Fatal Error Definition of Implicitly Declared Destructor
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Electronic Circuit Simulation and PCB Design
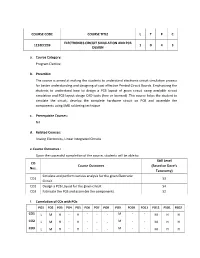
COURSE CODE COURSE TITLE L T P C ELECTRONICS CIRCUIT SIMULATION AND PCB 1152EC239 1 0 4 3 DESIGN a. Course Category: Program Elective b. Preamble: The course is aimed at making the students to understand electronic circuit simulation process for better understanding and designing of cost effective Printed Circuit Boards. Emphasizing the students to understand how to design a PCB layout of given circuit using available circuit simulation and PCB layout design CAD tools (free or licensed) .This course helps the student to simulate the circuit, develop the complete hardware circuit on PCB and assemble the components using SMD soldering technique c. Prerequisite Courses: Nil d. Related Courses: Analog Electronics, Linear Integrated Circuits e. Course Outcomes : Upon the successful completion of the course, students will be able to: Skill Level CO Course Outcomes (Based on Dave’s Nos. Taxonomy) Simulate and perform various analysis for the given Electronic CO1 S3 Circuit. CO2 Design a PCB Layout for the given circuit S4 CO3 Fabricate the PCB and assemble the components. S2 f. Correlation of COs with POs PO1 PO2 PO3 PO4 PO5 PO6 PO7 PO8 PO9 PO10 PO11 PO12 PSO1 PSO2 CO1 L M H - H - - - M - - M H H CO2 L M H - H - - - M - - M H H CO3 L M H - H - - - M - - M H H g. Examination scheme Examination Scheme for practical dominated course Internal evaluation Semester end evaluation (40M) (60M) Laboratory experiment Model laboratory test Part-A Part-B (15M) (25M) (20M) (40M) Performa Result Viv Reco Performa Result Viv Theory Performa Result Viv nce in and a rd nce in and a questions nce in and a- conductin analys Voc (4) conductin analys Voc to evaluate conductin analys Voc g is e g is e the g is e experime (3 ) ( 3) experime (5) ( 5) knowledge experime (10) (5) nt nt and nt ( 5 ) ( 15 ) understand (25) ing (20) h. -

Metadefender Core V4.12.2
MetaDefender Core v4.12.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

Alexis Rodriguez Jr
Alexis Rodriguez Jr. 701 SW 62nd Blvd - Apt 104 - Gainesville - FL - 32604 Cell: 305-370-8334 Email: [email protected] Education: University of Florida Gainesville, FL Current M.S. Computer and Electrical Engineering University of Florida Gainesville, FL 2018 B.S. Electrical Engineering - Cum Laude Miami Dade College Miami, FL 2013 A.A. Engineering - Computer Projects: FPGA Networking Research Current Nallatech 385a Communication Research Current Glove Controlled Drone Design 2 Fall 2017 32-bit ARM Cortex (TI MSP432) used to interpret hand gestures via sensors for drone flight, transmit user intended controls to the drone via RF communication, and detect and display communication errors and react accordingly for safety 32-bit MIPS Emulated Processor Digital Design Spring 2017 Altera Cyclone-III FPGA used to emulate MIPS processor via VHDL Guitar Tuner Design 1 Spring 2017 Microchip PIC18F4620 microcontroller and discrete analog components used to determine correct input frequency via analog filtering and DSP techniques Employment: University of Florida - ARC Lab Gainesville, FL Current Research Assistant - FPGA ❖ Research systems integration of Nallatech 385a FPGA card and its components including the Intel Arria 10 FPGA, Intel’s Avalon bus, and PCIe communication via Linux ❖ Create partial reconfiguration region for Nallatech 385a for general use in research lab ❖ Research cloud and network implementations of FPGAs Intel San Jose, CA Summer 2019/2020 Programmable Solutions Group Intern ❖ Assisted with Agilex Linux driver development ❖ ITU G spec testing compliance and characterization for IEEE 1588 on Intel N3000 ❖ Developed automated tools for ITU network timestamp testing ❖ System validation of IEEE 1588 for Wireless 5G technology and communicated need and data across many teams ❖ Developed Arduino workshop for hobbyists Alexis Rodriguez Jr. -

Altium's Journey and Its Vision of Industry Transformation
A Winning Strategy for Value-Creation ALTIUM’S JOURNEY AND ITS VISION OF INDUSTRY TRANSFORMATION 18 June 2021 Agenda 1 Altium’s Journey of Transformation 2 Uniqueness of Altium in the Engineering Software Ecosystem 3 Altium’s Confidence in its Ability to Execute 4 Our Flight Path to Dominance Outstanding Value-Creation Track-Record Over Time ALU Set in 2019 and confident of achieving $500M * Stock Price Revenue Target Set in 2016 and fell short with COVID, $189M ** Delivering Value for our Shareholders $200M is a Hallmark of Altium… Revenue Target • A history of setting and over-achieving Set in 2014 and overachieved, $110M $100M aggressive long-term financial targets Revenue Target • Eight consecutive years of double-digit revenue growth & expanding margin ? • Focused execution with the “ingenuity of and” A$41.60 delivering strong operating leverage A$10.15 • Transparency for stakeholders and all-in reporting (no capitalization of R&D expenses) A$4.36 • Value creation at every stage from leadership to dominance to industry transformation A$0.76 Performing Leading Dominating Transforming 2012 2015 2017 2020 2025 * The target revenue of $500M may include 10-20% from future acquisitions. 3 ** Three months out analysts’ consensus pointed to a revenue target of $208M for FY2020 Pursuing Dominance and Transformation from a Position of Strength Financial Altium Designer Altium 365 Performance Dominance Adoption Altium is the fastest growing EDA company Altium Designer is the most widespread The world’s first digital platform for with 8 consecutive -

Getting Started with PCB Design
Getting Started with PCB Design This introductory tutorial is designed to give you an overview Summary of how to create a schematic, update the design information to a PCB and generate manufacturing output files. It also Tutorial investigates the concept of projects and integrated libraries TU0117 (v2.0) February 12, 2008 and provides a summary of the 3D PCB environment and creating 3D bodies for component footprints. Welcome to the world of Altium Designer – a complete electronic product development environment. This tutorial will get you started with creating a PCB project based on an astable multivibrator design. If you are new to Altium Designer then you might like read the guide Welcome to the Altium Designer Environment for an explanation of the interface, information on how to use panels and managing design documents. Creating a New PCB Project A project in Altium Designer consists of links to all documents and setups related to a design. A project file, eg. xxx.PrjPCB, is an ASCII text file that lists which documents are in the project and related output setups, eg. for printing and CAM. Documents that are not associated with a project are called ‘free documents’. Links to schematic sheets and a target output, eg. PCB, FPGA, embedded (VHDL) or library package, are added to a project. Once the project is compiled, design verification, synchronization and comparison can take place. Any changes to the original schematics or PCB, for example, are updated in the project when compiled. The process of creating a new project is the same for all project types. -

Module 11: PCB Design Flow, Transferring a Design and Navigation
Module 11: PCB Design Flow, Transferring a Design and Navigation Module 11: PCB Design Flow, Transferring a Design and Navigation 11.1 PCB design process....................................................................... 11-1 11.2 Transferring design information to the PCB.................................... 11-3 11.2.1 Design synchronization ................................................................................11-3 11.2.2 Resolving synchronization errors .................................................................11-4 11.2.3 Exercise – Transferring the design ..............................................................11-5 11.3 Using the PCB Panel ...................................................................... 11-7 11.3.1 PCB Panel....................................................................................................11-7 11.3.2 PCB Rules and Violations ..........................................................................11-14 11.3.3 Exercise – Browsing a PCB document ......................................................11-15 11.4 Project Navigation and Cross Probing ....................................... 11-16 11.4.1 Compiling the PCB project .........................................................................11-16 11.4.2 Navigating ..................................................................................................11-16 11.4.3 Cross probing from the schematic to the PCB...........................................11-17 11.4.4 Exercise — Navigation and Cross Probing................................................11-18 -

Virtual Kit Detail Ürünler Direkt Tedarikçiden Gelecektir Ya Da Indirilecektir
Virtual Kit Detail Ürünler direkt tedarikçiden gelecektir ya da indirilecektir. Sana kit içerikleri çok zengin. Takımlarımız en güncel haline FIRST sitesi üzerideki DashBoard üzerinden kuponlarına erişebilirler. Kimi ürünlerde kargo ücreti olduğuna dikkat ediniz. Başlıklarına tıklayarak detaylı bilgileri alabilirsiniz Ürün Bağış Kuponları Kullanım alanı örnekleri Verilen Sürüş Control Elektriksel Alışveriş Teşekkürler… Destek Son tarih Ekipman System Tedarik Pneumatics Sensors Material/Alet AndyMark $450 4/15/19 X X X X X X Armabot One RS7 4/27/19 X Encoder AutomationDirect $35 4/30/19 X X X X X X Clippard $20 9/1/19 X Inventables $100 5/1/19 X REV Robotics $40 4/30/19 X X X X X TE Connectivity $25 6/1/19 X X Yazılım Kullanım alanı örnekleri Thank you… Verilen destek Son tarih Animasyon CAD CAM Sertifika Devre Programming Simulation Eğitim Design Altium Altium Designer 12/31/19 X Fusion360 n/a X X X Inventor n/a X X X Autodesk Synthesis n/a X Eagle n/a X 3DSMax n/a X X Mastercam 2019 Educational 9/30/19 X Suite National LabVIEW 1/15/20 X Instruments Multisim 1/15/20 Ultiboard 1/15/20 PTC Creo n/a X Mathcad n/a Windchill n/a Vuforia n/a Siemens Solid Edge 12/31/19 X Solid Edge 12/31/19 X Certification SolidProfessor One Membership n/a X SOLIDWORKS SOLIDWORKS n/a X CAD Premium SOLIDWORKS n/a X Simulation Premium SOLIDWORKS n/a X Flow Simulation SOLIDWORKS n/a X Motion SOLIDWORKS n/a X CAM Professional SOLIDWORKS n/a X Visualize Professional SOLIDWORKS n/a X Composer SOLIDWORKS n/a X X Electrical Professional MySolidWorks n/a X Professional DETAYLAR Altium What: Altium Designer, 1-5 student licenses to be shared per high school team. -

PLM Industry Summary Jillian Hayes, Editor Vol
PLM Industry Summary Jillian Hayes, Editor Vol. 16 No. 41 Friday 10 October 2014 Contents CIMdata News _____________________________________________________________________ 2 CIMdata’s President, Peter Bilello, to Kick-off PDT Europe 2014 _________________________________2 CIMdata’s President, Peter Bilello, to speak at PI Congress San Diego _____________________________3 CIMdata to be Featured in Webinar on Model-Based Systems Engineering __________________________4 Acquisitions _______________________________________________________________________ 5 GRAITEC Acquires Robobat Polska ________________________________________________________5 Nemetschek Acquires Bluebeam Software ____________________________________________________6 Company News _____________________________________________________________________ 7 Bentley Announces Project Finalists in 2014 Be Inspired Awards Competition _______________________7 CADsoft Consulting Earns Autodesk Advisor Partner Status for BIM 360 ___________________________8 CGS Contributes to Charitable Organizations through Global Volunteerism and Philanthropic Campaigns _9 CSC is Now Operating as Tekla ____________________________________________________________9 EDA Consortium Reports Revenue Increase for Q2 2014 _______________________________________10 Geometric and College of Engineering, Pune come together to promote 3D Printing __________________11 Hankook Delcam Holds World’s Biggest Meeting for CAM Users _______________________________12 HP To Separate Into Two New Industry-Leading Public Companies -

Altium Designer Feature Set Summary
Altium Designer Feature Set Summary Updated March 2013 Altium Designer is available in license options that maximize your choices and make accessing Altium Designer flexible. Whether you are part of a large design team or a consulting engineer operating on your own, Altium Designer presents everything you need to innovate, be competitive and design new products in new ways. Altium Designer 2013 lets designers create a product from concept to manufacture, in a single design environment, embracing hardware, software and programmable hardware (FPGAs). If your design team has engineers who don’t do board implementation but are capturing and verifying the design, implementing systems on FPGAs and specifying the board, choose Altium Designer SE. Altium Designer Altium Designer Altium Designer Altium Designer Feature Description 2013 Viewer 2013 SD 2013 SE 2013 Software integration platform, consistent GUI provided for all supporting editors and viewers, Design DXP Platform Insight for design document preview, design release management, design compiler, file management, P P P version control interface and scripting engine Schematic – Viewer Open, view and print schematic documents and libraries P P P P PCB – Viewer Open, view and print PCB documents, additionally view and navigate 3D PCBs P P P P CAM File – Viewer Open CAM and mechanical files P P P P All schematic and schematic library editing capabilities (except in PCB Projects and Free Documents), Schematic – Soft Design Editing P netlist generation P P VHDL simulation engine, integrated -

Download Easyeda PDF Tutorial
EasyEDA Tutorial 2020.06.14 v6.3.53 EasyEDA Editor:https://lceda.cn/editor EasyEDA Desktop Client:https://lceda.cn/download Remark This document will be updated as the new features of the editor are updated. The latest revison please refer at EasyEDA Tutorials.pdf Editor FAQ Please spend a few minutes reading this FAQ, it will save you lots of time getting started with EasyEDA. Video Tutorials https://www.youtube.com/channel/UCRoMhHNzl7tMW8pFsdJGUIA/videos Contact Us https://docs.easyeda.com/en/FAQ/Contact-Us/index.html Update Records Update Records Can I use EasyEDA in my company? You are free to use EasyEDA for individuals, business and education. If you add our Logo and link on your PCB/Video we will appreciate. I don't like others seeing my design. How can I stop that happening? Set your project as Private. For extra security you can even save your work locally. What happens if EasyEDA service is offline for some reason? EasyEDA can be run as an offline application. Is EasyEDA safe? There are no absolutely secure things in the world but even if you have the misfortune - as happened to one of our team - of losing one laptop and having two hard drives break, EasyEDA will try to protect your designs in following ways: 1. We utilize SSL throughout the entire domain EasyEDA.com. Secure Socket Layer (SSL) technology encrypts all data transferred between your computer and our servers. Your data is for your eyes only. 2. You can save your files locally. 3. Multiple copies of every file are saved in your local database. -

Yuniel Freire Hernández.Pdf
Universidad Central “Marta Abreu” de Las Villas Facultad de Ingeniería Eléctrica Departamento de Telecomunicaciones y Electrónica TRABAJO DE DIPLOMA Simulación de Circuitos Digitales con Software Libre Autor: Yuniel Freire Hernández Tutor: Ing. Erisbel Orozco Crespo Santa Clara 2012 Universidad Central “Marta Abreu” de Las Villas Facultad de Ingeniería Eléctrica Departamento de Telecomunicaciones y Electrónica TRABAJO DE DIPLOMA Simulación de Circuitos Digitales con Software Libre Autor: Yuniel Freire Hernández Tutor: Ing. Erisbel Orozco Crespo Profesor, Dpto. Telec. Y Electrónica Santa Clara 2012 Hago constar que el presente trabajo de diploma fue realizado en la Universidad Central “Marta Abreu” de Las Villas como parte de la culminación de estudios de la especialidad de Ingeniería en Telecomunicaciones y Electrónica, autorizando a que el mismo sea utilizado por la Institución, para los fines que estime conveniente, tanto de forma parcial como total y que además no podrá ser presentado en eventos, ni publicados sin autorización de la Universidad. Firma del Autor Los abajo firmantes certificamos que el presente trabajo ha sido realizado según acuerdo de la dirección de nuestro centro y el mismo cumple con los requisitos que debe tener un trabajo de esta envergadura referido a la temática señalada. Firma del Tutor Firma del Jefe de Departamento donde se defiende el trabajo Firma del Responsable de Información Científico-Técnica PENSAMIENTO No fracasé, sólo descubrí 999 maneras de cómo no hacer una bombilla. Thomas Alva Edison AGRADECIMIENTOS A todos los profesores que brindaron sus conocimientos para mi formación. A mi tutor por su paciencia, esmero y dedicación. A mis amigos y compañeros por resistirme. -

EPW Quick Start Guide
ECAD Part Wizard (EPW) Quick Start Guide The ECAD Part Wizard has been developed by RS Components and SamacSys to provide a range of highly accurate ECAD models, offering schematic symbol and PCB footprint information for electronic components. The ECAD Part Wizard (EPW) gives engineers full control of the symbol fracturing and symbol pin positions (left, right, top, bottom). ECAD Symbols & footprints can be downloaded directly from within the EPW application or from manufacturer and RS Component websites around the world. These .epw files are then loaded into the ECAD Part Wizard. If the model you require is not yet available you may request it from within EPW and it will be created for you, free of charge. The ECAD Part Wizard is available free of charge, look out for the EPW icon: Having fractured the symbol and placed the pins as required models may be exported from EPW to any of the supported ECAD tool formats: Developed by: Downloading the EPW Application You will need EXCEL 2007 or Newer to run the ECAD Part Wizard The ECAD Part Wizard application does not require special permissions to install. Microsoft Excel 2007 (or later) must be installed on your PC for EPW to run. The download file has a “.ex_” extension as some web browsers do not allow a “.exe” to download. The ECAD Part Wizard application may be downloaded by clicking on the following link: Please: CLICK HERE If you cannot access the download file please email us at [email protected] and we will send you a copy (2Mb).