Porting Kernel Code to Four Bsds and Linux
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

BSD UNIX Toolbox: 1000+ Commands for Freebsd, Openbsd and Netbsd Christopher Negus, Francois Caen
To purchase this product, please visit https://www.wiley.com/en-bo/9780470387252 BSD UNIX Toolbox: 1000+ Commands for FreeBSD, OpenBSD and NetBSD Christopher Negus, Francois Caen E-Book 978-0-470-38725-2 April 2008 $16.99 DESCRIPTION Learn how to use BSD UNIX systems from the command line with BSD UNIX Toolbox: 1000+ Commands for FreeBSD, OpenBSD and NetBSD. Learn to use BSD operation systems the way the experts do, by trying more than 1,000 commands to find and obtain software, monitor system health and security, and access network resources. Apply your newly developed skills to use and administer servers and desktops running FreeBSD, OpenBSD, NetBSD, or any other BSD variety. Become more proficient at creating file systems, troubleshooting networks, and locking down security. ABOUT THE AUTHOR Christopher Negus served for eight years on development teams for the UNIX operating system at the AT&T labs, where UNIX was created and developed. He also worked with Novell on UNIX and UnixWare development. Chris is the author of the bestselling Fedora and Red Hat Linux Bible series, Linux Toys II, Linux Troubleshooting Bible, and Linux Bible 2008 Edition. Francois Caen hosts and manages business application infrastructures through his company Turbosphere LLC. As an open- source advocate, he has lectured on OSS network management and Internet services, and served as president of the Tacoma Linux User Group. He is a Red Hat Certified Engineer (RHCE). To purchase this product, please visit https://www.wiley.com/en-bo/9780470387252. -

Lecture 1: Introduction to UNIX
The Operating System Course Overview Getting Started Lecture 1: Introduction to UNIX CS2042 - UNIX Tools September 29, 2008 Lecture 1: UNIX Intro The Operating System Description and History Course Overview UNIX Flavors Getting Started Advantages and Disadvantages Lecture Outline 1 The Operating System Description and History UNIX Flavors Advantages and Disadvantages 2 Course Overview Class Specifics 3 Getting Started Login Information Lecture 1: UNIX Intro The Operating System Description and History Course Overview UNIX Flavors Getting Started Advantages and Disadvantages What is UNIX? One of the first widely-used operating systems Basis for many modern OSes Helped set the standard for multi-tasking, multi-user systems Strictly a teaching tool (in its original form) Lecture 1: UNIX Intro The Operating System Description and History Course Overview UNIX Flavors Getting Started Advantages and Disadvantages A Brief History of UNIX Origins The first version of UNIX was created in 1969 by a group of guys working for AT&T's Bell Labs. It was one of the first big projects written in the emerging C language. It gained popularity throughout the '70s and '80s, although non-AT&T versions eventually took the lion's share of the market. Predates Microsoft's DOS by 12 years! Lecture 1: UNIX Intro The Operating System Description and History Course Overview UNIX Flavors Getting Started Advantages and Disadvantages Lecture Outline 1 The Operating System Description and History UNIX Flavors Advantages and Disadvantages 2 Course Overview Class Specifics 3 -

The Dragonflybsd Operating System
1 The DragonFlyBSD Operating System Jeffrey M. Hsu, Member, FreeBSD and DragonFlyBSD directories with slightly over 8 million lines of code, 2 million Abstract— The DragonFlyBSD operating system is a fork of of which are in the kernel. the highly successful FreeBSD operating system. Its goals are to The project has a number of resources available to the maintain the high quality and performance of the FreeBSD 4 public, including an on-line CVS repository with mirror sites, branch, while exploiting new concepts to further improve accessible through the web as well as the cvsup service, performance and stability. In this paper, we discuss the motivation for a new BSD operating system, new concepts being mailing list forums, and a bug submission system. explored in the BSD context, the software infrastructure put in place to explore these concepts, and their application to the III. MOTIVATION network subsystem in particular. A. Technical Goals Index Terms— Message passing, Multiprocessing, Network The DragonFlyBSD operating system has several long- operating systems, Protocols, System software. range technical goals that it hopes to accomplish within the next few years. The first goal is to add lightweight threads to the BSD kernel. These threads are lightweight in the sense I. INTRODUCTION that, while user processes have an associated thread and a HE DragonFlyBSD operating system is a fork of the process context, kernel processes are pure threads with no T highly successful FreeBSD operating system. Its goals are process context. The threading model makes several to maintain the high quality and performance of the FreeBSD guarantees with respect to scheduling to ensure high 4 branch, while exploring new concepts to further improve performance and simplify reasoning about concurrency. -

BSD UNIX Toolbox 1000+ Commands for Freebsd, Openbsd
76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page i BSD UNIX® TOOLBOX 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iv BSD UNIX® Toolbox: 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD® Power Users Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2008 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN: 978-0-470-37603-4 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 Library of Congress Cataloging-in-Publication Data is available from the publisher. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permis- sion should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions. -

Mandoc: Becoming the Main BSD Manual Toolbox
mandoc: becoming the main BSD manual toolbox BSDCan 2015, June 13, Ottawa Ingo Schwarze <[email protected]> Cynthia Livingston’sOTTB “Bedifferent” (c) 2013 C. Livingston (with permission) > Ingo Schwarze: mandoc page 2: INTROI BSDCan 2015, June 13, Ottawa Brief history of UNIX documentation • The key point: All documentation in one place and one format. Easy to find, uniform and easy to read and write. Be correct, complete, concise. • 1964: RUNOFF/roffmarkup syntax by Jerome H. Saltzer,MIT. Unobtrusive,diff(1)-friendly,easy to hand-edit, simple tools, high quality output. • 1971: Basic manual structure by Ken Thompson and Dennis Ritchie for the AT&T Version 1 UNIX manuals, Bell Labs. • 1979: man(7) physical markup language for AT&T Version 7 UNIX. • 1989: mdoc(7) semantic markup by Cynthia Livingston for 4.3BSD-Reno. Powerful, self-contained, portable. • 1989: GNU troffbyJames Clarke. • 2001: mdoc(7) rewrite by Werner Lemberg and Ruslan Ermilovfor groff-1.17. • 2008: mandoc(1) started by Kristaps Dzonsons. • 2010: mandoc(1) is the only documentation formatter in the OpenBSD base system. • 2014: mandoc(1) used by default in OpenBSD, FreeBSD, NetBSD, illumos. 16:19:30 What is the mandoc toolbox? → < > Ingo Schwarze: mandoc page 3: INTROIIBSDCan 2015, June 13, Ottawa What is the mandoc toolbox? User perspective:man(1), the manual viewer One comprehensive tool! Normal operation always proceeds in three steps: 1. Find one or more manuals in the file system or using a database by manual name — man(1) — or by search query — apropos(1) =man -k The result of this step can be printed out with man -w. -

OPENBSD HARDWARE SENSORS FRAMEWORK a Unified and Ready-To-Use System for Hassle-�Ee Hardware Monitoring
OPENBSD HARDWARE SENSORS FRAMEWORK A unified and ready-to-use system for hassle-ee hardware monitoring. Constantine A. Murenin and Raouf Boutaba University of Waterloo AsiaBSDCon 2009 — 12–15 March 2009 — Tokyo, Japan Abstract In this paper, we will discuss the origin, history, design guidelines, API and the device drivers of the hardware sensors framework available in OpenBSD. The framework spans multiple utilities in the base system and the ports tree, is utilised by over 70 drivers, and is considered to be a distinctive and ready-to-use feature that sets OpenBSD apart from many other operating systems, and in its root is inseparable from the OpenBSD experience. 1. Introduction Another trend that has been particularly common in the recent years is the availability of defined inter- We will start by investigating into the matter of what faces for software-based temperature readout from hardware monitoring sensors represent, how common individual components of personal computers, such as is it for them to appear in the general-purpose com- the CPU, or the add-on cards, such as those imple- puter hardware that has been available on the market menting the 802.11 wireless functionality or 10 Giga- in the last decade or so, and what benefits can we gain bit Ethernet. Popular examples include recent Intel by having a unified, simple and straightforward inter- Xeon and Core series of processors (as well as budget face for getting the data out of these sensors. models that are marketed under different brands) Although it may come as a surprise to some users, the [admtemp.4] [cpu.4]; all AMD64 processors from majority of personal computers that have been avail- AMD (Families 0Fh, 10h, 11h) [kate.4] [km.4]; Intel able on the market in the last decade have an inte- WiFi Link 4965/5100/5300 wireless network devices grated hardware monitoring circuitry whose main [iwn.4]. -

History of the Openbsd Hardware Sensors Framework
History of the OpenBSD Hardware Sensors Framework Constantine A. Murenin University of Waterloo AsiaBSDCon 2009 — 12/15 March 2009 — Tokyo, Japan Outline • Introduction • Framework API and utilities • Drivers • I²C Bus Scan • Conclusion What is a sensor? • Any device with a sensor-like data: • temperature • voltage • fan speed • … • logical drive status • time offset Are these common at all? • many Super I/O chips have integrated hardware monitors • Intel Core and AMD K8 / K10 have integrated thermal sensors • IPMI in servers / ACPI in laptops • SCSI enclosures • 10GbE and 802.11 Why sensors framework? • Monitoring environmental values can predict, detect, troubleshoot system failure. (Voltage, temperature, fan, logical drive status.) • Unified interface, no configuration required, works out-of-the-box. • Sensors are fun! Uber cool drivers • sdtemp(4) — SO-DIMM temperature sensors • km(4) — AMD Family 10h processors (Phenom, Opteron Barcelona) and Family 11h (Turion X2 Ultra et al) neither of these two are in Linux yet! http://theos.com/deraadt/jc-42.4-pic1.jpg http://theos.com/deraadt/jc-42.4-pic2.jpg Design decisions • Keep it simple, secure and usable • Make it work by default • Overengineering is useless — many devices have incomplete specifications • No buttons™ How voltage sensors work? • Most chips have sensors from 0 to 4 V • Excess voltage removed by resistors • Resistor “recommendations” How voltage sensors read? function maths result original readin’ 0xcb 203 sensor voltage 203 * 16 mV 3.24 V scale for +5 V 3.24 V * 1.68 5.44 V scale for +12 V 3.24 V * 3.80 12.31 V Resistor recommendations • Ignored by some motherboard designers • Not given in documentation for some chips • Results: • voltage “doesn’t scale” • do the best with what you have Framework API /sys/sys/sensors.h • struct sensor / struct sensordev, transport over sysctl(3) • sensor description, e.g. -

A Brief History of Unix
A Brief History of Unix Tom Ryder [email protected] https://sanctum.geek.nz/ I Love Unix ∴ I Love Linux ● When I started using Linux, I was impressed because of the ethics behind it. ● I loved the idea that an operating system could be both free to customise, and free of charge. – Being a cash-strapped student helped a lot, too. ● As my experience grew, I came to appreciate the design behind it. ● And the design is UNIX. ● Linux isn’t a perfect Unix, but it has all the really important bits. What do we actually mean? ● We’re referring to the Unix family of operating systems. – Unix from Bell Labs (Research Unix) – GNU/Linux – Berkeley Software Distribution (BSD) Unix – Mac OS X – Minix (Intel loves it) – ...and many more Warning signs: 1/2 If your operating system shows many of the following symptoms, it may be a Unix: – Multi-user, multi-tasking – Hierarchical filesystem, with a single root – Devices represented as files – Streams of text everywhere as a user interface – “Formatless” files ● Data is just data: streams of bytes saved in sequence ● There isn’t a “text file” attribute, for example Warning signs: 2/2 – Bourne-style shell with a “pipe”: ● $ program1 | program2 – “Shebangs” specifying file interpreters: ● #!/bin/sh – C programming language baked in everywhere – Classic programs: sh(1), awk(1), grep(1), sed(1) – Users with beards, long hair, glasses, and very strong opinions... Nobody saw it coming! “The number of Unix installations has grown to 10, with more expected.” — Ken Thompson and Dennis Ritchie (1972) ● Unix in some flavour is in servers, desktops, embedded software (including Intel’s management engine), mobile phones, network equipment, single-board computers.. -
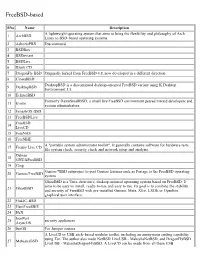
List of BSD Operating Systems
FreeBSD-based SNo Name Description A lightweight operating system that aims to bring the flexibility and philosophy of Arch 1 ArchBSD Linux to BSD-based operating systems. 2 AskoziaPBX Discontinued 3 BSDBox 4 BSDeviant 5 BSDLive 6 Bzerk CD 7 DragonFly BSD Originally forked from FreeBSD 4.8, now developed in a different direction 8 ClosedBSD DesktopBSD is a discontinued desktop-oriented FreeBSD variant using K Desktop 9 DesktopBSD Environment 3.5. 10 EclipseBSD Formerly DamnSmallBSD; a small live FreeBSD environment geared toward developers and 11 Evoke system administrators. 12 FenestrOS BSD 13 FreeBSDLive FreeBSD 14 LiveCD 15 FreeNAS 16 FreeSBIE A "portable system administrator toolkit". It generally contains software for hardware tests, 17 Frenzy Live CD file system check, security check and network setup and analysis. Debian 18 GNU/kFreeBSD 19 Ging Gentoo/*BSD subproject to port Gentoo features such as Portage to the FreeBSD operating 20 Gentoo/FreeBSD system GhostBSD is a Unix-derivative, desktop-oriented operating system based on FreeBSD. It aims to be easy to install, ready-to-use and easy to use. Its goal is to combine the stability 21 GhostBSD and security of FreeBSD with pre-installed Gnome, Mate, Xfce, LXDE or Openbox graphical user interface. 22 GuLIC-BSD 23 HamFreeSBIE 24 HeX IronPort 25 security appliances AsyncOS 26 JunOS For Juniper routers A LiveCD or USB stick-based modular toolkit, including an anonymous surfing capability using Tor. The author also made NetBSD LiveUSB - MaheshaNetBSD, and DragonFlyBSD 27 MaheshaBSD LiveUSB - MaheshaDragonFlyBSD. A LiveCD can be made from all these USB distributions by running the /makeiso script in the root directory. -

Openafs: BSD Clients 2009
OpenAFS: BSD Clients 2009 Matt Benjamin <[email protected]> OpenAFS: BSD Clients 2009 Who am I? ● OpenAFS developer interested in various new-code development topics ● for the last while, “portmaster” for BSD clients except DARWIN/MacOS X ● involves evolving the ports, interfacing withusers and port maintainers in the BSD communities OpenAFS: BSD Clients 2009 Former Maintainers ● Tom Maher, MIT ● Jim Rees, University of Michigan (former Gatekeeper and Elder) ● Garret Wollman, MIT OpenAFS: BSD Clients 2009 Other Active ● Ben Kaduk (FreeBSD) ● Tony Jago (FreeBSD) ● Jamie Fournier (NetBSD) OpenAFS: BSD Clients 2009 Historical Remarks ● AFS originated in a BSD 4.2 environment ● extend UFS with coherence across a group of machines ● Terminology in common with BSD, SunOS, etc, e.g., vnodes ● Followed SunOS and Ultrix to Solaris and Digital Unix in Transarc period ● 386BSD released at 4.3 level in the Transarc period, some client development never publically released (or independent of Transarc) OpenAFS: BSD Clients 2009 BSD Clients Today ● Descendents of 386BSD distribution and successors, not including DARWIN/MacOS X ● DARWIN separately maintained, though of course there are similarities OpenAFS: BSD Clients 2009 Today ● FreeBSD ● OpenBSD Soon ● NetBSD ● OpenBSD Not yet supported (as a client): ● Dragonfly BSD OpenAFS: BSD Clients 2009 BSD Port History I ● First 386BSD port probably that of John Kohl (MIT), for NetBSD ● First to appear in OpenAFS is FreeBSD, by Tom Maher ● Next to appear in OpenAFS is OpenBSD, by Jim Rees ● Significant evolution -

Free, Functional, and Secure
Free, Functional, and Secure Dante Catalfamo What is OpenBSD? Not Linux? ● Unix-like ● Similar layout ● Similar tools ● POSIX ● NOT the same History ● Originated at AT&T, who were unable to compete in the industry (1970s) ● Given to Universities for educational purposes ● Universities improved the code under the BSD license The License The license: ● Retain the copyright notice ● No warranty ● Don’t use the author's name to promote the product History Cont’d ● After 15 years, the partnership ended ● Almost the entire OS had been rewritten ● The university released the (now mostly BSD licensed) code for free History Cont’d ● AT&T launching Unix System Labories (USL) ● Sued UC Berkeley ● Berkeley fought back, claiming the code didn’t belong to AT&T ● 2 year lawsuit ● AT&T lost, and was found guilty of violating the BSD license History Cont’d ● BSD4.4-Lite released ● The only operating system ever released incomplete ● This became the base of FreeBSD and NetBSD, and eventually OpenBSD and MacOS History Cont’d ● Theo DeRaadt ○ Originally a NetBSD developer ○ Forked NetBSD into OpenBSD after disagreement the direction of the project *fork* Innovations W^X ● Pioneered by the OpenBSD project in 3.3 in 2002, strictly enforced in 6.0 ● Memory can either be write or execute, but but both (XOR) ● Similar to PaX Linux kernel extension (developed later) AnonCVS ● First project with a public source tree featuring version control (1995) ● Now an extremely popular model of software development anonymous anonymous anonymous anonymous anonymous IPSec ● First free operating system to implement an IPSec VPN stack Privilege Separation ● First implemented in 3.2 ● Split a program into processes performing different sub-functions ● Now used in almost all privileged programs in OpenBSD like httpd, bgpd, dhcpd, syslog, sndio, etc. -

Recent Security Enhancements in Netbsd
Recent Security Enhancements in NetBSD Elad Efrat < [email protected] > September 2006 Abstract Over the years, NetBSD obtained the position of the BSD focusing on portability. While it is true that NetBSD offers an easily portable operating system, care is also given to other areas, such as security. This paper presents the NetBSD philosophy of security, design decisions, and currently offered security features. Finally, some of the current and future research will be revealed. 1. Introduction Running on almost twenty different architectures, and easily portable to others, NetBSD gained its reputation as the most portable operating system on the planet. While that may indicate high quality code, the ever demanding networked world cares about more than just that. Over the past year, NetBSD evolved quite a bit in various areas; this paper, however, will focus on the aspect relating to security. This paper was written and structured to present a full overview of the recent security enhancements in NetBSD in an easily readable and balanced form that will satisfy new, intermediate, and experienced users. References were sprinkled across the text to provide more information to those who want the gory details, while preserving the continuity. Section 2 will present the bigger picture of security in NetBSD: how NetBSD perceives security, the design decisions of NetBSD software in general and the security infrastructure and features more specifically. Section 3 will present a detailed overview of the recent enhancements in the security infrastructure and features of NetBSD including, where relevant, details about the design, implementation, and possible future development. Section 4 will present current security-related research and development in NetBSD, and section 5 will discuss how the described enhancements work together to provide a more secure platform.