Securing Users and Processes in Oracle® Solaris 11.4
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

80842-Su | Cc/Led/27W/E26-E39/Mv/50K Corn Cob Sunlite
Item: 80842-SU CC/LED/27W/E26-E39/MV/50K CORN COB SUNLITE General Characteristics Bulb Corn Lamp Type Corn Cob Lamp Life Hours 50000 Hours Material Aluminium & Plastic LED Type LG5630 Base Medium (E26) Lumens Per Watt (LPW) 135.00 Life (based on 3hr/day) 45.7 Years Estimated Energy Cost $3.25 per Year Safety Rating UL Listed Ingress Protection IP64 Sunlite CC/LED/27W/E26-E39/MV/50K LED 27W (100W MHL/HPSW Electrical Characteristics Equivalent) Corn Bulb, Medium (E26), Watts 27 5000K Super White Volts 100-277 Equivalent Watts 100 LED Chip Manufacturer LG5630 Sunlite's super efficient LED corn lamps were created to Number of LEDs 84 replace the equivalent but power hungry metal halide and Power Factor 0.9 high-pressure sodium lamps. Capable of withstanding water sprays from any direction in thanks to its IP64 rating, these Temperature -40° To 140° bulbs will keep outdoor paths, back yards and many more locations illuminated for a significantly longer period of time Light Characteristics when compared to a high-pressure sodium lamp or a metal Brightness 3645 Lumens halide while also lowering your electrical usage. Color Accuracy (CRI) 85 Light Appearance Super White Color Temperature 5000K • This modern corn cob lamp produces an efficient 5000K Beam Angle 360° super white beam of 360° light at a powerful 3645 lumens • On average, this multi-volt LED corn cob lamp lasts up to Product Dimensions an astonishing 50,000 hours and features 84 energy MOL (in) 7.4 saving diodes Diameter (in) 3.65 • Ideal for all post lights, Street lights, security Lighting, high Package Dimensions (in) (W) 3.70 (H) 11.90 (D) 3.80 bay lights while also designed for indoor as well as Product Data outdoor usage. -

Unix Security Overview: 1
CIS/CSE 643: Computer Security (Syracuse University) Unix Security Overview: 1 Unix Security Overview 1 User and Group • Users – root: super user (uid = 0) – daemon: handle networks. – nobody: owns no files, used as a default user for unprivileged operations. ∗ Web browser can run with this mode. – User needs to log in with a password. The encrypted password is stored in /etc/shadow. – User information is stored in /etc/passwd, the place that was used to store passwords (not anymore). The following is an example of an entry in this file. john:x:30000:40000:John Doe:/home/john:/usr/local/bin/tcsh • Groups – Sometimes, it is more convenient if we can assign permissions to a group of users, i.e. we would like to assign permission based on groups. – A user has a primary group (listed in /etc/passwd), and this is the one associated to the files the user created. – Any user can be a member of multiple groups. – Group member information is stored in /etc/group % groups uid (display the groups that uid belongs to) – For systems that use NIS (Network Information Service), originally called Yellow Page (YP), we can get the group information using the command ypcat. % ypcat group (can display all the groups and their members) 2 File Permissions • File Permissions – The meaning of the permission bits in Unix. ∗ Owner (u), Group (g), and Others (o). ∗ Readable (r), Writable (w), and Executable (x). ∗ Example: -rwxrwxrwx (777) • Permissions on Directories: – r: the directory can be listed. – w: can create/delete a file or a directory within the directory. -

Lab Intro to Console Commands
New Lab Intro to KDE Terminal Konsole After completing this lab activity the student will be able to; Access the KDE Terminal Konsole and enter basic commands. Enter commands using a typical command line interface (CLI). Explain the use of the following commands, ls, ls –al, dir, mkdir, whoami, Explain the directory structure of a typical user. This lab activity will introduce you to one of the many command line interfaces available in Linux/UNIX operating systems and a few of the most basic commands. The command line interface you will be using for this lab activity is the console called the Konsole and is also referred to as Terminal. Note: As you notice, in the KDE system many features are written with the capital letter “K” in place of the first letter or the utility to reflect the fact it was modified for the KDE system. The original UNIX system did not use a graphical user interface GUI but rather was a command line interface (CLI) similar to the command prompt in Windows operating systems. The command line interface is referred to as a shell. Even today the command line interface (the shell) is used to issue commands on a Linux server to minimize system resources. For example, there is no need to start the GUI on the server to add a new user to an existing system. Starting the GUI will reduce the system performance because it requires RAM to run the GUI. A GUI will affect the overall performance of the server when it is supporting many users (clients). -

Open Data/Open Source: Seismic Unix Scripts to Process a 2D Land Line
Open Data/Open Source: Seismic Unix scripts to process a 2D land line Karl Schleicher k [email protected] John A. and Katherine G. Jackson School of Geosciences The University of Texas at Austin University Station, Box X Austin, TX 78713-8924 (January 29, 2012) Running head: Alaska ABSTRACT This paper describes how to process an internet downloadable 2D land line data set though a very basic processing sequence using Seismic Unix. The data from the Alaska North Slope has good signal, although it may be suitable for testing ground-roll and noise burst attenuation programs. The detailed steps to download the dataset from the Internet and process it are described. You should be able to follow these steps and recreate my results. I hope this will accelerate the testing and validation of programs developed in different research groups. The paper starts with background information such as data downloading, region overview, data acquisition, and previous processing. The scripts and custom programs for Seismic Unix translation, header load, qc, shotrecord velocity filter, deconvolution, CDP gather, velocity analysis, residual statics, stack, and post stack migration can be downloaded to 1 your computer. Header loading is not well described in other Seismic Unix documentation or papers. One approach to header loading is described here. The velocity analysis script is more advanced than what I found in previous publications. This paper is the beginning of an effort to build an open data/open source library for research, software testing, demonstrations, and user training. I encourage you to use these scripts and improve on my results. -

User Accounts User Accounts User Info /Etc/Passwd User Info /Etc
User Accounts Even a single-user workstation (Desktop Computer) uses multiple accounts. Such a computer may have just one user account, but several system accounts help keep the computer running. Accounts enable multiple users to share a single computer without causing each other too much trouble. User Accounts The Users in a Linux system are stored in the /etc/passwd file. If you are on your own VM - somewhere near the bottom you should see yourself and joe. On a brand new install you will see many users listed. Of course if you recall, we only added ourselves and joe. So what are all these other users for? These users are added because we don’t want to give sudo power to all of our programs. So each program installed gets its own user with its own limited permissions. This is a protection for our computer. User Info /etc/passwd Examine the /etc/passwd file using cat or less . Here is what we are seeing: It is colon : separated. So each : denotes a new column. username password The x is just a place-holder. The password is not really in this file User ID (UID) Just like every computer needs a unique ip address, every user needs a unique id. User Info /etc/passwd Group ID (GID) Every user belongs to its own group, with its own group id Comment field This is the Full name, phone number, office number, etc. It is okay if it is blank. Home Directory This is the location of the users home directory - This is how we can know the full path of any users home directory - /home/smorgan vs /home/s/smorgan. -

Unix Commands (09/04/2014)
Unix Commands (09/04/2014) • Access control – login <login_name> – exit – passwd <login_name> – yppassswd <loginname> – su – • Login as Super user – su <login> • Login as user <login> • Root Prompt – [root@localhost ~] # • User Prompt – [bms@raxama ~] $ On Line Documentation – man <command/topic> – info <command/topic> • Working with directories – mkdir –p <subdir> ... {-p create all directories in path if not present} mkdir –p /2015/Jan/21/14 will create /2015, Jan, 21 & 14 in case any of these is absent – cd <dir> – rm -r <subdir> ... Man Pages • 1 Executable programs or shell commands • 2 System calls (functions provided by the kernel) • 3 Library calls (functions within program libraries) • 4 Special files (usually found in /dev) • 5 File formats and conventions eg /etc/passwd • 6 Games • 7 Miscellaneous (including macro packages and conventions), e.g. man(7), groff(7) • 8 System administration commands (usually only for root) • 9 Kernel routines [Non standard] – man grep, {awk,sed,find,cut,sort} – man –k mysql, man –k dhcp – man crontab ,man 5 crontab – man printf, man 3 printf – man read, man 2 read – man info Runlevels used by Fedora/RHS Refer /etc/inittab • 0 - halt (Do NOT set initdefault to this) • 1 - Single user mode • 2 - Multiuser, – without NFS (The same as 3, if you do not have networking) • 3 - Full multi user mode w/o X • 4 - unused • 5 - X11 • 6 - reboot (Do NOT set init default to this) – init 6 {Reboot System} – init 0 {Halt the System} – reboot {Requires Super User} – <ctrl> <alt> <del> • in tty[2-7] mode – tty switching • <ctrl> <alt> <F1-7> • In Fedora 10 tty1 is X. -

Gnu Coreutils Core GNU Utilities for Version 5.93, 2 November 2005
gnu Coreutils Core GNU utilities for version 5.93, 2 November 2005 David MacKenzie et al. This manual documents version 5.93 of the gnu core utilities, including the standard pro- grams for text and file manipulation. Copyright c 1994, 1995, 1996, 2000, 2001, 2002, 2003, 2004, 2005 Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.1 or any later version published by the Free Software Foundation; with no Invariant Sections, with no Front-Cover Texts, and with no Back-Cover Texts. A copy of the license is included in the section entitled “GNU Free Documentation License”. Chapter 1: Introduction 1 1 Introduction This manual is a work in progress: many sections make no attempt to explain basic concepts in a way suitable for novices. Thus, if you are interested, please get involved in improving this manual. The entire gnu community will benefit. The gnu utilities documented here are mostly compatible with the POSIX standard. Please report bugs to [email protected]. Remember to include the version number, machine architecture, input files, and any other information needed to reproduce the bug: your input, what you expected, what you got, and why it is wrong. Diffs are welcome, but please include a description of the problem as well, since this is sometimes difficult to infer. See section “Bugs” in Using and Porting GNU CC. This manual was originally derived from the Unix man pages in the distributions, which were written by David MacKenzie and updated by Jim Meyering. -

UNIQ: Uniform Noise Injection for Non-Uniform Quantization of Neural
UNIQ:U NIFORM N OISE I NJECTIONFOR N ON -U NIFORM Q UANTIZATIONOF N EURAL N ETWORKS Chaim Baskin * 1 Eli Schwartz * 2 Evgenii Zheltonozhskii 1 Natan Liss 1 Raja Giryes 2 Alex Bronstein 1 Avi Mendelson 1 A BSTRACT We present a novel method for neural network quantization that emulates a non-uniform k-quantile quantizer, which adapts to the distribution of the quantized parameters. Our approach provides a novel alternative to the existing uniform quantization techniques for neural networks. We suggest to compare the results as a function of the bit-operations (BOPS) performed, assuming a look-up table availability for the non-uniform case. In this setup, we show the advantages of our strategy in the low computational budget regime. While the proposed solution is harder to implement in hardware, we believe it sets a basis for new alternatives to neural networks quantization. 1 I NTRODUCTION of two reduces the amount of hardware by roughly a factor of four. (A more accurate analysis of the effects of quanti- Deep neural networks are widely used in many fields today zation is presented in Section 4.2). Quantization allows to including computer vision, signal processing, computational fit bigger networks into a device, which is especially crit- imaging, image processing, and speech and language pro- ical for embedded devices and custom hardware. On the cessing (Hinton et al., 2012; Lai et al., 2015; Chen et al., other hand, activations are passed between layers, and thus, 2016). Yet, a major drawback of these deep learning models if different layers are processed separately, activation size is their storage and computational cost. -

Gnu Coreutils Core GNU Utilities for Version 6.9, 22 March 2007
gnu Coreutils Core GNU utilities for version 6.9, 22 March 2007 David MacKenzie et al. This manual documents version 6.9 of the gnu core utilities, including the standard pro- grams for text and file manipulation. Copyright c 1994, 1995, 1996, 2000, 2001, 2002, 2003, 2004, 2005, 2006 Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, with no Front-Cover Texts, and with no Back-Cover Texts. A copy of the license is included in the section entitled \GNU Free Documentation License". Chapter 1: Introduction 1 1 Introduction This manual is a work in progress: many sections make no attempt to explain basic concepts in a way suitable for novices. Thus, if you are interested, please get involved in improving this manual. The entire gnu community will benefit. The gnu utilities documented here are mostly compatible with the POSIX standard. Please report bugs to [email protected]. Remember to include the version number, machine architecture, input files, and any other information needed to reproduce the bug: your input, what you expected, what you got, and why it is wrong. Diffs are welcome, but please include a description of the problem as well, since this is sometimes difficult to infer. See section \Bugs" in Using and Porting GNU CC. This manual was originally derived from the Unix man pages in the distributions, which were written by David MacKenzie and updated by Jim Meyering. -

UNIX System Commands for Nuclear Magnetic Resonance(NMR)
8/25/00 11:41 AM UNIX System Commands For Nuclear Magnetic Resonance(NMR) EMORY Dr. Shaoxiong Wu NMR Research Center at Emory 1996 /xiong/UNIX.doc September 25, 1996 Dr. Shaoxiong Wu The information in this document is based on my own experiences. It has been carefully checked. However, no responsibility is assumed if any one copied this document as their reference. UNIX Commands 10/05/96 12:50 PM Updated Commands for tape operation: Tape Utility %mt -f /dev/rst0 retention (rewind)* Tape Copy %tcopy /dev/rst0 /dev/rst1 rst0-source rst1 --target Tape Dump #/usr/etc/dump 0cdstfu 1000 700 18 /dev/rst0 /dev/sd3c (/dev/sd0a;/dev/sd0g) 150Mb tape This dump can be recovered by mini root!!!! #dump 0cdstfu 1000 425 9 /dev/rst0 /dev/rsd0a On Omega600 (60Mb tape) Recover some files from the dump tape #restore -i restore>ls List files on the tape restore>add file name restore>extract you may extract file into a temp.dir first Tape Backup #../tar cvf /dev/rst0 dir-to-be-backup #../tar tvf /dev/rst0 ---list file on the tape #../tar xvfp /dev/rst0 ./restoredir (current dir) DATA Compression and Tape Backup #tar cf directoryname.tar directoryname ------compress all files in the directoryname #rm -r directoryname #compress directoryname.tar -------a new file name will be -------.tar.Z #tar cvf /dev/rst0 -----tar.Z ------save the file on a tape *******Retrieve the files #tar xvf /dev/rst0 ------tar.Z #uncompress ------tar.Z -----a new file will appear -----.tar 1 /xiong/UNIX.doc September 25, 1996 Dr. -

CST8207 – Linux O/S I
Installation Basic Commands Todd Kelley [email protected] CST8207 – Todd Kelley 1 Installation Root User Command Line Logging On/Off Basic Commands Help Absolute vs. Relative Paths Using Linux at home via VMWare Player 2 Partitions needed for Linux installation ◦ To install Linux, you need to create at least two partitions: / (called root partition) Swap (for virtual memory) ◦ In addition to those two partition, you can create other partitions, such as /boot, /usr … ◦ The filesystem type of Linux native partition is ext2, ext3, or ext4 3 Root is referred to as Super user or administrator in Linux Login as root, you have the all the permissions /privileges to change system settings. So do only what you have to do and know exactly what you are doing. Root user’s home directory ◦ /root Login as root, you can easily create a regular user account by using command useradd 4 Linux GUI is convenient to use ◦ administrators still prefer to use command line utilities to do administration tasks (fast forward – cool administrators use scripts!) Command line utilities run on character-based terminals Command line utilities are often faster, more powerful and complete than their GUI counterparts, sometimes there is no GUI counterpart to a command line utility To run commands in FC12 GNOME environment, ◦ Applications -> System Tools ->Terminal to open a console window 5 There are two approaches to logon and logoff Linux Using Linux command in a console or text mode ◦ At login prompt, type in username and press <Enter>. -
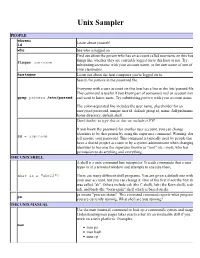
Unix Sampler
Unix Sampler PEOPLE whoami Learn about yourself. id who See who is logged on Find out about the person who has an account called username on this host things like whether they are currently logged on to this host or not. Try finger username subsituting username with your account name, or the user name of one of your classmates. hostname Learn out about the host computer you're logged on to. Search for pattern in the password file. Everyone with a user account on this host has a line in the /etc/passwd file This command is useful if you know part of someone's real or account nam grep pattern /etc/passwd and want to know more. Try substituting pattern with your account name. The colon-separated line includes the user name, placeholder for an encrypted password, unique user id, default group id, name, full pathname home directory, default shell. Don't bother to type this in, but we include it FYI. If you know the password for another user account, you can change identities to be that person by using the superuser command. Warning: don su - username tell anyone your password. This command is typically used by people that have a shared project account or by a system administrator when changing identities to become the superuser known as "root" (su - root), who has permission to do anything and everything. THE UNIX SHELL A shell is a unix command line interpreter. It reads commands that a user types in at a terminal window and attempts to execute them. What is a "shell"? There are many different shell programs.