Considerations, Best Practices and Requirements for a Virtualised Mobile Network CONSIDERATIONS, BEST PRACTICES and REQUIREMENTS for a VIRTUALISED MOBILE NETWORK
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Glossary See Also
Glossary See also: SDN-R Glossary Definitions AAF: Application Authorization Framework fine-grained authorization library and service; one of the ONAP Common Services AAI = A&AI: Active and Available Inventory (component of ONAP runtime) Real-time views of Resources, Services, Products, Customer Subscriptions, and their relationships AID: Architecture Integration Document Akka: handles clustering (used OpenDaylight controllers) akka.io AJSC: see JSC Amsterdam: Code name for the first release of ONAP APPC (formerly APP-C): Application Controller (part of ONAP) handles the life cycle management of Virtual Network Functions (VNFs) Beijing: Code name for the second release of ONAP BPEL: Business Process Execution Language (OASIS Standard) XML-based language that allows Web services in a service-oriented architecture (SOA) to interconnect and share data. BPMN: Business Process Model and Notation (Wikipedia) or Business Process Management Notation (ONAP.pdf) graphical representation for specifying business processes BRMS: Business Rules Management System BSS: Business Support System CCSDK: Common Controller SDK project Code shared across controllers (e.g. SDNC, APP-C) CDAP: Cask Data Application Platform open source framework to build and deploy data applications on Apache™ Hadoop® (CDAP.io site) CDS: Controller Design Studio it is not the tool for the design of controllers instead it is common design tool to support both SDNC and generic L4-7 NF controllers integrated with SDC (e.g. APPC, VFC) part of CCSDK project, see vFW CDS Casablanca - -

Software Defined Networking and Network Function Virtualization: Bridging the World of Virtual Networks
Software Defined Networking and Network Function Virtualization: bridging the world of virtual networks Roberto Morabito Department of Communications and Networking (Comnet), Aalto University, Espoo, Finland [email protected] Abstract— Software Defined Networking (SDN) and Network Function Virtualization (NFV) are two emerging and complementary concepts that can be considered as key players in the virtual networks world. In particular, SDN allows managing different network services through abstraction of higher-level functionality, while NFV leverages the use of virtualization technologies to virtualize specific network functions. Although SDN and NFV are considered stand-alone technologies, they are often put in relationship, because their connections, and overlapped use cases. In this paper, we present a short survey providing an overview of the two different models, highlighting the complementarities, together with the standardization activities and the open source community efforts to make these two paradigms connected to each other. Keywords—Software Defined Networking; SDN; Network Function Virtualization; NFV; I. INTRODUCTION Fig. 1. SDN architecture [4] [INTRODUCTION] à [1,2,3] The remainder of this paper is organized as follows. In Section II, we summarize general background information B. Network Function Virtualization (NFV) about Software Defined Networking (SDN), and Network Function Virtualization (NFV). Section III clarifies the distinctions between SDN and NFV, however emphasizing [6], [7] point of contact and common use cases. In Section IV, a quick overview of ongoing standardization efforts is presented, together with the activities of the Open Source community in the virtual networks world. Section V concludes the paper providing final remarks. II. BACKGROUND In this section, we provide an overview of the different approaches, which are object of the paper. -

OPNFV: Open Source Software to Enable NFV
OPNFV: Open Source Software to Enable NFV Ashiq Khan, PhD DOCOMO R&D TSC Member NTT DOCOMO, INC. Open Platform for NFV CLOUDOPEN Japan June 3, 2015 © 2015, NTT DOCOMO. INC. All Rights Reserved. 1 Contents Telco virtualization and NFV Why open source Open Platform for NFV © 2015, NTT DOCOMO. INC. All Rights Reserved. 2 Lesson learned … Mar 2011 Massive number of call attempts (roughly 60-fold increase) were made. Call restriction control were in place. Earthquake 14:46 Mar.11 Call Restriction Call Restriction 15:00, Mar. 11 – 2:00, Mar. 12 6:00, Mar.12 – 1:00, Mar. 13 <Massive Congestion> 12.6-fold The number of call attempts were increased roughly 60-fold in outgoing and 40-fold in incoming. The number of calls out in 7.9-fold out in After the A week disaster ago Friday, Mar.11 Saturday, Mar.12 source: http://www.soumu.go.jp/menu_news/s-news/01kiban02_02000043.html Deploying resources to process such load is practically impossible © 2015, NTT DOCOMO. INC. All Rights Reserved. 3 Enter virtualization We need a mean to do resource sharing Normal At disaster More on highly demanded More on voice calls etc. to Internet access (Rich media confirm safety of relatives Contents) than voice calls and friends Voice Mail Rich Media (Video etc.) This is a joint research work supported by "Experimental challenges for dynamic virtualized networking resource control over an evolved mobile core network - a new approach to reduce massive traffic congestion after a devastating disaster" of the Ministry of Internal Affairs and Communications, Japan. -

2016 Mega NFV Report Pt. 1: MANO and NFVI
Market Report 2016 Mega NFV Report Pt. 1: MANO and NFVI The Trusted News and Resource Site for SDx, SDN, NFV, Cloud and Virtualization Infrastructure Market Report | 2016 Mega NFV Report Pt. 1: MANO and NFVI contents Table of Contents Introduction – NFV Platforms Grow Up . 1 Investment Benefits of NFV in NFVI and MANO . 3 NFV Architecture . 5 NFV Market Landscape . 11 NFV MANO Products. 16 NFVI Products . 16 NFV Monitoring and Testing Products . 17 Vendor Profiles . 18 MANO and NFVI Products [Featured] Brocade: Brocade SDN Controller . 21 Brocade: Brocade Vyatta Network OS . 22 Cisco Systems, Inc.: Cisco NFV Infrastructure . 23 Cisco Systems, Inc.: Cisco Network Services Orchestrator (NSO) enabled by Tail-f . 23 Cisco Systems, Inc.: Cisco Virtual Topology System (VTS) . 23 Cisco Systems, Inc.: Cisco Elastic Services Controller (ESC) . 23 Juniper Networks, Inc.: Juniper Networks Contrail . 24 Wind River: Titanium Server . .26 MANO ADVA Optical Networking: Ensemble Orchestrator . 27 Affirmed Networks: Affirmed Mobile Content Cloud . 27 Amartus: Chameleon SDS . .27 Anuta Networks, Inc.: Anuta Network NCX . .28 ATTO Research: Athena . 28 Avaya Inc.: Avaya SDN Fx Architecture . 28 Brocade: Brocade VNF Manager . .29 Canonical: Ubuntu OpenStack . 29 CA Technologies: CA Virtual Network Assurance . 29 CENX, Inc: Exanova Service Intelligence . 30 Ciena: Ciena Blue Planet . .30 Ericsson Network Manager & Ericsson Cloud Manager . 30 Fujitsu: Network Virtuora OM and Virtuora RV . 31 Huawei: Huawei FusionSphere . 31 MRV Communications: MRV Pro-Vision . 31 Nakina Systems: NI-CONTROLLER . 32 Nakina Systems: NI-FRAMEWORK . .32 NEC/Netcracker: NEC/Netcracker Orchestration . 32 Nokia: CloudBand . 33 © 2016 SDNCentral LLC. All Rights Reserved. Page ii Market Report | 2016 Mega NFV Report Pt. -

Member Guide January 2019
Member Guide January 2019 www.lfnetworking.org Table of Contents Welcome to LF Networking 3 How to Engage 22 LF Networking Organizational Overview 4 Information for Board Members 23 The Role of the Linux Foundation 6 Marketing Advisory Council (MAC) 24 Your Staff Contacts 7 Technical Advisory Council (TAC) 26 Project Technical Steering 28 Introduction to LF Networking 9 Committees (TSCs) Projects Technical Onboarding 29 FD.io 10 Other Ways to Engage 35 ONAP 11 End User Advisory Groups (EUAGs) 35 OpenDaylight 12 Academic Outreach and Internships 35 OPNFV 13 OSN User Groups 35 PNDA 14 SNAS 15 Tungsten Fabric 16 LFN Support Programs 17 Independent Market Education 18 Compliance and Verification Programs 19 Powered by OpenDaylight 19 OPNFV Verified 19 Training 21 LF Networking Member Guide CHAPTER ONE Welcome to LF Networking Thank you for joining the LF Networking community as a member. Your support is vitally important in sustaining the health and innovative momentum of the LF Networking projects. We’ve written this guide to provide you a complete reference to the LF Networking community. You will learn how to engage with your communities of interest, all the different ways you can contribute, and how to get help when you need it. If you have suggestions for enhancing this guide, please get in touch with LFN staff or email [email protected]. LF Networking Organizational Overview Learn more about LF Networking here: LF Networking (LFN) is a consortium of open source networking projects hosted by the Linux Website Charter Wiki Foundation. The Linux Foundation provides staff members to help manage various operational aspects of these projects, but developing the code and sharing it with the world is in the hands of our passionate developers and other community members. -

I Driver Globali Sul 5G
2 notiziariotecnico anno 26 1/2017 3 volatilità del mercato finanziario, perché dunque attorno al 5G vi è I DRIVER GLOBALI così tanto interesse e discussione ? Come per tutti i libri di maggiore successo e fortuna nel tempo, il SUL 5G 5G si presta a letture molto diver- se ed ogni stakeholder può trovare Gabriele Elia, Pierpaolo Marchese nel 5G ragioni differenti e profonde di necessità e di sviluppo di questa nuova tecnologia che per le sue va- Introduzione ficilmente appariranno sul mercato con contenuti ultra broadband, e rie implicazioni ed aspettative tra- prima del 2020. Si sta addirittura lo stesso avverrà con le Olimpiadi scende il puro fatto tecnico. Di qui Nell’evoluzione della Industry TLC verificando anche una “competi- di Tokio del 2020 che saranno sicu- anche la varietà dei percorsi che, ed Informatica il 5G è sicuramente zione” tra macroregioni economi- ramente trasmesse a qualità video partendo anche da punti di vista e l’Hype del momento. Qualsiasi ri- che, gli USA, l’Asia e l’Europa. In 8K su reti 5G. aspettative differenti, convergono cerca su Google su “5G” restituisce Nord America AT&T e Verizon han- La Commissione Europea ha lan- verso il 5G. migliaia di riferimenti, ogni bollet- no deciso di anticipare al massimo ciano un piano chiamato 5G Action A nostro parere vari sono i drivers tino tecnico che quotidianamente i tempi, anche nei gruppi di stan- Plan [nota 1] per stimolare, facili- che guidano questi percorsi, ma al- riceviamo comprende almeno un dardizzazione, almeno per poter tare e armonizzare le iniziative in cuni si impongono più di altri: approfondimento 5G. -
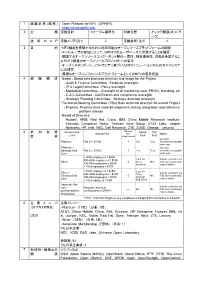
1 組織名称 ( 略称 ) Open Platform for NFV (OPNFV)
1 組織名称( 略称) Open Platform for NFV (OPNFV) https://www.opnfv.org/ 2 分類 活動目的 フォーラム標準化 対象分野 インフラ関連(ネットワ ーク) 技術MAP 活動エリア(注1) -2 活動技術(注2) -1 3 目 的 ・NFV機能を構築するために利用可能なオープンソースプラットフォームの開発 ・エンドユーザの参加によって、OPNFVがユーザニーズに合致することを確認 ・関連するオープンソースコンポーネント間の一貫性、相互運用性、性能を確認するこ とでNFV関連のオープンソースプロジェクトへの寄与 ・オープンスタンダード、ソフトウェアに基づいたNFVソリューションのためのエコシステ ムの確立 ・最適なオープンレファレンスプラットフォームとしてのNFVの普及促進 4 組織構成 ・Board : Board sets business direction and scope for the Project - Audit & Finance Committee : Financial oversight - IP & Legal Committee : Policy oversight - Marketing Committee : Oversight of all marketing; web, PR/AR, branding, etc - C & C Committee : Certification and compliance oversight - Strategic Planning Committee : Strategic direction oversight ・Technical Steering Committee (TSC):Sets technical direction for overall Project - Projects: Projects drive code development, testing, integration and reference platform release ・Board of Directors: Huawei, ARM, Red Hat, Cisco, IBM, China Mobile Research Institute, Ericsson, Canonical, Nokia, Telecom Italia Group, AT&T Labs, Juniper Networks, HP, Intel, NEC, Dell Research, ZTE, SUSE, Orange, Lenovo) Minimum 5 参加資格 Membership Board TSC Annual Fee FTE* Notes Level Seat Seat 会費 Requirement 2yr initial Platinum Flat fee: $200k 2 Yes Yes commitment, payable each year Platinum – 2yr initial Strategic End Flat fee: $100k 1 Yes Yes commitment, payable User each year > 5000 employees = $50K 500-4999 employees = $30K 1 per 10 Can be elected to the Silver 0 Silver No TSC as a community 100-499 employees = $20K members representative < 100 employees = $10K > 5000 employees = $25K 1 per 10 Silver – Can be elected to the 500-4999 employees = $15K Silver Strategic End 0 No TSC as a community 100-499 employees = $10K Strategic User representative < 100 employees = $5K End Users Associate (for non- Requires technical Can be elected to the ← No No TSC as a community profit/academic contributions to OPNFV representative institutions) * FTE = Full Time Engineer (e.g. -

5G-PPP Vision on Software Networks
White Paper – Software Networks WG Vision on Software Networks and 5G SN WG – January 2017 (final version 2.0) 1 White Paper – Software Networks WG Table of Contents 1 Introduction .......................................................................................................................... 3 2 NFV and SDN and 5G ............................................................................................................. 4 3 Terminology .......................................................................................................................... 5 4 Combining NFV and SDN: architectural trends and existing gaps ........................................ 7 4.1 Introduction: early steps combining NFV and SDN ....................................................... 7 4.2 An architecture proposal to integrate NFV and SDN for 5G ......................................... 9 4.3 Some examples of software network features and scenarios .................................... 10 4.3.1 Cloud RAN............................................................................................................ 10 4.3.2 Mobile Edge Computing ...................................................................................... 11 4.3.3 Multi-domain/Multi-provider Orchestration ...................................................... 13 4.3.4 Network Programmability ................................................................................... 16 4.3.5 Network slicing ................................................................................................... -

The SDN, NFV & Network Virtualization Bible
The SDN, NFV & Network Virtualization Bible: 2015 – 2020 Opportunities, Challenges, Strategies & Forecasts Table of Contents 1 Chapter 1: Introduction ................................................................................... 20 1.1 Executive Summary ....................................................................................................................................... 20 1.2 Topics Covered .............................................................................................................................................. 22 1.3 Forecast Segmentation ................................................................................................................................. 23 1.4 Key Questions Answered ............................................................................................................................... 25 1.5 Key Findings ................................................................................................................................................... 27 1.6 Methodology ................................................................................................................................................. 28 1.7 Target Audience ............................................................................................................................................ 29 1.8 Companies & Organizations Mentioned ....................................................................................................... 30 2 Chapter 2: An Overview of SDN, NFV -

A Primer on NFV (Release 1.0) March 2016
NFV INTERNATIONAL INTERCONNECTION FORUM FOR SERVICES OVER IP (i3 FORUM) (www.i3forum.org) Source: i3 forum keyword: NFV A Primer on NFV (Release 1.0) March 2016 This document provides the i3 forum’s perspective on NFV, focusing on the role of and the impact to international carriers. It does not intend to duplicate other existing specifications or documents on the same issue, but to complement these documents with the perspective of the international carrier members of i3 forum. “A Primer on NFV”, Release 1.0 – March 8, 2016 1 NFV Table of Contents 1. Scope and Objective of the Document ................................................................ 3 2. Acronyms ............................................................................................................ 4 3. Introduction .......................................................................................................... 5 3.1. What Is NFV? ................................................................................................... 5 3.2. What Has Enabled NFV? .................................................................................. 6 4. NFV Drivers ......................................................................................................... 7 5. NFV Market Data ................................................................................................. 8 5.1. Infonetics .......................................................................................................... 8 5.2. SDxCentral ...................................................................................................... -

A Comprehensive Survey of Network Function Virtualization
Computer Networks 133 (2018) 212–262 Contents lists available at ScienceDirect Computer Networks journal homepage: www.elsevier.com/locate/comnet Review article A comprehensive survey of Network Function Virtualization ∗ Bo Yi a, Xingwei Wang b, , Keqin Li c, Sajal k. Das d, Min Huang e a College of Computer Science and Engineering, Northeastern University, Shenyang 110169, China b College of Software, Northeastern University, Shenyang 110169, China c Department of Computer Science, State University of New York, New York 12561, USA d Department of Computer Science, Missouri University of Science and Technology, Rolla, MO 65409, USA e College of Information Science and Engineering, State Key Laboratory of Synthetical Automation for Process Industries, Northeastern University, Shenyang 110819, China a r t i c l e i n f o a b s t r a c t Article history: Today’s networks are filled with a massive and ever-growing variety of network functions that coupled Received 13 April 2017 with proprietary devices, which leads to network ossification and difficulty in network management and Revised 15 January 2018 service provision. Network Function Virtualization (NFV) is a promising paradigm to change such situa- Accepted 17 January 2018 tion by decoupling network functions from the underlying dedicated hardware and realizing them in the form of software, which are referred to as Virtual Network Functions (VNFs). Such decoupling introduces Keywords: many benefits which include reduction of Capital Expenditure (CAPEX) and Operation Expense (OPEX), Network Function Virtualization improved flexibility of service provision, etc. In this paper, we intend to present a comprehensive survey Virtual network function on NFV, which starts from the introduction of NFV motivations. -

NFV and OPNFV
NFV and OPNFV Stanislav Guerassimov Betreuer: Edwin Cordeiro, Lukas Schwaighofer Seminar Innovative Internettechnologien und Mobilkommunikation SS2016 Lehrstuhl Netzarchitekturen und Netzdienste Fakultät für Informatik, Technische Universität München Email: [email protected] ABSTRACT along with existing OPNFV versions, projects and architec- The demand for flexible and economically viable cloud com- ture. The reader will become familiarized with theoretical puting and virtualization technologies is continuously in- concept designs for NFV, including NFV in the datacenter creasing. In this paper we discuss how Network Function and even in industrial automation systems in section 4, as Virtualization (NFV) enables simplified network function well as with existing industry implementations of NFV in management and other benefits and challenges that it brings. section 5. We also note major NFV standardization efforts, while de- scribing OPNFV in depth. Further, this paper introduces a couple of use-cases for NFV, such as deployment alongside 2. NFV SDN in a datacenter and even deployment in industrial au- Unlike server virtualization, network virtualization is not a tomation systems. We also provide a collection of analyses mature technology that is widely adapted. of existing pilot implementations of NFV. As a result, this paper should provide the reader with an up-to-date state of Network virtualization has the same goals as server virtual- network function virtualization technologies. ization. Analogous to those technologies, NFV should allow the network and it’s functions to appear to hosts as a real physical ones. This should allow network engineers to deploy Keywords previously physical networking devices as software applica- NFV OPNFV network function virtualization tions.