EIS Amendment May-21 at ACADEMY - MUMBAI 1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Oprogramowanie Klasy Erp Dystrybuowane Na Zasadach Licencji Open Source
OPROGRAMOWANIE KLASY ERP DYSTRYBUOWANE NA ZASADACH LICENCJI OPEN SOURCE Stanisław IWAN Streszczenie: Jedn ą z istotnych trudno ści, zwi ązanych z wykorzystywaniem technologii informacyjnych do wspomagania procesów zarz ądzania s ą wysokie koszty zwi ązane z opłatami licencyjnymi za oprogramowanie komputerowe. Mog ą one ulec znacznemu obni żeniu przy zastosowaniu alternatywnych metod dystrybuowania programów. W opracowaniu przedstawiono ogólne zało żenia licencji open source oraz wybrane przykłady systemów klasy ERP dystrybuowanych na jej zasadach. Słowa kluczowe: ERP, licencje oprogramowania, otwarte oprogramowanie, open source, technologie sieciowe. 1. Wprowadzenie Jedn ą z istotnych trudno ści, zwi ązanych z wykorzystywaniem technologii informacyjnych do wspomagania procesów zarz ądzania s ą wysokie koszty z tym zwi ązane. Cho ć znaczn ą ich cz ęść stanowi ą koszty zakupu i eksploatacji sprz ętu komputerowego, to jednak koszty zakupu licencji oprogramowania mog ą w wielu wypadkach (szczególnie w odniesieniu do mocno wyspecjalizowanych zada ń) stanowi ć element dominuj ący i niekiedy znacznie przewy ższa ć koszty sprz ętu. Dodatkowo firmy software’owe stosuj ą ró żne metody utrzymania klientów i zapewnienia sobie stałego dopływu opłat licencyjnych. Przykładem niechaj b ędą niektóre kontrowersyjne zapisy, zawarte w umowach licencyjnych jednego z producentów, mówi ące, że: − użytkownik nie jest wła ścicielem oprogramowania, które zakupił; − użytkownik nie mo że uruchamia ć wi ęcej ni ż jednej kopii systemu; − system operacyjny stanowi cz ęść zestawu oprogramowanie-komputer, nie mo że zatem by ć u żytkowany na komputerze innym, ni ż ten na którym został zainstalowany i zarejestrowany po raz pierwszy; − producent nie ponosi odpowiedzialno ści za straty, jakie poniesie u żytkownik w skutek u żytkowania systemu (pomimo wysokich opłat licencyjnych). -

Facultad De Ingeniería Carrera Profesional De Ingeniería De Sistemas E Informática
UNIVERSIDAD PRIVADA DE TRUJILLO FACULTAD DE INGENIERÍA CARRERA PROFESIONAL DE INGENIERÍA DE SISTEMAS E INFORMÁTICA CRITERIOS DE EVALUACIÓN PARA LA SELECCIÓN DE UN SISTEMA ERP OPEN SOURCE PARA LA EMPRESA INVERSIONES AVÍCOLA GÉNESIS, TRUJILLO, 2020. TESIS PARA OPTAR EL TÍTULO PROFESIONAL DE INGENIERO DE SISTEMAS E INFORMÁTICA AUTOR: Bach. Kennedy Vidal Valverde Alvites ASESOR: Ing. José Alberto Gómez Ávila Trujillo – Perú 2021 CRITERIOS DE EVALUACIÓN PARA LA SELECCIÓN DE UN SISTEMA ERP OPEN SOURCE PARA LA EMPRESA INVERSIONES AVÍCOLA GÉNESIS, TRUJILLO, 2020. APROBACIÓN DE LA TESIS El asesor y los miembros del jurado evaluador asignados, APRUEBAN la tesis desarrollada por el Bachiller Kennedy Vidal Valverde Alvites, denominada: “CRITERIOS DE EVALUACIÓN PARA LA SELECCIÓN DE UN SISTEMA ERP OPEN SOURCE PARA LA EMPRESA INVERSIONES AVÍCOLA GÉNESIS, TRUJILLO, 2020” Dr. Gómez Ávila José Alberto PRESIDENTE Mg. Santos Fernández Juan Pedro SECRETARIO Mg. Díaz Díaz Franklin Alexis VOCAL VALVERDE ALVITES, KENNEDY VIDAL Pág. ii CRITERIOS DE EVALUACIÓN PARA LA SELECCIÓN DE UN SISTEMA ERP OPEN SOURCE PARA LA EMPRESA INVERSIONES AVÍCOLA GÉNESIS, TRUJILLO, 2020. DEDICATORIA A Dios todopoderoso, creador de los cielos y la tierra, el Alfa y la Omega, el que es y que era y que ha de venir. A mi padre Vidal y a mi madre Alvina, con mucho amor. A mis hermanos Joel, Benony, Paúl, Rafael y mi hermana Jackelyne, en mis alegrías y tristezas, con mucho cariño. VALVERDE ALVITES, KENNEDY VIDAL Pág. iii CRITERIOS DE EVALUACIÓN PARA LA SELECCIÓN DE UN SISTEMA ERP OPEN SOURCE PARA LA EMPRESA INVERSIONES AVÍCOLA GÉNESIS, TRUJILLO, 2020. AGRADECIMIENTO A mi Dios Eterno, por darme la vida, la sabiduría, por cuidarme y guiarme en sus caminos. -

An In-Depth Review of Enterprise Resource Planning ERP System Overview, Methodology & List of Software Options Contents
An In-Depth Review of Enterprise Resource Planning ERP System Overview, Methodology & List of Software Options Contents 1 Enterprise resource planning 1 1.1 Origin ................................................. 1 1.2 Expansion ............................................... 1 1.3 Characteristics ............................................. 2 1.4 Functional areas of ERP ........................................ 2 1.5 Components .............................................. 2 1.6 Best practices ............................................. 2 1.7 Connectivity to plant floor information ................................ 3 1.8 Implementation ............................................ 3 1.8.1 Process preparation ...................................... 3 1.8.2 Configuration ......................................... 3 1.8.3 Two tier enterprise resource planning ............................. 4 1.8.4 Customization ......................................... 4 1.8.5 Extensions ........................................... 5 1.8.6 Data migration ........................................ 5 1.9 Comparison to special–purpose applications ............................. 5 1.9.1 Advantages .......................................... 5 1.9.2 Benefits ............................................ 5 1.9.3 Disadvantages ......................................... 6 1.10 See also ................................................ 6 1.11 References ............................................... 6 1.12 Bibliography .............................................. 8 1.13 -

Kartoitus Avoimen Lähdekoodin Toiminnanohjausjärjestelmistä
KARTOITUS AVOIMEN LÄHDEKOODIN TOIMINNANOHJAUSJÄRJESTELMISTÄ Pilvi Tontti Opinnäytetyö Maaliskuu 2017 Liiketalouden koulutusohjelma TIIVISTELMÄ Tampereen ammattikorkeakoulu Liiketalouden koulutusohjelma PILVI TONTTI Kartoitus avoimen lähdekoodin toiminnanohjausjärjestelmistä Opinnäytetyö 60 sivua, joista liitteitä 17 sivua Maaliskuu 2017 Sähköisen kaupankäynnin ja tiedonsiirron yleistyttyä on liiketoiminnan sähköisten työ- kalujen käyttö lisääntynyt. Toiminnanohjausjärjestelmät ovat yksi esimerkki edellä mainituista ohjelmistoista. Ne ovat käytössä useilla eri toimialoilla. Usein pieni organi- saatio ei voi hankkia järjestelmää suurten kustannusten takia. Avoimen lähdekoodin ratkaisut ovat lisänneet kilpailuetuaan markkinoilla suljettuihin ohjelmistoihin nähden edullisuutensa ja yhteisö-ideologiansa ansiosta. Yhdistämällä yhteisökehityksen edut ja toiminnanohjaus luodaan pienellekin toimijalle mahdollisuus hankkia järjestelmä. Opinnäytetyö tehdään Suomen avoimien tietojärjestelmien keskukselle - COSS ry:lle. Yhdistyksen tarkoituksena on avoimen teknologian edistäminen ja avoimia ohjelmistoja tarjoavien jäsenyritystensä liiketoiminnan tukeminen. Opinnäytteessä keskityttiin tar- kastelemaan avoimen lähdekoodin ERP-järjestelmiä. Työn tavoitteena oli perehtyä avoimeen lähdekoodiin ja toiminnanohjausjärjestelmiin. Työn tarkoituksena oli tehdä kartoitus markkinoilla olevista avoimen lähdekoodin ERP-järjestelmistä sekä selvittää niiden ominaisuuksia. Avoimen lähdekoodin ERP-järjestelmiä on paljon tarjolla. Kartoituksessa selvisi, että suomalaisia -

Downloads O License: GNU Gplv3 O Has Proprietary Features: Yes
1.0 ﺑﺮﻧﺎﻣﺞ اﻟﺘﻌﺎﻣﻼت اﻟﻜﺘﺮوﻧﻴﺔ اﻟﺤﻜﻮﻣﻴﺔ ّ(ﻳﺴﺮ) 2019 ................................................................................................................................................. ................................................................................................................................ .............................................................................................................................................. ................................................................................................................................... ......................................................................................................................... CMS ..................................................................................................................... DMS ................................................................................................................ .................................................................................................................................... ........................ ...................................................................................................... ............................................................................................. ................................................................................................................. ........................................................................................................................... ...................................................................................................................................... -

Enterprise Open Source Platforms
SEA - Practical Application of Science Volume I, Issue 1 (1), 2013 Bogdan MICU GHILIC George STANCU ADAPTING OPEN-SOURCE SOFTWARE FOR ENTERPRISE Keywords Open-source Software enterprise CRM ERP OFBIZ JEL classification M15 Abstract Low developed companies do not use ERP solutions for resource management, they don't have CRM systems for tracking customers, online presence is low and consequently they are selling low volumes. Their work does not generate enough capital to buy specialized software and the local community is too small to create open-source software for them. When adapting an open-source enterprise solution, from a certain level of integration, it is necessary to align to the Romanian legislation. For this you need more than a simple translation. For example, in accounting, the Romanian chart of accounts should be used, the local fiscal calendar, the rules of the Romanian legislation and the specific identifiers for Romanian companies. The solution: Open source applications can be localized. A small community cannot create complex system starting from nothing, but they can adapt existing ones already created and used all over the world. Given the individual characteristics of the Romanian market, open source ERP, CRM and e-commerce will be integrated by specialized consultancy agency in Romania just as is done in France (Compiere), Spain (Openbravo), Belgium (OpenERP) or the United States (Apache oFBiz). This will not generate license costs for the companies, only the expenses for hardware and implementation consultancy. If we can create a common infrastructure, hardware cost will be waived for cloud SaaS offering, in opposition with the on-premise option. -
Innovative Low Cost Open Source Business Intelligence Systems For
IJCST VOL . 5, Iss UE SPL - 2, JAN - MAR C H 2014 ISSN : 0976-8491 (Online) | ISSN : 2229-4333 (Print) Innovative Low Cost Open Source Business Intelligence Systems For MID Size Companies 1Priyabrata Nayak, 2Arabinda Tripathy, 3Manmathnath Das 1,2,3Gandhi Institute for Technology, Bhubaneswar, Odisha, India Abstract While BI is implemented to take decision quickly, it takes around BI is one of those buzz phrases that sound super- cool but are 18 months for data warehousing system to completely implement often misunderstood. Very small to very large companies use BI the system. [4] In today’s fast paced and unpredictable industrial to improve decision making, cut costs and identify new business scenario waiting with such patience just to watch the execution opportunities. BI converts data into useful information and through of BI seems difficult. human analysis to knowledge. Knowledge is power but spending Business intelligence environment requires a broader range a giant wad of money on fancy BI software won’t do any good. of specialized skills with necessary experience in toolsets and SAP, Oracle, IBM, Microsoft are some of the big names in BI methods. In addition, this range of knowledge and skills cannot with big price tags. These proprietary vendors sell BI systems as usually be found in a single person, and so a team of staff is fragmented products, buying all the pieces may prove to be overly required to provide a comprehensive and effective approach to expensive. On a feature by feature comparison open source BI business intelligence either physically or virtually. Hence arising tools can’t beat these leading closed source offering. -

Rep Itm Pre Gonzalez.Pdf (1.793Mb)
HERRAMIENTA LIBRE PARA LA TIENDA “LA ILUSIÓN” Mónica Cano Ramírez Zoraida González Londoño Ingeniería de Sistemas Diana Patricia Bedoya Ruiz INSTITUTO TECNOLÓGICO METROPOLITANO 13/07/2018 RESUMEN La tienda “La ilusión” es un proyecto comunitario que beneficia familias campesinas del Sur Oeste Antioqueño, quienes producen pequeñas cantidades de diferentes productos agroecológicos que necesitan comercializar para el sustento de sus familias. El objetivo de este proyecto es implantar una herramienta informática en Software libre que fortalezca el proceso administrativo de la tienda “La Ilusión” y que a su vez potencie el crecimiento de las familias campesinas. De acuerdo a la metodología Proceso Unificado UP, se debe definir un modelo de dominio del sistema y a partir de este los requisitos funcionales para llevar a cabo la diagramación de los casos de uso. Para una mejor comprensión de los procesos de inventario, compra y venta de productos agroecológicos se construye a representación de dichos procesos como diagramas de actividades, de forma tal que dieran claridad en los flujos de información necesarios en cada proceso, buscando proveer mayor seguridad a la información almacenada en el sistema se definen los perfiles de acceso y con miras a proporcionar una herramienta de fácil uso se hacen las adecuamos necesarias a las diferentes interfaces de usuario Después de analizar diferentes ERP libres, que permiten una adecuación para diferentes necesidades, se selecciona la herramienta Tryton, como software de base para la tienda “La Ilusión”, una vez finalizada la adecuación del ERP, se realiza la implantación y carga de datos que permitan a la tienda realizar pruebas de campo y verificar su funcionalidad, finalmente se realiza la capacitación a los integrantes de la tienda “La Ilusión”. -

Estudio De Factibilidad Para La Prestación De Software Erp Como Servicio Basado En Cloud Computing En La Pequeña Y Mediana Empresa De La Ciudad De Medellín
ESTUDIO DE FACTIBILIDAD PARA LA PRESTACIÓN DE SOFTWARE ERP COMO SERVICIO BASADO EN CLOUD COMPUTING EN LA PEQUEÑA Y MEDIANA EMPRESA DE LA CIUDAD DE MEDELLÍN Álvaro Zapata Ocaña Raúl Vergara Kerguelén MAESTRÍA EN ADMINISTRACIÓN ESCUELA DE ADMINISTRACIÓN UNIVERSIDAD EAFIT MEDELLÍN, 2014 1 ESTUDIO DE FACTIBILIDAD PARA LA PRESTACIÓN DE SOFTWARE ERP COMO SERVICIO BASADO EN CLOUD COMPUTING EN LA PEQUEÑA Y MEDIANA EMPRESA DE LA CIUDAD DE MEDELLÍN Álvaro Zapata Ocaña Raúl Vergara Kerguelén Trabajo de Grado para optar al Título de Maestría en Administración Asesor temático: Elkin Arcesio Gómez Salazar Asesor metodológico: Mónica Henao Cálad MAESTRÍA EN ADMINISTRACIÓN ESCUELA DE ADMINISTRACIÓN UNIVERSIDAD EAFIT MEDELLÍN, 2014 2 NOTA DE ACEPTACIÓN _______________________ _______________________ _______________________ _______________________ Medellín, noviembre de 2014 3 A mis hijos Andrés y Daniel, quienes son el motor de mi vida y que durante mis periodos de ausencia me ofrecieron su paciencia y comprensión. A mi esposa Diana por su amor, generosidad y sacrificio inspirador para ser día a día mejor, gracias por tu incondicional apoyo Alvaro Zapata O. A mi Esposa e Hija quienes fueron de gran apoyo para hacer realidad este Proyecto. Su sacrificio por el tiempo no compartido fueron la inspiración de este trabajo y permitieron llevarlo a feliz término. Raúl Vergara K. Agradecimientos Queremos agradecer de manera especial y sincera a todos los docentes que participaron en el proceso de formación de nuestra maestría y aquellas personas que colaboraron y ayudaron para la elaboración de este proyecto de grado. Agradecimientos especiales A Elkin Gómez Salazar y Mónica Henao Cálad. 4 Tabla de contenido 1. -
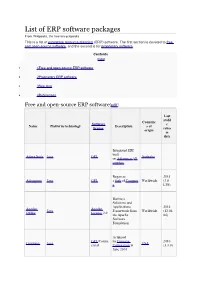
List of ERP Software Packages from Wikipedia, the Free Encyclopedia This Is a List of Enterprise Resource Planning (ERP) Software
List of ERP software packages From Wikipedia, the free encyclopedia This is a list of enterprise resource planning (ERP) software. The first section is devoted to free and open-source software, and the second is for proprietary software. Contents [hide] 1Free and open-source ERP software 2Proprietary ERP software 3See also 4References Free and open-source ERP software[edit] Last stabl Countrie Software e Name Platform technology Description s of license relea origin se date Integrated ERP built Adaxa Suite Java GPL Australia on Adempiere/iD empiere Began as 2015 Adempiere Java GPL a fork of Compier Worldwide (3.8 e LTS) Business Solutions and Applications 2014 Apache Apache Java Framework from Worldwide (12.04. OFBiz License 2.0 the Apache 04) Software Foundation Acquired GPL/Comm by Consona 2010 Compiere Java USA ercial Corporation in (3.3.0) June 2010 Last stabl Countrie Software e Name Platform technology Description s of license relea origin se date Web application (LAMP based system) to JavaScript, PHP, MySQL or manage small and 2015 Dolibarr GPLv3 France PostgreSQL medium (3.6.2) companies, foundations or freelancers A framework for building ERP/CRM Poland, US 2015 Epesi PHP, MySQL MIT license applications. A (1.7.0) Business Information Manager. Based on unified Python, JavaScript, Zope, M model for mid to 2014 ERP5 GPL Worldwide ariaDB or MySQL large size (5.5) organizations ERP for small 2014 ERPNEXT Python, JavaScript, MySQL GPL and medium-size India (4.1.0) businesses FrontAccou 2014 PHP, MySQL GPLv3 Web application ? nting -

Adaptive and Scalable Information Modeling to Enable Autonomous Decision Making for Real-Time Interoperable Factories
Adaptive and Scalable Information Modeling to Enable Autonomous Decision Making for Real-Time Interoperable Factories Adaptive und skalierbare Informationsmodellierung zur Erm¨oglichung autonomer Entscheidungsfindungsprozesse f¨urinteroperable, reaktive Fertigungen Von der Fakult¨atf¨ur Maschinenwesen der Rheinisch-Westf¨alischen Technischen Hochschule Aachen zur Erlangung des akademischen Grades eines Doktors der Ingenieurwissenschaften genehmigte Dissertation vorgelegt von Max Hoffmann Berichter: Univ.-Prof. Dr. rer. nat. Sabina Jeschke Univ.-Prof. Dr.-Ing. Birgit Vogel-Heuser Tag der m¨undlichen Pr¨ufung: 26. Juni 2017 Diese Dissertation ist auf den Internetseiten der Universit¨atsbibliothekonline verf¨ugbar. Acknowledgments This work was created as part of my employment at the Institute of Information Management in Mechanical Engineering (IMA) of the RWTH Aachen University throughout the past five years. During this time, I had the opportunity to work on exciting projects, talk to people of many different scientific backgrounds and learn a lot about various interesting topics. First of all, I would like to thank my colleagues who accompanied me along this journey to my Ph.D. thesis. Great thanks are dedicated to Prof. Dr.-Ing. Tobias Meisen, whose scientific advise was extremely helpful during the process of my scientific development and in the course of this work. I would like to thank my working colleagues from the Production Technology research group at the IMA for many enlightening conversations and their feedback in terms of my research. I also thank all further colleagues at the Cybernetics Lab IMA/ZLW & IfU at the RWTH Aachen University for making this institute to such a special place. Many thanks go to the various student coworkers, who spend days { and sometimes night shifts { in developing and finalizing programming code, applications or demonstration scenarios for the use-cases of this work. -

Financial and Accounting Systems Introduction
No.1 for CA/CWA & MEC/CEC MASTER MINDS 2. FINANCIAL AND ACCOUNTING SYSTEMS INTRODUCTION Q.No.1. What is a System? Define the terms INTEGRATED (ERP) and NON-INTEGRATED Systems? (A) 1. The word "system" can be explained as, "a set of detailed methods, procedures and routines created to carry out a specific activity, perform a duty, or solve a problem". 2. It is an organized, purposeful structure that consists of interrelated and interdependent elements (components, entities, factors, members, parts etc.). 3. All systems generally have - a) Inputs, outputs and feedback mechanisms, b) Maintain an internal steady-state despite a changing external environment, c) Have boundaries that are usually defined by the system observer. 4. An Integrated System that has combined different functions together in order to work as one entity and maintaining data in a centralized manner. Central database is the main characteristics of an integrated ERP system. 5. A Non-Integrated System is a system of maintaining data in a decentralized way. Each department shall maintain its own data separately and not in an integrated way. In case of non- integrated systems, separate database is maintained by each department separately. Q.No.2. Discuss the features of Master Data and Non-Master Data?(A) Every accounting systems stores data in two ways: Master Data and Non-Master Data 1. MASTER DATA: a) Relatively permanent data not expected to change frequently. b) Master data is generally not typed by the user, it is selected from the available list. c) Master data entry is usually done less frequently say once a year or when there is a need to update.