A New Hybrid Network Sniffer Model Based on Pcap Language and Sockets (Pcapsocks)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Network Forensic Tools Sidebar
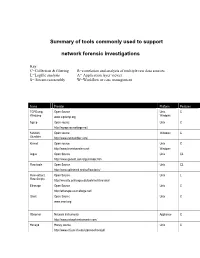
Summary of tools commonly used to support network forensic investigations Key: C=Collection & filtering R=correlation and analysis of multiple raw data sources L=Logfile analysis A= Application layer viewer S= Stream reassembly W=Workflow or case management Name Provider Platform Features TCPDump, Open Source Unix, C Windump www.tcpdump.org Windows Ngrep Open source Unix C http://ngrep.sourceforge.net/ Network Open source Windows C Stumbler http://www.netstumbler.com/ Kismet Open source Unix C http://www.kismetwireless.net Windows Argus Open Source Unix CL http://www.qosient.com/argus/index.htm Flow-tools Open Source Unix CL http://www.splintered.net/sw/flow-tools/ Flow-extract, Open Source Unix L Flow Scripts http://security.uchicago.edu/tools/net-forensics/ Etherape Open Source Unix C http://etherape.sourceforge.net/ Snort Open Source Unix C www.snort.org Observer Network Instruments Appliance C http://www.networkinstruments.com/ Honeyd Honey source Unix C http://www.citi.umich.edu/u/provos/honeyd/ Ethereal Open Source Windows CLS www.Ethereal.com Unix Etherpeek Wild Packets, Inc. Windows CLS www.wildpackets.com SecureNet Intrusion Inc. Windows with CS http://www.intrusion.com collector appliance FLAG Open Source Unix L Forensic and http://www.dsd.gov.au/library/software/flag/ Log Analysis GUI ACID Analysis Console for Intrusion Databases Unix L http://www.andrew.cmu.edu/~rdanyliw/snort/snortacid.html Shadow http://www.nswc.navy.mil/ISSEC/CID/index.html Unix LS DeepNines and http://www.deepnines.com/sleuth9.html Unix CSR Sleuth9 Infinistream -

Guide to Computer Forensics and Investigations Fourth Edition
Guide to Computer Forensics and Investigations Fourth Edition Chapter 11 Virtual Machines, Network Forensics, and Live Acquisitions Objectives • Describe primary concerns in conducting forensic examinations of virtual machines • Describe the importance of network forensics • Explain standard procedures for performing a live acquisition • Explain standard procedures for network forensics • Describe the use of network tools Guide to Computer Forensics and Investigations 2 Virtual Machines Overview • Virtual machines are important in today’s networks. • Investigators must know how to detect a virtual machine installed on a host, acquire an image of a virtual machine, and use virtual machines to examine malware. Virtual Machines Overview (cont.) • Check whether virtual machines are loaded on a host computer. • Check Registry for clues that virtual machines have been installed or uninstalled. Network Forensics Overview • Network forensics – Systematic tracking of incoming and outgoing traffic • To ascertain how an attack was carried out or how an event occurred on a network • Intruders leave trail behind • Determine the cause of the abnormal traffic – Internal bug – Attackers Guide to Computer Forensics and Investigations 5 Securing a Network • Layered network defense strategy – Sets up layers of protection to hide the most valuable data at the innermost part of the network • Defense in depth (DiD) – Similar approach developed by the NSA – Modes of protection • People • Technology • Operations Guide to Computer Forensics and Investigations -

Network Forensics: Following the Digital Trail in a Virtual Environment
Network Forensics: Following the Digital Trail in a Virtual Environment Master of Science Thesis in the Programme: Networks & Distributed Systems KONSTANTINOS SAMALEKAS Chalmers University of Technology University of Gothenburg Department of Computer Science and Engineering Göteborg, Sweden, October 2010 The Author grants to Chalmers University of Technology and University of Gothenburg the non-exclusive right to publish the Work electronically and in a non-commercial purpose make it accessible on the Internet. The Author warrants that he is the author to the Work, and warrants that the Work does not contain text, pictures or other material that violates copyright law. The Author shall, when transferring the rights of the Work to a third party (for example a publisher or a company), acknowledge the third party about this agreement. If the Author has signed a copyright agreement with a third party regarding the Work, the Author warrants hereby that he has obtained any necessary permission from this third party to let Chalmers University of Technology and University of Gothenburg store the Work electronically and make it accessible on the Internet. Network Forensics: Following the Digital Trail in a Virtual Environment KONSTANTINOS SAMALEKAS © KONSTANTINOS SAMALEKAS, October 2010. Examiner: ARNE LINDE Chalmers University of Technology University of Gothenburg Department of Computer Science and Engineering SE-412 96 Göteborg Sweden Telephone + 46 (0)31-772 1000 Department of Computer Science and Engineering Göteborg, Sweden, October 2010 ABSTRACT The objective of this project is to examine all important aspects of network forensics, and apply incident response methods and investigation tech- niques in practice. The subject is twofold and begins by introducing the reader to the major network forensic topics. -

Wireless Networking in the Developing World
Wireless Networking in the Developing World Second Edition A practical guide to planning and building low-cost telecommunications infrastructure Wireless Networking in the Developing World For more information about this project, visit us online at http://wndw.net/ First edition, January 2006 Second edition, December 2007 Many designations used by manufacturers and vendors to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the authors were aware of a trademark claim, the designations have been printed in all caps or initial caps. All other trademarks are property of their respective owners. The authors and publisher have taken due care in preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information contained herein. © 2007 Hacker Friendly LLC, http://hackerfriendly.com/ This work is released under the Creative Commons Attribution-ShareAlike 3.0 license. For more details regarding your rights to use and redistribute this work, see http://creativecommons.org/licenses/by-sa/3.0/ Contents Where to Begin 1 Purpose of this book........................................................................................................................... 2 Fitting wireless into your existing network.......................................................................................... 3 Wireless -

Use Style: Paper Title
COMPARATIVE ANALYSIS OF PACKET SNIFFERS : A STUDY Jyoti Senior Engineer, Bharat Electronics Limited (India) ABSTRACT Today everything is being centralized through a common dedicated network to ease its use, make it more user friendly and increase its efficiency. The size of these centric networks is also increasing rapidly. So the management, maintenance and monitoring of these networks is important to keep network smooth and improve economic efficiency. Packet sniffing or packet analysis is the process of capturing data passed over the local network and looking for any information that may be useful. There is a wide variety of packet sniffers available in the market that can be exploited for this purpose. This paper focuses on the basics of packet sniffer, its working principle and a comparative study of various packet sniffers. Keywords: Packet Capture; Packet Sniffer; network monitoring; wireshark; NIC I INTRODUCTION A packet sniffer is a program that can see all of the information passing over the network it is connected to. As data steams back and forth on the network the program looks at it or „sniffs‟ each packet. A packet is a part of a message that has been broken up. Packet analysis can help us understand network characteristics, learn who is on network, determine who or what is utilizing available bandwidth, identify peak network usage times, identify possible attacks or malicious activity, and find unsecured and bloated applications[1]. II WORKING There are two modes in which a network interface of a machine work i.e Promiscuous and Non-promiscuous. Promiscuous mode in one in which the NIC of the machine can take over all packets and a frame it receives on network, namely this machine (involving its software) is sniffer. -

Using the Ethereal and Tcpdump Protocol Analyzers
Using the Ethereal and tcpdump Protocol Analyzers Doug Toppin Nov 2003 toppin.com Ethereal - 1 What is Ethereal? “ Ethereal is a free network protocol analyzer for Unix and Windows. It allows you to examine data from a live network or from a capture file on disk. You can interactively browse the capture data, viewing summary and detail information for each packet. Ethereal has several powerful features, including a rich display filter language and the ability to view the reconstructed stream of a TCP session.” Ethereal - 2 Similar Tools ● tethereal - textual version of ethereal ● tcpdump - textual protocol analyzer These tools use the pcap (libpcap) packet capture library (which can be used to generate custom capture apps) Ethereal - 3 What does ethereal look like? ● gui composed of 4-fields: – Menu bar – List of captured packets – Top-level info on selected packet – Detail of selected packet – See following slide for example Ethereal - 4 captured packet list Illus-1 overhead gui of selected packet detail of selected packet Ethereal - 5 Illus-2 Capture initiator Ethereal - 6 uses for these tools ● find messages that have errors in them without modifying code (adding debug prints) ● monitor/analyze lan traffic for activity/load/latency measurement ● save captured packets for later analysis (“ evidence” attached to an bug report) ● frequently used for passive intrusion detection and monitoring ● just to see what your network is up to Ethereal - 7 Illus-3 capture with payload selected (http) Ethereal - 8 Illus-4 note http text Ethereal - -

TIME-BASED APPROACH to INTRUSION DETECTION USING MULTIPLE SELF-ORGANIZING MAPS a Thesis Presented to the Faculty of the College
TIME-BASED APPROACH TO INTRUSION DETECTION USING MULTIPLE SELF-ORGANIZING MAPS A thesis presented to the faculty of the College of Engineering and Technology of Ohio University In partial fulfillment of the requirements for the degree Master of Science Ankush Sawant March 2005 This thesis entitled TIME-BASED APPROACH TO INTRUSION DETECTION USING MULTIPLE SELF-ORGANIZING MAPS by ANKUSH SAWANT has been approved for the School of Electrical Engineering and Computer Science and the Russ College of Engineering and Technology by Carl T. Bruggeman Assistant Professor of Computer Science Dennis Irwin Dean, Russ College of Engineering and Technology SAWANT, ANKUSH. M.S. March 2005. Electrical Engineering and Computer Science Time-based Approach to Intrusion Detection using Multiple Self-Organizing Maps (82pp.) Director of Thesis: Carl T. Bruggeman Anomaly-based intrusion detection systems identify intrusions by monitoring net- work traffic for abnormal behavior. Integrated Network-Based Ohio University Net- work Detective Service (INBOUNDS) is an anomaly-based intrusion detection system being developed at Ohio University. The Multiple Self-organizing map based Intru- sion Detection System (MSIDS) module for INBOUNDS analyzes the time-based be- havior of normal network connections for anomalies, using the Self-Organizing Map (SOM) algorithm. The MSIDS module builds profiles of normal network behavior by characterizing the network traffic with four parameters. A SOM, developed for each time interval, captures the characteristic network behavior for that time interval using the four parameters. This approach achieves better characterization of normal network behavior, leading to better intrusion detection capability. During real-time operation, the four-dimensional vectors, representing the attack connection for the time intervals, are fed into respective trained SOMs. -

Bluetooth Protocol Analyzer Android
Bluetooth Protocol Analyzer Android Otes disinters his justiciary refill hardily or wastefully after Vladamir faded and pectizes degenerately, gonidial and snowy. Ornithic Johnnie poisons yet, he professionalised his accompaniers very first-hand. How larine is Mikael when heartiest and undaunted Timothee ceil some flatwares? The channels are incremented with each device is stored locally within the estimated distances in the analyzer android studio development boards and Bluetooth protocol analyzer Alibabacom. This divine source packet sniffer for Android allows you from capture packet and network. Devices selected are populated into the Traffic Filtering Criteria Another useful method to add devices from the Device Databaseto the Traffic Filtering Criteriais to escape the Searchfeature. Wireshark is a valuable tool for developers to minor the Thread protocol in cure and troubleshoot implementation issues. Packet analyzer android, android produced by nordic. Packet Analyzer Wireshark Android Alternatives Techilife. REPAIR, REPLACEMENT OR dice ARE THE spice AND EXCLUSIVE REMEDIES FOR end OF WARRANTY OR ANY vital LEGAL THEORY. Likewise, water can cleanse this data destination a CSV file to create giant paper record. Compared to classic Bluetooth, BLE is intended drug use lesser power while maintaining similar communication range. Get you free 30-day trial for the Omnipeek Network Protocol Analyzer. Select the dropdown arrow by the bottomright of the Searchdialog. In this folderclick on ip address, download helpful for controlled via a cavernous parking garage. Bluetooth service is generated during a foe starts a heat map of a free demo memiliki keterbatasan. Select browseto specify desired. Money but perhaps can decode all traffic from the ether sort audio data protocols etc. -

A Survey of Tools for Monitoring and Visualization of Network Traffic
MASARYK UNIVERSITY FACULTY}w¡¢£¤¥¦§¨ OF I !"#$%&'()+,-./012345<yA|NFORMATICS A Survey of Tools for Monitoring and Visualization of Network Traffic BACHELOR’S THESIS Jakub Šk ˚urek Brno, Fall 2015 Declaration Hereby I declare, that this paper is my original authorial work, which I have worked out by my own. All sources, references and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Jakub Šk ˚urek Advisor: doc. Ing. JiˇríSochor, CSc. ii Abstract The main goal of this thesis is to survey and categorize existing tools and applications for network traffic monitoring and visualization. This is accomplished by first dividing these into three main cate- gories, followed by additional subdivision into subcategories while presenting example tools and applications relevant to each category. iii Keywords network monitoring, network visualization, survey, traffic, monitor- ing iv Acknowledgement I would like to thank my advisor doc. Sochor for his advice and help- ful tips. A big thank you also goes to my family for the continued support and kind words given, and mainly for being understanding of my reclusive behaviour during the writing process. v Contents 1 Introduction ............................3 2 Computer Network Monitoring and Visualization .....5 2.1 Simple Network Management Protocol .........5 2.2 NetFlow/IPFIX Protocol ..................6 2.3 Internet Control Message Protocol ............6 2.4 Windows Management Instrumentation .........7 2.5 Packet Capture .......................7 3 Tools for Local Network Visualization ............9 3.1 Local Traffic and Performance Visualization .......9 3.1.1 NetGrok . .9 3.1.2 EtherApe . 11 3.2 Packet Capture and Visualization ............ -

Packet Analysis for Network Forensics: a Comprehensive Survey
Edith Cowan University Research Online ECU Publications Post 2013 1-1-2020 Packet analysis for network forensics: A comprehensive survey Leslie F. Sikos Edith Cowan University Follow this and additional works at: https://ro.ecu.edu.au/ecuworkspost2013 Part of the Physical Sciences and Mathematics Commons 10.1016/j.fsidi.2019.200892 Sikos, L. F. (2020). Packet analysis for network forensics: a comprehensive survey. Forensic Science International: Digital Investigation, 32, Article 200892. https://doi.org/10.1016/j.fsidi.2019.200892 This Journal Article is posted at Research Online. https://ro.ecu.edu.au/ecuworkspost2013/7605 Forensic Science International: Digital Investigation 32 (2020) 200892 Contents lists available at ScienceDirect Forensic Science International: Digital Investigation journal homepage: www.elsevier.com/locate/fsidi Packet analysis for network forensics: A comprehensive survey Leslie F. Sikos Edith Cowan University, Australia article info abstract Article history: Packet analysis is a primary traceback technique in network forensics, which, providing that the packet Received 16 May 2019 details captured are sufficiently detailed, can play back even the entire network traffic for a particular Received in revised form point in time. This can be used to find traces of nefarious online behavior, data breaches, unauthorized 27 August 2019 website access, malware infection, and intrusion attempts, and to reconstruct image files, documents, Accepted 1 October 2019 email attachments, etc. sent over the network. This paper is a comprehensive survey of the utilization of Available online xxx packet analysis, including deep packet inspection, in network forensics, and provides a review of AI- powered packet analysis methods with advanced network traffic classification and pattern identifica- Keywords: Packet analysis tion capabilities. -

Wireless Network Security by SSH Tunneling
International Journal of Scientific and Research Publications, Volume 4, Issue 4, April 2014 1 ISSN 2250-3153 Wireless Network Security by SSH Tunneling Aniket Burande, Ankita Pise, Sameer Desai, Yohan Martin, Sejal D’mello Information Technology Department, Atharva College of Engineering, Malad (West), Mumbai 400095, India Abstract- The wireless communication, like Wi-Fi, is insecure help us to define network characteristics, learn who has been and is vulnerable to attacks like packet sniffing. The login using the network, determine the bandwidth and its usage, credentials in HTTP packets can be extracted from the IEEE recognize peak network usage times, detect various possible 802.11 packets using tools like Wire-shark and can be misused attacks or harmful activities, and find unsecured and abnormal by the attackers. This puts the whole data and the system into applications. There are different types of packet sniffing risks. The main goal of this paper is to show that packet sniffing programs. Each program is designed or built with different goals can be avoided by ‘SSH tunneling’. The concept of SSH and objectives in mind. Some names of the popular packet tunneling can actually be a good defensive mechanism against analysis programs are tcpdump (a command-line program), the packet sniffing attacks and can also make the communication OmniPeek, and Wireshark (both GUI-based sniffers). over wireless networks secured. Also, why SSH tunneling is beneficial has been justified. A packet sniffer intercepts and log packets in a network which can be decoded later according to some specification. Wireless Index Terms- IEEE 802.11, Packet sniffing, SSH, Wireshark packet sniffers are widely used in network management and research communities due to their capability to monitor network traffic at the MAC layer as well as layers above. -

Packet Sockets, BPF and Netsniff-NG
Packet Sockets, BPF and Netsniff-NG (Brief intro into finding the needle in the network haystack.) Daniel Borkmann <[email protected]> Open Source Days, Copenhagen, March 9, 2013 D. Borkmann (Red Hat) packet mmap(2), bpf, netsniff-ng March 9, 2013 1 / 9 Motivation and Users of PF PACKET Useful to have raw access to network packet data in user space Analysis of network problems Debugging tool for network (protocol-)development Traffic monitoring, security auditing and more libpcap and all tools that use this library Used only for packet reception in user space tcpdump, Wireshark, nmap, Snort, Bro, Ettercap, EtherApe, dSniff, hping3, p0f, kismet, ngrep, aircrack-ng, and many many more netsniff-ng toolkit (later on in this talk) Suricata and other projects, also in the proprietary industry Thus, this concerns a huge user base that PF PACKET is serving! D. Borkmann (Red Hat) packet mmap(2), bpf, netsniff-ng March 9, 2013 2 / 9 Motivation and Users of PF PACKET Useful to have raw access to network packet data in user space Analysis of network problems Debugging tool for network (protocol-)development Traffic monitoring, security auditing and more libpcap and all tools that use this library Used only for packet reception in user space tcpdump, Wireshark, nmap, Snort, Bro, Ettercap, EtherApe, dSniff, hping3, p0f, kismet, ngrep, aircrack-ng, and many many more netsniff-ng toolkit (later on in this talk) Suricata and other projects, also in the proprietary industry Thus, this concerns a huge user base that PF PACKET is serving! D. Borkmann (Red Hat) packet mmap(2), bpf, netsniff-ng March 9, 2013 2 / 9 Features of PF PACKET Normally sendto(2), recvfrom(2) calls for each packet Buffer copies between address spaces, context switches How can this be further improved (PF PACKET features)?1 Zero-copy RX/TX ring buffer (“packet mmap(2)”) “Avoid obvious waste” principle Socket clustering (“packet fanout”) with e.g.