Bootstrap, Pc Bios, and Ia32 Memory Modes
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Problem 1 : Write-Based Skippy. Problem 2 : Skippy Variant
CMU 18-746 Storage Systems Assigned: 1 Feb 2010 Spring 2010 Homework 2 Due: 22 Feb 2010 Solutions are due at the beginning of class on the due date and must be typed and neatly organized. Late homeworks will not be accepted. You are permitted to discuss these problems with your classmates; how- ever, your work and answers must be your own. All questions should be directed to the teaching assistant. Problem 1 : Write-based Skippy. Before answering the following two problems, please read the following paper: Microbenchmark-based Extraction of Local and Global Disk Characteristics by Nisha Talagala, Remzi H. Arpaci-Dusseau, and David Patterson (Berkeley TR CSD-99-1063). It is available from the course website. (a) First, describe in words the functionality of lseek. Specifically, what happens when lseek(fd, 1048576, SEEK CUR) is issued? (b) Refer to Figure 1, which shows the result of simulating the Skippy experiment on a disk simulator. Label this graph with the following values: rotational latency, MTM, sectors per track, number of heads, head switch time, and cylinder switch time. Also label the head and cylinder switches. Make sure you mark the parts of the figure that indicate these values. (c) How would Figure 1 change, if the disk were replaced with one that has a higher rotation speed, but is the same in every other respect? (d) If the WRITEs used in the Skippy experiment were replaced with READs, do you think the observed value for MTM would change? Explain your answer. Problem 2 : Skippy variant. Assume the skippy algorithm is replaced with the following: fd = open ( ‘ ‘ raw d i s k d e v i c e ’ ’ ) ; ¡ f o r ( i = 0 ; i measurements ; i + + ) l s e e k ( fd , 0 , SEEK SET ) ; w r i t e ( fd , b u f f e r , SINGLE SECTOR ) ; / / time t h e f o l l o w i n g w r i t e and o u t p u t i , time ¢ / / i i s t h e hop s i z e l s e e k ( fd , i £ SINGLE SECTOR , SEEK SET ) ; w r i t e ( fd , b u f f e r , SINGLE SECTOR ) ; ¤ c l o s e ( fd ) ; Figure 2 shows the results of running this experiment (it is a plot of time vs. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

Computer Organization & Architecture Eie
COMPUTER ORGANIZATION & ARCHITECTURE EIE 411 Course Lecturer: Engr Banji Adedayo. Reg COREN. The characteristics of different computers vary considerably from category to category. Computers for data processing activities have different features than those with scientific features. Even computers configured within the same application area have variations in design. Computer architecture is the science of integrating those components to achieve a level of functionality and performance. It is logical organization or designs of the hardware that make up the computer system. The internal organization of a digital system is defined by the sequence of micro operations it performs on the data stored in its registers. The internal structure of a MICRO-PROCESSOR is called its architecture and includes the number lay out and functionality of registers, memory cell, decoders, controllers and clocks. HISTORY OF COMPUTER HARDWARE The first use of the word ‘Computer’ was recorded in 1613, referring to a person who carried out calculation or computation. A brief History: Computer as we all know 2day had its beginning with 19th century English Mathematics Professor named Chales Babage. He designed the analytical engine and it was this design that the basic frame work of the computer of today are based on. 1st Generation 1937-1946 The first electronic digital computer was built by Dr John V. Atanasoff & Berry Cliford (ABC). In 1943 an electronic computer named colossus was built for military. 1946 – The first general purpose digital computer- the Electronic Numerical Integrator and computer (ENIAC) was built. This computer weighed 30 tons and had 18,000 vacuum tubes which were used for processing. -

Lecture 5: Feb 4Th, 2020 5.1 OS Boot Process
CMPSCI 577 Operating Systems Design and Implementation Spring 2020 Lecture 5: Feb 4th, 2020 Lecturer: Prashant Shenoy Scribe: Serena Chan 5.1 OS Boot Process While seemingly mundane and not directly relevant to the modifications we will be making in this course, understanding the OS boot process is important for modifying the kernel. There are six steps that take the machine to a running state from when it is first turned on. 5.1.1 Step 1: BIOS (Basic Input/Output System) The BIOS is a small piece of code that lives in the firmware and is the first software that runs upon boot. When the computer is turned on, the BIOS runs the Power-on Self Test, where the RAM is initialized and hardware such as disks and peripherals are identified and checked. Once the disk is found, the BIOSwill start the boot process from the disk (‘bootstrapping’). The BIOS is often stored on EEPROM/ROM (read-only memory); because of its hardware-specific nature, it is not designed to be easily user modifiable. In addition, since the BIOS is the lowest level of softwarein the PC, it also acts as an interface for the OS to perform I/O and communicate with hardware. 5.1.2 Step 2: MBR (Master Boot Record) The MDR is the first 512 bytes of memory and consists of three components. In particular, thefirst440 bytes contain the bootstrap code that is used to continue the boot process, or the 1st stage boot loader; this is executed by the BIOS. The functionality of the code is to simply search through the partition table and find the root partition, where is where the OS resides. -

Virus Infection Techniques: Boot Record Viruses
Virus Infection Techniques: Boot Record Viruses Bill Harrison CS4440/7440 Malware Analysis and Defense Reading } Start reading Chapter 4 of Szor 2 Virus Infection Techniques } We will survey common locations of virus infections: MBR (Master Boot Record) Boot sector Executable files (*.EXE, *.COM, *.BAT, etc.) } Most of the examples of these viruses, especially the first two types, are from the DOS and floppy disk era 3 Why Study Older Viruses? } Vulnerabilities remain very similar over time, along with the means to exploit them and defend against them } Modern Internet worms differ mainly in the use of the internet for transport, and are otherwise similar to older viruses } Older viruses illustrate the virus vs. antivirus battle over many generations 4 Boot-up Infections and the PC Boot-up Sequence } PC boot-up sequence: 1. BIOS searches for boot device (might be a diskette, hard disk, or CD-ROM) 2. MBR (Master Boot Record) is read into memory from the beginning of the first disk partition; execution proceeds from memory 5 Master Boot Record Structure Boot-up Sequence cont’d. 3. Beginning of MBR has tiny code called the boot- strap loader 4. Data area within MBR has the disk PT (partition table) 5. Boot-strap loader reads PT and finds the active boot partition 6. Boot-strap loader loads the first sector of the active partition into memory and jumps to it; this is called the boot sector 7 Boot-up Sequence cont’d. } MBR is always at BIOS the very first sector of the hard MBR: Expanded View MBR Boot-strap loader code (446 disk (first 512 -

Patching DOS 5 and up for the Pcjr
Patching DOS 5 and up for the PCjr November 29th, 2020 [email protected] Background Patching DOS 5+ Theory of operation Preparing a DOS 5 disk Patching the DOS 5+ disk Create FORMATJR.COM Hard drive installation Fdisk and create a DOS partition Format the hard drive partition Appendix A - Wiping out a boot sector Background The PCjr shipped in 1983 in two configurations: a 64KB machine with no floppy disk drive or a 128KB machine with a single floppy disk drive. The architecture of the machine has the video buffer “borrow” memory from the main memory of the machine. With the standard 16KB video buffer this makes the available RAM either 48KB or 112KB. IBM never offered a hard drive solution. Adding extra memory to a PCjr became possible, but it required a device driver to be loaded at boot time. Microsoft, Tecmar, and other vendors provided device drivers with their memory expansions. The best of the device drivers was a shareware program called jrConfig written by Larry Newcomb. jrConfig can be downloaded from http://www.brutman.com/PCjr/pcjr_downloads.html. The original version of DOS that shipped with the PCjr was PC DOS 2.1. DOS versions 2.1 through 3.3 work on the machine as is. To run DOS 5 or later two things are required: ● Extra memory is required. While extra memory is useful for DOS 2.1 - 3.3, DOS 5 won’t even boot on a small system. I BM formally states the requirement is 512KB and the PCjr is not supported. ● DOS 5 can be patched to work on a PCjr even though it is not supported. -

Lecture 7 Slides
✬ ✩ Computer Science CSCI 251 Systems and Networks Dr. Peter Walsh Department of Computer Science Vancouver Island University [email protected] ✫ 1: Computer Science CSCI 251 — Lecture 7 ✪ ✬ ✩ Virtualization Process • CPU virtualization Address Space • memory virtualization File • persistent storage virtualization ✫ 2: Computer Science CSCI 251 — Lecture 7 ✪ ✬ ✩ Formatting Low Level • sector creation • sector addressing using LBA (Logical Block Addressing) e.g., (cylinder 0, head 0, sector 1) = LBA 0, (cylinder 0, head 0, sector 2) = LBA 1 etc. • usually completed at time of manufacture Partitioning • each physical disk can be divided into partitions • a partition is a logical disk under OS control High Level • typically involves file system creation ✫ 3: Computer Science CSCI 251 — Lecture 7 ✪ ✬ ✩ IBM PC Basic I/O System (BIOS) BIOS • firmware executes on power-on startup • assumes disk data structure and boot-loader code starting at LBA 0 of bootable disk Legacy BIOS • LBA 0 contains MBR (Master Boot Record) • MBR contains the partition table • a partition entry contains a 32 bit start LBA field UEFI (Unified Extensible Firmware Interface) • GPT (GUID Partition Table) starts at LBA 0 • GPT contains the partition table • a partition entry contains a 64 bit start LBA field ✫ 4: Computer Science CSCI 251 — Lecture 7 ✪ ✬ ✩ IBM PC Basic I/O System (BIOS) cont. 3ΤΙςΕΞΜΡΚ7]ΩΞΙΘ &−37 9)∗− 4ΕςΞΜΞΜΣΡ 1&6 +48 4ΕςΞΜΞΜΣΡ 8ΕΦΠΙ 8ΕΦΠΙ &ΣΣΞ &ΣΣΞ 0ΣΕΗΙς 0ΣΕΗΙς −&14∋,ΕςΗ[ΕςΙ ✫ 5: Computer Science CSCI 251 — Lecture 7 ✪ ✬ ✩ IDE Devices Controller • typically can support 4 drives (2 ports) Old Naming Convention Device Name Port# Drive# /dev/hda 1 1 /dev/hdb 1 2 /dev/hdc 2 3 /dev/hdd 2 4 New Naming Convention Device Name Port# Drive# /dev/sda 1 1 /dev/sdb 1 2 /dev/sdc 2 3 /dev/sdd 2 4 ✫ 6: Computer Science CSCI 251 — Lecture 7 ✪ ✬ ✩ SATA Devices Controller • typically can support 2 - 6 drives (2 - 6 ports) Naming Convention Device Name Port# Drive# /dev/sda 1 1 /dev/sdb 2 2 ....... -
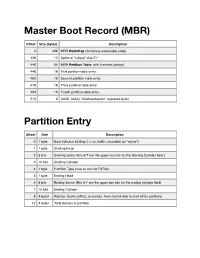
Master Boot Record (MBR)
Master Boot Record (MBR) Offset Size (bytes) Description 0 436 MBR Bootstrap (flat binary executable code) 436 10 Optional "unique" disk ID1 446 64 MBR Partition Table, with 4 entries (below) 446 16 First partition table entry 462 16 Second partition table entry 478 16 Third partition table entry 494 16 Fourth partition table entry 510 2 (0x55, 0xAA) "Valid bootsector" signature bytes Partition Entry Offset Size Description 0 1 byte Boot indicator bit flag: 0 = no, 0x80 = bootable (or "active") 1 1 byte Starting head 2 6 bits Starting sector (Bits 6-7 are the upper two bits for the Starting Cylinder field.) 3 10 bits Starting Cylinder 4 1 byte Partition Type (0xB or 0xC for FAT32). 5 1 byte Ending Head 6 6 bits Ending Sector (Bits 6-7 are the upper two bits for the ending cylinder field) 7 10 bits Ending Cylinder 8 4 bytes Relative Sector (offset, in sectors, from start of disk to start of the partition) 12 4 bytes Total Sectors in partition BIOS Parameter Block (BPB) Offset Size Meaning (bytes) (bytes) 0 3 The first three bytes EB XX 90 disassemble to JMP SHORT XX NOP. 3 8 OEM identifier. 11 2 The number of Bytes per sector (all numbers are in the little-endian format). 13 1 Number of sectors per cluster. 14 2 Number of reserved sectors. The boot record sectors are included in this value. 16 1 Number of File Allocation Tables (FAT's) on the storage media. Often 2. 17 2 Max # of directory entries (0 for FAT32 which stores directories in data region). -

6.823 Computer System Architecture
6.823 Computer System Architecture Instructors: Daniel Sanchez and Joel Emer TA: Hyun Ryong (Ryan) Lee What you’ll understand after The processor you taking 6.823 built in 6.004 September 8, 2021 MIT 6.823 Fall 2021 L01-1 Computing devices then… September 8, 2021 MIT 6.823 Fall 2021 L01-2 Computing devices now September 8, 2021 MIT 6.823 Fall 2021 L01-3 A journey through this space • What do computer architects actually do? • Illustrate via historical examples – Early days: ENIAC, EDVAC, and EDSAC – Arrival of IBM 650 and then IBM 360 – Seymour Cray – CDC 6600, Cray 1 – Microprocessors and PCs – Multicores – Cell phones • Focus on ideas, mechanisms, and principles, especially those that have withstood the test of time September 8, 2021 MIT 6.823 Fall 2021 L01-4 Abstraction layers Application Algorithm Parallel computing, Programming Language specialization, Original Operating System/Virtual Machine security, … domain of the Instruction Set Architecture (ISA) Domain of computer Microarchitecture computer architect architecture (‘90s) (‘50s-‘80s) Register-Transfer Level (RTL) Circuits Reliability, power Devices Expansion of Physics computer architecture, mid- 2000s onward. September 8, 2021 MIT 6.823 Fall 2021 L01-5 Computer Architecture is the design of abstraction layers • What do abstraction layers provide? – Environmental stability within generation – Environmental stability across generations – Consistency across a large number of units • What are the consequences? – Encouragement to create reusable foundations: • Toolchains, operating systems, libraries – Enticement for application innovation September 8, 2021 MIT 6.823 Fall 2021 L01-6 Technology is the dominant factor in computer design Technology Transistors Computers Integrated circuits VLSI (initially) Flash memories, … Technology Core memories Computers Magnetic tapes Disks Technology ROMs, RAMs VLSI Computers Packaging Low Power September 8, 2021 MIT 6.823 Fall 2021 L01-7 But Software.. -

Programming the IBM 650
RICHARD v ANDREE ASSOCIATE PROFESSOR OF MATHEMATIC S UNIVERSITY OF OKLAH O MA c - .....- If' '" .. " \ ' 0 .. N G OA t .. ........ ".•0t0l .... --\I'• .Q\; ....... -, OtU;t1Q1t•" ~ .;. ... 1<• ..,'0<" ~ut .....ucnooo ....' U .. "CO Olffhl.. Ow I • ~ 0 0 4. • 0 0 &8CMltU ~ aut\lU '-'Sfb&tJTOIt L ~ ItI~ :U· IlCII'.'" tu.II _ ife» '-'*' QHaAnoe , ...."a SfOfJ SINN no-C .~~' . '. - " ..,. I ( , I. • • • • • • • • "'f"'. ~.. • ',01 ~ IoOW1I ~ _ ....... ... ,~..- J 4«t* , no.. .., , , 't' ' \' , ,.' ~ .' ;' .. I~ MOGt£MMtO NW oa. • 0 0 • • " ,. ~ I ( ,. I 0 If • C()trl:ft.Ol ~. DGPUoy ovtut&'W ~ '''0'1 -- , , . ' I .. .. 'I O(.. IAM (O MJI ~T! " ,I,(Cu' ~I"O""¥I .. ~ .•• ~, I I I "'.' I HH;( I __ ~ S1"" I SlO'. ~ I IlUf HUT U$U l......... ' , • j ~ ~., " id , ~j ~' ·;1 ,IJ ', ',' .' • t., ." '" (, It \ t \' .. , '.3 ~: . f .. _ ... ~ .. ~ ~ . " ' . , '. \t J \' '' ':l!~ t. ','l ) '. J '\ :..' ~. , • , • • ,_ r: .. ' : ,' rW , Ii •• , ' . ~ • " f ,,;. " ,',.' • -elf!" ~-iJ~ !) , r "" ... _, _ _ .. ... .. - ".'" 't. ~" ~ _ ~ f. _ _ ." ~'f--_ _ i __ ~ '* - ;. 4 ' ~ ! /~ RICHARD V. ANDREE ASSOCIATE PROFESSOR OF MATHEMATICS UNIVERSITY OF OKLAHOMA U U U 11 ;J n I] HOLT, RINEHART AND WINSTON, INC. 383 MADISON AVENUE, NEW YORK 17, N. Y. Dedication II II I I I I I II I I I I I III I I II I 1111 " I I I I II I III I I I I III I II 10000010000010000000111000000000100000110010000001000001000000000110000000000000 1 2 3 4 5 6 7 8 9 1011121314151617181920212223242526 272829 JO 313233343536 37 38 39 40414243« 45 46 47 48 49 50 5152535455565158596061626364656667686970717213747576 -

Booting up and Shutting Down
Booting Up and Shutting Down lctseng (2019-2020, CC BY-SA) ? (1996-2018) 交大資工系資訊中心 Computer Center of Department of Computer Science, NCTU 1 Handbook and Manual pages ● Complete guide and be found at ○ https://www.freebsd.org/doc/en/books/handbook/boot.html ○ https://www.freebsd.org/doc/zh_TW/books/handbook/boot.html 2 Booting Overview - After Powering On ● BIOS (Basic Input/Output System) - stored on motherboard ○ Find MBR in the bootable media (disk,cd,usb stick,...) ● MBR (Master Boot Record) - stored on the first sector of disk/media ○ Record partition information of the disk ○ Load boot loader in Boot Sector (prompt if multiple choices available) ● Boot Sector - stored in the each slice (outside of usual file system) ○ Recognize FreeBSD file system. Find kernel loader under /boot ● Kernel loader - stored in main file system (all below) ○ Show booting prompt and load selected kernel ● OS Kernel ○ Initialize hardware/drivers ● Init ○ Mount filesystem, acquire DHCP, start shell, ... 3 MBR – Master Boot Record ● First 512 bytes of disk, outside the FreeBSD filesystem ○ Last 2 Bytes are 0x55AA ○ Corresponding copy in FreeBSD is /boot/boot0 or /boot/mbr nctucs [~] -lctseng- ls -l /boot/boot0 -r--r--r-- 1 root Wheel 512 Nov 12 2014 /boot/boot0 nctucs [~] -lctseng- ls -l /boot/mbr -r--r--r-- 1 root Wheel 512 Nov 12 2014 /boot/mbr nctucs [~] -lctseng- xxd /boot/mbr 00000000: fc31 c08e c08e d88e d0bc 007c be1a 7cbf .1.........|..|. 00000010: 1a06 b9e6 01f3 a4e9 008a 31f6 bbbe 07b1 ..........1..... … 000001d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................ 000001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ............... -

History of Digital Storage White Paper
History of Digital Storage Dean Klein Vice President of System Memory Development Micron Technology, Inc. December 15, 2008 Purpose Introduction: Throughout modern history many and various digital The Need to Store Data storage systems have been researched, developed, Since men first scribbled on cave walls, humanity has manufactured, and eventually surpassed in an effort to recognized the instrinic value of information and has address ever-increasing demands for density, operating employed a variety of ways and means to safely store speed, low latency, endurance, and economy.1 This cycle it. The ability to reference numbers for calculation or to of innovation has lead us to a new generation of NAND review information for planning, learning, and action Flash memory-based solid state drives (SSDs) that repre- is fundamental since “all computations, either mental, sent the next evolutionary step in both enterprise and mechanical, or electronic require a storage system of consumer storage applications. some kind, whether the numbers be written on paper, remembered in our brain, counted on the mechanical This paper surveys the memory storage landscape of devices of a gear, punched as holes in paper, or translated the past 50 years—starting at the beginning of digital into electronic circuitry.”2 storage and paying homage to IBM’s groundbreaking RAMAC disk storage unit and StorageTek’s DRAM-based In day-to-day life, this fundamental need to store data SSD; then enumerating the benefits of modern NAND generates innumerable documents, spreadsheets, files, Flash memory and advanced SSDs; and finally looking e-mails, and trillions of other work-related bytes all forward to the near-future possibilities of nonvolatile stored on disks around the globe.