Navigating Terra Incognita: Why the Digital Millennium Copyright Act Was Needed to Chart the Course of Online Service Provider Liability for Copyright Infringement
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

UC Berkeley Recent Work
UC Berkeley Recent Work Title The Internet and E-commerce Development in Mexico Permalink https://escholarship.org/uc/item/6c17b69n Authors Kenney, Martin Curry, James Contreras, Oscar Publication Date 2001-05-01 eScholarship.org Powered by the California Digital Library University of California The Internet and E-commerce Development in Mexico BRIE Working Paper 144 January 2, 2002 ©Copyright 2001 by the authors By James Curry Profesor-Investigador El Colegio de la Frontera Norte Tijuana, Baja California, México U.S. Mail: P.O. Box L Chula Vista, CA 91912 [email protected] and Oscar Contreras Profesor-Investigador El Colegio de Sonora Hermosillo, Sonora, Mexico and Martin Kenney Professor Department of Human and Community Development University of California, Davis Davis, California 95616 [email protected] & Senior Research Associate Berkeley Roundtable on the International Economy University of California, Berkeley Berkeley, CA 94720-2322 The authors thank the UC MEXUS-CONACYT program for the funding that is reported in this research. Generous support for production of the BRIE Working Papers Series was provided by the Alfred P. Sloan Foundation. Table of Contents · Summary and Findings · Introduction · Methodology · The Internet in Mexico The Early History of the Internet in Mexico Growth in Internet Usage Internet Access and Service Providers · E-Commerce in Mexico Barriers to the Growth of E-Commerce · Business-to-Consumer E-Commerce Mexico and the U.S. Hispanic and Pan-Latin American/Hispanic Markets Customization Brief Descriptions -

Blue Coat Proxysg Configuration and Management Guide, Version 4.1.4
Blue Coat® Systems ProxySG™ Configuration and Management Guide Version SGOS 4.1.4 Blue Coat ProxySG Configuration and Management Guide Contact Information Blue Coat Systems Inc. 420 North Mary Ave Sunnyvale, CA 94085-4121 http://www.bluecoat.com/support/index.html [email protected] [email protected] http://www.bluecoat.com For concerns or feedback about the documentation: [email protected] Copyright© 1999-2006 Blue Coat Systems, Inc. All rights reserved worldwide. No part of this document may be reproduced by any means nor modified, decompiled, disassembled, published or distributed, in whole or in part, or translated to any electronic medium or other means without the written consent of Blue Coat Systems, Inc. All right, title and interest in and to the Software and documentation are and shall remain the exclusive property of Blue Coat Systems, Inc. and its licensors. ProxySG™, ProxyAV™, CacheOS™, SGOS™, Spyware Interceptor™, Scope™ are trademarks of Blue Coat Systems, Inc. and CacheFlow®, Blue Coat®, Accelerating The Internet®, WinProxy®, AccessNow®, Ositis®, Powering Internet Management®, and The Ultimate Internet Sharing Solution® are registered trademarks of Blue Coat Systems, Inc. All other trademarks contained in this document and in the Software are the property of their respective owners. BLUE COAT SYSTEMS, INC. DISCLAIMS ALL WARRANTIES, CONDITIONS OR OTHER TERMS, EXPRESS OR IMPLIED, STATUTORY OR OTHERWISE, ON SOFTWARE AND DOCUMENTATION FURNISHED HEREUNDER INCLUDING WITHOUT LIMITATION THE WARRANTIES OF DESIGN, MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL BLUE COAT SYSTEMS, INC., ITS SUPPLIERS OR ITS LICENSORS BE LIABLE FOR ANY DAMAGES, WHETHER ARISING IN TORT, CONTRACT OR ANY OTHER LEGAL THEORY EVEN IF BLUE COAT SYSTEMS, INC. -

Neural Network FAQ, Part 1 of 7
Neural Network FAQ, part 1 of 7: Introduction Archive-name: ai-faq/neural-nets/part1 Last-modified: 2002-05-17 URL: ftp://ftp.sas.com/pub/neural/FAQ.html Maintainer: [email protected] (Warren S. Sarle) Copyright 1997, 1998, 1999, 2000, 2001, 2002 by Warren S. Sarle, Cary, NC, USA. --------------------------------------------------------------- Additions, corrections, or improvements are always welcome. Anybody who is willing to contribute any information, please email me; if it is relevant, I will incorporate it. The monthly posting departs around the 28th of every month. --------------------------------------------------------------- This is the first of seven parts of a monthly posting to the Usenet newsgroup comp.ai.neural-nets (as well as comp.answers and news.answers, where it should be findable at any time). Its purpose is to provide basic information for individuals who are new to the field of neural networks or who are just beginning to read this group. It will help to avoid lengthy discussion of questions that often arise for beginners. SO, PLEASE, SEARCH THIS POSTING FIRST IF YOU HAVE A QUESTION and DON'T POST ANSWERS TO FAQs: POINT THE ASKER TO THIS POSTING The latest version of the FAQ is available as a hypertext document, readable by any WWW (World Wide Web) browser such as Netscape, under the URL: ftp://ftp.sas.com/pub/neural/FAQ.html. If you are reading the version of the FAQ posted in comp.ai.neural-nets, be sure to view it with a monospace font such as Courier. If you view it with a proportional font, tables and formulas will be mangled. -

Case 15-10104-LSS Doc 309 Filed 04/08/15 Page 1 of 98
Case 15-10104-LSS Doc 309 Filed 04/08/15 Page 1 of 98 UNITED STATES BANKRUPTCY COURT FOR THE DISTRICT OF DELAWARE In re: Chapter 11 HIPCRICKET, INC.,1 Case No. 15-10104 (LSS) Debtor. AFFIDAVIT OF SERVICE STATE OF CALIFORNIA } } ss.: COUNTY OF LOS ANGELES } DARLEEN SAHAGUN, being duly sworn, deposes and says: 1. I am employed by Rust Consulting/Omni Bankruptcy, located at 5955 DeSoto Avenue, Suite 100, Woodland Hills, CA 91367. I am over the age of eighteen years and am not a party to the above-captioned action. 2. On April 3, 2015, I caused to be served the: a) Notice of (I) Conditional Approval of the Amended Disclosure Statement; (II) Hearing to Consider Confirmation of the Plan; (III) Deadline for Filing Objections to Confirmation of the Plan; (IV) Deadline for Voting on the Plan; and (V) Bar Date for Filing Administrative Claims Established by the Plan, (the “Notice”), b) Amended Plan of Reorganization of the Debtor Dated March 31, 2015 [Docket No. 293], c) Amended Disclosure Statement for the Plan of Reorganization of Hipcricket, Inc. [Docket No. 294], d) Committee Plan Support Letter (re: Recommendation of Creditors’ Committee in Favor of Chapter 11 Plan of Reorganization), (2a through 2d collectively referred to as the “Solicitation Package”) e) Class 3 General Unsecured Claims Ballot to Accept or Reject Chapter 11 Plan of Reorganization (the “Class 3 Ballot”), 1 The last four digits of the Debtor’s tax identification number are 2076. The location of the Debtor’s headquarters and the service address for the Debtor is 110 110th Avenue NE. -
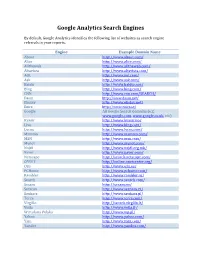
Google Analytics Search Engines
Google Analytics Search Engines By default, Google Analytics identifies the following list of websites as search engine referrals in your reports. Engine Example Domain Name About http://www.about.com/ Alice http://www.alice.com/ Alltheweb http://www.alltheweb.com/ Altavista http://www.altavista.com/ AOL http://www.aol.com/ Ask http://www.ask.com/ Baidu http://www.baidu.com/ Bing http://www.bing.com/ CNN http://www.cnn.com/SEARCH/ Daum http://www.daum.net/ Ekolay http://www.ekolay.net/ Eniro http://www.eniro.se/ Google All Google Search domains (e.g. www.google.com, www.google.co.uk, etc) Kvasir http://www.kvasir.no/ Live http://www.bing.com/ Lycos http://www.lycos.com/ Mamma http://www.mamma.com/ MSN http://www.msn.com/ Mynet http://www.mynet.com/ Najdi http://www.najdi.org.mk/ Naver http://www.naver.com/ Netscape http://search.netscape.com/ O*NET http://online.onetcenter.org/ Ozu http://www.ozu.es/ PCHome http://www.pchome.com/ Rambler http://www.rambler.ru/ Search http://www.search.com/ Sesam http://sesam.no/ Seznam http://www.seznam.cz/ Szukacz http://www.szukacz.pl/ Terra http://www.terra.com/ Virgilio http://search.virgilio.it/ Voila http://www.voila.fr/ Wirtulana Polska http://www.wp.pl/ Yahoo http://www.yahoo.com/ Yam http://www.yam.com/ Yandex http://www.yandex.com/ . -

Hoodwinked: Watching Movies with Eyes Wide Open Refers to an Ancient Term Used in Secret Societies
Contents Introduction..............................................................................................ix I. Poli-Sci-Fi (Political Science Fiction) 1. The Matrix': Sci-Fi, Metaphysics, and Soul Liberation ..................3 2. 'Minority Report': Spielberg's Psychic Dictatorship ......................11 3. 'The Postman': Reluctant Hero Delivers Hope .............................15 4. 'Solaris': Life Is A Trance................................................................19 5. 'Soldier': Future Cannon Fodder Goes High-Tech ..........................24 6. 'Sixth Day': Downtown Atlantis Revisited......................................26 7. 'Signs': Mel Gibson Loses His BS (Belief System) .......................30 8. 'Starship Troopers': Teenage Fascists Battle Giant Bugs ................36 9. 'The Truman Show': Storming the Reality Studio...........................40 10. 'The X-Files': When Conspiracies Collide ...................................43 II. Illuminati, Mind Control and Other PsyOps 11. 'Arlington Road': The Terrorist Next Door .....................................51 12. 'Avengers': Weather Control for Fun and Profit..............................55 13. 'Blade': Secrets of the Illuminati ...................................................59 14. 'Conspiracy Theory': Deconstructing Hidden History......................64 15. 'Dark Angel': The Threat of Digital Slavery ...................................70 16. 'Disturbing Behavior': Mind Control High School..........................78 17. 'Eyes Wide Shut': Occult Entertainment -

Start-Up Space Report 2020
Start-Up Space Update on Investment in Commercial Space Ventures 2020 i Bryce Space and Technology brycetech.com CONTENTS EXECUTIVE SUMMARY ........................................... III INTRODUCTION. 1 Purpose and Background . 1 Methodology ...................................................1 OVERVIEW OF START-UP SPACE VENTURES. 3 TYPES OF SPACE INVESTOR ......................................4 SPACE INVESTMENT BY THE NUMBERS ...........................11 Seed Funding . 15 Venture Capital . 16 Private Equity . 17 Acquisition ...................................................18 Public Offering ................................................19 Debt Financing . 19 Investment Across All Types .....................................19 Valuation ....................................................21 Casualties ...................................................22 SPACE INVESTORS BY THE NUMBERS ............................23 Overall ......................................................23 Angels ......................................................27 Venture Capital Firms . 28 Private Equity Groups ..........................................31 Corporations . 32 Banks and Other Financial Institutions .............................33 SPECIAL TOPIC: CHINESE ACTIVITY IN START-UP SPACE VENTURES. 35 START-UP SPACE: WHAT’S NEXT?. 38 ACKNOWLEDGEMENTS. 41 ii brycetech.com Bryce Space and Technology EXECUTIVE SUMMARY Three significant trends are shaping the start-up space environment as we enter the 2020s. First, investors continue to pour large amounts -

3/1996 Info1mat1on• Technology
OCCASION This publication has been made available to the public on the occasion of the 50th anniversary of the United Nations Industrial Development Organisation. DISCLAIMER This document has been produced without formal United Nations editing. The designations employed and the presentation of the material in this document do not imply the expression of any opinion whatsoever on the part of the Secretariat of the United Nations Industrial Development Organization (UNIDO) concerning the legal status of any country, territory, city or area or of its authorities, or concerning the delimitation of its frontiers or boundaries, or its economic system or degree of development. Designations such as “developed”, “industrialized” and “developing” are intended for statistical convenience and do not necessarily express a judgment about the stage reached by a particular country or area in the development process. Mention of firm names or commercial products does not constitute an endorsement by UNIDO. FAIR USE POLICY Any part of this publication may be quoted and referenced for educational and research purposes without additional permission from UNIDO. However, those who make use of quoting and referencing this publication are requested to follow the Fair Use Policy of giving due credit to UNIDO. CONTACT Please contact [email protected] for further information concerning UNIDO publications. For more information about UNIDO, please visit us at www.unido.org UNITED NATIONS INDUSTRIAL DEVELOPMENT ORGANIZATION Vienna International Centre, P.O. Box 300, 1400 Vienna, Austria Tel: (+43-1) 26026-0 · www.unido.org · [email protected] (v), 6 9 p · 21850 EMERGING TECHNOLOGY SERIES 3/1996 Info1mat1on• Technology UNITED NATIONS INDUSTRIAL DEVEWPMENT ORGANIZATION Vienna, 1997 TO OUR READERS EMERGING TECHNOLOGY This issue of lnfonnation Technology brings a cover paper on intranets. -

Terra Lycos: Creating a Global and Profitable Integrated Media Company
INSEAD Terra Lycos: Creating a Global and Profitable Integrated Media Company INSPECTIONNot For Reproduction COPY 06/2002-5042 This case was written by Patricia Reese, Research Associate, under the supervision of Soumitra Dutta, The Roland Berger Chaired Professor of E-Business and Information Technology, and Theodoros Evgeniou, Assistant Professor of Information Systems, all at INSEAD. It is intended to be used as a basis for class discussion rather than to illustrate either effective or ineffective handling of an administrative situation. Copyright © 2002 INSEAD, Fontainebleau, France. N.B. PLEASE NOTE THAT DETAILS OF ORDERING INSEAD CASES ARE FOUND ON THE BACK COVER. COPIES MAY NOT BE MADE WITHOUT PERMISSION. INSPECTIONNot For Reproduction COPY INSEAD 1 5042 “Market leadership is a challenge within our reach, but requires us to achieve several objectives: consolidating our product offerings to make our portals the most comprehensive and compelling on the World Wide Web, taking advantage of our extraordinary cash position to grow profits and extend our website network, and finally offering small- and medium-sized businesses effective e-commerce solutions. Terra Lycos must make full use of our advantage in the convergence of media, communications and interactive content, thanks to strategic alliances with Telefónica, our majority stockholder, and Bertelsmann.” Joaquim Agut, Executive Chairman, Terra Lycos The bright mid-September morning had not started well for Rafael Bonnelly, Terra Lycos’ vice-presidentNot For of content Reproduction management. He had just found out that FIFA,1 the governing body INSPECTIONof World Cup soccer, had given COPY the nod to Yahoo! to design and manage the official 2002 World Cup website. -

Are Sales of Copyrighted Items Exposing Internet Auction Sites to Liability
Loyola of Los Angeles Entertainment Law Review Volume 21 Number 1 Article 4 9-1-2000 Going Once, Going Twice, Sold - Are Sales of Copyrighted Items Exposing Internet Auction Sites to Liability Kelley E. Moohr Follow this and additional works at: https://digitalcommons.lmu.edu/elr Part of the Law Commons Recommended Citation Kelley E. Moohr, Going Once, Going Twice, Sold - Are Sales of Copyrighted Items Exposing Internet Auction Sites to Liability, 21 Loy. L.A. Ent. L. Rev. 97 (2000). Available at: https://digitalcommons.lmu.edu/elr/vol21/iss1/4 This Notes and Comments is brought to you for free and open access by the Law Reviews at Digital Commons @ Loyola Marymount University and Loyola Law School. It has been accepted for inclusion in Loyola of Los Angeles Entertainment Law Review by an authorized administrator of Digital Commons@Loyola Marymount University and Loyola Law School. For more information, please contact [email protected]. GOING ONCE, GOING TWICE, SOLD! ARE SALES OF COPYRIGHTED ITEMS EXPOSING INTERNET AUCTION SITES TO LIABILITY? I. INTRODUCTION Internet auction sites have become havens for people looking for either a fast dollar or that elusive item they can no longer find in stores. On-line service providers ("OSPs")' such as Yahoo.coM, 2 Amazon.corn, and eBay,4 which provide auction forums, have enjoyed increasing popularity within the last few years.' In fact, eBay, the leading venue, has hosted at least fifty-seven million auctions on its site since 1995.6 EBay users post new auctions on the site at a 7 rate of 340 per minute, which translates to a rate of 500,000 per day. -

Internet Valuations: the Case of Terra-Lycos
European Research Studies, Volume XV, Issue (2), 2012 Internet Valuations: the Case of Terra-Lycos Pablo Fernández1 Abstract: In this paper, we review twelve valuations of Terra performed by Spanish and non- Spanish bank analysts and brokers. Of the twelve valuations, only one used cash flow discounting. Another valuation was based on multiples, but also used cash flow discounting to perform a reverse valuation. All others used several multiples. Only one valuation report recommended to sell. Terra started trading on the stock market in November 1999. The placement price was 13 euros per share (11.81 for retailers). In February 2000, its price stood at 139.75 euros. Between November 1999 and February 2000, Terra provided a return of 975% for its shareholders. However, by December 2000, the share price had plummeted to 11.6 euros, 8.3% of its February high. The average annual volatility of the Terra share was almost 100%. If you can’t find a rational explanation for a share to continue rising, you can be sure that it will fall. To become a millionaire, you must sell your shares at the right time. A website is not necessarily a business. Selling below cost gets you lots of customers, but not much money. Key Words: Internet, Valuation, Internet valuation, Analysts JEL Classification: G12, G31, M21 1 PricewaterhouseCoopers, Professor of Corporate Finance, IESE Business School, Camino del Cerro del Aguila 3, 28023 Madrid, Spain, Telephone 34-91-357 08 09, e-mail: [email protected] 4 European Research Studies, Volume XV, Issue (2), 2012 1. Introduction Terra started trading on the stock market in November 1999. -

Local Damage Mounting in Writers' Strike
20080107p001CN_.qxp 1/4/2008 9:17 PM Page 1 REPORT TOP STORIES ’08 OUTLOOK Traffic caps halt City anxious Virgin America’s as Wall St. JFK expansion plan falters PAGE 2 ® PAGES 13-17 Banks burned by bad loans as problems spread VOL. XXIV, NO. 1 WWW.CRAINSNEWYORK.COM JANUARY 7-13, 2008 PRICE: $3.00 beyond subprime PAGE 2 IOWA CAUCUS FALLOUT Local damage ONE DOWN: Crain’s picks 5 Barack Obama local stocks to ride captured the 38% biggest share of Barack Obama Democratic votes mounting in in tough 2008 in the Iowa INVESTING, PAGES 3-4 caucus. 30% Suzy Welch gets John Edwards writers’ strike $1 million for a new book 29% tailspin,” says John Ford, president Hillary Clinton Thousands jobless, of studio mechanics union Local NEW YORK, NEW YORK, P. 6 bloomberg news suppliers take hits; 52.“Everyone is out of work now.” The writers began their strike The rules Crain’s pilot season could in November. They are seeking lives by, in print Obama’s NY allies residuals from the Alliance of Mo- be jeopardized tion Picture and Television Pro- and online ducers for work that appears on the BY MIRIAM KREININ SOUCCAR GREG DAVID, PAGE 11 move into spotlight Internet and other new media. About a dozen TV series are david letterman and Conan shot in New York, including 30 The New Yorkers who en- O’Brien might be back on the air, Rock and Law and Order; they have BUSINESS LIVES African-American dorsed Mr. Obama exulted in but the Writers Guild of America run out of scripts and stopped film- WINTER BLAHS? pols bucked party; Iowa’s perceived ideals—a more strike that put them in reruns for ing.