Index.Indd 391 I N D E X
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

What Are the Problems with Embedded Linux?
What Are the Problems with Embedded Linux? Every Operating System Has Benefits and Drawbacks Linux is ubiquitous. It runs most internet servers, is inside Android* smartphones, and is used on millions of embedded systems that, in the past, ran Real-Time Operating Systems (RTOSes). Linux can (and should) be used were possible for embedded projects, but while it gives you extreme choice, it also presents the risk of extreme complexity. What, then, are the trade-offs between embedded Linux and an RTOS? In this article, we cover some key considerations when evaluating Linux for a new development: ■ Design your system architecture first ■ What is Linux? ■ Linux vs. RTOSes ■ Free software is about liberty—not price ■ How much does Embedded Linux cost? ■ Why pay for Embedded Linux? ■ Should you buy Embedded Linux or roll-your-own (RYO)? ■ To fork or not to fork? ■ Software patching ■ Open source licensing ■ Making an informed decision The important thing is not whether Linux or an RTOS is “the best,” but whether either operating system—or both together—makes the most technical and financial sense for your project. We hope this article helps you make an informed decision. Design Your System Architecture First It is important to design your system architecture first—before choosing either Linux or an RTOS—because both choices can limit architectural freedom. You may discover that aspects of your design require neither Linux nor an RTOS, making your design a strong candidate for a heterogeneous approach that includes one or more bare-metal environments (with possibly a Linux and/or RTOS environment as well). -

Virtual Machine Technologies and Their Application in the Delivery of ICT
Virtual Machine Technologies and Their Application In The Delivery Of ICT William McEwan accq.ac.nz n Christchurch Polytechnic Institute of Technology Christchurch, New Zealand [email protected] ABSTRACT related areas - a virtual machine or network of virtual machines can be specially configured, allowing an Virtual Machine (VM) technology was first ordinary user supervisor rights, and it can be tested implemented and developed by IBM to destruction without any adverse effect on the corporation in the early 1960's as a underlying host system. mechanism for providing multi-user facilities This paper hopes to also illustrate how VM in a secure mainframe computing configurations can greatly reduce our dependency on environment. In recent years the power of special purpose, complex, and expensive laboratory personal computers has resulted in renewed setups. It also suggests the important additional role interest in the technology. This paper begins that VM and VNL is likely to play in offering hands-on by describing the development of VM. It practical experience to students in a distance e- discusses the different approaches by which learning environment. a VM can be implemented, and it briefly considers the advantages and disadvantages Keywords: Virtual Machines, operating systems, of each approach. VM technology has proven networks, e-learning, infrastructure, server hosting. to be extremely useful in facilitating the Annual NACCQ, Hamilton New Zealand July, 2002 www. Annual NACCQ, Hamilton New Zealand July, teaching of multiple operating systems. It th offers an alternative to the traditional 1. INTRODUCTION approaches of using complex combinations Virtual Machine (VM) technology is not new. It was of specially prepared and configured OS implemented on mainframe computing systems by the images installed via the network or installed IBM Corporation in the early 1960’s (Varian 1997 pp permanently on multiple partitions or on 3-25, Gribben 1989 p.2, Thornton 2000 p.3, Sugarman multiple physical hard drives. -

CASE STUDY Userful Multiplier and Win4lin Pro Reduce Costs of Point
CASE STUDY TM Userful Multiplier and Win4Lin Pro Reduce Costs of Point-of-Sale Terminals A Case Study by Omni Technology Solutions, leverage the Linux Desktop, he recommended the Userful a Userful Partner Multiplier*, a software add-on that allows multiple users to share a single computer. Win4Lin Pro Desktop was installed to allow Birchwood to run Simply Accounting on Linux. “Userful Multiplier* cut the hardware DOSEMU, which comes bundled with SUSE Linux, handled costs in half and Win4Lin Pro Desktop the DOS-based Framer’s Assistant point-of-sale application provided Windows compatibility to run quite nicely. their Simply Accounting package.” “Birchwood Art Gallery was always running into virus and - Mike Ducharme, spyware infections when they were using Windows 98 and IT consultant, Windows XP. Even with up-to-date anti-virus and anti- Birchwood Art Gallery spyware software, the systems were still getting major infections on a monthly basis, resulting in costly down-time Overview until they were cleaned up,” said Mr. Ducharme. “The security of Novell’s SUSE Linux Desktop provides peace of mind to Birchwood Art Gallery - based in Winnipeg, Canada - their staff,” continued Ducharme, “allowing them to carry out specializes in fine art reproductions and original artwork their work activities without fear of virus or spyware infesta- by a wide range of Canadian and international artists. On tion. Additionally, the Userful Multiplier* cut the hardware their web site and in their gallery, you will find artwork, costs in half and Win4Lin Pro Desktop provided Windows sculptures, prints and books from hundreds of artists. Lyn compatibility to run their Simply Accounting package.” Chercoe and Carole Solmundson, Birchwood Art Gallery’s owners, have earned a reputation for customer service The Results excellence since 1993 and sell art online all over the world. -

Openprinting Plenary
OpenPrinting Plenary Till Kamppeter, OpenPrinting IPP Everywhere under Linux – Driverless Printing · Support completely implemented: cups-filters: gstoraster/pdftoraster turns PDF into PWG Raster to send to IPP Everywhere printer, rastertopdf accepts PWG Raster as input for CUPS queue to emulate IPP Everywhere printer cups-browsed: If activated IPP Everywhere printers are discovered and a queue auto-generated, even with PPD file (PPD generator taken from CUPS 2.1.x, experimental) Ghostscript: PWG Raster format can be generated via “pwgraster” device or via “cups” device and MediaClass “PwgRaster” Printing stack of Level 2 is enough · Ubuntu Vivid (15.04) contains all this and therefore should fully support IPP Everywhere · Backport to Ubuntu Trusty (14.04 LTS) planned, but we need testing by manufacturers first · NEEDED: Testing all this by printer manufacturers, so please take Ubuntu 15.04 and test with your printers 2 Mobile Printing · Printing stack ready for mobile: cupsd and cups-browsed can be run on-demand, with systemd (most modern distros, incl. Ubuntu 15.04) or Upstart (Ubuntu Phone) Packaging of printing stack in three levels, level 2 for mobile, level 3 for desktop, server can be level 2 (appliance) or level 3 (computer) Printing stack is same software for mobile and desktop, so convergence (connect mobile phone to monitor to get desktop) is easy · MISSING: Mobile print dialog, but will be implemented soon for Ubuntu Mobile · Nice to have: Lightweight renderer like MuPDF 3 cups-filters · Most important changes: Create -

Linux Games Page 1 of 7
Linux Games Page 1 of 7 Linux Games INTRODUCTION such as the number of players and the size of the map, then you start the game. Once the game is running clients may Hello. My name is Andrew Howlett. I've been using Linux join the game. Clients connect to the game using TCP/IP, since 1997. In 2000 I cutover to Linux for all my projects, so it is very easy to play multi-player games over the except I dual-booted Windows to play games. I like to play Internet. Like many Free games, clients are available for computer games. About a year ago I stopped dual booting. many platforms, including Windows, Amiga and Now I play computer games under Linux. The games I Macintosh. So there are lots of players out there. If you play can be divided into four groups: Free Games, native don't want to play against other humans, then Freeciv linux commercial games, Windows Emulated games, and includes some nasty AIs. Win4Lin enabled games. This presentation will demonstrate games from each of these four groups. BZFlag Platform BZFlag is a tank combat game along the same lines as the old BattleZone game. Like FreeCiv, BZFlag uses a client/ Before I get started, a little bit about my setup so you can server architecture over TCP/IP networks. Unlike FreeCiv, relate this to whatever you are running. This is a P3 900 the game contains no AIs – you must play this game MHz machine. It has a Crystal Sound 4600 sound card and against other humans (? entities ?) over the Internet. -

Happy Birthday Linux
25 Jahre Linux! Am Anfang war der Quellcode Entstehungsgeschichte und Werdegang von Linux Entwicklung und Diversifizierung der Distributionen Der Wert von Linux oder: „Wat nix kost, dat is och nix.“ Andreas Klein ORR 2016 1 Am Anfang war der Quellcode (70er) ● 1969, Ken Thompson u. Dennis Ritchie erstellen die erste Version von Unix in Assembler. ● Von 1969-1971 entwickeln sie gemeinsam die Programmiersprache B. ● Ab 1971 erweiterte in erster Linie Dennis Ritchie B, um weitere Elemente und nannte sie Anfangs NB (new B). ● 1973 waren die Erweiterungen soweit gediehen, das er die stark verbesserte Sprache C nannte (Brian W. Kernighan hat ebenfalls maßgeblich dazu beigetragen). //Unix=25 PCs ● Bis 1974 war das gesamte Betriebssystem UNIX vollständig in C implementiert und wurde mit einem C-Compiler kostenfrei an verschiedene Universitäten verteilt. ● 1978 wurden bereits über 600 Computer mit dem UNIX-Betriebssystemen betrieben. ● Das aufblühende Zeitalter der Computerisierung der 70er Jahre war geprägt vom regen und freien Austausch von Programmen und dessen zugrunde liegenden Ideen. Sinnvoller Weise tauschte man diese als Quellcode untereinander aus. ● 1979 wurde von AT&T die letzte UNIX-Version 7, mit freiem Quellcode veröffentlicht. Andreas Klein ORR 2016 2 Am Anfang war der Quellcode (80er) ● 1980 – 1983 AT&T sowie zahlreiche andere Unternehmen beginnen mit der Kommerzialisierung von UNIX, durch Koppelung an stark beschränkenden Lizenzen und Geheimhaltung des zugrunde liegenden Quelltextes. ● Richard Stallman kündigt am 27. September 1983 in den Newsgroups net.unix-wizards und net.usoft das GNU-Projekt an. ● Am 5. Januar 1984 begann Stallman offiziell mit der Arbeit am GNU-Projekt, nachdem er seine Stelle am MIT gekündigt hatte. -
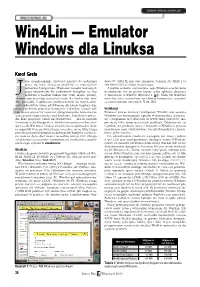
Win4lin — Emulator Windows Dla Linuksa
Win4Lin — Emulator Windows dla Linuksa Karol Grela ako chemik−organik, używający Linuksa do codziennej dows 95 OSR2 PL mój stary komputer Pentium 233 MMX z 64 pracy, nie mam zazwyczaj problemu ze znalezieniem MB RAM−u był aż nadto wystarczający. potrzebnych programów. Większość narzędzi tworzonych Z punktu widzenia użytkownika, sesja Windows uruchomiona przez naukowców dla naukowców kompiluje się bez w emulatorze jest po prostu jeszcze jedną aplikacją działającą problemu w każdym Uniksie (np. VMD, mopac, platon), w środowisku X Window (Rysunek 1, [8a]). Okno MS Windows a komercyjne posiadają zazwyczaj wersje dla Linuksa (np. mol− może być także wyświetlone na zdalnym komputerze, za pomo− den, pcmodel). Z aplikacjami przeznaczonymi dla innych syste− cą mechanizmów sieciowych X−ów [8b]. mów uniksowych, takimi jak XWinnmr dla Silicon Graphics, daje się bez problemu pracować w systemie X Window. Czasem jed− Instalacja nak muszę używać lub testować oprogramowanie, które nie po− Ponieważ proces instalacji i konfiguracji Win4Lin oraz systemu siada jeszcze odpowiednika pod Linuksem. Dodatkowo prowa− Windows jest wyczerpująco opisany w dokumentacji dostarcza− dzę kilka projektów, takich jak ChemPerfect — zestaw narzędzi nej z programem oraz dostępnej na WWW firmy TreLOS [5], sku− chemicznych do Wordperfecta. Projekt ten rozwijam w dwu wer− pię się na kilku mniej oczywistych punktach. Zakładam też, że sjach — dla Windows i Linuksa. Czasem muszę wprowadzić drob− Czytelnik zna podstawy pracy z Linuksem (i Windows), posiada ne poprawki w tej pierwszej wersji, a nie chce mi się tylko z tego uprawnienia roota i (ewentualnie) wie jak skompilować i zainsta− powodu restartować komputera i ładować MS Windows. Co więcej, lować jądro systemu. -

Sysvinit / Upstart / Systemd
SysVinit / Upstart / Systemd Zahemszky Gábor mérnök tanácsadó Zahemszky Gábor SysVinit / Upstart / Systemd init? ● Mire jó? ● Mire nem jó? ● Mi lenne, ha … (kávét főzne, kitakarítana, betakarítana, észlelné a bekapcsolt BT-fejhallgatót, a bedugot mobildiszket ...) Zahemszky Gábor SysVinit / Upstart / Systemd Ki mit használ jelenleg? Debian SysVinit Fedora Systemd OpenSUSE Systemd RHEL5 SysVinit RHEL6 Upstart SLES 10/11 SysVinit Ubuntu Upstart Többi? Kit érdekel? SysVinit Zahemszky Gábor SysVinit / Upstart / Systemd Előnyei ● Egyszerű maga az eszköz ● Egyszerűek az elindítot parancsfájlok ● Egyszerű a használt könyvtárstruktúra Zahemszky Gábor SysVinit / Upstart / Systemd Hátrányai ● Nem is annyira egyszerűek a parancsfájlok ● Mi van, ha az elindítot szerviz meghal? ● Miért fusson minden mindig, akkor is, ha csak ritkán akarjuk használni? Zahemszky Gábor SysVinit / Upstart / Systemd Mi a megoldás a problémákra? ● Bonyolítsuk el az egyszerű programot! ● Dobjuk ki az egyszerű scripteket! ● Strukturáljuk át az ismert, szabványosítot (LFS FHS) felépítésű fájlrendszert! Upstart Zahemszky Gábor SysVinit / Upstart / Systemd Upstart ● „Eseményvezérelt init-helyetesítő, amelynél a feladatok (task) és szolgáltatások (service) események (event) hatására indulnak el és állnak le” (*) ● Ellenben a feladatok és események elindítása / leállása más eseményeket generálhat ● Un. job segítségével mondhatjuk meg mi, merre, hány méter (mi, hogyan induljon/álljon le) ● Vezérlésre az initctl parancs szolgál (*) lásd upstart.ubuntu.com Zahemszky Gábor SysVinit -

Nixos: a Purely Functional Linux Distribution
NixOS: A Purely Functional Linux Distribution Eelco Dolstra Andres Loh¨ Delft University of Technology, The Netherlands Utrecht University, The Netherlands [email protected] [email protected] Abstract change after they have been built; rather, the system is updated to Existing package and system configuration management tools suf- a new configuration by changing the specification and rebuilding fer from an imperative model, where system administration actions the system from it. This allows a system to be built determinis- such as upgrading packages or changes to system configuration tically, and therefore reproducibly. It allows the user to roll back files are stateful: they destructively update the state of the sys- the system to previous configurations, since previous configura- tem. This leads to many problems, such as the inability to roll back tions are not overwritten. Perhaps most importantly, statelessness changes easily, to run multiple versions of a package side-by-side, makes configuration actions predictable: they do not mysteriously to reproduce a configuration deterministically on another machine, fail because of some unknown aspect of the state of the system. or to reliably upgrade a system. In this paper we show that we can We have previously shown how package management — the overcome these problems by moving to a purely functional system installation and management of software packages — can be done configuration model. This means that all static parts of a system in a purely functional way, in contrast to the imperative models (such as software packages, configuration files and system startup of conventional tools such as RPM (Foster-Johnson 2003). -

Crossover Compared to Competing Emulation Solutions
CrossOver Compared to Competing Emulation Solutions CrossOver Compared to Competing Emulation Solutions CrossOver Compared to Competing Emulation Solutions Overview: Whether you’re running a Linux or Mac OS X machine, chances are you need a way to run at least some Windows applications or games that aren’t available on your platform of choice. And you have your choice of potential solutions to this problem. This page illustrates some of the key Every Windows advantages that CrossOver has in relation to the compatibility solution has other compatibility solutions. pros and cons. When presented with the need to run Windows applications on a Mac or Linux machine, you have basically three main choices: Dual-booting: running two separate operating systems on one PC, and switching between them as needed by rebooting. Applications such as Apple’s Bootcamp allow this to occur on a Mac OS X machine, for example. Running a virtual machine: Emulation products such as VMWare and Parallels allow you to install a copy of Windows within a logical partition within your native operating system. The Windows applications essentially run in a separate “box within a box.” Running Wine or CrossOver: Unlike emulation, Wine is a re-implementation of the Win32 API, allowing applications to run as if natively on the target OS. CrossOver is a commercialized version of Wine. Each solution has its advantages and disadvantages. This document is provided to help identify and evaluate key points of comparison between CodeWeavers’ CrossOver products and some of its key competitors. Technology Approach General Approach Dual-booting is exactly what it sounds like—shutting down one operating system, starting another, and dealing with the file transfer issues associated with same. -

An Empirical Study Into the Security Exposure to Hosts of Hostile Virtualized Environments
An Empirical Study into the Security Exposure to Hosts of Hostile Virtualized Environments Tavis Ormandy [email protected] Google, Inc. Abstract machine monitor is ‘root secure’[25], meaning that no level of As virtual machines become increasingly commonplace as privilege within the virtualized guest environment permits a method of separating hostile or hazardous code from com- interference with the host system. modity systems, the potential security exposure from imple- Detection mentation flaws has increased dramatically. This paper Detecting virtualized environments has been explored in investigates the state of popular virtual machine implementa- detail by other researchers[22]. Virtual machines employed in tions for x86 systems, employing a combination of source code malware analysis or honeypots should endeavour to be unde- auditing and blackbox random testing to assess the security tectable or risk changing the behaviour of the emulated code. exposure to the hosts of hostile virtualized environments. An emulated malware sample could choose to act benignly, Keywords for example, but when executed on a physical machine imme- virtualization, security, software testing diately performs some malicious action. Detection will not be considered any further in this paper, although being able to detect a virtual machine, or more spe- I. INTRODUCTION cifically, virtual machine implementation, may be a prerequi- Secure isolation is one of the fundamental concepts of vir- site for the more serious attacks investigated in this paper. tualization[15], confining a program to a virtualized environ- Without being able to identify which virtual machine imple- ment should guarantee that any action performed inside the mentation is present, an attacker would have difficulty deter- virtual machine cannot interfere with the system that hosts it1. -

Ubuntu Kung Fu.Pdf
Prepared exclusively for J.S. Ash Beta Book Agile publishing for agile developers The book you’re reading is still under development. As part of our Beta book program, we’re releasing this copy well before we normally would. That way you’ll be able to get this content a couple of months before it’s available in finished form, and we’ll get feedback to make the book even better. The idea is that everyone wins! Be warned. The book has not had a full technical edit, so it will con- tain errors. It has not been copyedited, so it will be full of typos and other weirdness. And there’s been no effort spent doing layout, so you’ll find bad page breaks, over-long lines with little black rectan- gles, incorrect hyphenations, and all the other ugly things that you wouldn’t expect to see in a finished book. We can’t be held liable if you use this book to try to create a spiffy application and you somehow end up with a strangely shaped farm implement instead. Despite all this, we think you’ll enjoy it! Throughout this process you’ll be able to download updated PDFs from your account on http://pragprog.com. When the book is finally ready, you’ll get the final version (and subsequent updates) from the same address. In the meantime, we’d appreciate you sending us your feedback on this book at http://books.pragprog.com/titles/ktuk/errata, or by using the links at the bottom of each page.