Mobile Device Security Issues Within the U.S. Disadvantaged Business Enterprise Program
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Top 20 Influencers
Top 20 AR/VR InfluencersWhat Fits You Best? Sanem Avcil Palmer Luckey @Sanemavcil @PalmerLuckey Founder of Coolo Games, Founder of Oculus Rift; CEO of Politehelp & And, the well known Imprezscion Yazilim Ve voice in VR. Elektronik. Chris Milk Alex Kipman @milk @akipman Maker of stuff, Key player in the launch of Co-Founder/CEO of Within. Microsoft Hololens. Creator of Focusing on innovative human the Microsoft Kinect experiences in VR. motion controller. Philip Rosedale Tony Parisi @philiprosedale @auradeluxe Founder of Head of AR and VR Strategy at 2000s MMO experience, Unity, began his VR career Second Life. co-founding VRML in 1994 with Mark Pesce. Kent Bye Clay Bavor @kentbye @claybavor Host of leading Vice President of Virtual Reality VR podcast, Voices of VR & at Google. Esoteric Voices. Rob Crasco Benjamin Lang @RoblemVR @benz145 VR Consultant at Co-founder & Executive Editor of VR/AR Consulting. Writes roadtovr.com, one of the leading monthly articles on VR for VR news sites in the world. Bright Metallic magazine. Vanessa Radd Chris Madsen @vanradd @deep_rifter Founder, XR Researcher; Director at Morph3D, President, VRAR Association. Ambassador at Edge of Discovery. VR/AR/Experiencial Technology. Helen Papagiannis Cathy Hackl @ARstories @CathyHackl PhD; Augmented Reality Founder, Latinos in VR/AR. Specialist. Author of Marketing Co-Chair at VR/AR Augmented Human. Assciation; VR/AR Speaker. Brad Waid Ambarish Mitra @Techbradwaid @rishmitra Global Speaker, Futurist, Founder & CEO at blippar, Educator, Entrepreneur. Young Global Leader at Wef, Investor in AugmentedReality, AI & Genomics. Tom Emrich Gaia Dempsey @tomemrich @fianxu VC at Super Ventures, Co-founder at DAQRI, Fonder, We Are Wearables; Augmented Reality Futurist. -

The Android Platform Security Model∗
The Android Platform Security Model∗ RENÉ MAYRHOFER, Google and Johannes Kepler University Linz JEFFREY VANDER STOEP, Google CHAD BRUBAKER, Google NICK KRALEVICH, Google Android is the most widely deployed end-user focused operating system. With its growing set of use cases encompassing communication, navigation, media consumption, entertainment, finance, health, and access to sensors, actuators, cameras, or microphones, its underlying security model needs to address a host of practical threats in a wide variety of scenarios while being useful to non-security experts. The model needs to strike a difficult balance between security, privacy, and usability for end users, assurances for app developers, and system performance under tight hardware constraints. While many of the underlying design principles have implicitly informed the overall system architecture, access control mechanisms, and mitigation techniques, the Android security model has previously not been formally published. This paper aims to both document the abstract model and discuss its implications. Based on a definition of the threat model and Android ecosystem context in which it operates, we analyze how the different security measures in past and current Android implementations work together to mitigate these threats. There are some special cases in applying the security model, and we discuss such deliberate deviations from the abstract model. CCS Concepts: • Security and privacy → Software and application security; Domain-specific security and privacy architectures; Operating systems security; • Human-centered computing → Ubiquitous and mobile devices. Additional Key Words and Phrases: Android, security, operating system, informal model 1 INTRODUCTION Android is, at the time of this writing, the most widely deployed end-user operating system. -

User Manual Please Read This Manual Before Operating Your Device and Keep It for Future Reference
User Manual Please read this manual before operating your device and keep it for future reference. Table of Contents Support .......................................................................... 3 Basic Navigation and Selection ............................25 Using the Touchpad ..............................................25 Read me first ................................................................ 4 Moving the On-Screen Pointer ............................28 Wearing the Gear VR .............................................. 5 Making a Selection ...............................................29 Precautions ............................................................... 6 Navigation - Home Screen ...................................30 Before Using the Gear VR Headset ..................... 6 Navigation - App Screen ......................................31 About the Gear VR .................................................. 7 Using the Universal Menu ....................................34 Additional Notifications ........................................... 8 Calls .........................................................................40 Getting Started ............................................................ 9 Viewing Notifications .............................................41 Device Features ....................................................... 9 Function Overview .................................................12 Applications ................................................................42 Loading New Applications -
Android (Operating System) 1 Android (Operating System)
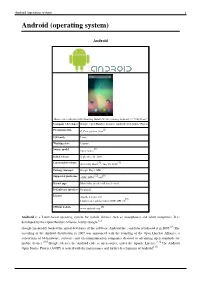
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Galaxy Nexus, running Android 4.1 "Jelly Bean" Company / developer Google, Open Handset Alliance, Android Open Source Project [1] Programmed in C, C++, python, Java OS family Linux Working state Current [2] Source model Open source Initial release September 20, 2008 [3] [4] Latest stable release 4.1.1 Jelly Bean / July 10, 2012 Package manager Google Play / APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) Default user interface Graphical License Apache License 2.0 [7] Linux kernel patches under GNU GPL v2 [8] Official website www.android.com Android is a Linux-based operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance, led by Google.[2] Google financially backed the initial developer of the software, Android Inc., and later purchased it in 2005.[9] The unveiling of the Android distribution in 2007 was announced with the founding of the Open Handset Alliance, a consortium of 86 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[10] Google releases the Android code as open-source, under the Apache License.[11] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[12] Android (operating system) 2 Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. Developers write primarily in a customized version of Java.[13] Apps can be downloaded from third-party sites or through online stores such as Google Play (formerly Android Market), the app store run by Google. -

SM-R320 Samsung Gear VR User Manual
User Manual Please read this manual before operating your device and keep it for future reference. Table of Contents Support .......................................................................... 3 Basic Navigation and Selection ............................25 Using the Touchpad ..............................................25 Read me first ................................................................ 4 Moving the On-Screen Pointer ............................28 Wearing the Gear VR .............................................. 5 Making a Selection ...............................................29 Precautions ............................................................... 6 Navigation - Home Screen ...................................30 Before Using the Gear VR Headset ..................... 6 Navigation - App Screen ......................................31 About the Gear VR .................................................. 7 Using the Universal Menu ....................................34 Additional Notifications ........................................... 8 Calls .........................................................................40 Getting Started ............................................................ 9 Viewing Notifications .............................................41 Device Features ....................................................... 9 Function Overview .................................................12 Applications ................................................................42 Loading New Applications -

Google Cardboard Virtual Reality
Google Cardboard Virtual Reality At a Glance... Access It At... Various services, such as YouTube, Google Maps, •Allows users to wear virtual- and more reality goggles and experience virtual reality photo-spheres or video-spheres Required Knowledge... •School provides cardboard •Basic mobile device usage goggles; student provides •Basic web browsing BYOD mobile device •High level of engagement, Username / Password brings learning to life •Varies, based on which service you use Note that LRMS provides “Google Cardboard” goggles, but students must provide their own device to use inside of it. LRMS owns no small mobile devices that will work with Google Cardboard. To begin with, you’ll need to access virtual-reality photo/videospheres. These exist on many services. Here are some common ones. Note to view these video/photos, you’ll need to access the content through the app for the service. For example, pulling up “YouTube” using a web browser on a phone will not enable the VR features. But, if you install and launch the YouTube app, you WILL be able to access them. YouTube A great place to start is the YouTube VR channel. Search YouTube for “Google Cardboard” and look for the channel “360° Videos.” Google Maps Street View You can find many locations throughout the world to experience in “360.” Install the app, find a location on the map, and launch the VR view. Google Expeditions This app is designed for education and contains tools that let the teacher lead “expeditions” through international locations. Note this app is still in the testing phase and has not been released to the public as of April, 2016. -

Thrive Hearing Control App User Guide
Thrive Hearing Control App User Guide Congratulations on your journey to better hearing Thrive Hearing Control app Table of Contents Table of Contents Introduction . 4 Wellness Score Screens Apple Users Overall . 19 Pairing/Connecting . 5 Engagement . 19 Downloading . 8 Activity . 20 Android Users Fall Detection and Alerts . 21 Downloading . 9 Accessories . 23 Pairing/Connecting . 10 Voice AI. 23 Home Screen Settings Connection Status . 13 User Guide . 24 Thrive Assistant . 13 Device Settings . 24 Wellness Score . 13 Wellness Score . 25 Current Memory . 13 Fall Alert . 26 Settings/Help . 13 Translate . 27 Volume . 14 Transcribe . 27 Mute . 14 Self Check . 28 Edge Mode . 14 Reminders . 28 Navigation . 15 TeleHear Remote Programming . 30 Home . 15 Thrive Care app . 31 Memory Menu . 15 Find My Hearing Aids . 31 Customize Screens App Settings . 32 Customize Screens . 16 About . 32 Equalizer . 16 Demo Mode . 32 Speech in Noise . 16 Safety Information . 33 Machine Noise . 17 Wind . 17 Microphone Direction . 18 SoundSpace . 18 All features vary by hearing aid model and technology tier. Ask your hearing professional for specific information. This app may have slight differences depending on your phone and/or hearing aid model. 4 | Introduction Apple: Pairing/Connecting | 5 Thrive-Compatible Hearing Aids Connectivity for Apple Devices In order to use the Thrive app, you must first pair your hearing aids with your iOS device. 1. Ensure Bluetooth® setting is enabled on your iOS device. Within the Settings Power Plus BTE 13 BTE R RIC R RIC 312 mRIC 312 ITE R ITC/HS R CIC BTE 13 menu go to Bluetooth and toggle to On. -

User Manual Sm-R323
USER MANUAL SM-R323 Printed in Korea GH68-46732A Rev.1.1 English (EU). 08/2016 About the Gear VR The Samsung Gear VR allows you to enjoy 2D, 3D, and 360-degree content by connecting it with your mobile device. You can also view webpages and your own 360-degree images or videos. Connect other devices, such as game controllers or Bluetooth headsets (sold separately), to the mobile device for a more immersive experience. Table of Contents About the Gear VR Basics 31 Using the touchpad 33 Moving the pointer or the Read me first screen 34 Selecting items Getting started 34 Using the Universal menu 7 Package contents 37 Downloading apps and 8 Device layout content 13 Connecting the mobile 38 Viewing notifications device and wearing the Gear received on the mobile VR device 28 Installing the Gear VR app (Oculus) 3 Table of Contents Viewing content 40 Viewing content on the Oculus Home screen 44 Viewing content on the mobile device 45 Viewing online content Health and safety warnings Safety information Appendix 66 Troubleshooting 4 Read me first • Please read this manual before using the Samsung Gear VR (also referred to as Gear VR) to ensure safe and proper use. • To prevent injury or damage to your devices, read the health and safety warnings and information before using the Gear VR. • Use the Gear VR for its intended purpose only. Using the Gear VR for other purposes may result in injury. • The Gear VR cannot be operated by itself. To use the Gear VR, connect a mobile device to it. -

Using Google Cardboard to Perform a Visual Field Screening Test Dhanraj Selvaraj Iowa State University
Iowa State University Capstones, Theses and Graduate Theses and Dissertations Dissertations 2018 Using Google Cardboard to perform a visual field screening test Dhanraj Selvaraj Iowa State University Follow this and additional works at: https://lib.dr.iastate.edu/etd Part of the Engineering Commons Recommended Citation Selvaraj, Dhanraj, "Using Google Cardboard to perform a visual field screening test" (2018). Graduate Theses and Dissertations. 16461. https://lib.dr.iastate.edu/etd/16461 This Thesis is brought to you for free and open access by the Iowa State University Capstones, Theses and Dissertations at Iowa State University Digital Repository. It has been accepted for inclusion in Graduate Theses and Dissertations by an authorized administrator of Iowa State University Digital Repository. For more information, please contact [email protected]. Using Google Cardboard to perform a visual field screening test by Dhanraj Selvaraj A thesis submitted to the graduate faculty in partial fulfillment of the requirements for the degree of MASTER OF SCIENCE Major: Mechanical Engineering Program of Study Committee: Greg Luecke, Major Professor Judy Vance Stephen Gilbert The student author, whose presentation of the scholarship herein was approved by the program of study committee, is solely responsible for the content of this thesis. The Graduate College will ensure this thesis is globally accessible and will not permit alterations after a degree is conferred. Iowa State University Ames, Iowa 2018 Copyright © Dhanraj Selvaraj, 2018. All rights reserved. ii DEDICATION I dedicate this thesis to my parents, Dr. Eunice Selvaraj and Dr. Selvaraj Rajendran, and my sister, Suganthi Selvaraj for their constant support, encouragement, devotion to my dreams and ambition to become an engineer. -

Oculus Go Reviewer's Guide
Oculus Go Reviewer's Guide Welcome to Oculus Go. The easiest way to jump into VR, for just $199. Oculus Go is an all-new standalone headset that doesn't require you to snap in a phone, attach a cable or power up a PC. Oculus Go is hands-down the easiest way for people to get into VR. It's perfect for those who haven't experienced VR to play games, watch movies and connect with friends and family in new ways. It provides next-gen optics, crisp audio and 1000+ VR experiences. SETTING UP OCULUS GO Install the Oculus App: Since you are reviewing Oculus Go before the companion app has officially launched, you'll be downloading a pre-launch version: iPhone Users: you will receive an email from TestFlight with detailed instructions. Android Users: you will receive an email from the Oculus Beta Testers Google Group with relevant instructions. The Oculus App will take you through the set-up process, step by step. Here's a quick overview: Plug In Your Oculus Go: Connect your headset to a power source (micro USB on the left- hand side of the device). Press the power button - a white LED will turn on. The headset will have some battery power, but you may want to plug it in while you go through the startup process. When your device is fully charged, the LED will be green. Connect Your Oculus Go: The Oculus App will walk you through how to connect to WiFi and your phone (via Bluetooth). Set Up Your Controller: Insert the AA battery (included in the box) into the controller. -

How the Design of Youtube Influences User Sense of Agency
How the Design of YouTube Influences User Sense of Agency Kai Lukoff Ulrik lyngs Himanshu Zade University of Washington University of Oxford University of Washington [email protected] [email protected] [email protected] J. Vera Liao James Choi Kaiyue Fan University of Washington University of Washington University of Washington [email protected] [email protected] [email protected] Sean A. Munson Alexis Hiniker University of Washington University of Washington [email protected] [email protected] ABSTRACT 1 INTRODUCTION In the attention economy, video apps employ design mechanisms “At Netflix, we are competing for our customers’ time, so our competi- like autoplay that exploit psychological vulnerabilities to maximize tors include Snapchat, YouTube, sleep, etc.” watch time. Consequently, many people feel a lack of agency over - Reed Hastings, Netflix CEO [118, p.50] their app use, which is linked to negative life effects such as loss of sleep. Prior design research has innovated external mechanisms In the attention economy, social media apps employ a variety of that police multiple apps, such as lockout timers. In this work, design mechanisms–such as eye-catching notification icons, tempt- we shift the focus to how the internal mechanisms of an app can ing clickbait, and never-ending autoplay–to maximize their share support user agency, taking the popular YouTube mobile app as of the user’s time. In this pursuit, designers and tech industry in- a test case. From a survey of 120 U.S. users, we find that autoplay siders warn that many of these mechanisms exploit psychological and recommendations primarily undermine sense of agency, while vulnerabilities and harm the interests of the user [18, 63]. -

Kit Contents
Virtual Reality Kit Contents Kit Contents 1 OculusGO VR headset in a black case. Oculus Go Standalone Virtual Reality Headset - 32GB goggles Remote control 2 Spare AA rechargeable batteries in a mini zipper bag 10 foot USB cable and USB wall plug adapter. 1 Google Cardboard VR Headset 1 Onn plastic smartphone VR Headset, Blue or Pink Laminated instruction manual 1 SteelSeries Stratus Duo Wireless Gaming Controller 1 iPad Mini 2 - 16GB 1 Apple USB charger cord 1 Apple wall plug adapter 1 Laminated sheet: Casting to the iPad Mini 1 Black 3 ring binder Black USB flash drive 7 laminated VR activities menus 1 laminated Oculus Go VR warnings notice Technology How-To Guide spiral-bound booklet - glossy card VR in Libraries spiral-bound booklet Keep Talking and Nobody Explodes: Bomb Defusal Manual spiral-bound booklet Clipboard Feedback form Plastic zippered bag with cleaning supplies: Clorox wipes Purell wipes Anti-static screen cleaners Grey screen cleaning micro cloth Introduction - 1 Virtual Reality Resource Kit ─ Introduction Virtual reality (VR) is defined as the computer-generated simulation of images or whole environments that can be experienced using special electronic equipment. Traditional virtual reality creates environments, allowing people to be “present” in that alternative environment. Content is consumed and experienced from a viewer-centric perspective. Augmented reality (AR) starts with the real world, usually as seen through a camera or seeming clear glasses, and overlays virtual objects and information. The game Pokemon Go is a good example of this. Spherical, immersive, or 360-degree video is a video that captures an entire scene in which the viewer can look up, down, and around.