Introduction to E-Commerce Combining Business and Information Technology
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Describing Media Content of Binary Data in XML W3C Working Group Note 2 May 2005
Table of Contents Describing Media Content of Binary Data in XML W3C Working Group Note 2 May 2005 This version: http://www.w3.org/TR/2005/NOTE-xml-media-types-20050502 Latest version: http://www.w3.org/TR/xml-media-types Previous version: http://www.w3.org/TR/2004/WD-xml-media-types-20041102 Editors: Anish Karmarkar, Oracle Ümit Yalçınalp, SAP (formerly of Oracle) Copyright © 2005 W3C ® (MIT, ERCIM, Keio), All Rights Reserved. W3C liability, trademark and document use rules apply. > >Abstract This document addresses the need to indicate the content-type associated with binary element content in an XML document and the need to specify, in XML Schema, the expected content-type(s) associated with binary element content. It is expected that the additional information about the content-type will be used for optimizing the handling of binary data that is part of a Web services message. Status of this Document This section describes the status of this document at the time of its publication. Other documents may supersede this document. A list of current W3C publications and the latest revision of this technical report can be found in the W3C technical reports index at http://www.w3.org/TR/. This document is a W3C Working Group Note. This document includes the resolution of the comments received on the Last Call Working Draft previously published. The comments on this document and their resolution can be found in the Web Services Description Working Group’s issues list and in the section C Change Log [p.11] . A diff-marked version against the previous version of this document is available. -
XML Specifications Growth of the Web
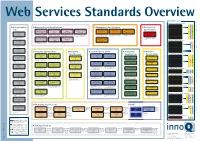
Web Services Standards Overview Dependencies Messaging Specifications SOAP 1.1 SOAP 1.2 Interoperability Business Process Specifications Management Specifications Presentation SOAP Message Transmission Optimization Mechanism WS-Notification the trademarks of their respective owners. of their respective the trademarks Management Using Web Management Of WS-BaseNotification Issues Business Process Execution WS-Choreography Model Web Service Choreography Web Service Choreography WS-Management Specifications Services (WSDM-MUWS) Web Services (WSDM-MOWS) Language for Web Services 1.1 Overview Interface Description Language AMD, Dell, Intel, Microsoft and Sun WS-Topics (BPEL4WS) · 1.1 · BEA Systems, IBM, (WSCI) · 1.0 · W3C 1.0 1.0 1.0 · W3C (CDL4WS) · 1.0 · W3C Microsystems Microsoft, SAP, Sun Microsystems, SAP, BEA Systems WS-BrokeredNotification Working Draft Candidate Recommendation OASIS OASIS Published Specification Web Services for Remote Security Resource Basic Profile Siebel Systems · OASIS-Standard and Intalio · Note OASIS-Standard OASIS-Standard Metadata Portlets (WSRP) WS-Addressing – Core 1.1 ̆ ̆ ̆ ̆ ̆ ̆ ̆ 2.0 WS-I Business Process Execution Language for Web Services WS-Choreography Model Overview defines the format Web Service Choreography Interface (WSCI) describes Web Service Choreography Description Language Web Service Distributed Management: Management Using Web Service Distributed Management: Management Of WS-Management describes a general SOAP-based WS-Addressing – WSDL Binding 1.1(BPEL4WS) provides a language for the formal -

Curious About Cryptocurrencies? Investors Need to Make Sure They Separate “Investing” from “Speculation” by Don Mcarthur, CFA®
Curious About Cryptocurrencies? Investors Need to Make Sure They Separate “Investing” from “Speculation” By Don McArthur, CFA® Bitcoin and other cryptocurrencies have received plenty of media coverage lately, and it is natural for investors to wonder about them. Even celebrities have become associated with Bitcoin publicity through social media. Interest has piqued to a point where there are even Exchange Traded Funds (ETFs) that invest in Bitcoin, giving investors the means to invest in the Futures market. After having performed in-depth research on Bitcoin and other cryptocurrencies, our position at Commerce Trust Company is that they should not currently play a role in client portfolios. As part of that research, Commerce Senior Vice President and Investment Analyst Don McArthur, CFA, put together a primer on the topic of cryptocurrencies in general. In the following commentary, he explains why Bitcoin at this stage is more about speculating than investing in something with intrinsic value. He also touches on how Blockchain networking technology not only supports cryptocurrencies, but many other industrial applications as well. We thought you would enjoy this commentary as McArthur shares his thoughts in a mind-opening Q&A. Q . What is Bitcoin and how did it start? A. Bitcoin is one of hundreds of digital currencies, or cryptocurrency, based on Blockchain technology. As an early mover, Bitcoin is by far the largest digital currency. Bitcoin was launched in 2009 by a mysterious person (or persons) known only by the pseudonym Satoshi Nakamoto. Unlike traditional currencies, which are issued by central banks, Bitcoin has no central monetary authority. -

Price Comparison, Price Competition, and the Effects of Shopbots Kirsten A
Journal of Business & Economics Research – September 2013 Volume 11, Number 9 Price Comparison, Price Competition, And The Effects Of ShopBots Kirsten A. Passyn, Salisbury University, USA Memo Diriker, Salisbury University, USA Robert B. Settle, Salisbury University, USA ABSTRACT Two ShopBots were used to determine high-to-low price dispersion for identical models of 25 consumer durables, in 2007 and again in 2011, revealing substantial but declining price dispersion ratios. A survey of 1,135 American online shoppers revealed their dependence on ShopBots and frequency of other online shopping actions. Typical respondent reported they "very often" used search sites to locate what they wanted. Nearly 30 percent used the most often named price comparison site, Yahoo! Shopping, in the past year, suggesting substantial potential for future price rationalization. Several customer relationship management tools online merchants might use to avoid the resulting direct price competition are discussed. Finally, the impact of m- commerce, tablets, and apps on online price comparison behavior is explored. Keywords: Consumer Behavior; Database Marketing; Direct Marketing; Electronic Commerce; Online Shopping; Price Dispersion INTRODUCTION s annual online shopping in North America reaches the $200 Billion mark (Lumry, 2011), the emergence of ShopBots such as Yahoo! Shopping and Google Product Search has facilitated consumers’ ability to gather price and product information, virtually mitigating search costs. It was Atherefore initially assumed that as ShopBots became increasingly prevalent on-line merchants would come under increased price competition, eventually leading to price convergence. With ShopBots now the third most popular online shopping option after eBay and Amazon, we reassess the impact of ShopBots on price as they reach their tipping point. -

Technical Report
Cost-Effective Cloud Edge Traffic Engineering with CASCARA Rachee Singh Sharad Agarwal Matt Calder Victor Bahl Microsoft Abstract Inter-domain bandwidth costs comprise a significant amount of the operating expenditure of cloud providers. Traffic engi- neering systems at the cloud edge must strike a fine balance between minimizing costs and maintaining the latency ex- pected by clients. The nature of this tradeoff is complex due to non-linear pricing schemes prevalent in the market for inter-domain bandwidth. We quantify this tradeoff and un- cover several key insights from the link-utilization between a large cloud provider and Internet service providers. Based Figure 1: Present-day and CASCARA-optimized bandwidth allo- on these insights, we propose CASCARA, a cloud edge traffic cation distributions for one week, across a pair of links between a engineering framework to optimize inter-domain bandwidth large cloud provider and tier-1 North American ISPs. Costs depend allocations with non-linear pricing schemes. CASCARA lever- on the 95th-percentile of the allocation distributions (vertical lines). ages the abundance of latency-equivalent peer links on the CASCARA-optimized allocations reduce total costs by 35% over the cloud edge to minimize costs without impacting latency sig- present-day allocations while satisfying the same demand. nificantly. Extensive evaluation on production traffic demands of a commercial cloud provider shows that CASCARA saves In this work, we show that recent increases in interconnec- 11–50% in bandwidth costs per cloud PoP, while bounding tion and infrastructure scale enable significant potential to re- the increase in client latency by 3 milliseconds1. duce the costs of inter-domain traffic. -

New Insights on Retail E-Commerce (July 26, 2017)
U.S. Department of Commerce Economics Newand Insights Statistics on Retail Administration E-Commerce Office of the Chief Economist New Insights on Retail E-Commerce Executive Summary The U.S. Census Bureau has been collecting data on retail sales since the 1950s and data on e-commerce retail sales since 1998. As the Internet has become ubiquitous, many retailers have created websites and even entire divisions devoted to fulfilling online orders. Many consumers have By turned to e-commerce as a matter of convenience or to increase the Jessica R. Nicholson variety of goods available to them. Whatever the reason, retail e- commerce sales have skyrocketed and the Internet will undoubtedly continue to influence how consumers shop, underscoring the need for good data to track this increasingly important economic activity. In June 2017, the Census Bureau released a new supplemental data table on retail e-commerce by type of retailer. The Census Bureau developed these estimates by re-categorizing e-commerce sales data from its ESA Issue Brief existing “electronic shopping” sales data according to the primary #04-17 business type of the retailer, such as clothing stores, food stores, or electronics stores. This report examines how the new estimates enhance our understanding of where consumers are shopping online and also provides an overview of trends in retail and e-commerce sales. Findings from this report include: E-commerce sales accounted for 7.2 percent of all retail sales in 2015, up dramatically from 0.2 percent in 1998. July 26, 2017 E-commerce sales have been growing nine times faster than traditional in-store sales since 1998. -

Rootkit- Rootkits.For.Dummies 2007.Pdf
01_917106 ffirs.qxp 12/21/06 12:04 AM Page i Rootkits FOR DUMmIES‰ 01_917106 ffirs.qxp 12/21/06 12:04 AM Page ii 01_917106 ffirs.qxp 12/21/06 12:04 AM Page iii Rootkits FOR DUMmIES‰ by Larry Stevenson and Nancy Altholz 01_917106 ffirs.qxp 12/21/06 12:04 AM Page iv Rootkits For Dummies® Published by Wiley Publishing, Inc. 111 River Street Hoboken, NJ 07030-5774 www.wiley.com Copyright © 2007 by Wiley Publishing, Inc., Indianapolis, Indiana Published by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permit- ted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions. Trademarks: Wiley, the Wiley Publishing logo, For Dummies, the Dummies Man logo, A Reference for the Rest of Us!, The Dummies Way, Dummies Daily, The Fun and Easy Way, Dummies.com, and related trade dress are trademarks or registered trademarks of John Wiley & Sons, Inc. and/or its affiliates in the United States and other countries, and may not be used without written permission. -

Ioc Containers in Spring
301AA - Advanced Programming Lecturer: Andrea Corradini [email protected] http://pages.di.unipi.it/corradini/ AP-2018-11: Frameworks and Inversion of Control Frameworks and Inversion of Control • Recap: JavaBeans as Components • Frameworks, Component Frameworks and their features • Frameworks vs IDEs • Inversion of Control and Containers • Frameworks vs Libraries • Decoupling Components • Dependency Injection • IoC Containers in Spring 2 Components: a recap A software component is a unit of composition with contractually specified interfaces and explicit context dependencies only. A software component can be deployed independently and is subject to composition by third party. Clemens Szyperski, ECOOP 1996 • Examples: Java Beans, CLR Assemblies • Contractually specified interfaces: events, methods and properties • Explicit context dependencies: serializable, constructor with no argument • Subject to composition: connection to other beans – Using connection oriented programming (event source and listeners/delegates) 3 Towards Component Frameworks • Software Framework: A collection of common code providing generic functionality that can be selectively overridden or specialized by user code providing specific functionality • Application Framework: A software framework used to implement the standard structure of an application for a specific development environment. • Examples: – GUI Frameworks – Web Frameworks – Concurrency Frameworks 4 Examples of Frameworks Web Application Frameworks GUI Toolkits 5 Examples: General Software Frameworks – .NET – Windows platform. Provides language interoperability – Android SDK – Supports development of apps in Java (but does not use a JVM!) – Cocoa – Apple’s native OO API for macOS. Includes C standard library and the Objective-C runtime. – Eclipse – Cross-platform, easily extensible IDE with plugins 6 Examples: GUI Frameworks • Frameworks for Application with GUI – MFC - Microsoft Foundation Class Library. -

Use of Bioinformatics Resources and Tools by Users of Bioinformatics Centers in India Meera Yadav University of Delhi, [email protected]
University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln Library Philosophy and Practice (e-journal) Libraries at University of Nebraska-Lincoln 2015 Use of Bioinformatics Resources and Tools by Users of Bioinformatics Centers in India meera yadav University of Delhi, [email protected] Manlunching Tawmbing Saha Institute of Nuclear Physisc, [email protected] Follow this and additional works at: http://digitalcommons.unl.edu/libphilprac Part of the Library and Information Science Commons yadav, meera and Tawmbing, Manlunching, "Use of Bioinformatics Resources and Tools by Users of Bioinformatics Centers in India" (2015). Library Philosophy and Practice (e-journal). 1254. http://digitalcommons.unl.edu/libphilprac/1254 Use of Bioinformatics Resources and Tools by Users of Bioinformatics Centers in India Dr Meera, Manlunching Department of Library and Information Science, University of Delhi, India [email protected], [email protected] Abstract Information plays a vital role in Bioinformatics to achieve the existing Bioinformatics information technologies. Librarians have to identify the information needs, uses and problems faced to meet the needs and requirements of the Bioinformatics users. The paper analyses the response of 315 Bioinformatics users of 15 Bioinformatics centers in India. The papers analyze the data with respect to use of different Bioinformatics databases and tools used by scholars and scientists, areas of major research in Bioinformatics, Major research project, thrust areas of research and use of different resources by the user. The study identifies the various Bioinformatics services and resources used by the Bioinformatics researchers. Keywords: Informaion services, Users, Inforamtion needs, Bioinformatics resources 1. Introduction ‘Needs’ refer to lack of self-sufficiency and also represent gaps in the present knowledge of the users. -

Establishing the Basis for a CIS (Computer Information Systems) Undergraduate Program: on Seeking the Body of Knowledge
Information Systems Education Journal (ISEDJ) 13 (5) ISSN: 1545-679X September 2015 Establishing the Basis for a CIS (Computer Information Systems) Undergraduate Program: On Seeking the Body of Knowledge Herbert E. Longenecker, Jr. [email protected] University of South Alabama Mobile, AL 36688, USA Jeffry Babb [email protected] West Texas A&M University Canyon, TX 79016, USA Leslie J. Waguespack [email protected] Bentley University Waltham, Massachusetts 02452, USA Thomas N. Janicki [email protected] University of North Carolina Wilmington Wilmington, NC 28403, USA David Feinstein [email protected] University of South Alabama Mobile, AL 36688, USA Abstract The evolution of computing education spans a spectrum from computer science (CS) grounded in the theory of computing, to information systems (IS), grounded in the organizational application of data processing. This paper reports on a project focusing on a particular slice of that spectrum commonly labeled as computer information systems (CIS) and reflected in undergraduate academic programs designed to prepare graduates for professions as software developers building systems in government, commercial and not-for-profit enterprises. These programs with varying titles number in the hundreds. This project is an effort to determine if a common knowledge footprint characterizes CIS. If so, an eventual goal would be to describe the proportions of those essential knowledge components and propose guidelines specifically for effective undergraduate CIS curricula. Professional computing societies (ACM, IEEE, AITP (formerly DPMA), etc.) over the past fifty years have sponsored curriculum guidelines for various slices of education that in aggregate offer a compendium of knowledge areas in ©2015 EDSIG (Education Special Interest Group of the AITP) Page 37 www.aitp-edsig.org /www.isedj.org Information Systems Education Journal (ISEDJ) 13 (5) ISSN: 1545-679X September 2015 computing. -

Service Power Warranty Claims Management
A Special SFGSM Analyst’s Take Ensuring Quality Customer Service Performance in the Global Insurance Segment Written by Bill Pollock ServicePower.com Enabling InsurTech Organizations to Enhance your Customer’s Experience and Boost their Bottom Line August 2018 Bill Pollock Putting Things Forward from the Perspective President & Principal of the Global Insurance Industry Consulting Analyst Strategies For GrowthSM / The results from research analyst firm, Strategies for PollockOnService Growth’s 2018 Warranty Chain Management Benchmark Survey clearly reveal that insurance organizations that have either implemented a new warranty management solution or, at the very least, upgraded their existing solution, are now experiencing an average of up to 10% improvement in warranty claims processing times, as well as commensurate upticks in customer satisfaction and the overall customer Westtown, Pennsylvania USA experience. +1 610-399-9717 As many of these implementations are now supported by [email protected] state-of-the-art Artificial Intelligence (AI) technology, those www.PollockOnService.com organizations that have taken this path benefit twice – from both the improved functionality of their “new” warranty management systems, as well as the introduction of AI technology into their business operations. A SPECIAL SFGSM ANALYST’S TAKE 1 “The insurance segment will continue to be highly dependent on the introduction of new technology into their business operations and, as a result, will be searching for vendors and solutions that will ease their -

Business Model Development for E-Commerce Initiative
Ilkka Heikinniemi Business Model Development for E-commerce Initiative Metropolia University of Applied Sciences Bachelor of Engineering Industrial Management Bachelor’s Thesis 7 May 2019 Abstract Author Ilkka Heikinniemi Title Business Model Development for E-commerce Initiative Number of Pages 51 pages + 4 appendices Date 7 May 2019 Degree Bachelor of Engineering Degree Programme Industrial Management Professional Major Process Management Instructors Antti Matinlauri, Global Business Development Manager Thomas Rohweder, DSc (Econ), Principal Lecturer The objective of this thesis was to develop a preliminary e-commerce business model, which would provide mutual benefit for the case company and its channel partners. The need for e-commerce emerges from increased online buying, and from urgency to better serve digital native customers. However, the existing business model, which relies on distributors and channel partners generating majority of the revenue, is currently a challenge. This work strives to find an e-commerce solution where intermediaries are not disregarded, whereby the channel conflict between traditional and digital channels can be avoided. The thesis was conducted by using the action research method with pragmatic and iterative approach. Firstly, literature best practices regarding e-commerce and channel conflict miti- gation was reviewed. It was followed by a current state analysis, where internal data were utilized, and relevant senior management interviewed. Thirdly, based on the analysis of the previous phases and on the case company’s strategic intents, a development phase was carried out to combine existing and new business elements. An ecosystem-based model was developed to address the business challenge. The model is based on a webshop, which utilizes local channel partners in the end of customer journey.