TSO/E REXX User's Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Rexx Programmer's Reference
01_579967 ffirs.qxd 2/3/05 9:00 PM Page i Rexx Programmer’s Reference Howard Fosdick 01_579967 ffirs.qxd 2/3/05 9:00 PM Page iv 01_579967 ffirs.qxd 2/3/05 9:00 PM Page i Rexx Programmer’s Reference Howard Fosdick 01_579967 ffirs.qxd 2/3/05 9:00 PM Page ii Rexx Programmer’s Reference Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2005 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN: 0-7645-7996-7 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 1MA/ST/QS/QV/IN No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, e-mail: [email protected]. LIMIT OF LIABILITY/DISCLAIMER OF WARRANTY: THE PUBLISHER AND THE AUTHOR MAKE NO REPRESENTATIONS OR WARRANTIES WITH RESPECT TO THE ACCURACY OR COM- PLETENESS OF THE CONTENTS OF THIS WORK AND SPECIFICALLY DISCLAIM ALL WAR- RANTIES, INCLUDING WITHOUT LIMITATION WARRANTIES OF FITNESS FOR A PARTICULAR PURPOSE. -

Z/OS ISPF Services Guide COMMAND NAME
z/OS 2.4 ISPF Services Guide IBM SC19-3626-40 Note Before using this information and the product it supports, read the information in “Notices” on page 399. This edition applies to Version 2 Release 4 of z/OS (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2021-06-22 © Copyright International Business Machines Corporation 1980, 2021. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures................................................................................................................ xv Tables................................................................................................................xvii Preface...............................................................................................................xix Who should use this document?............................................................................................................... xix What is in this document?......................................................................................................................... xix How to read the syntax diagrams..............................................................................................................xix z/OS information...............................................................................................xxiii How to send your comments to IBM................................................................... -

Creating Java Applications Using Netrexx
SG24-2216-00 Creating Java Applications Using NetRexx September 1997 IBML International Technical Support Organization SG24-2216-00 Creating Java Applications Using NetRexx September 1997 Take Note! Before using this information and the product it supports, be sure to read the general information in Appendix B, “Special Notices” on page 273. First Edition (September 1997) This edition applies to Version 1.0 and Version 1.1 of NetRexx with Java Development Kit 1.1.1 for use with the OS/2 Warp, Windows 95, and Windows NT operating systems. Because NetRexx runs on any platform where Java is implemented, it applies to other platforms and operating systems as well. SAMPLE CODE ON THE INTERNET The sample code for this redbook is available as nrxredbk.zip on the ITSO home page on the Internet: ftp://www.redbooks.ibm.com/redbooks/SG242216 Download the sample code and read “Installing the Sample Programs” on page 4. Comments may be addressed to: IBM Corporation, International Technical Support Organization Dept. QXXE Building 80-E2 650 Harry Road San Jose, California 95120-6099 When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1997. All rights reserved. Note to U.S. Government Users — Documentation related to restricted rights — Use, duplication or disclosure is subject to restrictions set forth in GSA ADP Schedule Contract with IBM Corp. Contents Figures . xi Tables . xv Preface . xvii How This Document is Organized ................................ xviii The Team That Wrote This Redbook ............................... -

TSO/E Programming Guide
z/OS Version 2 Release 3 TSO/E Programming Guide IBM SA32-0981-30 Note Before using this information and the product it supports, read the information in “Notices” on page 137. This edition applies to Version 2 Release 3 of z/OS (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2019-02-16 © Copyright International Business Machines Corporation 1988, 2017. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents List of Figures....................................................................................................... ix List of Tables........................................................................................................ xi About this document...........................................................................................xiii Who should use this document.................................................................................................................xiii How this document is organized............................................................................................................... xiii How to use this document.........................................................................................................................xiii Where to find more information................................................................................................................ xiii How to send your comments to IBM......................................................................xv -

REXX Parsing for Today’S Slides and Other Webinars Visit: PARSE Forms
REXX Parsing For today’s slides and other webinars visit: www.themisinc.com/webinars PARSE Forms PARSE ARG template Parameters passed to program or subroutine PARSE EXTERNAL template Read from Terminal (TSO/E, VM only) PARSE NUMERIC template Current NUMERIC settings (TSO/E, VM only) PARSE PULL template Remove data from REXX STACK PARSE SOURCE template Information about the current program PARSE VALUE expression WITH template Information comes from expression PARSE VAR name template Parse one variable into other variables PARSE VERSION template Information about the REXX interpreter General Rules for Parsing • Parsing processes the data string from left to right • If there is more data than defined variables, the last variable receives ALL the remaining data • If there are more variables than data, the remaining variables are set as null • A period (.) may be used as a “placeholder” to bypass setting a variable PARSE VAR Keyword PARSE [UPPER] VAR origin template Use designated variable as input to template PARSING Example origin_data = ‘This is the original data’ PARSE VAR origin_data var1 var2 var3 var1 = This var2 = is var3 = the original data PARSING Example #2 origin_data = ‘This is the original data’ PARSE VAR origin_data var1 . var3 var1 = This var3 = original data PARSING Example #3 origin_data = ‘This is the original data’ PARSE VAR origin_data var1 var2 var3 . var1 = This var2 = is var3 = the PARSING Example #4 origin_data = ‘This is the original data’ PARSE VAR origin_data var1 “the” var3 . var1 = This is var3 = original NOTE: The placeholder (.) removes the last bit of data as space-delimited. Parsing Example Evaluate the following PARSE template: • What will dsn and member contain? dsname = "'SYS1.PROCLIB(JES2)'" PARSE VAR dsname "'" dsn '(' member ')' . -

The Design of the REXX Language
The design of the REXX language by M. F. Cowlishaw One way of classifying computer languagesis by two (consciously or otherwise) to be easy to compile or classes: languages needing skilled programmers, and easy to interpret, it is designed (with the help of personal languages usedby an expanding population of general users. REstructured extended executor feedback from hundreds of users) to be easy to use. (REXX) isa flexible personal language designed with particular attention to feedback from its users. It has Three major factors affect the usability of a language. proved to be effective and easyto use, yet it is suffi- First, the basic concepts of a language affect its ciently general and powerfulto fulfil theneeds of many demanding professional applications.REXX is system syntax, grammar, and consistency. Second, the his- and hardware independent,so that it has been possi- tory and development of a language determine its ble to integrate it experimentally into several operating function, usability, and completeness. Third, but systems. Here REXX isused for such purposes as com- quite independently, the implementation of a lan- mand and macro programming, prototyping, educa- guage affects its acceptability, portability, and distri- tion, and personal programming. This paper introduces REXX and describes the basic design principles that bution. This paper introduces REXX and then dis- were followed in developingit. cusses basic concepts and developmental history as applied to the design of the REXX language. There are several experimental implementations of the REXX language within IBM for both large and small machines. One of these, by the author, has omputer languages may be classified in many become a part of the Virtual Machine/System Prod- ways. -
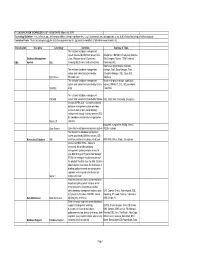
TECHNOLOGY LIST - ISSUE DATE: March 18, 2019 Technology Definition: a Set of Knowledge, Skills And/Or Abilities, Taking a Significant Time (E.G
IT CLASSIFICATION TECHNOLOGY LIST - ISSUE DATE: March 18, 2019 Technology Definition: A set of knowledge, skills and/or abilities, taking a significant time (e.g. 6 months) to learn, and applicable to the defined classification specification assigned. Example of Tools: These are examples only for illustration purposes and are not meant to constitute a full and/or comprehensive list. Classification Discipline Technology Definition Example of Tools The relational database management system provided by IBM that runs on Unix, Omegamon, IBM Admin Tools, Log Analyzer, Database Management Linux, Windows and z/OS platforms DB2 Compare, Nsynch, TSM, Universal DBA System DB2 including DB2 Connect and related tools Command, SQL SQL Server Mgmt Studio, Red Gate, The relational database management Vantage, Tivoli, Snap Manager, Toad, system and related tools provided by Enterprise Manager, SQL, Azure SQL SQL Server Microsoft Corp Database The relational database management Oracle enterprise manager, application system and related tools provided by Oracle express, RMAN, PL SQL, SQL developer, ORACLE Corp Toad, SQL The relational database management SYBASE system and related tools provided by Sybase ASE, OEM, RAC, Partioning, Encryption Cincom SUPRA SQL – Cincom's relational database management system provides access to data in open and proprietary environments through industry-standard SQL for standalone and client/server application Supra 2.X solutions. phpadmin, mysqladmin, MySql, Vertica, Open Source Open Source database management system SQLite, Hadoop The hierarchical database management system provided by IBM that runs on z/OS Hierarchical Database IMS mainframe platform including related tools BMC IMS Utilities, Strobe, Omegamon Cincom SUPRA® PDM – Cincom's networked, hierarchical database management system provides access to your data through a Physical Data Manager (PDM) that manages the data structures of the physical files that store the data. -

Computer Performance Evaluation Users Group (CPEUG)
COMPUTER SCIENCE & TECHNOLOGY: National Bureau of Standards Library, E-01 Admin. Bidg. OCT 1 1981 19105^1 QC / 00 COMPUTER PERFORMANCE EVALUATION USERS GROUP CPEUG 13th Meeting NBS Special Publication 500-18 U.S. DEPARTMENT OF COMMERCE National Bureau of Standards 3-18 NATIONAL BUREAU OF STANDARDS The National Bureau of Standards^ was established by an act of Congress March 3, 1901. The Bureau's overall goal is to strengthen and advance the Nation's science and technology and facilitate their effective application for public benefit. To this end, the Bureau conducts research and provides: (1) a basis for the Nation's physical measurement system, (2) scientific and technological services for industry and government, (3) a technical basis for equity in trade, and (4) technical services to pro- mote public safety. The Bureau consists of the Institute for Basic Standards, the Institute for Materials Research, the Institute for Applied Technology, the Institute for Computer Sciences and Technology, the Office for Information Programs, and the Office of Experimental Technology Incentives Program. THE INSTITUTE FOR BASIC STANDARDS provides the central basis within the United States of a complete and consist- ent system of physical measurement; coordinates that system with measurement systems of other nations; and furnishes essen- tial services leading to accurate and uniform physical measurements throughout the Nation's scientific community, industry, and commerce. The Institute consists of the Office of Measurement Services, and the following -

IBM Tivoli Netview for Z/OS Programming: PL/I and C, Describes How to Write Command Processors and Installation Exit Routines for the Netview Product Using PL/I and C
IBM Tivoli NetView for z/OS Version 6 Release 1 Programming: PL/I and C SC27-2860-00 IBM Tivoli NetView for z/OS Version 6 Release 1 Programming: PL/I and C SC27-2860-00 Note Before using this information and the product it supports, read the information in “Notices” on page 317. This edition applies to version 6, release 1 of IBM Tivoli NetView for z/OS (product number 5697-NV6) and to all subsequent versions, releases, and modifications until otherwise indicated in new editions. © Copyright IBM Corporation 1997, 2011. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures ....................................xi About this publication .............................xiii Intended audience .................................xiii Publications ...................................xiii IBM Tivoli NetView for z/OS library .........................xiii Related publications ...............................xv Accessing terminology online ............................xv Using NetView for z/OS online help .........................xvi Using LookAt to look up message explanations ......................xvi Accessing publications online ............................xvii Ordering publications ..............................xvii Accessibility ..................................xvii Tivoli technical training ...............................xvii Tivoli user groups ................................xviii Downloads ...................................xviii Support information................................xviii -

Open Source - Who Cares and Why?
Open Source - Who Cares and Why? Al Williams Session 8480 SHARE 103, New York, NY August 20, 2004 http://lily.garden.et-test.psu.edu/~alw/whyopen.pdf Agenda What is Open Source? What is it being used for? Who is using Open Source? Open Source Myths? What does this mean? What is Open Source? Open Source Is Application, program, or utility where The computer instructions (code, source) are provided with the program Licensed in such a way that it can be improved, enhanced, or localized freely Isn’t necessarily zero cost Popular revolution - some good work being done More lengthly definition at http://www.opensource.org Open Source Initiative The Open Source Initiative is now a California public benefit (not-for- profit) corporation Prompted by Netscape source code availability press release: http://wp.netscape.com/newsref/pr/newsrelease558.html http://www.opensource.org/ It’s Free, Right? Lots of software is free to download Not necessarily cost-free Need to have programmers to support yourself Need to have infrastructure to participate in development Can be resold by vendors who add value May need to pay for support from a vendor Some free software isn’t open source If You Want Free Software Free Software Foundation Open Source and Free http://www.fsf.org New Idea? No, our operating systems used to be source maintained HASP CMS We were familiar with source management SHARE has a history of sharing improvements in this area (mods) Perhaps Open Source is a new opportunity for us Circle of Life? Twenty-four years ago our favorite vendor extolled the value of Object Code Only control your system programmers reduce maintenance cost improve security and reliability Now Open Source is in (again) control your destiny share development effort match your business needs support “Open Standards” How is it Developed? Several formal projects (Foundries) What’s a Foundry? Foundries provide a place for end-users, developers and other interested parties to communicate, discuss new ideas, and learn about new software and technologies which may benefit them. -

An Empirical Comparison of C, C++, Java, Perl, Python, Rexx, and Tcl
Submission to IEEE Computer An empirical comparison of C, C++, Java, Perl, Python, Rexx, and Tcl Lutz Prechelt ([email protected]) Fakult¨at f¨ur Informatik, Universit¨at Karlsruhe D-76128 Karlsruhe, Germany +49/721/608-4068, Fax: +49/721/608-7343 http://wwwipd.ira.uka.de/˜prechelt/ March 14, 2000 Summary memory consumption, and reliability. 80 implementations of the same set of requirements are We will consider the languages both individually and compared for several properties, such as run time, memory combined into groups: Perl, Python, Rexx, and Tcl and consumption, source text length, comment density, program often called scripting languages and will form one group structure, reliability, and the amount of effort required for called the script group. The name scripting language com- writing them. The results indicate that, for the given pro- monly refers to languages that are for instance (more or gramming problem, which regards string manipulation and less) interpreted rather than compiled, at least during the search in a dictionary, “scripting languages” (Perl, Python, program development phase, and that do typically not re- Rexx, Tcl) are more productive than “conventional lan- quire variable declarations. The alternative are the more guages” (C, C++, Java). In terms of run time and mem- conventional programming languages which I will call the ory consumption, they often turn out better than Java and non-script group. These languages (C, C++, and Java) are not much worse than C or C++. In general, the differences more or less compiled and require typed variable declara- between languages tend to be smaller than the typical dif- tions. -

Programming: REXX and the Netview Command List Language
IBM Tivoli NetView for z/OS Version 6 Release 2 Programming: REXX and the NetView Command List Language IBM SC27-2861-02 IBM Tivoli NetView for z/OS Version 6 Release 2 Programming: REXX and the NetView Command List Language IBM SC27-2861-02 Note Before using this information and the product it supports, read the information in “Notices” on page 203. This edition applies to version 6, release 2 of IBM Tivoli NetView for z/OS (product number 5697-NV6) and to all subsequent versions, releases, and modifications until otherwise indicated in new editions. This edition replaces SC27-2861-01. © Copyright IBM Corporation 1997, 2013. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures ................................... vii About this publication ............................. ix Intended audience ................................. ix Publications ................................... ix IBM Tivoli NetView for z/OS library .......................... ix Related publications ............................... xi Accessing terminology online ............................ xi Using NetView for z/OS online help .......................... xii Accessing publications online ............................ xii Ordering publications ............................... xii Accessibility ................................... xiii Service Management Connect ............................. xiii Tivoli technical training ............................... xiii Tivoli user groups ................................