) 4 Adjacency matrix • adjacency matrix : An N × N matrix where: the non-diagonal entry a[i,j] is the number of edges joining vertex i and vertex j (or the weight of the edge joining vertex i and vertex j). -

Introduction to Graphs
Multidimensional Arrays & Graphs CMSC 420: Lecture 3 Mini-Review • Abstract Data Types: • Implementations: • List • Linked Lists • Stack • Circularly linked lists • Queue • Doubly linked lists • Deque • XOR Doubly linked lists • Dictionary • Ring buffers • Set • Double stacks • Bit vectors Techniques: Sentinels, Zig-zag scan, link inversion, bit twiddling, self- organizing lists, constant-time initialization Constant-Time Initialization • Design problem: - Suppose you have a long array, most values are 0. - Want constant time access and update - Have as much space as you need. • Create a big array: - a = new int[LARGE_N]; - Too slow: for(i=0; i < LARGE_N; i++) a[i] = 0 • Want to somehow implicitly initialize all values to 0 in constant time... Constant-Time Initialization means unchanged 1 2 6 12 13 Data[] = • Access(i): if (0≤ When[i] < count and Where[When[i]] == i) return Where[] = 6 13 12 Count = 3 Count holds # of elements changed Where holds indices of the changed elements. When[] = 1 3 2 When maps from index i to the time step when item i was first changed. Access(i): if 0 ≤ When[i] < Count and Where[When[i]] == i: return Data[i] else: return DEFAULT Multidimensional Arrays • Often it’s more natural to index data items by keys that have several dimensions. E.g.: • (longitude, latitude) • (row, column) of a matrix • (x,y,z) point in 3d space • Aside: why is a plane “2-dimensional”? Row-major vs. Column-major order • 2-dimensional arrays can be mapped to linear memory in two ways: 1 2 3 4 5 1 2 3 4 5 1 1 2 3 4 5 1 1 5 9 13 17 2 6 7 8 9 10 2 2 6 10 14 18 3 11 12 13 14 15 3 3 7 11 15 19 4 16 17 18 19 20 4 4 8 12 16 20 Row-major order Column-major order Addr(i,j) = Base + 5(i-1) + (j-1) Addr(i,j) = Base + (i-1) + 4(j-1) Row-major vs. -
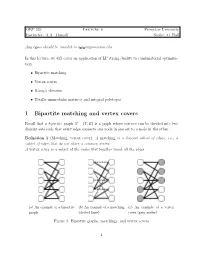
1 Bipartite Matching and Vertex Covers
ORF 523 Lecture 6 Princeton University Instructor: A.A. Ahmadi Scribe: G. Hall Any typos should be emailed to a a [email protected]. In this lecture, we will cover an application of LP strong duality to combinatorial optimiza- tion: • Bipartite matching • Vertex covers • K¨onig'stheorem • Totally unimodular matrices and integral polytopes. 1 Bipartite matching and vertex covers Recall that a bipartite graph G = (V; E) is a graph whose vertices can be divided into two disjoint sets such that every edge connects one node in one set to a node in the other. Definition 1 (Matching, vertex cover). A matching is a disjoint subset of edges, i.e., a subset of edges that do not share a common vertex. A vertex cover is a subset of the nodes that together touch all the edges. (a) An example of a bipartite (b) An example of a matching (c) An example of a vertex graph (dotted lines) cover (grey nodes) Figure 1: Bipartite graphs, matchings, and vertex covers 1 Lemma 1. The cardinality of any matching is less than or equal to the cardinality of any vertex cover. This is easy to see: consider any matching. Any vertex cover must have nodes that at least touch the edges in the matching. Moreover, a single node can at most cover one edge in the matching because the edges are disjoint. As it will become clear shortly, this property can also be seen as an immediate consequence of weak duality in linear programming. Theorem 1 (K¨onig). If G is bipartite, the cardinality of the maximum matching is equal to the cardinality of the minimum vertex cover. -

An Enduring Error
Version June 5, 2008 Branko Grünbaum: An enduring error 1. Introduction. Mathematical truths are immutable, but mathematicians do make errors, especially when carrying out non-trivial enumerations. Some of the errors are "innocent" –– plain mis- takes that get corrected as soon as an independent enumeration is carried out. For example, Daublebsky [14] in 1895 found that there are precisely 228 types of configurations (123), that is, collections of 12 lines and 12 points, each incident with three of the others. In fact, as found by Gropp [19] in 1990, the correct number is 229. Another example is provided by the enumeration of the uniform tilings of the 3-dimensional space by Andreini [1] in 1905; he claimed that there are precisely 25 types. However, as shown [20] in 1994, the correct num- ber is 28. Andreini listed some tilings that should not have been included, and missed several others –– but again, these are simple errors easily corrected. Much more insidious are errors that arise by replacing enumeration of one kind of ob- ject by enumeration of some other objects –– only to disregard the logical and mathematical distinctions between the two enumerations. It is surprising how errors of this type escape detection for a long time, even though there is frequent mention of the results. One example is provided by the enumeration of 4-dimensional simple polytopes with 8 facets, by Brückner [7] in 1909. He replaces this enumeration by that of 3-dimensional "diagrams" that he inter- preted as Schlegel diagrams of convex 4-polytopes, and claimed that the enumeration of these objects is equivalent to that of the polytopes. -

9 the Graph Data Model
CHAPTER 9 ✦ ✦ ✦ ✦ The Graph Data Model A graph is, in a sense, nothing more than a binary relation. However, it has a powerful visualization as a set of points (called nodes) connected by lines (called edges) or by arrows (called arcs). In this regard, the graph is a generalization of the tree data model that we studied in Chapter 5. Like trees, graphs come in several forms: directed/undirected, and labeled/unlabeled. Also like trees, graphs are useful in a wide spectrum of problems such as com- puting distances, finding circularities in relationships, and determining connectiv- ities. We have already seen graphs used to represent the structure of programs in Chapter 2. Graphs were used in Chapter 7 to represent binary relations and to illustrate certain properties of relations, like commutativity. We shall see graphs used to represent automata in Chapter 10 and to represent electronic circuits in Chapter 13. Several other important applications of graphs are discussed in this chapter. ✦ ✦ ✦ ✦ 9.1 What This Chapter Is About The main topics of this chapter are ✦ The definitions concerning directed and undirected graphs (Sections 9.2 and 9.10). ✦ The two principal data structures for representing graphs: adjacency lists and adjacency matrices (Section 9.3). ✦ An algorithm and data structure for finding the connected components of an undirected graph (Section 9.4). ✦ A technique for finding minimal spanning trees (Section 9.5). ✦ A useful technique for exploring graphs, called “depth-first search” (Section 9.6). 451 452 THE GRAPH DATA MODEL ✦ Applications of depth-first search to test whether a directed graph has a cycle, to find a topological order for acyclic graphs, and to determine whether there is a path from one node to another (Section 9.7). -

A Multigraph Approach to Social Network Analysis
1 Introduction Network data involving relational structure representing interactions between actors are commonly represented by graphs where the actors are referred to as vertices or nodes, and the relations are referred to as edges or ties connecting pairs of actors. Research on social networks is a well established branch of study and many issues concerning social network analysis can be found in Wasserman and Faust (1994), Carrington et al. (2005), Butts (2008), Frank (2009), Kolaczyk (2009), Scott and Carrington (2011), Snijders (2011), and Robins (2013). A common approach to social network analysis is to only consider binary relations, i.e. edges between pairs of vertices are either present or not. These simple graphs only consider one type of relation and exclude the possibility for self relations where a vertex is both the sender and receiver of an edge (also called edge loops or just shortly loops). In contrast, a complex graph is defined according to Wasserman and Faust (1994): If a graph contains loops and/or any pairs of nodes is adjacent via more than one line the graph is complex. [p. 146] In practice, simple graphs can be derived from complex graphs by collapsing the multiple edges into single ones and removing the loops. However, this approach discards information inherent in the original network. In order to use all available network information, we must allow for multiple relations and the possibility for loops. This leads us to the study of multigraphs which has not been treated as extensively as simple graphs in the literature. As an example, consider a network with vertices representing different branches of an organ- isation.