Installing Platform LSF on UNIX and Linux Chapter 1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Pcoip® Host Software for Linux User Guide
PCoIP® Host Software for Linux User Guide TER1104006 Issue 7 PCoIP® Host Software for Linux User Guide Teradici Corporation #101-4621 Canada Way, Burnaby, BC V5G 4X8 Canada phone +1.604.451.5800 fax +1.604.451.5818 www.teradici.com The information contained in this documentation represents the current view of Teradici Corporation as of the date of publication. Because Teradici must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Teradici, and Teradici cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. TERADICI MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Teradici Corporation. Teradici may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Teradici, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. Visit Notice of Intellectual Property Rights for more information. © 2000-2015 Teradici Corporation. All rights reserved. Teradici, PC-over-IP, and PCoIP are trademarks of Teradici Corporation and may be registered in the United States and/or other countries. -

AEDIT Text Editor Iii Notational Conventions This Manual Uses the Following Conventions: • Computer Input and Output Appear in This Font
Quick Contents Chapter 1. Introduction and Tutorial Chapter 2. The Editor Basics Chapter 3. Editing Commands Chapter 4. AEDIT Invocation Chapter 5. Macro Commands Chapter 6. AEDIT Variables Chapter 7. Calc Command Chapter 8. Advanced AEDIT Usage Chapter 9. Configuration Commands Appendix A. AEDIT Command Summary Appendix B. AEDIT Error Messages Appendix C. Summary of AEDIT Variables Appendix D. Configuring AEDIT for Other Terminals Appendix E. ASCII Codes Index AEDIT Text Editor iii Notational Conventions This manual uses the following conventions: • Computer input and output appear in this font. • Command names appear in this font. ✏ Note Notes indicate important information. iv Contents 1 Introduction and Tutorial AEDIT Tutorial ............................................................................................... 2 Activating the Editor ................................................................................ 2 Entering, Changing, and Deleting Text .................................................... 3 Copying Text............................................................................................ 5 Using the Other Command....................................................................... 5 Exiting the Editor ..................................................................................... 6 2 The Editor Basics Keyboard ......................................................................................................... 8 AEDIT Display Format .................................................................................. -

IBM Explorer for Z/OS: Host Configuration Reference Guide RSE Daemon and Thread Pool Logging
IBM Explorer for z/OS IBM Host Configuration Reference Guide SC27-8438-02 IBM Explorer for z/OS IBM Host Configuration Reference Guide SC27-8438-02 Note Before using this information, be sure to read the general information under “Notices” on page 175. Third edition (September, 2017) This edition applies to IBM Explorer for z/OS Version 3.1.1 (program number 5655-EX1) and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright IBM Corporation 2017. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures .............. vii Certificate Authority (CA) validation ..... 24 (Optional) Query a Certificate Revocation List Tables ............... ix (CRL) ............... 25 Authentication by your security software ... 25 Authentication by RSE daemon....... 26 About this document ......... xi Port Of Entry (POE) checking ........ 27 Who should use this document ........ xi Altering client functions .......... 27 Description of the document content ...... xi OFF.REMOTECOPY.MVS ......... 28 Understanding z/OS Explorer ....... xii Push-to-client developer groups ....... 28 Security considerations ......... xii Send message security........... 30 TCP/IP considerations ......... xii Log file security ............. 31 WLM considerations .......... xii UNIXPRIV class permits.......... 32 Tuning considerations .......... xii BPX.SUPERUSER profile permit ....... 33 Performance considerations ........ xii UID 0 ............... 33 Push-to-client considerations ....... xii Miscellaneous information ......... 33 User exit considerations ......... xii GATE trashing ............ 33 Customizing the TSO environment ..... xiii Managed ACEE ............ 33 Troubleshooting configuration problems ... xiii ACEE caching ............ 34 Setting up encrypted communication and X.509 TCP/IP port reservation ......... 34 authentication ............ xiii z/OS Explorer configuration files ....... 34 Setting up TCP/IP........... xiii JES Job Monitor - FEJJCNFG....... -

Reconfigurable Embedded Control Systems: Problems and Solutions
RECONFIGURABLE EMBEDDED CONTROL SYSTEMS: PROBLEMS AND SOLUTIONS By Dr.rer.nat.Habil. Mohamed Khalgui ⃝c Copyright by Dr.rer.nat.Habil. Mohamed Khalgui, 2012 v Martin Luther University, Germany Research Manuscript for Habilitation Diploma in Computer Science 1. Reviewer: Prof.Dr. Hans-Michael Hanisch, Martin Luther University, Germany, 2. Reviewer: Prof.Dr. Georg Frey, Saarland University, Germany, 3. Reviewer: Prof.Dr. Wolf Zimmermann, Martin Luther University, Germany, Day of the defense: Monday January 23rd 2012, Table of Contents Table of Contents vi English Abstract x German Abstract xi English Keywords xii German Keywords xiii Acknowledgements xiv Dedicate xv 1 General Introduction 1 2 Embedded Architectures: Overview on Hardware and Operating Systems 3 2.1 Embedded Hardware Components . 3 2.1.1 Microcontrollers . 3 2.1.2 Digital Signal Processors (DSP): . 4 2.1.3 System on Chip (SoC): . 5 2.1.4 Programmable Logic Controllers (PLC): . 6 2.2 Real-Time Embedded Operating Systems (RTOS) . 8 2.2.1 QNX . 9 2.2.2 RTLinux . 9 2.2.3 VxWorks . 9 2.2.4 Windows CE . 10 2.3 Known Embedded Software Solutions . 11 2.3.1 Simple Control Loop . 12 2.3.2 Interrupt Controlled System . 12 2.3.3 Cooperative Multitasking . 12 2.3.4 Preemptive Multitasking or Multi-Threading . 12 2.3.5 Microkernels . 13 2.3.6 Monolithic Kernels . 13 2.3.7 Additional Software Components: . 13 2.4 Conclusion . 14 3 Embedded Systems: Overview on Software Components 15 3.1 Basic Concepts of Components . 15 3.2 Architecture Description Languages . 17 3.2.1 Acme Language . -

Text Editing in UNIX: an Introduction to Vi and Editing
Text Editing in UNIX A short introduction to vi, pico, and gedit Copyright 20062009 Stewart Weiss About UNIX editors There are two types of text editors in UNIX: those that run in terminal windows, called text mode editors, and those that are graphical, with menus and mouse pointers. The latter require a windowing system, usually X Windows, to run. If you are remotely logged into UNIX, say through SSH, then you should use a text mode editor. It is possible to use a graphical editor, but it will be much slower to use. I will explain more about that later. 2 CSci 132 Practical UNIX with Perl Text mode editors The three text mode editors of choice in UNIX are vi, emacs, and pico (really nano, to be explained later.) vi is the original editor; it is very fast, easy to use, and available on virtually every UNIX system. The vi commands are the same as those of the sed filter as well as several other common UNIX tools. emacs is a very powerful editor, but it takes more effort to learn how to use it. pico is the easiest editor to learn, and the least powerful. pico was part of the Pine email client; nano is a clone of pico. 3 CSci 132 Practical UNIX with Perl What these slides contain These slides concentrate on vi because it is very fast and always available. Although the set of commands is very cryptic, by learning a small subset of the commands, you can edit text very quickly. What follows is an outline of the basic concepts that define vi. -

1. Run Nslookup to Obtain the IP Address of a Web Server in Europe
1. Run nslookup to obtain the IP address of a Web server in Europe. frigate:Desktop drb$ nslookup home.web.cern.ch Server: 130.215.32.18 Address: 130.215.32.18#53 Non-authoritative answer: home.web.cern.ch canonical name = drupalprod.cern.ch. Name: drupalprod.cern.ch Address: 137.138.76.28 Note that the #53 denotes the DNS service is running on port 53. 2. Run nslookup to determine the authoritative DNS servers for a university in Asia. frigate:Desktop drb$ nslookup -type=NS tsinghua.edu.cn Server: 130.215.32.18 Address: 130.215.32.18#53 Non-authoritative answer: tsinghua.edu.cn nameserver = dns2.tsinghua.edu.cn. tsinghua.edu.cn nameserver = dns.tsinghua.edu.cn. tsinghua.edu.cn nameserver = dns2.edu.cn. tsinghua.edu.cn nameserver = ns2.cuhk.edu.hk. Authoritative answers can be found from: dns2.tsinghua.edu.cn internet address = 166.111.8.31 ns2.cuhk.edu.hk internet address = 137.189.6.21 ns2.cuhk.edu.hk has AAAA address 2405:3000:3:6::15 dns2.edu.cn internet address = 202.112.0.13 dns.tsinghua.edu.cn internet address = 166.111.8.30 Note that there can be multiple authoritative servers. The response we got back was from a cached record. To confirm the authoritative DNS servers, we perform the same DNS query of one of the servers that can provide authoritative answers. frigate:Desktop drb$ nslookup -type=NS tsinghua.edu.cn dns.tsinghua.edu.cn Server: dns.tsinghua.edu.cn Address: 166.111.8.30#53 tsinghua.edu.cn nameserver = dns2.edu.cn. -

Platform LSF Foundations Chapter 1
Platform LSF Version 9 Release 1.3 Foundations SC27-5304-03 Platform LSF Version 9 Release 1.3 Foundations SC27-5304-03 Note Before using this information and the product it supports, read the information in “Notices” on page 21. First edition This edition applies to version 9, release 1 of IBM Platform LSF (product number 5725G82) and to all subsequent releases and modifications until otherwise indicated in new editions. Significant changes or additions to the text and illustrations are indicated by a vertical line (|) to the left of the change. If you find an error in any Platform Computing documentation, or you have a suggestion for improving it, please let us know. In the IBM Knowledge Center, add your comments and feedback to any topic. You can also send your suggestions, comments and questions to the following email address: [email protected] Be sure include the publication title and order number, and, if applicable, the specific location of the information about which you have comments (for example, a page number or a browser URL). When you send information to IBM, you grant IBM a nonexclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. © Copyright IBM Corporation 1992, 2014. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Chapter 1. IBM Platform LSF: An Job submission .............12 Overview ..............1 Job scheduling and dispatch .........13 Introduction to IBM Platform LSF .......1 Host selection .............15 LSF cluster components...........2 Job execution environment .........15 Chapter 2. -

PPP Over Ethernet Client
PPP over Ethernet Client The PPP over Ethernet Client feature provides PPP over Ethernet (PPPoE) client support on routers. PPPoE is a commonly used application in the deployment of digital subscriber lines (DSLs). The PPP over Ethernet Client feature expands PPPoE functionality by providing support for PPPoE on the client and the server. • Finding Feature Information, page 1 • Prerequisites for PPP over Ethernet Client, page 1 • Restrictions for PPP over Ethernet Client, page 2 • Information About PPP over Ethernet Client, page 2 • How to Configure PPP over Ethernet Client, page 5 • Configuration Examples for the PPP over Ethernet Client, page 13 • Additional References, page 19 • Feature Information for PPP over Ethernet Client, page 20 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required. Prerequisites for PPP over Ethernet Client PPP connections must be established between two endpoints over a serial link. Broadband Access Aggregation and DSL Configuration Guide, Cisco IOS XE -

Avocent® ACS800/8000 Advanced Console System Command Reference Guide TABLE of CONTENTS
Avocent® ACS800/8000 Advanced Console System Command Reference Guide The information contained in this document is subject to change without notice and may not be suitable for all applications. While every precaution has been taken to ensure the accuracy and completeness of this document, Vertiv assumes no responsibility and disclaims all liability for damages resulting from use of this information or for any errors or omissions. Refer to other local practices or building codes as applicable for the correct methods, tools, and materials to be used in performing procedures not specifically described in this document. The products covered by this instruction manual are manufactured and/or sold by Vertiv. This document is the property of Vertiv and contains confidential and proprietary information owned by Vertiv. Any copying, use or disclosure of it without the written permission of Vertiv is strictly prohibited. Names of companies and products are trademarks or registered trademarks of the respective companies. Any questions regarding usage of trademark names should be directed to the original manufacturer. Technical Support Site If you encounter any installation or operational issues with your product, check the pertinent section of this manual to see if the issue can be resolved by following outlined procedures. Visit https://www.VertivCo.com/en-us/support/ for additional assistance. Vertiv™ | Avocent® ACS800/8000 Advanced Console System Command Reference Guide TABLE OF CONTENTS 1 Introduction, Navigation and Commands 1 1.1 AccessOptionsand -

IBM Platform Computing Cloud Service Ready to Use Platform LSF & Symphony Clusters in the Softlayer Cloud
Platform Computing IBM Platform Computing Cloud Service Ready to use Platform LSF & Symphony clusters in the SoftLayer cloud February 25, 2014 1 © 2014 IBM Corporation Platform Computing Agenda v Mapping clients needs to cloud technologies v Addressing your pain points v Introducing IBM Platform Computing Cloud Service v Product features and benefits v Use cases v Performance benchmarks 2 © 2014 IBM Corporation Platform Computing HPC cloud characteristics and economics are different than general-purpose computing • High-end hardware and special purpose devices (e.g. GPUs) are typically used to supply the needed processing, memory, network, and storage capabilities • The performance requirements of technical computing and service-oriented workloads means that performance may be impacted in a virtualized cloud environment, especially when latency or I/O is a constraint • HPC cluster/grid utilization is usually in the 70-90% range, removing a major potential advantage of a public cloud service provider for stable workload volumes HPC Workloads Recommended for Private Cloud HPC Workloads with Best Potential for Virtualized Public & Hybrid Cloud Primary HPC Workloads 3 © 2014 IBM Corporation Platform Computing IBM’s HPC cloud strategy provides a flexible approach to address a variety of client needs Private Hybrid Public Clouds Clouds Clouds Evolve existing infrastructure to Enable integrated HPC Cloud to enhance approach to improve Access additional responsiveness, HPC cost and HPC capacity with flexibility, and capability variable cost model -
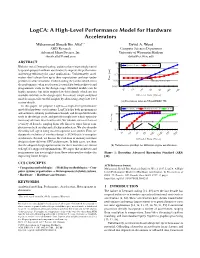
Logca: a High-Level Performance Model for Hardware Accelerators Muhammad Shoaib Bin Altaf ∗ David A
LogCA: A High-Level Performance Model for Hardware Accelerators Muhammad Shoaib Bin Altaf ∗ David A. Wood AMD Research Computer Sciences Department Advanced Micro Devices, Inc. University of Wisconsin-Madison [email protected] [email protected] ABSTRACT 10 With the end of Dennard scaling, architects have increasingly turned Unaccelerated Accelerated 1 to special-purpose hardware accelerators to improve the performance and energy efficiency for some applications. Unfortunately, accel- 0.1 erators don’t always live up to their expectations and may under- perform in some situations. Understanding the factors which effect Time (ms) 0.01 Break-even point the performance of an accelerator is crucial for both architects and 0.001 programmers early in the design stage. Detailed models can be 16 64 highly accurate, but often require low-level details which are not 256 1K 4K 16K 64K available until late in the design cycle. In contrast, simple analytical Offloaded Data (Bytes) models can provide useful insights by abstracting away low-level system details. (a) Execution time on UltraSPARC T2. In this paper, we propose LogCA—a high-level performance 100 model for hardware accelerators. LogCA helps both programmers SPARC T4 UltraSPARC T2 GPU and architects identify performance bounds and design bottlenecks 10 early in the design cycle, and provide insight into which optimiza- tions may alleviate these bottlenecks. We validate our model across Speedup 1 Break-even point a variety of kernels, ranging from sub-linear to super-linear com- plexities on both on-chip and off-chip accelerators. We also describe the utility of LogCA using two retrospective case studies. -

Foreign Library Interface by Daniel Adler Dia Applications That Can Run on a Multitude of Plat- Forms
30 CONTRIBUTED RESEARCH ARTICLES Foreign Library Interface by Daniel Adler dia applications that can run on a multitude of plat- forms. Abstract We present an improved Foreign Function Interface (FFI) for R to call arbitary na- tive functions without the need for C wrapper Foreign function interfaces code. Further we discuss a dynamic linkage framework for binding standard C libraries to FFIs provide the backbone of a language to inter- R across platforms using a universal type infor- face with foreign code. Depending on the design of mation format. The package rdyncall comprises this service, it can largely unburden developers from the framework and an initial repository of cross- writing additional wrapper code. In this section, we platform bindings for standard libraries such as compare the built-in R FFI with that provided by (legacy and modern) OpenGL, the family of SDL rdyncall. We use a simple example that sketches the libraries and Expat. The package enables system- different work flow paths for making an R binding to level programming using the R language; sam- a function from a foreign C library. ple applications are given in the article. We out- line the underlying automation tool-chain that extracts cross-platform bindings from C headers, FFI of base R making the repository extendable and open for Suppose that we wish to invoke the C function sqrt library developers. of the Standard C Math library. The function is de- clared as follows in C: Introduction double sqrt(double x); We present an improved Foreign Function Interface The .C function from the base R FFI offers a call (FFI) for R that significantly reduces the amount of gate to C code with very strict conversion rules, and C wrapper code needed to interface with C.