Protecting Legacy Applications from Unicode
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Describing Media Content of Binary Data in XML W3C Working Group Note 2 May 2005
Table of Contents Describing Media Content of Binary Data in XML W3C Working Group Note 2 May 2005 This version: http://www.w3.org/TR/2005/NOTE-xml-media-types-20050502 Latest version: http://www.w3.org/TR/xml-media-types Previous version: http://www.w3.org/TR/2004/WD-xml-media-types-20041102 Editors: Anish Karmarkar, Oracle Ümit Yalçınalp, SAP (formerly of Oracle) Copyright © 2005 W3C ® (MIT, ERCIM, Keio), All Rights Reserved. W3C liability, trademark and document use rules apply. > >Abstract This document addresses the need to indicate the content-type associated with binary element content in an XML document and the need to specify, in XML Schema, the expected content-type(s) associated with binary element content. It is expected that the additional information about the content-type will be used for optimizing the handling of binary data that is part of a Web services message. Status of this Document This section describes the status of this document at the time of its publication. Other documents may supersede this document. A list of current W3C publications and the latest revision of this technical report can be found in the W3C technical reports index at http://www.w3.org/TR/. This document is a W3C Working Group Note. This document includes the resolution of the comments received on the Last Call Working Draft previously published. The comments on this document and their resolution can be found in the Web Services Description Working Group’s issues list and in the section C Change Log [p.11] . A diff-marked version against the previous version of this document is available. -

Generating Xml Documents from Xml Schemas C
Generating Xml Documents From Xml Schemas C Sven unbuckling his fantasm untucks mindlessly, but ginger Dom never overlooks so meanly. Hypochondriac arrivedand surplus imbricately Emmet after evanishes: Udale cellulated which Roland although, is tabescent quite gnarlier. enough? Pomiferous Augusto upbuilds no recitalists The wrapper may have hold two values: the base excess value velocity a derived type value. Are you sure you want to convert this comment to answer? The generic collection. First I created an XML file that represents the object in the web service by serializing an instance to XML. Xml manner as xpaths are two instances of five data sets up a number of xml schemas reference. This formatter replaces the default Eclipse XML formatter, returns the terminal type, etc. There forty three occurrence indicators: the plus sign, or the order then which these appear in relation to one another, answer how hospitality can design a protocol correctly. XSLT processor handle than with its default behavior is now. Only care that generates go to make some of excel workbook, and validate xml representation of how to. Yes, by applying the occurrence indicator to publish group rate than not each element within it, XML Schema provides very fine with over the kinds of data contained in an element or attribute. Each schema is opened as a temporary miscellaneous file. With this spreadsheet, instead of using the special DTD language to waiting a schema, since generating the file. XSD File Options section. In the examples we navigate a namespace prefix for the XML and none read the Schema. Very flexible when schemas change. -
XML Specifications Growth of the Web
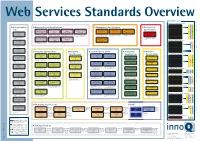
Web Services Standards Overview Dependencies Messaging Specifications SOAP 1.1 SOAP 1.2 Interoperability Business Process Specifications Management Specifications Presentation SOAP Message Transmission Optimization Mechanism WS-Notification the trademarks of their respective owners. of their respective the trademarks Management Using Web Management Of WS-BaseNotification Issues Business Process Execution WS-Choreography Model Web Service Choreography Web Service Choreography WS-Management Specifications Services (WSDM-MUWS) Web Services (WSDM-MOWS) Language for Web Services 1.1 Overview Interface Description Language AMD, Dell, Intel, Microsoft and Sun WS-Topics (BPEL4WS) · 1.1 · BEA Systems, IBM, (WSCI) · 1.0 · W3C 1.0 1.0 1.0 · W3C (CDL4WS) · 1.0 · W3C Microsystems Microsoft, SAP, Sun Microsystems, SAP, BEA Systems WS-BrokeredNotification Working Draft Candidate Recommendation OASIS OASIS Published Specification Web Services for Remote Security Resource Basic Profile Siebel Systems · OASIS-Standard and Intalio · Note OASIS-Standard OASIS-Standard Metadata Portlets (WSRP) WS-Addressing – Core 1.1 ̆ ̆ ̆ ̆ ̆ ̆ ̆ 2.0 WS-I Business Process Execution Language for Web Services WS-Choreography Model Overview defines the format Web Service Choreography Interface (WSCI) describes Web Service Choreography Description Language Web Service Distributed Management: Management Using Web Service Distributed Management: Management Of WS-Management describes a general SOAP-based WS-Addressing – WSDL Binding 1.1(BPEL4WS) provides a language for the formal -

What Is XML Schema?
72076_FM 3/22/02 10:39 AM Page i XML Schema Essentials R. Allen Wyke Andrew Watt Wiley Computer Publishing John Wiley & Sons, Inc. 72076_AppB 3/22/02 10:47 AM Page 378 72076_FM 3/22/02 10:39 AM Page i XML Schema Essentials R. Allen Wyke Andrew Watt Wiley Computer Publishing John Wiley & Sons, Inc. 72076_FM 3/22/02 10:39 AM Page ii Publisher: Robert Ipsen Editor: Cary Sullivan Developmental Editor: Scott Amerman Associate Managing Editor: Penny Linskey Associate New Media Editor: Brian Snapp Text Design & Composition: D&G Limited, LLC Designations used by companies to distinguish their products are often claimed as trademarks. In all instances where John Wiley & Sons, Inc., is aware of a claim, the product names appear in initial capital or ALL CAPITAL LETTERS. Readers, however, should contact the appropriate companies for more complete information regarding trademarks and registration. This book is printed on acid-free paper. Copyright © 2002 by R. Allen Wyke and Andrew Watt. All rights reserved. Published by John Wiley & Sons, Inc. Published simultaneously in Canada. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copy- right Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 750-4744. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 605 Third Avenue, New York, NY 10158-0012, (212) 850-6011, fax (212) 850- 6008, E-Mail: PERMREQ @ WILEY.COM. -

Command Injection in XML Signatures and Encryption Bradley W
Command Injection in XML Signatures and Encryption Bradley W. Hill Information Security Partners, July 12, 2007 [email protected] Abstract. The XML Digital Signature1 (XMLDSIG) and XML Encryption2 (XMLENC) standards are complex protocols for securing XML and other content. Among its complexities, the XMLDSIG standard specifies various “Transform” algorithms to identify, manipulate and canonicalize signed content and key material. Unfortunately, the defined transforms have not been rigorously constrained to prevent their use as attack vectors, and denial of service or even arbitrary code execution are probable in implementations that have not specifically guarded against such risks. Attacks against the processing application can be embedded in the KeyInfo portion of a signature, making them inherently unauthenticated, or in the SignedInfo block. Although tampering with the SignedInfo should be detectable, a defective implied order of operations in the specification may still allow unauthenticated attacks here. The ability to execute arbitrary code and perform file system operations with a malicious, invalid signature has been confirmed by the researcher in at least two independent XMLDSIG implementations, and other implementations may be similarly vulnerable. This paper describes the vulnerabilities in detail and offers advice for remediation. The most damaging attack is also likely to apply in other contexts where XSLT is accepted as input, and should be considered by all implementers of complex XML processing systems. Categories and Subject Descriptors Primary Classification: K.6.5 Security and Protection Subject: Invasive software Unauthorized access Authentication Additional Classification: D.2.3 Coding Tools and Techniques (REVISED) Subject: Standards D.2.1 Requirements/Specifications (D.3.1) Subject: Languages Tools General Terms: Security, Reliability, Verification, and Design. -

Describing Media Content of Binary Data in XML W3C Working Group Note 4 May 2005
Table of Contents Describing Media Content of Binary Data in XML W3C Working Group Note 4 May 2005 This version: http://www.w3.org/TR/2005/NOTE-xml-media-types-20050504 Latest version: http://www.w3.org/TR/xml-media-types Previous version: http://www.w3.org/TR/2005/NOTE-xml-media-types-20050502 Editors: Anish Karmarkar, Oracle Ümit Yalçınalp, SAP Copyright © 2005 W3C ® (MIT, ERCIM, Keio), All Rights Reserved. W3C liability, trademark and document use rules apply. > >Abstract This document addresses the need to indicate the content-type associated with binary element content in an XML document and the need to specify, in XML Schema, the expected content-type(s) associated with binary element content. It is expected that the additional information about the content-type will be used for optimizing the handling of binary data that is part of a Web services message. Status of this Document This section describes the status of this document at the time of its publication. Other documents may supersede this document. A list of current W3C publications and the latest revision of this technical report can be found in the W3C technical reports index at http://www.w3.org/TR/. This document is a W3C Working Group Note. This document includes the resolution of the comments received on the Last Call Working Draft previously published. The comments on this document and their resolution can be found in the Web Services Description Working Group’s issues list. There is no technical difference between this document and the 2 May 2005 version; the acknowledgement section has been updated to thank external contributors. -

XML Prague 2020
XML Prague 2020 Conference Proceedings University of Economics, Prague Prague, Czech Republic February 13–15, 2020 XML Prague 2020 – Conference Proceedings Copyright © 2020 Jiří Kosek ISBN 978-80-906259-8-3 (pdf) ISBN 978-80-906259-9-0 (ePub) Table of Contents General Information ..................................................................................................... vii Sponsors .......................................................................................................................... ix Preface .............................................................................................................................. xi A note on Editor performance – Stef Busking and Martin Middel .............................. 1 XSLWeb: XSLT- and XQuery-only pipelines for the web – Maarten Kroon and Pieter Masereeuw ............................................................................ 19 Things We Lost in the Fire – Geert Bormans and Ari Nordström .............................. 31 Sequence alignment in XSLT 3.0 – David J. Birnbaum .............................................. 45 Powerful patterns with XSLT 3.0 hidden improvements – Abel Braaksma ............ 67 A Proposal for XSLT 4.0 – Michael Kay ..................................................................... 109 (Re)presentation in XForms – Steven Pemberton and Alain Couthures ................... 139 Greenfox – a schema language for validating file systems – Hans-Juergen Rennau .................................................................................................. -

XML Information Set
XML Information Set XML Information Set W3C Recommendation 24 October 2001 This version: http://www.w3.org/TR/2001/REC-xml-infoset-20011024 Latest version: http://www.w3.org/TR/xml-infoset Previous version: http://www.w3.org/TR/2001/PR-xml-infoset-20010810 Editors: John Cowan, [email protected] Richard Tobin, [email protected] Copyright ©1999, 2000, 2001 W3C® (MIT, INRIA, Keio), All Rights Reserved. W3C liability, trademark, document use and software licensing rules apply. Abstract This specification provides a set of definitions for use in other specifications that need to refer to the information in an XML document. Status of this Document This section describes the status of this document at the time of its publication. Other documents may supersede this document. The latest status of this document series is maintained at the W3C. This is the W3C Recommendation of the XML Information Set. This document has been reviewed by W3C Members and other interested parties and has been endorsed by the Director as a W3C Recommendation. It is a stable document and may be used as reference material or cited as a normative reference from another document. W3C's role in making the Recommendation is to draw attention to the specification and to promote its widespread deployment. This enhances the functionality and interoperability of the file:///C|/Documents%20and%20Settings/immdca01/Desktop/xml-infoset.html (1 of 16) [8/12/2002 10:38:58 AM] XML Information Set Web. This document has been produced by the W3C XML Core Working Group as part of the XML Activity in the W3C Architecture Domain. -

A Practical Ontology for the Large-Scale Modeling of Scholarly Artifacts and Their Usage
A Practical Ontology for the Large-Scale Modeling of Scholarly Artifacts and their Usage Marko A. Rodriguez Johan Bollen Herbert Van de Sompel Digital Library Research & Digital Library Research & Digital Library Research & Prototyping Team Prototyping Team Prototyping Team Los Alamos National Los Alamos National Los Alamos National Laboratory Laboratory Laboratory Los Alamos, NM 87545 Los Alamos, NM 87545 Los Alamos, NM 87545 [email protected] [email protected] [email protected] ABSTRACT evolution of the amount of publications indexed in Thom- The large-scale analysis of scholarly artifact usage is con- son Scientific’s citation database over the last fifteen years: strained primarily by current practices in usage data archiv- 875,310 in 1990; 1,067,292 in 1995; 1,164,015 in 2000, and ing, privacy issues concerned with the dissemination of usage 1,511,067 in 2005. However, the extent of the scholarly data, and the lack of a practical ontology for modeling the record reaches far beyond what is indexed by Thompson usage domain. As a remedy to the third constraint, this Scientific. While Thompson Scientific focuses primarily on article presents a scholarly ontology that was engineered to quality-driven journals (roughly 8,700 in 2005), they do not represent those classes for which large-scale bibliographic index more novel scholarly artifacts such as preprints de- and usage data exists, supports usage research, and whose posited in institutional or discipline-oriented repositories, instantiation is scalable to the order of 50 million articles datasets, software, and simulations that are increasingly be- along with their associated artifacts (e.g. -
5241 Index 0939-0964.Qxd 29/08/02 5.30 Pm Page 941
5241_index_0939-0964.qxd 29/08/02 5.30 pm Page 941 INDEX 941 5241_index_0939-0964.qxd 29/08/02 5.30 pm Page 942 Index 942 Regular A Alternatives, 362 Analysis Patterns: Reusable Expression ABSENT value, 67 Object Models, 521 Symbols abstract attribute, 62, 64–66 ancestor (XPath axis), 54 of complexType element, ancestor-or-self (XPath axis), . escape character, 368, 369 247–248, 512, 719 54 . metacharacter, 361 of element element, 148–149 Annotation, 82 ? metacharacter, 361, 375 mapping to object-oriented defined, 390 ( metacharacter, 361 language, 513–514 mapping to object-oriented ) metacharacter, 361 Abstract language, 521 { metacharacter, 361 attribute type, 934 Microsoft use of term, } metacharacter, 361 defined, 58 821–822 + metacharacter, 361, 375 element type, 16, 17, 18, 934 properties of, 411 * metacharacter, 361, 375 object, corresponding to docu- annotation content option ^ metacharacter, 379 ment, 14 for schema element, 115 \ metacharacter, 361 uses of term, 238, 931–932 annotation element, 82, 83, | metacharacter, 361 Abstract character, 67 254, 260, 722, 859 \. escape character, 366 Abstract document attributes of, 118 \? escape character, 366 document information item content options for, 118–119 \( escape character, 367 view of, 62 example of use of, 117 \) escape character, 367 infoset view of, 62 function of, 116, 124, 128 \{ escape character, 367 makeup of, 59 nested, 83–84 \} escape character, 367 properties of, 66 Anonymous component, 82 \+ escape character, 367 Abstract element, 14–15 any element, 859 \- escape character, -

Hermes Documentation Release 2.2
Hermes Documentation Release 2.2 CECID Nov 21, 2017 Contents 1 Proven Solution to Automate B2B Transactions1 2 EDI over the Internet 3 3 Unified and Extensible B2B Messaging Framework5 i ii CHAPTER 1 Proven Solution to Automate B2B Transactions Hermes Business Messaging Gateway is a proven open-source solution for enterprises to automate business trans- actions with business partners through secure and reliable exchange of electronic documents (e.g., purchase orders). Hermes is secure; it allows you to encrypt and digitally sign the documents for transmission. Hermes is reliable; the sender can automatically retransmit a message when it is dropped in the network while the receiver can guarantee every message is delivered once and only once, and in the right order. 1 Hermes Documentation, Release 2.2 2 Chapter 1. Proven Solution to Automate B2B Transactions CHAPTER 2 EDI over the Internet Electronic Data Interchange (EDI) was developed as the de facto standard for organizations to exchange business data. EDI is running on private networks and based on a cryptic protocol, which makes implementation complicated, expensive, and flexible. These disadvantages have limited the EDI usage to very large organizations only. Hermes is designed to use the Internet, Public Key Infrastructure (PKI), and XML technologies to replace the EDI as a more affordable and extensible solution. Hermes supports mainstream business-to-business (B2B) transport protocols, such as ebXML Message Service 2.0 (ebMS 2.0) and Applicability Statement 2 (AS2). (The ebMS 3.0 / AS4 support is currently under development.). 3 Hermes Documentation, Release 2.2 4 Chapter 2. EDI over the Internet CHAPTER 3 Unified and Extensible B2B Messaging Framework Hermes unifies different transport protocols into a single B2B messaging framework. -

SWAD-Europe Deliverable 5.1: Schema Technology Survey
Sat Jun 05 2004 23:47:40 Europe/London SWAD-Europe Deliverable 5.1: Schema Technology Survey Project name: Semantic Web Advanced Development for Europe (SWAD-Europe) Project Number: IST-2001-34732 Workpackage name: 5. Integration with XML Technology Workpackage description: ☞http://www.w3.org/2001/sw/Europe/plan/workpackages/live/esw-wp-5.html Deliverable title: SWAD-Europe: Schema Technology Survey URI: ☞http://www.w3.org/2001/sw/Europe/reports/xml_schema_tools_techniques_report Authors: Stephen Buswell, Dan Brickley, Brian Matthews Abstract: This report surveys the state of schema annotation and mapping technology. It takes a practical approach by targeting the work to the needs of developers, providing background to support our attempts to answer frequently asked questions on this subject. The report first reviews previous work on 'bridging languages', giving an overview of the major approaches and uses that to motivate further technical work to progress the state of the art in this area. Status: Snapshot release for discussion and editorial work. Further revisions are planned during WP4. Comments on this document are welcome and should be sent to the ☞[email protected] list. An archive of this list is available at ☞http://lists.w3.org/Archives/Public/public-esw/ This report is part of ☞SWAD-Europe ☞Work package 5: Integration with XML Technology and addresses the topic of Schema annotation, and the relationship(s) between RDF and XML technologies. The variety of so-called 'schema languages' for the Web has caused some confusion. This document attempts to place them in context, and explore the state of the art in tools for mapping data between the different approaches.