CFRS 730 Forensic Deep Packt Inspection
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Implementing Cisco Cyber Security Operations
2019 CLUS Implementing Cisco Cyber Security Operations Paul Ostrowski / Patrick Lao / James Risler Cisco Security Content Development Engineers LTRCRT-2222 2019 CLUS Cisco Webex Teams Questions? Use Cisco Webex Teams to chat with the speaker after the session How 1 Find this session in the Cisco Live Mobile App 2 Click “Join the Discussion” 3 Install Webex Teams or go directly to the team space 4 Enter messages/questions in the team space Webex Teams will be moderated cs.co/ciscolivebot#LTRCRT-2222 by the speaker until June 16, 2019. 2019 CLUS © 2019 Cisco and/or its affiliates. All rights reserved. Cisco Public 3 Agenda • Goals and Objectives • Prerequisite Knowledge & Skills (PKS) • Introduction to Security Onion • SECOPS Labs and Topologies • Access SECFND / SECOPS eLearning Lab Training Environment • Lab Evaluation • Cisco Cybersecurity Certification and Education Offerings 2019 CLUS LTRCRT-2222 © 2019 Cisco and/or its affiliates. All rights reserved. Cisco Public 4 Goals and Objectives: • Today's organizations are challenged with rapidly detecting cybersecurity breaches in order to effectively respond to security incidents. Cybersecurity provides the critical foundation organizations require to protect themselves, enable trust, move faster, add greater value and grow. • Teams of cybersecurity analysts within Security Operations Centers (SOC) keep a vigilant eye on network security monitoring systems designed to protect their organizations by detecting and responding to cybersecurity threats. • The goal of Cisco’s CCNA Cyber OPS (SECFND / SECOPS) courses is to teach the fundamental skills required to begin a career working as an associate/entry-level cybersecurity analyst within a threat centric security operations center. • This session will provide the student with an understanding of Security Onion as an open source network security monitoring tool (NSM). -
Network Forensic Tools Sidebar
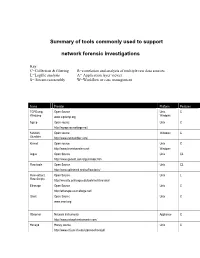
Summary of tools commonly used to support network forensic investigations Key: C=Collection & filtering R=correlation and analysis of multiple raw data sources L=Logfile analysis A= Application layer viewer S= Stream reassembly W=Workflow or case management Name Provider Platform Features TCPDump, Open Source Unix, C Windump www.tcpdump.org Windows Ngrep Open source Unix C http://ngrep.sourceforge.net/ Network Open source Windows C Stumbler http://www.netstumbler.com/ Kismet Open source Unix C http://www.kismetwireless.net Windows Argus Open Source Unix CL http://www.qosient.com/argus/index.htm Flow-tools Open Source Unix CL http://www.splintered.net/sw/flow-tools/ Flow-extract, Open Source Unix L Flow Scripts http://security.uchicago.edu/tools/net-forensics/ Etherape Open Source Unix C http://etherape.sourceforge.net/ Snort Open Source Unix C www.snort.org Observer Network Instruments Appliance C http://www.networkinstruments.com/ Honeyd Honey source Unix C http://www.citi.umich.edu/u/provos/honeyd/ Ethereal Open Source Windows CLS www.Ethereal.com Unix Etherpeek Wild Packets, Inc. Windows CLS www.wildpackets.com SecureNet Intrusion Inc. Windows with CS http://www.intrusion.com collector appliance FLAG Open Source Unix L Forensic and http://www.dsd.gov.au/library/software/flag/ Log Analysis GUI ACID Analysis Console for Intrusion Databases Unix L http://www.andrew.cmu.edu/~rdanyliw/snort/snortacid.html Shadow http://www.nswc.navy.mil/ISSEC/CID/index.html Unix LS DeepNines and http://www.deepnines.com/sleuth9.html Unix CSR Sleuth9 Infinistream -

Guide to Computer Forensics and Investigations Fourth Edition
Guide to Computer Forensics and Investigations Fourth Edition Chapter 11 Virtual Machines, Network Forensics, and Live Acquisitions Objectives • Describe primary concerns in conducting forensic examinations of virtual machines • Describe the importance of network forensics • Explain standard procedures for performing a live acquisition • Explain standard procedures for network forensics • Describe the use of network tools Guide to Computer Forensics and Investigations 2 Virtual Machines Overview • Virtual machines are important in today’s networks. • Investigators must know how to detect a virtual machine installed on a host, acquire an image of a virtual machine, and use virtual machines to examine malware. Virtual Machines Overview (cont.) • Check whether virtual machines are loaded on a host computer. • Check Registry for clues that virtual machines have been installed or uninstalled. Network Forensics Overview • Network forensics – Systematic tracking of incoming and outgoing traffic • To ascertain how an attack was carried out or how an event occurred on a network • Intruders leave trail behind • Determine the cause of the abnormal traffic – Internal bug – Attackers Guide to Computer Forensics and Investigations 5 Securing a Network • Layered network defense strategy – Sets up layers of protection to hide the most valuable data at the innermost part of the network • Defense in depth (DiD) – Similar approach developed by the NSA – Modes of protection • People • Technology • Operations Guide to Computer Forensics and Investigations -

Linux Networking Cookbook.Pdf
Linux Networking Cookbook ™ Carla Schroder Beijing • Cambridge • Farnham • Köln • Paris • Sebastopol • Taipei • Tokyo Linux Networking Cookbook™ by Carla Schroder Copyright © 2008 O’Reilly Media, Inc. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (safari.oreilly.com). For more information, contact our corporate/institutional sales department: (800) 998-9938 or [email protected]. Editor: Mike Loukides Indexer: John Bickelhaupt Production Editor: Sumita Mukherji Cover Designer: Karen Montgomery Copyeditor: Derek Di Matteo Interior Designer: David Futato Proofreader: Sumita Mukherji Illustrator: Jessamyn Read Printing History: November 2007: First Edition. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. The Cookbook series designations, Linux Networking Cookbook, the image of a female blacksmith, and related trade dress are trademarks of O’Reilly Media, Inc. Java™ is a trademark of Sun Microsystems, Inc. .NET is a registered trademark of Microsoft Corporation. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. -

Wireshark & Ethereal Network Protocol Analyzer
377_Eth2e_FM.qxd 11/14/06 1:23 PM Page i Visit us at www.syngress.com Syngress is committed to publishing high-quality books for IT Professionals and delivering those books in media and formats that fit the demands of our cus- tomers. We are also committed to extending the utility of the book you purchase via additional materials available from our Web site. SOLUTIONS WEB SITE To register your book, visit www.syngress.com/solutions. Once registered, you can access our [email protected] Web pages. There you may find an assortment of value-added features such as free e-books related to the topic of this book, URLs of related Web sites, FAQs from the book, corrections, and any updates from the author(s). ULTIMATE CDs Our Ultimate CD product line offers our readers budget-conscious compilations of some of our best-selling backlist titles in Adobe PDF form. These CDs are the perfect way to extend your reference library on key topics pertaining to your area of exper- tise, including Cisco Engineering, Microsoft Windows System Administration, CyberCrime Investigation, Open Source Security, and Firewall Configuration, to name a few. DOWNLOADABLE E-BOOKS For readers who can’t wait for hard copy, we offer most of our titles in download- able Adobe PDF form. These e-books are often available weeks before hard copies, and are priced affordably. SYNGRESS OUTLET Our outlet store at syngress.com features overstocked, out-of-print, or slightly hurt books at significant savings. SITE LICENSING Syngress has a well-established program for site licensing our e-books onto servers in corporations, educational institutions, and large organizations. -

Wireless Networking in the Developing World
Wireless Networking in the Developing World Second Edition A practical guide to planning and building low-cost telecommunications infrastructure Wireless Networking in the Developing World For more information about this project, visit us online at http://wndw.net/ First edition, January 2006 Second edition, December 2007 Many designations used by manufacturers and vendors to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the authors were aware of a trademark claim, the designations have been printed in all caps or initial caps. All other trademarks are property of their respective owners. The authors and publisher have taken due care in preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information contained herein. © 2007 Hacker Friendly LLC, http://hackerfriendly.com/ This work is released under the Creative Commons Attribution-ShareAlike 3.0 license. For more details regarding your rights to use and redistribute this work, see http://creativecommons.org/licenses/by-sa/3.0/ Contents Where to Begin 1 Purpose of this book........................................................................................................................... 2 Fitting wireless into your existing network.......................................................................................... 3 Wireless -

Introducing Network Analysis
377_Eth_2e_ch01.qxd 11/14/06 9:27 AM Page 1 Chapter 1 Introducing Network Analysis Solutions in this chapter: ■ What is Network Analysis and Sniffing? ■ Who Uses Network Analysis? ■ How Does it Work? ■ Detecting Sniffers ■ Protecting Against Sniffers ■ Network Analysis and Policy Summary Solutions Fast Track Frequently Asked Questions 1 377_Eth_2e_ch01.qxd 11/14/06 9:27 AM Page 2 2 Chapter 1 • Introducing Network Analysis Introduction “Why is the network slow?”“Why can’t I access my e-mail?”“Why can’t I get to the shared drive?”“Why is my computer acting strange?” If you are a systems administrator, network engineer, or security engineer you have heard these ques- tions countless times.Thus begins the tedious and sometimes painful journey of troubleshooting.You start by trying to replicate the problem from your computer, but you can’t connect to the local network or the Internet either. What should you do? Go to each of the servers and make sure they are up and functioning? Check that your router is functioning? Check each computer for a malfunctioning network card? Now consider this scenario.You go to your main network switch or border router and configure one of the unused ports for port mirroring.You plug in your laptop, fire up your network analyzer, and see thousands of Transmission Control Protocol (TCP) packets (destined for port 25) with various Internet Protocol (IP) addresses.You investigate and learn that there is a virus on the network that spreads through e-mail, and immediately apply access filters to block these packets from entering or exiting your network.Thankfully, you were able to contain the problem relatively quickly because of your knowledge and use of your network analyzer. -

Use Style: Paper Title
COMPARATIVE ANALYSIS OF PACKET SNIFFERS : A STUDY Jyoti Senior Engineer, Bharat Electronics Limited (India) ABSTRACT Today everything is being centralized through a common dedicated network to ease its use, make it more user friendly and increase its efficiency. The size of these centric networks is also increasing rapidly. So the management, maintenance and monitoring of these networks is important to keep network smooth and improve economic efficiency. Packet sniffing or packet analysis is the process of capturing data passed over the local network and looking for any information that may be useful. There is a wide variety of packet sniffers available in the market that can be exploited for this purpose. This paper focuses on the basics of packet sniffer, its working principle and a comparative study of various packet sniffers. Keywords: Packet Capture; Packet Sniffer; network monitoring; wireshark; NIC I INTRODUCTION A packet sniffer is a program that can see all of the information passing over the network it is connected to. As data steams back and forth on the network the program looks at it or „sniffs‟ each packet. A packet is a part of a message that has been broken up. Packet analysis can help us understand network characteristics, learn who is on network, determine who or what is utilizing available bandwidth, identify peak network usage times, identify possible attacks or malicious activity, and find unsecured and bloated applications[1]. II WORKING There are two modes in which a network interface of a machine work i.e Promiscuous and Non-promiscuous. Promiscuous mode in one in which the NIC of the machine can take over all packets and a frame it receives on network, namely this machine (involving its software) is sniffer. -

Using the Ethereal and Tcpdump Protocol Analyzers
Using the Ethereal and tcpdump Protocol Analyzers Doug Toppin Nov 2003 toppin.com Ethereal - 1 What is Ethereal? “ Ethereal is a free network protocol analyzer for Unix and Windows. It allows you to examine data from a live network or from a capture file on disk. You can interactively browse the capture data, viewing summary and detail information for each packet. Ethereal has several powerful features, including a rich display filter language and the ability to view the reconstructed stream of a TCP session.” Ethereal - 2 Similar Tools ● tethereal - textual version of ethereal ● tcpdump - textual protocol analyzer These tools use the pcap (libpcap) packet capture library (which can be used to generate custom capture apps) Ethereal - 3 What does ethereal look like? ● gui composed of 4-fields: – Menu bar – List of captured packets – Top-level info on selected packet – Detail of selected packet – See following slide for example Ethereal - 4 captured packet list Illus-1 overhead gui of selected packet detail of selected packet Ethereal - 5 Illus-2 Capture initiator Ethereal - 6 uses for these tools ● find messages that have errors in them without modifying code (adding debug prints) ● monitor/analyze lan traffic for activity/load/latency measurement ● save captured packets for later analysis (“ evidence” attached to an bug report) ● frequently used for passive intrusion detection and monitoring ● just to see what your network is up to Ethereal - 7 Illus-3 capture with payload selected (http) Ethereal - 8 Illus-4 note http text Ethereal - -

The Golden Age of Hacking
The golden age of hacking Sniffing and spoofing Session hijacking Netcat DoS attacks Sniffing • A sniffer captures data via promiscuous mode • Useful for troubleshooting – Admin/root account is usually needed – Hub vs. switch • Island hopping attack • Passive vs. active sniffers – Tcpdump, Windump, ngrep – WireShark, Tshark – Sniffit, got ability to sniff sessions interactively – Dsniff - fragroute guy – Snort IDS - overkill for hacking – WinPcap: The Windows Packet Capture Library – Cain, Ettercap Passive OS fingerprinting • Every OS has its peculiarities regarding TCP stack etc. • P0f v2, identifies OS on: – Machines that connect to your box (SYN mode) – Machines you connect to (SYN+ACK mode) – Machine you cannot connect to (RST+ mode) – Machines whose communications you can observe – Firewall presence, NAT use (useful for policy enforcement) – Existence of a load balancer setup – The distance to the remote system and its uptime – Other guy's network hookup (DSL, optical/avian carriers) and his ISP – http://lcamtuf.coredump.cx/p0f.shtml • Tutorial - Passive OS Fingerprinting With P0f And Ettercap – http://www.irongeek.com/i.php?page=videos/passive-os-fingerprinting – Ettercap • http://ettercap.sourceforge.net/ • PVS (Passive Vulnerability Scanner) – Tenable Network Security (Nessus) ARP operation Jumbo Frames > 1500 • Ethernet frame • ARP packet Dsniff suite - foiling switches http://monkey.org/~dugsong/dsniff/ • Unix tools with good parsing capabilities for many clear-text protocols • MAC flooding switch attack – CAM (Content Addressable -

TIME-BASED APPROACH to INTRUSION DETECTION USING MULTIPLE SELF-ORGANIZING MAPS a Thesis Presented to the Faculty of the College
TIME-BASED APPROACH TO INTRUSION DETECTION USING MULTIPLE SELF-ORGANIZING MAPS A thesis presented to the faculty of the College of Engineering and Technology of Ohio University In partial fulfillment of the requirements for the degree Master of Science Ankush Sawant March 2005 This thesis entitled TIME-BASED APPROACH TO INTRUSION DETECTION USING MULTIPLE SELF-ORGANIZING MAPS by ANKUSH SAWANT has been approved for the School of Electrical Engineering and Computer Science and the Russ College of Engineering and Technology by Carl T. Bruggeman Assistant Professor of Computer Science Dennis Irwin Dean, Russ College of Engineering and Technology SAWANT, ANKUSH. M.S. March 2005. Electrical Engineering and Computer Science Time-based Approach to Intrusion Detection using Multiple Self-Organizing Maps (82pp.) Director of Thesis: Carl T. Bruggeman Anomaly-based intrusion detection systems identify intrusions by monitoring net- work traffic for abnormal behavior. Integrated Network-Based Ohio University Net- work Detective Service (INBOUNDS) is an anomaly-based intrusion detection system being developed at Ohio University. The Multiple Self-organizing map based Intru- sion Detection System (MSIDS) module for INBOUNDS analyzes the time-based be- havior of normal network connections for anomalies, using the Self-Organizing Map (SOM) algorithm. The MSIDS module builds profiles of normal network behavior by characterizing the network traffic with four parameters. A SOM, developed for each time interval, captures the characteristic network behavior for that time interval using the four parameters. This approach achieves better characterization of normal network behavior, leading to better intrusion detection capability. During real-time operation, the four-dimensional vectors, representing the attack connection for the time intervals, are fed into respective trained SOMs. -

A Survey of Tools for Monitoring and Visualization of Network Traffic
MASARYK UNIVERSITY FACULTY}w¡¢£¤¥¦§¨ OF I !"#$%&'()+,-./012345<yA|NFORMATICS A Survey of Tools for Monitoring and Visualization of Network Traffic BACHELOR’S THESIS Jakub Šk ˚urek Brno, Fall 2015 Declaration Hereby I declare, that this paper is my original authorial work, which I have worked out by my own. All sources, references and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Jakub Šk ˚urek Advisor: doc. Ing. JiˇríSochor, CSc. ii Abstract The main goal of this thesis is to survey and categorize existing tools and applications for network traffic monitoring and visualization. This is accomplished by first dividing these into three main cate- gories, followed by additional subdivision into subcategories while presenting example tools and applications relevant to each category. iii Keywords network monitoring, network visualization, survey, traffic, monitor- ing iv Acknowledgement I would like to thank my advisor doc. Sochor for his advice and help- ful tips. A big thank you also goes to my family for the continued support and kind words given, and mainly for being understanding of my reclusive behaviour during the writing process. v Contents 1 Introduction ............................3 2 Computer Network Monitoring and Visualization .....5 2.1 Simple Network Management Protocol .........5 2.2 NetFlow/IPFIX Protocol ..................6 2.3 Internet Control Message Protocol ............6 2.4 Windows Management Instrumentation .........7 2.5 Packet Capture .......................7 3 Tools for Local Network Visualization ............9 3.1 Local Traffic and Performance Visualization .......9 3.1.1 NetGrok . .9 3.1.2 EtherApe . 11 3.2 Packet Capture and Visualization ............