Graph Mining: Social Network Analysis and Information Diffusion
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Directed Graph Algorithms
Directed Graph Algorithms CSE 373 Data Structures Readings • Reading Chapter 13 › Sections 13.3 and 13.4 Digraphs 2 Topological Sort 142 322 143 321 Problem: Find an order in which all these courses can 326 be taken. 370 341 Example: 142 Æ 143 Æ 378 Æ 370 Æ 321 Æ 341 Æ 322 Æ 326 Æ 421 Æ 401 378 421 In order to take a course, you must 401 take all of its prerequisites first Digraphs 3 Topological Sort Given a digraph G = (V, E), find a linear ordering of its vertices such that: for any edge (v, w) in E, v precedes w in the ordering B C A F D E Digraphs 4 Topo sort – valid solution B C Any linear ordering in which A all the arrows go to the right F is a valid solution D E A B F C D E Note that F can go anywhere in this list because it is not connected. Also the solution is not unique. Digraphs 5 Topo sort – invalid solution B C A Any linear ordering in which an arrow goes to the left F is not a valid solution D E A B F C E D NO! Digraphs 6 Paths and Cycles • Given a digraph G = (V,E), a path is a sequence of vertices v1,v2, …,vk such that: ›(vi,vi+1) in E for 1 < i < k › path length = number of edges in the path › path cost = sum of costs of each edge • A path is a cycle if : › k > 1; v1 = vk •G is acyclic if it has no cycles. -

Graph Varieties Axiomatized by Semimedial, Medial, and Some Other Groupoid Identities
Discussiones Mathematicae General Algebra and Applications 40 (2020) 143–157 doi:10.7151/dmgaa.1344 GRAPH VARIETIES AXIOMATIZED BY SEMIMEDIAL, MEDIAL, AND SOME OTHER GROUPOID IDENTITIES Erkko Lehtonen Technische Universit¨at Dresden Institut f¨ur Algebra 01062 Dresden, Germany e-mail: [email protected] and Chaowat Manyuen Department of Mathematics, Faculty of Science Khon Kaen University Khon Kaen 40002, Thailand e-mail: [email protected] Abstract Directed graphs without multiple edges can be represented as algebras of type (2, 0), so-called graph algebras. A graph is said to satisfy an identity if the corresponding graph algebra does, and the set of all graphs satisfying a set of identities is called a graph variety. We describe the graph varieties axiomatized by certain groupoid identities (medial, semimedial, autodis- tributive, commutative, idempotent, unipotent, zeropotent, alternative). Keywords: graph algebra, groupoid, identities, semimediality, mediality. 2010 Mathematics Subject Classification: 05C25, 03C05. 1. Introduction Graph algebras were introduced by Shallon [10] in 1979 with the purpose of providing examples of nonfinitely based finite algebras. Let us briefly recall this concept. Given a directed graph G = (V, E) without multiple edges, the graph algebra associated with G is the algebra A(G) = (V ∪ {∞}, ◦, ∞) of type (2, 0), 144 E. Lehtonen and C. Manyuen where ∞ is an element not belonging to V and the binary operation ◦ is defined by the rule u, if (u, v) ∈ E, u ◦ v := (∞, otherwise, for all u, v ∈ V ∪ {∞}. We will denote the product u ◦ v simply by juxtaposition uv. Using this representation, we may view any algebraic property of a graph algebra as a property of the graph with which it is associated. -

Networkx: Network Analysis with Python
NetworkX: Network Analysis with Python Salvatore Scellato Full tutorial presented at the XXX SunBelt Conference “NetworkX introduction: Hacking social networks using the Python programming language” by Aric Hagberg & Drew Conway Outline 1. Introduction to NetworkX 2. Getting started with Python and NetworkX 3. Basic network analysis 4. Writing your own code 5. You are ready for your project! 1. Introduction to NetworkX. Introduction to NetworkX - network analysis Vast amounts of network data are being generated and collected • Sociology: web pages, mobile phones, social networks • Technology: Internet routers, vehicular flows, power grids How can we analyze this networks? Introduction to NetworkX - Python awesomeness Introduction to NetworkX “Python package for the creation, manipulation and study of the structure, dynamics and functions of complex networks.” • Data structures for representing many types of networks, or graphs • Nodes can be any (hashable) Python object, edges can contain arbitrary data • Flexibility ideal for representing networks found in many different fields • Easy to install on multiple platforms • Online up-to-date documentation • First public release in April 2005 Introduction to NetworkX - design requirements • Tool to study the structure and dynamics of social, biological, and infrastructure networks • Ease-of-use and rapid development in a collaborative, multidisciplinary environment • Easy to learn, easy to teach • Open-source tool base that can easily grow in a multidisciplinary environment with non-expert users -

On the Archimedean Or Semiregular Polyhedra
ON THE ARCHIMEDEAN OR SEMIREGULAR POLYHEDRA Mark B. Villarino Depto. de Matem´atica, Universidad de Costa Rica, 2060 San Jos´e, Costa Rica May 11, 2005 Abstract We prove that there are thirteen Archimedean/semiregular polyhedra by using Euler’s polyhedral formula. Contents 1 Introduction 2 1.1 RegularPolyhedra .............................. 2 1.2 Archimedean/semiregular polyhedra . ..... 2 2 Proof techniques 3 2.1 Euclid’s proof for regular polyhedra . ..... 3 2.2 Euler’s polyhedral formula for regular polyhedra . ......... 4 2.3 ProofsofArchimedes’theorem. .. 4 3 Three lemmas 5 3.1 Lemma1.................................... 5 3.2 Lemma2.................................... 6 3.3 Lemma3.................................... 7 4 Topological Proof of Archimedes’ theorem 8 arXiv:math/0505488v1 [math.GT] 24 May 2005 4.1 Case1: fivefacesmeetatavertex: r=5. .. 8 4.1.1 At least one face is a triangle: p1 =3................ 8 4.1.2 All faces have at least four sides: p1 > 4 .............. 9 4.2 Case2: fourfacesmeetatavertex: r=4 . .. 10 4.2.1 At least one face is a triangle: p1 =3................ 10 4.2.2 All faces have at least four sides: p1 > 4 .............. 11 4.3 Case3: threefacesmeetatavertes: r=3 . ... 11 4.3.1 At least one face is a triangle: p1 =3................ 11 4.3.2 All faces have at least four sides and one exactly four sides: p1 =4 6 p2 6 p3. 12 4.3.3 All faces have at least five sides and one exactly five sides: p1 =5 6 p2 6 p3 13 1 5 Summary of our results 13 6 Final remarks 14 1 Introduction 1.1 Regular Polyhedra A polyhedron may be intuitively conceived as a “solid figure” bounded by plane faces and straight line edges so arranged that every edge joins exactly two (no more, no less) vertices and is a common side of two faces. -

Graph Theory
1 Graph Theory “Begin at the beginning,” the King said, gravely, “and go on till you come to the end; then stop.” — Lewis Carroll, Alice in Wonderland The Pregolya River passes through a city once known as K¨onigsberg. In the 1700s seven bridges were situated across this river in a manner similar to what you see in Figure 1.1. The city’s residents enjoyed strolling on these bridges, but, as hard as they tried, no residentof the city was ever able to walk a route that crossed each of these bridges exactly once. The Swiss mathematician Leonhard Euler learned of this frustrating phenomenon, and in 1736 he wrote an article [98] about it. His work on the “K¨onigsberg Bridge Problem” is considered by many to be the beginning of the field of graph theory. FIGURE 1.1. The bridges in K¨onigsberg. J.M. Harris et al., Combinatorics and Graph Theory , DOI: 10.1007/978-0-387-79711-3 1, °c Springer Science+Business Media, LLC 2008 2 1. Graph Theory At first, the usefulness of Euler’s ideas and of “graph theory” itself was found only in solving puzzles and in analyzing games and other recreations. In the mid 1800s, however, people began to realize that graphs could be used to model many things that were of interest in society. For instance, the “Four Color Map Conjec- ture,” introduced by DeMorgan in 1852, was a famous problem that was seem- ingly unrelated to graph theory. The conjecture stated that four is the maximum number of colors required to color any map where bordering regions are colored differently. -

Structural Graph Theory Meets Algorithms: Covering And
Structural Graph Theory Meets Algorithms: Covering and Connectivity Problems in Graphs Saeed Akhoondian Amiri Fakult¨atIV { Elektrotechnik und Informatik der Technischen Universit¨atBerlin zur Erlangung des akademischen Grades Doktor der Naturwissenschaften Dr. rer. nat. genehmigte Dissertation Promotionsausschuss: Vorsitzender: Prof. Dr. Rolf Niedermeier Gutachter: Prof. Dr. Stephan Kreutzer Gutachter: Prof. Dr. Marcin Pilipczuk Gutachter: Prof. Dr. Dimitrios Thilikos Tag der wissenschaftlichen Aussprache: 13. October 2017 Berlin 2017 2 This thesis is dedicated to my family, especially to my beautiful wife Atefe and my lovely son Shervin. 3 Contents Abstract iii Acknowledgementsv I. Introduction and Preliminaries1 1. Introduction2 1.0.1. General Techniques and Models......................3 1.1. Covering Problems.................................6 1.1.1. Covering Problems in Distributed Models: Case of Dominating Sets.6 1.1.2. Covering Problems in Directed Graphs: Finding Similar Patterns, the Case of Erd}os-P´osaproperty.......................9 1.2. Routing Problems in Directed Graphs...................... 11 1.2.1. Routing Problems............................. 11 1.2.2. Rerouting Problems............................ 12 1.3. Structure of the Thesis and Declaration of Authorship............. 14 2. Preliminaries and Notations 16 2.1. Basic Notations and Defnitions.......................... 16 2.1.1. Sets..................................... 16 2.1.2. Graphs................................... 16 2.2. Complexity Classes................................ -

Archimedean Solids
University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln MAT Exam Expository Papers Math in the Middle Institute Partnership 7-2008 Archimedean Solids Anna Anderson University of Nebraska-Lincoln Follow this and additional works at: https://digitalcommons.unl.edu/mathmidexppap Part of the Science and Mathematics Education Commons Anderson, Anna, "Archimedean Solids" (2008). MAT Exam Expository Papers. 4. https://digitalcommons.unl.edu/mathmidexppap/4 This Article is brought to you for free and open access by the Math in the Middle Institute Partnership at DigitalCommons@University of Nebraska - Lincoln. It has been accepted for inclusion in MAT Exam Expository Papers by an authorized administrator of DigitalCommons@University of Nebraska - Lincoln. Archimedean Solids Anna Anderson In partial fulfillment of the requirements for the Master of Arts in Teaching with a Specialization in the Teaching of Middle Level Mathematics in the Department of Mathematics. Jim Lewis, Advisor July 2008 2 Archimedean Solids A polygon is a simple, closed, planar figure with sides formed by joining line segments, where each line segment intersects exactly two others. If all of the sides have the same length and all of the angles are congruent, the polygon is called regular. The sum of the angles of a regular polygon with n sides, where n is 3 or more, is 180° x (n – 2) degrees. If a regular polygon were connected with other regular polygons in three dimensional space, a polyhedron could be created. In geometry, a polyhedron is a three- dimensional solid which consists of a collection of polygons joined at their edges. The word polyhedron is derived from the Greek word poly (many) and the Indo-European term hedron (seat). -

Katz Centrality for Directed Graphs • Understand How Katz Centrality Is an Extension of Eigenvector Centrality to Learning Directed Graphs
Prof. Ralucca Gera, [email protected] Applied Mathematics Department, ExcellenceNaval Postgraduate Through Knowledge School MA4404 Complex Networks Katz Centrality for directed graphs • Understand how Katz centrality is an extension of Eigenvector Centrality to Learning directed graphs. Outcomes • Compute Katz centrality per node. • Interpret the meaning of the values of Katz centrality. Recall: Centralities Quality: what makes a node Mathematical Description Appropriate Usage Identification important (central) Lots of one-hop connections The number of vertices that Local influence Degree from influences directly matters deg Small diameter Lots of one-hop connections The proportion of the vertices Local influence Degree centrality from relative to the size of that influences directly matters deg C the graph Small diameter |V(G)| Lots of one-hop connections A weighted degree centrality For example when the Eigenvector centrality to high centrality vertices based on the weight of the people you are (recursive formula): neighbors (instead of a weight connected to matter. ∝ of 1 as in degree centrality) Recall: Strongly connected Definition: A directed graph D = (V, E) is strongly connected if and only if, for each pair of nodes u, v ∈ V, there is a path from u to v. • The Web graph is not strongly connected since • there are pairs of nodes u and v, there is no path from u to v and from v to u. • This presents a challenge for nodes that have an in‐degree of zero Add a link from each page to v every page and give each link a small transition probability controlled by a parameter β. u Source: http://en.wikipedia.org/wiki/Directed_acyclic_graph 4 Katz Centrality • Recall that the eigenvector centrality is a weighted degree obtained from the leading eigenvector of A: A x =λx , so its entries are 1 λ Thoughts on how to adapt the above formula for directed graphs? • Katz centrality: ∑ + β, Where β is a constant initial weight given to each vertex so that vertices with zero in degree (or out degree) are included in calculations. -

A Gentle Introduction to Deep Learning for Graphs
A Gentle Introduction to Deep Learning for Graphs Davide Bacciua, Federico Erricaa, Alessio Michelia, Marco Poddaa aDepartment of Computer Science, University of Pisa, Italy. Abstract The adaptive processing of graph data is a long-standing research topic that has been lately consolidated as a theme of major interest in the deep learning community. The snap increase in the amount and breadth of related research has come at the price of little systematization of knowledge and attention to earlier literature. This work is a tutorial introduction to the field of deep learn- ing for graphs. It favors a consistent and progressive presentation of the main concepts and architectural aspects over an exposition of the most recent liter- ature, for which the reader is referred to available surveys. The paper takes a top-down view of the problem, introducing a generalized formulation of graph representation learning based on a local and iterative approach to structured in- formation processing. Moreover, it introduces the basic building blocks that can be combined to design novel and effective neural models for graphs. We com- plement the methodological exposition with a discussion of interesting research challenges and applications in the field. Keywords: deep learning for graphs, graph neural networks, learning for structured data arXiv:1912.12693v2 [cs.LG] 15 Jun 2020 1. Introduction Graphs are a powerful tool to represent data that is produced by a variety of artificial and natural processes. A graph has a compositional nature, being a compound of atomic information pieces, and a relational nature, as the links defining its structure denote relationships between the linked entities. -

A Faster Parameterized Algorithm for PSEUDOFOREST DELETION
A faster parameterized algorithm for PSEUDOFOREST DELETION Citation for published version (APA): Bodlaender, H. L., Ono, H., & Otachi, Y. (2018). A faster parameterized algorithm for PSEUDOFOREST DELETION. Discrete Applied Mathematics, 236, 42-56. https://doi.org/10.1016/j.dam.2017.10.018 Document license: Unspecified DOI: 10.1016/j.dam.2017.10.018 Document status and date: Published: 19/02/2018 Document Version: Accepted manuscript including changes made at the peer-review stage Please check the document version of this publication: • A submitted manuscript is the version of the article upon submission and before peer-review. There can be important differences between the submitted version and the official published version of record. People interested in the research are advised to contact the author for the final version of the publication, or visit the DOI to the publisher's website. • The final author version and the galley proof are versions of the publication after peer review. • The final published version features the final layout of the paper including the volume, issue and page numbers. Link to publication General rights Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. • Users may download and print one copy of any publication from the public portal for the purpose of private study or research. • You may not further distribute the material or use it for any profit-making activity or commercial gain • You may freely distribute the URL identifying the publication in the public portal. -
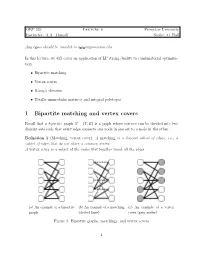
1 Bipartite Matching and Vertex Covers
ORF 523 Lecture 6 Princeton University Instructor: A.A. Ahmadi Scribe: G. Hall Any typos should be emailed to a a [email protected]. In this lecture, we will cover an application of LP strong duality to combinatorial optimiza- tion: • Bipartite matching • Vertex covers • K¨onig'stheorem • Totally unimodular matrices and integral polytopes. 1 Bipartite matching and vertex covers Recall that a bipartite graph G = (V; E) is a graph whose vertices can be divided into two disjoint sets such that every edge connects one node in one set to a node in the other. Definition 1 (Matching, vertex cover). A matching is a disjoint subset of edges, i.e., a subset of edges that do not share a common vertex. A vertex cover is a subset of the nodes that together touch all the edges. (a) An example of a bipartite (b) An example of a matching (c) An example of a vertex graph (dotted lines) cover (grey nodes) Figure 1: Bipartite graphs, matchings, and vertex covers 1 Lemma 1. The cardinality of any matching is less than or equal to the cardinality of any vertex cover. This is easy to see: consider any matching. Any vertex cover must have nodes that at least touch the edges in the matching. Moreover, a single node can at most cover one edge in the matching because the edges are disjoint. As it will become clear shortly, this property can also be seen as an immediate consequence of weak duality in linear programming. Theorem 1 (K¨onig). If G is bipartite, the cardinality of the maximum matching is equal to the cardinality of the minimum vertex cover. -

An Enduring Error
Version June 5, 2008 Branko Grünbaum: An enduring error 1. Introduction. Mathematical truths are immutable, but mathematicians do make errors, especially when carrying out non-trivial enumerations. Some of the errors are "innocent" –– plain mis- takes that get corrected as soon as an independent enumeration is carried out. For example, Daublebsky [14] in 1895 found that there are precisely 228 types of configurations (123), that is, collections of 12 lines and 12 points, each incident with three of the others. In fact, as found by Gropp [19] in 1990, the correct number is 229. Another example is provided by the enumeration of the uniform tilings of the 3-dimensional space by Andreini [1] in 1905; he claimed that there are precisely 25 types. However, as shown [20] in 1994, the correct num- ber is 28. Andreini listed some tilings that should not have been included, and missed several others –– but again, these are simple errors easily corrected. Much more insidious are errors that arise by replacing enumeration of one kind of ob- ject by enumeration of some other objects –– only to disregard the logical and mathematical distinctions between the two enumerations. It is surprising how errors of this type escape detection for a long time, even though there is frequent mention of the results. One example is provided by the enumeration of 4-dimensional simple polytopes with 8 facets, by Brückner [7] in 1909. He replaces this enumeration by that of 3-dimensional "diagrams" that he inter- preted as Schlegel diagrams of convex 4-polytopes, and claimed that the enumeration of these objects is equivalent to that of the polytopes.