A Comprehensive Survey of Network Function Virtualization
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Examining Factors of the NFV-I Impacting Performance and Portability
WHITE PAPER Examining Factors of the NFV-I Impacting Performance and Portability www.ixiacom.com 915-0953-01 Rev. A, May 2015 2 Table of Contents Introduction ................................................................................................. 4 Compute Platform ........................................................................................ 7 CPU/Motherboard and Storage .............................................................. 8 CPU Pinning ........................................................................................... 9 Logical Processor Support ................................................................... 11 QuickPath Interconnect (QPI) ...............................................................12 Packet Processing Enhancements and Acceleration ............................13 Storage .................................................................................................16 Network Interface Cards (NICs) .................................................................17 PCI Passthrough ...................................................................................18 Single Root I/O Virtualization (SR-IOV) ...............................................18 Host OS and Hypervisor ............................................................................21 Open Source NFV-I Platforms ............................................................. 23 Know the Performance Curve ............................................................. 24 Virtual Networking ................................................................................... -

Considerations, Best Practices and Requirements for a Virtualised Mobile Network CONSIDERATIONS, BEST PRACTICES and REQUIREMENTS for a VIRTUALISED MOBILE NETWORK
Considerations, Best Practices and Requirements for a Virtualised Mobile Network CONSIDERATIONS, BEST PRACTICES AND REQUIREMENTS FOR A VIRTUALISED MOBILE NETWORK About the GSMA Network 2020 Contents The GSMA represents the interests of mobile operators The GSMA’s Future Networks Programme is designed to worldwide, uniting nearly 800 operators with almost 300 help operators and the wider mobile industry to deliver all-IP companies in the broader mobile ecosystem, including handset networks so that everyone benefits regardless of where their and device makers, software companies, equipment providers starting point might be on the journey. and internet companies, as well as organisations in adjacent industry sectors. The GSMA also produces industry-leading The programme has three key work-streams focused on: events such as Mobile World Congress, Mobile World Congress The development and deployment of IP services, The 5.1.4 NFV carrier-grade reliability scope 24 Shanghai, Mobile World Congress Americas and the Mobile 360 evolution of the 4G networks in widespread use today, 1 Introduction 3 Series of conferences. The 5G Journey developing the next generation of mobile 1.1 Scope 4 5.2 Carrier Grade Service – Requirements 26 technologies and service. 1.2 Definitions 4 for NFV Reliability For more information, please visit the GSMA corporate website at www.gsma.com. Follow the GSMA on Twitter: @GSMA. For more information, please visit the Network 2020 website 1.3 Abbreviations 5 5.3 NFV Reliability Assessment Standard 26 at: www.gsma.com/network2020 -

Glossary See Also
Glossary See also: SDN-R Glossary Definitions AAF: Application Authorization Framework fine-grained authorization library and service; one of the ONAP Common Services AAI = A&AI: Active and Available Inventory (component of ONAP runtime) Real-time views of Resources, Services, Products, Customer Subscriptions, and their relationships AID: Architecture Integration Document Akka: handles clustering (used OpenDaylight controllers) akka.io AJSC: see JSC Amsterdam: Code name for the first release of ONAP APPC (formerly APP-C): Application Controller (part of ONAP) handles the life cycle management of Virtual Network Functions (VNFs) Beijing: Code name for the second release of ONAP BPEL: Business Process Execution Language (OASIS Standard) XML-based language that allows Web services in a service-oriented architecture (SOA) to interconnect and share data. BPMN: Business Process Model and Notation (Wikipedia) or Business Process Management Notation (ONAP.pdf) graphical representation for specifying business processes BRMS: Business Rules Management System BSS: Business Support System CCSDK: Common Controller SDK project Code shared across controllers (e.g. SDNC, APP-C) CDAP: Cask Data Application Platform open source framework to build and deploy data applications on Apache™ Hadoop® (CDAP.io site) CDS: Controller Design Studio it is not the tool for the design of controllers instead it is common design tool to support both SDNC and generic L4-7 NF controllers integrated with SDC (e.g. APPC, VFC) part of CCSDK project, see vFW CDS Casablanca - -

Software Defined Networking and Network Function Virtualization: Bridging the World of Virtual Networks
Software Defined Networking and Network Function Virtualization: bridging the world of virtual networks Roberto Morabito Department of Communications and Networking (Comnet), Aalto University, Espoo, Finland [email protected] Abstract— Software Defined Networking (SDN) and Network Function Virtualization (NFV) are two emerging and complementary concepts that can be considered as key players in the virtual networks world. In particular, SDN allows managing different network services through abstraction of higher-level functionality, while NFV leverages the use of virtualization technologies to virtualize specific network functions. Although SDN and NFV are considered stand-alone technologies, they are often put in relationship, because their connections, and overlapped use cases. In this paper, we present a short survey providing an overview of the two different models, highlighting the complementarities, together with the standardization activities and the open source community efforts to make these two paradigms connected to each other. Keywords—Software Defined Networking; SDN; Network Function Virtualization; NFV; I. INTRODUCTION Fig. 1. SDN architecture [4] [INTRODUCTION] à [1,2,3] The remainder of this paper is organized as follows. In Section II, we summarize general background information B. Network Function Virtualization (NFV) about Software Defined Networking (SDN), and Network Function Virtualization (NFV). Section III clarifies the distinctions between SDN and NFV, however emphasizing [6], [7] point of contact and common use cases. In Section IV, a quick overview of ongoing standardization efforts is presented, together with the activities of the Open Source community in the virtual networks world. Section V concludes the paper providing final remarks. II. BACKGROUND In this section, we provide an overview of the different approaches, which are object of the paper. -

OPNFV: Open Source Software to Enable NFV
OPNFV: Open Source Software to Enable NFV Ashiq Khan, PhD DOCOMO R&D TSC Member NTT DOCOMO, INC. Open Platform for NFV CLOUDOPEN Japan June 3, 2015 © 2015, NTT DOCOMO. INC. All Rights Reserved. 1 Contents Telco virtualization and NFV Why open source Open Platform for NFV © 2015, NTT DOCOMO. INC. All Rights Reserved. 2 Lesson learned … Mar 2011 Massive number of call attempts (roughly 60-fold increase) were made. Call restriction control were in place. Earthquake 14:46 Mar.11 Call Restriction Call Restriction 15:00, Mar. 11 – 2:00, Mar. 12 6:00, Mar.12 – 1:00, Mar. 13 <Massive Congestion> 12.6-fold The number of call attempts were increased roughly 60-fold in outgoing and 40-fold in incoming. The number of calls out in 7.9-fold out in After the A week disaster ago Friday, Mar.11 Saturday, Mar.12 source: http://www.soumu.go.jp/menu_news/s-news/01kiban02_02000043.html Deploying resources to process such load is practically impossible © 2015, NTT DOCOMO. INC. All Rights Reserved. 3 Enter virtualization We need a mean to do resource sharing Normal At disaster More on highly demanded More on voice calls etc. to Internet access (Rich media confirm safety of relatives Contents) than voice calls and friends Voice Mail Rich Media (Video etc.) This is a joint research work supported by "Experimental challenges for dynamic virtualized networking resource control over an evolved mobile core network - a new approach to reduce massive traffic congestion after a devastating disaster" of the Ministry of Internal Affairs and Communications, Japan. -

2016 Mega NFV Report Pt. 1: MANO and NFVI
Market Report 2016 Mega NFV Report Pt. 1: MANO and NFVI The Trusted News and Resource Site for SDx, SDN, NFV, Cloud and Virtualization Infrastructure Market Report | 2016 Mega NFV Report Pt. 1: MANO and NFVI contents Table of Contents Introduction – NFV Platforms Grow Up . 1 Investment Benefits of NFV in NFVI and MANO . 3 NFV Architecture . 5 NFV Market Landscape . 11 NFV MANO Products. 16 NFVI Products . 16 NFV Monitoring and Testing Products . 17 Vendor Profiles . 18 MANO and NFVI Products [Featured] Brocade: Brocade SDN Controller . 21 Brocade: Brocade Vyatta Network OS . 22 Cisco Systems, Inc.: Cisco NFV Infrastructure . 23 Cisco Systems, Inc.: Cisco Network Services Orchestrator (NSO) enabled by Tail-f . 23 Cisco Systems, Inc.: Cisco Virtual Topology System (VTS) . 23 Cisco Systems, Inc.: Cisco Elastic Services Controller (ESC) . 23 Juniper Networks, Inc.: Juniper Networks Contrail . 24 Wind River: Titanium Server . .26 MANO ADVA Optical Networking: Ensemble Orchestrator . 27 Affirmed Networks: Affirmed Mobile Content Cloud . 27 Amartus: Chameleon SDS . .27 Anuta Networks, Inc.: Anuta Network NCX . .28 ATTO Research: Athena . 28 Avaya Inc.: Avaya SDN Fx Architecture . 28 Brocade: Brocade VNF Manager . .29 Canonical: Ubuntu OpenStack . 29 CA Technologies: CA Virtual Network Assurance . 29 CENX, Inc: Exanova Service Intelligence . 30 Ciena: Ciena Blue Planet . .30 Ericsson Network Manager & Ericsson Cloud Manager . 30 Fujitsu: Network Virtuora OM and Virtuora RV . 31 Huawei: Huawei FusionSphere . 31 MRV Communications: MRV Pro-Vision . 31 Nakina Systems: NI-CONTROLLER . 32 Nakina Systems: NI-FRAMEWORK . .32 NEC/Netcracker: NEC/Netcracker Orchestration . 32 Nokia: CloudBand . 33 © 2016 SDNCentral LLC. All Rights Reserved. Page ii Market Report | 2016 Mega NFV Report Pt. -

Cisco Live 2014
Introduction to Software-Defined Networking (SDN) and Network Programmability BRKSDN-1014 Jason Davis, Distinguished Engineer (Services) Abstract SDN is an exciting new approach to network IT Service Management. You may have questions about SDN, Controllers, APIs, Overlays, OpenFlow and ACI. You may also be wondering what products and services are SDN-enabled and how you can solve your unique business challenges and enhance your differentiated services by leveraging network programmability. In this introductory session we will cover the genesis of SDN, what it is, what it is not, and Cisco's involvement in this space. Cisco's SDN- enabled Products and Services will be explained enabling you to consider your own implementations. Since SDN extends network flexibility and functionality which impacts Network Engineering and Operations teams, we'll also cover the IT Service Management impact. Network engineers, network operation staff, IT Service Managers, IT personnel managers, and application/compute SMEs will benefit from this session. BRKSDN-1014 © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Public 3 Agenda • What is SDN & Network Programmability • What are the Use Cases and Problems Solved with SDN? • An Overview of OpenFlow • What Are Cisco's solutions? • An Overview of Network Overlays • An Overview of Network Controllers • An Overview of ACI • The Impact to IT Service Management • How to Get Ready BRKSDN-1014 © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Public 4 What is Software-Defined Networking (SDN)? • An approach and architecture in networking where control and data planes are decoupled and intelligence and state are logically centralized • Enablement where underlying network infrastructure is abstracted from the applications [network virtualization] • A concept that leverages programmatic interfaces to enable external systems to influence network provisioning, control and operations BRKSDN-1014 © 2015 Cisco and/or its affiliates. -

Member Guide January 2019
Member Guide January 2019 www.lfnetworking.org Table of Contents Welcome to LF Networking 3 How to Engage 22 LF Networking Organizational Overview 4 Information for Board Members 23 The Role of the Linux Foundation 6 Marketing Advisory Council (MAC) 24 Your Staff Contacts 7 Technical Advisory Council (TAC) 26 Project Technical Steering 28 Introduction to LF Networking 9 Committees (TSCs) Projects Technical Onboarding 29 FD.io 10 Other Ways to Engage 35 ONAP 11 End User Advisory Groups (EUAGs) 35 OpenDaylight 12 Academic Outreach and Internships 35 OPNFV 13 OSN User Groups 35 PNDA 14 SNAS 15 Tungsten Fabric 16 LFN Support Programs 17 Independent Market Education 18 Compliance and Verification Programs 19 Powered by OpenDaylight 19 OPNFV Verified 19 Training 21 LF Networking Member Guide CHAPTER ONE Welcome to LF Networking Thank you for joining the LF Networking community as a member. Your support is vitally important in sustaining the health and innovative momentum of the LF Networking projects. We’ve written this guide to provide you a complete reference to the LF Networking community. You will learn how to engage with your communities of interest, all the different ways you can contribute, and how to get help when you need it. If you have suggestions for enhancing this guide, please get in touch with LFN staff or email [email protected]. LF Networking Organizational Overview Learn more about LF Networking here: LF Networking (LFN) is a consortium of open source networking projects hosted by the Linux Website Charter Wiki Foundation. The Linux Foundation provides staff members to help manage various operational aspects of these projects, but developing the code and sharing it with the world is in the hands of our passionate developers and other community members. -

Can Open-Source Projects (Re-)Shape the SDN/NFV-Driven Telecommunication Market?
DE GRUYTER OLDENBOURG it – Information Technology 2015; 57(5): 267–276 Special Issue Wouter Tavernier*, Bram Naudts, Didier Colle, Mario Pickavet, and Sofie Verbrugge Can open-source projects (re-)shape the SDN/NFV-driven telecommunication market? DOI 10.1515/itit-2015-0026 ACM CCS: Networks → Network services → Programmable Received June 30, 2015; revised July 17, 2015; accepted July 20, 2015 networks Abstract: Telecom network operators face rapidly chang- ing business needs. Due to their dependence on long prod- uct cycles they lack the ability to quickly respond to chang- 1 Introduction ing user demands. To spur innovation and stay competi- tive, network operators are investigating technological so- The increased softwarization and programmability have lutions with a proven track record in other application do- changed the telecom landscape significantly. Whereas mains such as open source software projects. Open source communication networks previously were under the rigid software enables parties to learn, use, or contribute to control of vendor-specific solutions or tightly standardized technology from which they were previously excluded. protocols, Software-Defined Networking (SDN) enabled OSS has reshaped many application areas including the network operators to configure the control of their net- landscape of operating systems and consumer software. works through their-own custom software. Network Func- The paradigm shift in telecommunication systems towards tion Virtualization (NFV) pushes this even further by mak- Software-Defined Networking introduces possibilities to ing it possible to code data plane behavior in software, en- benefit from open source projects. Implementing the con- abling it to run on general purpose server hardware rather trol part of networks in software enables speedier adap- than on expensive vendor-controlled hardware platforms. -

D2.1 Horizon 2020 – 732497 – 5GINFIRE
Deliverable D2.1 Horizon 2020 – 732497 – 5GINFIRE D2.1 - 5GinFIRE Experimental Infrastructure Architecture and 5G Automotive Use Case Editor: Riwal Kerherve, B-COM Deliverable nature: Report (R) Dissemination level: Public (PU) Date: planned | actual 30 April 2017 26 May 2017 Version | No. of pages 1.0 113 Keywords: State of the art, use cases, architecture, 5G, MANO, Automotive, Smart cities Abstract This deliverable is the first technical deliverable of the project. It is the result of the project work to establish the baseline of the state of the art in cloud computing, Software Defined Networking (SDN), Network Function Virtualisation (NFV) and Service Function Chaining (SFC). It captures a snapshot of available technologies and components. In addition this deliverable describes the use cases that will be demonstrated later in the project. Finally it describes the first draft 5GinFIRE architecture that will be deployed by the project. This deliverable is the basis for the future work of the project on Experimentation Architecture Tooling, Core MANO Service Management and Orchestration, as well as 5G Infrastructure Integration and Experimentation Enablement. Page 1 of (113) Horizon 2020 – 732497 – 5GINFIRE Deliverable D2.1 Disclaimer This document contains material, which is the copyright of certain 5GINFIRE consortium parties, and may not be reproduced or copied without permission. All 5GINFIRE consortium parties have agreed to full publication of this document. Neither the 5GINFIRE consortium as a whole, nor a certain part of the 5GINFIRE consortium, warrant that the information contained in this document is capable of use, nor that use of the information is free from risk, accepting no liability for loss or damage suffered by any person using this information. -
Prosupport Suite and Premium Support
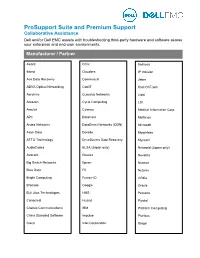
ProSupport Suite and Premium Support Collaborative Assistance Dell and/or Dell EMC assists with troubleshooting third-party hardware and software across your enterprise and end-user environments. Manufacturer / Partner 4ward Citrix Invincea 6wind Cloudera IP Infusion Ace Data Recovery Commvault Jabra ADVA Optical Networking CoolIT Kroll OnTrack Aerohive Cumulus Networks Liqid Amazon Cycle Computing LSI Amulet Cylance Medical Information Corp. APC DataCore Mellanox Aruba Networks DataDirect Networks (DDN) Microsoft Aster Data Dorado Morphlabs ATTO Technology DriveSavers Data Recovery Myricom AudioCodes ELSA (Japan only) Networld (Japan only) Avocent Emulex Nexenta Big Switch Networks Epson Nuance Blue Data F5 Nutanix Bright Computing Fusion-IO nVidia Brocade Google Oracle Bull Atos Technologies HMS Pentaho Canonical Huarui Pivotal Chelsio Communications IBM Platform Computing China Standard Software Impulse Pluribus Cisco Intel Corporation Qlogic QNAP Quantum Rackspace Red Hat SanDisk SAP1 Scality Silver Peak Software AG Solarflare Splunk StackIQ Stratus SUSE Symantec ThinkParq ThinLaunch Unicon/eLux Unidesk VeloCloud Versa Networks VMware Vormetric Wave 1. Customer must initiate case with SAP directly. SAP initiates collaboration requests with Dell and/or Dell EMC. Wind River Customer equipment and devices must be covered by manufacturer's warranty or customer provided maintenance contractXerox for Dell to engage with third-party vendor and to qualify for Dell collaborative assistance. Collaborative partners are subject to change without notice. Not all regions, products, and versions may be included in the scope of collaborative assistance. Product and service availability vary by country. Contact Dell for more information. Copyright © 2019 Dell Inc. or its subsidiaries. All Rights Reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. -

MANO-Deployed Virtual Router Simplifies Network Deployments
SOLUTION BRIEF Communications Service Providers Virtual Routers MANO-Deployed Virtual Router Simplifies Network Deployments 6WIND,* Advantech,* and Cloudify* create virtual routers with simplified deployment and lifecycle management to scale networks. Italian CommSP EOLO* utilizes this solution to create a backbone mesh connecting thousands of wireless base stations. Virtual routers provide the functionality of legacy, fixed-function routers with more flexibility and lower cost. The next step for communications service providers (CommSPs) who have embraced this technology and are deploying thousands of these virtual network functions (VNFs) throughout their network is to add management and network orchestration (MANO) features that can provide better configuration, deployment, and lifecycle management functions to all of the vRouters in a network. 6WIND,* Cloudify,* and Advantech*—all Intel® Network Builders ecosystem partners—have integrated their technologies to provide a MANO-deployed vRouter solution. vRouters Need MANO A virtual router is a virtual network function (VNF) application that runs on commercial off-the-shelf (COTS) server platforms and replaces legacy routers that run on fixed-function hardware appliances. The use of COTS servers typically makes vRouters less expensive to purchase, while the remote deployability and life cycle management of software-based vRouters reduces the cost to operate routed networks. Virtual router companies like 6WIND have made significant progress on evolving vRouter software. With new Intel® Xeon® Scalable processors and packet forwarding technology such as the open source Data Plane Development Kit (DPDK), vRouters can offer the outstanding performance that CommSPs require.¹ Now, 6WIND is tackling the challenge of mass deployment and management of vRouter networks by working with MANO software from Cloudify.