Packet Analysis for Network Forensics: a Comprehensive Survey
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

REAL-WORLD XAMARIN PROBLEMS and How to Solve Them Mobile Strategy
REAL-WORLD XAMARIN PROBLEMS And How To Solve Them Mobile Strategy It’s 2017. Developers have been making mobile apps for almost a decade and have some choice in how they build those apps. Whatever the approach, a mobile strategy is imperative—it’s how you achieve consistency in building and supporting mobile solutions. The choice of technology for mobile depends on various factors, including the skills of the team involved, app specifics, customer demographics and maintainability of code base. Here are the high level technology choices that could make up a mobile strategy: Progress.com 2 Mobile Web • Web apps that work nicely on mobile devices • Frameworks like Twitter Bootstrap & Kendo UI Core help. Native Apps • Native iOS/Android/Windows apps for each platform • Written in native languages and built with native toolkits • Closest to the metal and best possible UX • Expensive to write and maintain JS Native Apps • Use web technologies to build truly native mobile apps • Cross platform reach with single codebase • Big contenders being NativeScript and React Native • Potential to share code between web and mobile Cross-Compiled • Use beloved language and tools to write mobile app • Single codebase with cross-platform reach • App gets compiled down to native code on each platform • Primary contender is Xamarin Progress.com 3 Why Xamarin? If your development experience includes .NET, you probably already know C# and XAML—the primary programming languages for mobile development with Xamarin. Xamarin truly democratizes cross-platform mobile -

Getting Started with Ethereal
Ethereal: Getting Started Computer Networking: A Top- down Approach Featuring the Internet, 3rd edition. Version: July 2005 © 2005 J.F. Kurose, K.W. Ross. All Rights Reserved ªTell me and I forget. Show me and I remember. Involve me and I understand.º Chinese proverb One's understanding of network protocols can often be greatly deepened by ªseeing protocols in actionº and by ªplaying around with protocolsº ± observing the sequence of messages exchanged between two protocol entities, delving down into the details of protocol operation, and causing protocols to perform certain actions and then observing these actions and their consequences. The basic tool for observing the messages exchanged between executing protocol entities is called a packet sniffer. As the name suggests, a packet sniffer captures (ªsniffsº) messages being sent/received from/by your computer; it will also typically store and/or display the contents of the various protocol fields in these captured messages. A packet sniffer itself is passive. It observes messages being sent and received by applications and protocols running on your computer, but never sends packets itself. Similarly, received packets are never explicitly addressed to the packet sniffer. Instead, a packet sniffer receives a copy of packets that are sent/received from/by application and protocols executing on your machine. Figure 1 shows the structure of a packet sniffer. At the right of Figure 1 are the protocols (in this case, Internet protocols) and applications (such as a web browser or ftp client) that normally run on your computer. The packet sniffer, shown within the dashed rectangle in Figure 1 is an addition to the usual software in your computer, and consists of two parts. -

Part 1 Digital Forensics Module Jaap Van Ginkel Silvio Oertli
Part 1 Digital Forensics Module Jaap van Ginkel Silvio Oertli July 2016 Agenda • Part 1: Introduction – Definitions / Processes • Part 2: Theory in Practice – From planning to presentation • Part 3: Live Forensics – How to acquire a memory image – Investigate the image • Part 4: Advanced Topics – Tools – Where to go from here – And more 2 Disclaimer§ • A one or two-day course on forensics will not make you a forensics expert. – Professionals spend most of their working time performing forensic analysis and thus become an expert. • All we can offer is to shed some light on a quickly developing and broad field and a chance to look at some tools. • We will mostly cover Open Source Forensic Tools. 3 Introduction Forensics in History 4 Forensics – History 2000 BC 1200 BC 5 Introduction Definitions / Processes 6 Forensics – The Field digital forensics Computer Forensics Disk Forensics Mobil Forensics Memory Forensics Datenbase Forensics Live Forensics Network Forensics 7 Forensics - Definition • Digital Forensics [1]: – Digital forensics (sometimes known as digital forensic science) is a branch of forensic science encompassing the recovery and investigation of material found in digital devices, often in relation to computer crime. • Computer Forensics [2]: – Computer forensics (sometimes known as computer forensic science) is a branch of digital forensic science pertaining to legal evidence found in computers and digital storage media. The goal of computer forensics is to examine digital media in a forensically sound manner with the aim of identifying, preserving, recovering, analyzing and presenting facts and opinions about the information. 8 Forensics - Definitions • Network Forensics [3]: – Network forensics is a sub-branch of digital forensics relating to the monitoring and analysis of computer network traffic for the purposes of information gathering, legal evidence, or intrusion detection.[1] Unlike other areas of digital forensics, network investigations deal with volatile and dynamic information. -
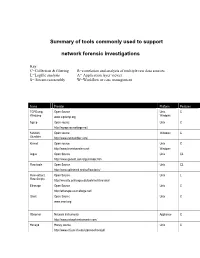
Network Forensic Tools Sidebar
Summary of tools commonly used to support network forensic investigations Key: C=Collection & filtering R=correlation and analysis of multiple raw data sources L=Logfile analysis A= Application layer viewer S= Stream reassembly W=Workflow or case management Name Provider Platform Features TCPDump, Open Source Unix, C Windump www.tcpdump.org Windows Ngrep Open source Unix C http://ngrep.sourceforge.net/ Network Open source Windows C Stumbler http://www.netstumbler.com/ Kismet Open source Unix C http://www.kismetwireless.net Windows Argus Open Source Unix CL http://www.qosient.com/argus/index.htm Flow-tools Open Source Unix CL http://www.splintered.net/sw/flow-tools/ Flow-extract, Open Source Unix L Flow Scripts http://security.uchicago.edu/tools/net-forensics/ Etherape Open Source Unix C http://etherape.sourceforge.net/ Snort Open Source Unix C www.snort.org Observer Network Instruments Appliance C http://www.networkinstruments.com/ Honeyd Honey source Unix C http://www.citi.umich.edu/u/provos/honeyd/ Ethereal Open Source Windows CLS www.Ethereal.com Unix Etherpeek Wild Packets, Inc. Windows CLS www.wildpackets.com SecureNet Intrusion Inc. Windows with CS http://www.intrusion.com collector appliance FLAG Open Source Unix L Forensic and http://www.dsd.gov.au/library/software/flag/ Log Analysis GUI ACID Analysis Console for Intrusion Databases Unix L http://www.andrew.cmu.edu/~rdanyliw/snort/snortacid.html Shadow http://www.nswc.navy.mil/ISSEC/CID/index.html Unix LS DeepNines and http://www.deepnines.com/sleuth9.html Unix CSR Sleuth9 Infinistream -

Digital Forensics Based Analysis of Mobile Phones
Journal of Android and IOS Applications and Testing Volume 4 Issue 3 Digital Forensics Based Analysis of Mobile Phones Pooja V Chavan PG Student, Department of Computer Engineering, K. J. Somaiya College of Engineering, Mumbai, Maharashtra, India Email: [email protected] DOI: Abstract Now-a-day’s ratio of mobile phone is increasing day by day. Digital forensics methodology is use to recover and investigate data that found in a digital devices. Mobile phone usage is more that’s why not only judicial events occurred but also mobile forensics and subdivision of digital forensics are emerged. Some hardware and software are used for mobile phone investigations. Keywords: Digital forensics, digital devices, mobile phone INTRODUCTION because electronic device have a variety of Forensic science’s subdivision is a digital different operating system, technology, forensic, is a one type of process. The storage structure, Features. First identify main objective of this process to find the crime after that digital forensic work evidence in digital devices [1]. Digital on four important steps (Figure 1): forensics are used for the analysis of data, such as audio, video, pictures, etc. After • Collection: The collected of evidence the analysis of electronic devices data that like fingerprints, broken fingernails help for legal process. The usage of blood and body fluids. advanced technology is increasing rapidly. • Examination: The examination of Electronic device have a variety of product process is depending on evidence. like tablet, flash memory, memory card, • Analysis: The crime scenes obtain SD card, etc. When forensic analysis is different digital evidence, analysis is performed at that time data should be done on storage evidence this secure. -

Guide to Computer Forensics and Investigations Fourth Edition
Guide to Computer Forensics and Investigations Fourth Edition Chapter 11 Virtual Machines, Network Forensics, and Live Acquisitions Objectives • Describe primary concerns in conducting forensic examinations of virtual machines • Describe the importance of network forensics • Explain standard procedures for performing a live acquisition • Explain standard procedures for network forensics • Describe the use of network tools Guide to Computer Forensics and Investigations 2 Virtual Machines Overview • Virtual machines are important in today’s networks. • Investigators must know how to detect a virtual machine installed on a host, acquire an image of a virtual machine, and use virtual machines to examine malware. Virtual Machines Overview (cont.) • Check whether virtual machines are loaded on a host computer. • Check Registry for clues that virtual machines have been installed or uninstalled. Network Forensics Overview • Network forensics – Systematic tracking of incoming and outgoing traffic • To ascertain how an attack was carried out or how an event occurred on a network • Intruders leave trail behind • Determine the cause of the abnormal traffic – Internal bug – Attackers Guide to Computer Forensics and Investigations 5 Securing a Network • Layered network defense strategy – Sets up layers of protection to hide the most valuable data at the innermost part of the network • Defense in depth (DiD) – Similar approach developed by the NSA – Modes of protection • People • Technology • Operations Guide to Computer Forensics and Investigations -

Troubleshooting Lans with Wirespeed Packet Capture and Expert Analysis
Application Note Troubleshooting LANs with Wirespeed Packet Capture and Expert Analysis Introduction This application note is one in a series of local area network (LAN) troubleshooting papers from JDSU Communications Test and Measurement. Troubleshooting LAN issues covers a wide array of network problems and diagnostic scenarios that may include: • evaluating network utilization over the course of a business day by link, virtual LAN (VLAN), or subnet • detecting excessive broadcast or multi-case traffic • finding “bandwidth hogs” • understanding what protocols are present on the network (and determining whether they should be) • identifying the “top-talkers” on the link—the IP devices that are consuming the most capacity • experiencing application performance issues (slow web server response time or intermittent unavail- ability of an e-mail server). Before network troubleshooting can begin, one must have a clear understanding of network test access. Testing tools used for network analysis and troubleshooting scenarios must be able to monitor the network traffic being tested. The most common means for monitoring a network is using the built-in port mirroring capabilities of a network device, such as the switch/router or to install a special “tap” device between the devices being analyzed, such as those between an application server and database server. Figures 1 and 2 show each test access mode for analyzing traffic between two servers. Ethernet Switch Port 1 Port 3 Port 2 Port 3 “mirrored” to Port 2 Application Database Server Server -

Current and Future Trends in Mobile Device Forensics: a Survey
Current and Future Trends in Mobile Device Forensics: A Survey KONSTANTIA BARMPATSALOU, TIAGO CRUZ, EDMUNDO MONTEIRO, and PAULO SIMOES, Centre for Informatics and Systems of the University of Coimbra, Department of Informatics (CISUC/DEI), University of Coimbra, Portugal Contemporary mobile devices are the result of an evolution process, during which computational and networking capabilities have been continuously pushed to keep pace with the constantly growing workload requirements. This has allowed devices such as smartphones, tablets and Personal Digital Assistants (PDAs) to perform increasingly complex tasks, up to the point of efficiently replacing traditional options such as desktop computers and notebooks. However, due to their portability and size, these devices are more prone to theft, to become compromised or to be exploited for attacks and other malicious activity. The need for investigation of the aforementioned incidents resulted in the creation of the Mobile Forensics (MF) discipline. MF, a sub-domain of Digital Forensics (DF), is specialized in extracting and processing evidence from mobile devices in such a way that attacking entities and actions are identified and traced. Beyond its primary research interest on evidence acquisition from mobile devices, MF has recently expanded its scope to encompass the organized and advanced evidence representation and analysis of future malicious entity behavior. Nonetheless, data acquisition still remains its main focus. While the field is under continuous research activity, new concepts such as the involvement of Cloud Computing in the MF ecosystem and the evolution of enterprise mobile solutions – particularly Mobile Device Management (MDM) and Bring Your Own Device (BYOD) – bring new opportunities and issues to the discipline. -

A User-Oriented Network Forensic Analyser: the Design of a High- Level Protocol Analyser
Edith Cowan University Research Online Australian Digital Forensics Conference Conferences, Symposia and Campus Events 2014 A user-oriented network forensic analyser: The design of a high- level protocol analyser D Joy Plymouth University F Li Plymouth University N L. Clarke Edith Cowan University S M. Furnell Edith Cowan University Follow this and additional works at: https://ro.ecu.edu.au/adf Part of the Computer Engineering Commons, and the Information Security Commons DOI: 10.4225/75/57b3e511fb87f 12th Australian Digital Forensics Conference. Held on the 1-3 December, 2014 at Edith Cowan University, Joondalup Campus, Perth, Western Australia. This Conference Proceeding is posted at Research Online. https://ro.ecu.edu.au/adf/135 A USER-ORIENTED NETWORK FORENSIC ANALYSER: THE DESIGN OF A HIGH-LEVEL PROTOCOL ANALYSER D. Joy1, F. Li1, N.L. Clarke1,2 and S.M. Furnell1,2 1Centre for Security, Communications and Network Research (CSCAN) Plymouth University, Plymouth, United Kingdom 2Security Research Institute, Edith Cowan University, Western Australia [email protected] Abstract Network forensics is becoming an increasingly important tool in the investigation of cyber and computer- assisted crimes. Unfortunately, whilst much effort has been undertaken in developing computer forensic file system analysers (e.g. Encase and FTK), such focus has not been given to Network Forensic Analysis Tools (NFATs). The single biggest barrier to effective NFATs is the handling of large volumes of low-level traffic and being able to exact and interpret forensic artefacts and their context – for example, being able extract and render application-level objects (such as emails, web pages and documents) from the low-level TCP/IP traffic but also understand how these applications/artefacts are being used. -

Wireshark & Ethereal Network Protocol Analyzer
377_Eth2e_FM.qxd 11/14/06 1:23 PM Page i Visit us at www.syngress.com Syngress is committed to publishing high-quality books for IT Professionals and delivering those books in media and formats that fit the demands of our cus- tomers. We are also committed to extending the utility of the book you purchase via additional materials available from our Web site. SOLUTIONS WEB SITE To register your book, visit www.syngress.com/solutions. Once registered, you can access our [email protected] Web pages. There you may find an assortment of value-added features such as free e-books related to the topic of this book, URLs of related Web sites, FAQs from the book, corrections, and any updates from the author(s). ULTIMATE CDs Our Ultimate CD product line offers our readers budget-conscious compilations of some of our best-selling backlist titles in Adobe PDF form. These CDs are the perfect way to extend your reference library on key topics pertaining to your area of exper- tise, including Cisco Engineering, Microsoft Windows System Administration, CyberCrime Investigation, Open Source Security, and Firewall Configuration, to name a few. DOWNLOADABLE E-BOOKS For readers who can’t wait for hard copy, we offer most of our titles in download- able Adobe PDF form. These e-books are often available weeks before hard copies, and are priced affordably. SYNGRESS OUTLET Our outlet store at syngress.com features overstocked, out-of-print, or slightly hurt books at significant savings. SITE LICENSING Syngress has a well-established program for site licensing our e-books onto servers in corporations, educational institutions, and large organizations. -

Packet Capture and Analysis in Hybrid Environments
Packet Capture and Analysis in Hybrid Environments Lawrence Miller Inside the Guide • Discover why packet capture and analysis of on- premises and cloud applications in modern hybrid environments is so challenging • Learn how to analyze packets at the Transport and Application Layers to uncover the root cause of issues • Explore how putting the right tools in the hands of the right people can help make your entire IT team more effective THE GORILLA GUIDE TO... Packet Capture and Analysis in Hybrid Environments Express Edition By Lawrence Miller Copyright © 2020 by ActualTech Media All rights reserved. This book or any portion thereof may not be reproduced or used in any manner whatsoever without the express written permission of the publisher except for the use of brief quotations in a book review. Printed in the United States of America. ACTUALTECH MEDIA 6650 Rivers Ave Ste 105 #22489 North Charleston, SC 29406-4829 www.actualtechmedia.com PUBLISHER’S ACKNOWLEDGEMENTS EDITOR Keith Ward, ActualTech Media PROJECT MANAGER Wendy Hernandez, ActualTech Media EXECUTIVE EDITOR James Green, ActualTech Media LAYOUT AND DESIGN Olivia Thomson, ActualTech Media WITH SPECIAL CONTRIBUTIONS FROM Paul R. Dietz, Riverbed Stephen Creel, Riverbed Heidi Gabrielson, Riverbed Kowshik Bhat, Riverbed TABLE OF CONTENTS Introduction 7 Chapter 1: A Primer on Packets 8 Looking at Packets and Packet-Switched Networks 8 Understanding the Open Systems Interconnection (OSI) Model and Packet Encapsulation 11 Addressing Modern Packet Capture and Analysis Challenges 13 -

Wireless Networking in the Developing World
Wireless Networking in the Developing World Second Edition A practical guide to planning and building low-cost telecommunications infrastructure Wireless Networking in the Developing World For more information about this project, visit us online at http://wndw.net/ First edition, January 2006 Second edition, December 2007 Many designations used by manufacturers and vendors to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the authors were aware of a trademark claim, the designations have been printed in all caps or initial caps. All other trademarks are property of their respective owners. The authors and publisher have taken due care in preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information contained herein. © 2007 Hacker Friendly LLC, http://hackerfriendly.com/ This work is released under the Creative Commons Attribution-ShareAlike 3.0 license. For more details regarding your rights to use and redistribute this work, see http://creativecommons.org/licenses/by-sa/3.0/ Contents Where to Begin 1 Purpose of this book........................................................................................................................... 2 Fitting wireless into your existing network.......................................................................................... 3 Wireless