3/1996 Info1mat1on• Technology
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

UC Berkeley Recent Work
UC Berkeley Recent Work Title The Internet and E-commerce Development in Mexico Permalink https://escholarship.org/uc/item/6c17b69n Authors Kenney, Martin Curry, James Contreras, Oscar Publication Date 2001-05-01 eScholarship.org Powered by the California Digital Library University of California The Internet and E-commerce Development in Mexico BRIE Working Paper 144 January 2, 2002 ©Copyright 2001 by the authors By James Curry Profesor-Investigador El Colegio de la Frontera Norte Tijuana, Baja California, México U.S. Mail: P.O. Box L Chula Vista, CA 91912 [email protected] and Oscar Contreras Profesor-Investigador El Colegio de Sonora Hermosillo, Sonora, Mexico and Martin Kenney Professor Department of Human and Community Development University of California, Davis Davis, California 95616 [email protected] & Senior Research Associate Berkeley Roundtable on the International Economy University of California, Berkeley Berkeley, CA 94720-2322 The authors thank the UC MEXUS-CONACYT program for the funding that is reported in this research. Generous support for production of the BRIE Working Papers Series was provided by the Alfred P. Sloan Foundation. Table of Contents · Summary and Findings · Introduction · Methodology · The Internet in Mexico The Early History of the Internet in Mexico Growth in Internet Usage Internet Access and Service Providers · E-Commerce in Mexico Barriers to the Growth of E-Commerce · Business-to-Consumer E-Commerce Mexico and the U.S. Hispanic and Pan-Latin American/Hispanic Markets Customization Brief Descriptions -

Blue Coat Proxysg Configuration and Management Guide, Version 4.1.4
Blue Coat® Systems ProxySG™ Configuration and Management Guide Version SGOS 4.1.4 Blue Coat ProxySG Configuration and Management Guide Contact Information Blue Coat Systems Inc. 420 North Mary Ave Sunnyvale, CA 94085-4121 http://www.bluecoat.com/support/index.html [email protected] [email protected] http://www.bluecoat.com For concerns or feedback about the documentation: [email protected] Copyright© 1999-2006 Blue Coat Systems, Inc. All rights reserved worldwide. No part of this document may be reproduced by any means nor modified, decompiled, disassembled, published or distributed, in whole or in part, or translated to any electronic medium or other means without the written consent of Blue Coat Systems, Inc. All right, title and interest in and to the Software and documentation are and shall remain the exclusive property of Blue Coat Systems, Inc. and its licensors. ProxySG™, ProxyAV™, CacheOS™, SGOS™, Spyware Interceptor™, Scope™ are trademarks of Blue Coat Systems, Inc. and CacheFlow®, Blue Coat®, Accelerating The Internet®, WinProxy®, AccessNow®, Ositis®, Powering Internet Management®, and The Ultimate Internet Sharing Solution® are registered trademarks of Blue Coat Systems, Inc. All other trademarks contained in this document and in the Software are the property of their respective owners. BLUE COAT SYSTEMS, INC. DISCLAIMS ALL WARRANTIES, CONDITIONS OR OTHER TERMS, EXPRESS OR IMPLIED, STATUTORY OR OTHERWISE, ON SOFTWARE AND DOCUMENTATION FURNISHED HEREUNDER INCLUDING WITHOUT LIMITATION THE WARRANTIES OF DESIGN, MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL BLUE COAT SYSTEMS, INC., ITS SUPPLIERS OR ITS LICENSORS BE LIABLE FOR ANY DAMAGES, WHETHER ARISING IN TORT, CONTRACT OR ANY OTHER LEGAL THEORY EVEN IF BLUE COAT SYSTEMS, INC. -

Neural Network FAQ, Part 1 of 7
Neural Network FAQ, part 1 of 7: Introduction Archive-name: ai-faq/neural-nets/part1 Last-modified: 2002-05-17 URL: ftp://ftp.sas.com/pub/neural/FAQ.html Maintainer: [email protected] (Warren S. Sarle) Copyright 1997, 1998, 1999, 2000, 2001, 2002 by Warren S. Sarle, Cary, NC, USA. --------------------------------------------------------------- Additions, corrections, or improvements are always welcome. Anybody who is willing to contribute any information, please email me; if it is relevant, I will incorporate it. The monthly posting departs around the 28th of every month. --------------------------------------------------------------- This is the first of seven parts of a monthly posting to the Usenet newsgroup comp.ai.neural-nets (as well as comp.answers and news.answers, where it should be findable at any time). Its purpose is to provide basic information for individuals who are new to the field of neural networks or who are just beginning to read this group. It will help to avoid lengthy discussion of questions that often arise for beginners. SO, PLEASE, SEARCH THIS POSTING FIRST IF YOU HAVE A QUESTION and DON'T POST ANSWERS TO FAQs: POINT THE ASKER TO THIS POSTING The latest version of the FAQ is available as a hypertext document, readable by any WWW (World Wide Web) browser such as Netscape, under the URL: ftp://ftp.sas.com/pub/neural/FAQ.html. If you are reading the version of the FAQ posted in comp.ai.neural-nets, be sure to view it with a monospace font such as Courier. If you view it with a proportional font, tables and formulas will be mangled. -

Case 15-10104-LSS Doc 309 Filed 04/08/15 Page 1 of 98
Case 15-10104-LSS Doc 309 Filed 04/08/15 Page 1 of 98 UNITED STATES BANKRUPTCY COURT FOR THE DISTRICT OF DELAWARE In re: Chapter 11 HIPCRICKET, INC.,1 Case No. 15-10104 (LSS) Debtor. AFFIDAVIT OF SERVICE STATE OF CALIFORNIA } } ss.: COUNTY OF LOS ANGELES } DARLEEN SAHAGUN, being duly sworn, deposes and says: 1. I am employed by Rust Consulting/Omni Bankruptcy, located at 5955 DeSoto Avenue, Suite 100, Woodland Hills, CA 91367. I am over the age of eighteen years and am not a party to the above-captioned action. 2. On April 3, 2015, I caused to be served the: a) Notice of (I) Conditional Approval of the Amended Disclosure Statement; (II) Hearing to Consider Confirmation of the Plan; (III) Deadline for Filing Objections to Confirmation of the Plan; (IV) Deadline for Voting on the Plan; and (V) Bar Date for Filing Administrative Claims Established by the Plan, (the “Notice”), b) Amended Plan of Reorganization of the Debtor Dated March 31, 2015 [Docket No. 293], c) Amended Disclosure Statement for the Plan of Reorganization of Hipcricket, Inc. [Docket No. 294], d) Committee Plan Support Letter (re: Recommendation of Creditors’ Committee in Favor of Chapter 11 Plan of Reorganization), (2a through 2d collectively referred to as the “Solicitation Package”) e) Class 3 General Unsecured Claims Ballot to Accept or Reject Chapter 11 Plan of Reorganization (the “Class 3 Ballot”), 1 The last four digits of the Debtor’s tax identification number are 2076. The location of the Debtor’s headquarters and the service address for the Debtor is 110 110th Avenue NE. -

Federal Depository Library Handbook
US Government Printing Office Federal Depository Library Program Federal Depository Library Handbook Federal Depository Library Handbook US Government Printing Office Library Services & Content Management, Library Planning & Development 732 N. Capitol St. NW, Washington, DC 20401 202-512-1800 • 866-512-1800 • Fax 202-512-2104 [email protected] Text highlighted in yellow refers to legal and/or program requirements for depository libraries. Preface The Federal Depository Library Handbook (Handbook), describes requirements of Federal depository libraries, both legal and those prescribed by the Government Printing Office (GPO). Additionally the Handbook provides guidance to libraries on how they can meet the requirements of the Federal Depository Library Program (FDLP). This information was previously found in two publications. Instructions to Depository Libraries contained the FDLP requirements while practical guidance for carrying out FDLP operations was in the Federal Depository Library Manual and its supplements. The Instructions and Manual are superseded by the Handbook. In accepting the privilege of Federal depository status for their libraries, directors agreed to abide by all the laws and requirements governing officially designated depository libraries. Recognizing this, chapter 2 of the Handbook outlines the legal requirements and each chapter of the Handbook includes a section for library administrators. These sections are also consolidated in Appendix C. Depository coordinators MUST ensure that all personnel involved in any aspect of depository operations are aware of the obligations of depository libraries and of the importance of the Handbook. Depository staff should review the Handbook on a regular basis and any questions can be directed to askGPO (http://www.gpoaccess.gov/help/index.html). -
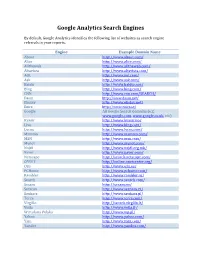
Google Analytics Search Engines
Google Analytics Search Engines By default, Google Analytics identifies the following list of websites as search engine referrals in your reports. Engine Example Domain Name About http://www.about.com/ Alice http://www.alice.com/ Alltheweb http://www.alltheweb.com/ Altavista http://www.altavista.com/ AOL http://www.aol.com/ Ask http://www.ask.com/ Baidu http://www.baidu.com/ Bing http://www.bing.com/ CNN http://www.cnn.com/SEARCH/ Daum http://www.daum.net/ Ekolay http://www.ekolay.net/ Eniro http://www.eniro.se/ Google All Google Search domains (e.g. www.google.com, www.google.co.uk, etc) Kvasir http://www.kvasir.no/ Live http://www.bing.com/ Lycos http://www.lycos.com/ Mamma http://www.mamma.com/ MSN http://www.msn.com/ Mynet http://www.mynet.com/ Najdi http://www.najdi.org.mk/ Naver http://www.naver.com/ Netscape http://search.netscape.com/ O*NET http://online.onetcenter.org/ Ozu http://www.ozu.es/ PCHome http://www.pchome.com/ Rambler http://www.rambler.ru/ Search http://www.search.com/ Sesam http://sesam.no/ Seznam http://www.seznam.cz/ Szukacz http://www.szukacz.pl/ Terra http://www.terra.com/ Virgilio http://search.virgilio.it/ Voila http://www.voila.fr/ Wirtulana Polska http://www.wp.pl/ Yahoo http://www.yahoo.com/ Yam http://www.yam.com/ Yandex http://www.yandex.com/ . -

Hoodwinked: Watching Movies with Eyes Wide Open Refers to an Ancient Term Used in Secret Societies
Contents Introduction..............................................................................................ix I. Poli-Sci-Fi (Political Science Fiction) 1. The Matrix': Sci-Fi, Metaphysics, and Soul Liberation ..................3 2. 'Minority Report': Spielberg's Psychic Dictatorship ......................11 3. 'The Postman': Reluctant Hero Delivers Hope .............................15 4. 'Solaris': Life Is A Trance................................................................19 5. 'Soldier': Future Cannon Fodder Goes High-Tech ..........................24 6. 'Sixth Day': Downtown Atlantis Revisited......................................26 7. 'Signs': Mel Gibson Loses His BS (Belief System) .......................30 8. 'Starship Troopers': Teenage Fascists Battle Giant Bugs ................36 9. 'The Truman Show': Storming the Reality Studio...........................40 10. 'The X-Files': When Conspiracies Collide ...................................43 II. Illuminati, Mind Control and Other PsyOps 11. 'Arlington Road': The Terrorist Next Door .....................................51 12. 'Avengers': Weather Control for Fun and Profit..............................55 13. 'Blade': Secrets of the Illuminati ...................................................59 14. 'Conspiracy Theory': Deconstructing Hidden History......................64 15. 'Dark Angel': The Threat of Digital Slavery ...................................70 16. 'Disturbing Behavior': Mind Control High School..........................78 17. 'Eyes Wide Shut': Occult Entertainment -

Numbers Are Footnotes for Positions Referenced Below
Gary L. Wade 320 Crescent Village Circle Unit 1396 San Jose, CA 95134 [email protected] 949-505-3223 KEY EXPERIENCES • Passion for developing solutions for Apple Inc.’s platforms (macOS, iOS, tvOS, watchOS) • Innovative in usability design and testing, and refactoring for performance • Design and development of multi-platform client/server/cloud software solutions • Facilitate instruction for technical and non-technical staff including one-on-one mentoring CURRENT TALENT SUMMARY (numbers are footnotes for positions referenced below) • Adobe Photoshop (24,17,10,9,8,1) • Macintosh (Mac OS X) SDK (28,27,26,21,20, • AppKit/macOS (28,27,26,21,20,19,18,17,1) 19,18,17,16,15,14,13,12,11,8,7,6,5,4,2,1) • C (28,27,26,24,23,22,21,20,19,18,17,16,15,14, • Objective-C (28,27,26,24,23,22,21,20,19,18, 13,12,11,8,7,6,5,4,1) 17,1) • C++ (21,20,18,17,16,15,14,13,12,11,8,7,6,5,1) • Perforce (21,20,15) • Client/Server/Cloud (28,27,26,25,24,22,21,20, • Quality Assurance (25,24,17,3,1) 19,18,17,16,13,7,6,4) • QuickTime/AVKit (25,24,22,17,13,10,9,6,5) • Cocoa (28,27,26,25,24,23,22,21,20,19,18,17,1) • REST (28,27,26,25,24,22,21) • CoreFoundation (28,27,26,22,21,20,18,17,16, • Sales support (21,10,9,6,1) 15,14,13,12,1) • sqlite (23) • Cross-platform (28,27,21,20,17,15,14,13,12,8, • Subversion (27,22,19,18,1) 7,6,5,4,2) • Swift (28,27,26,25,24) • git (28,27,26,25,24,23,22) • UIKit/iOS (28,27,26,24,23,22,1) • HTML (28,27,26,25,17,14,12,10,9,1) • UIKit/tvOS (25) • Int. -

By Michael L. Black Dissertation
TRANSPARENT CULTURES: IMAGINED USERS AND THE POLITICS OF SOFTWARE DESIGN (1975-2012) BY MICHAEL L. BLACK DISSERTATION Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in English in the Graduate College of the University of Illinois at Urbana-Champaign, 2014 Urbana, Illinois Doctoral Committee: Professor Robert Markley, Chair Associate Professor Ted Underwood Associate Professor Melissa Littlefield Associate Professor Spencer Schaffner Associate Professor John T. Newcomb ii Abstract The rapid pace of software’s development poses serious challenges for any cultural history of computing. While digital media studies often sidestep historicism, this project asserts that computing’s messy, and often hidden, history can be studied using digital tools built to adapt text-mining strategies to the textuality of source code. My project examines the emergence of personal computing, a platform underlying much of digital media studies but that itself has received little attention outside of corporate histories. Using an archive of technical papers, professional journals, popular magazines, and science fiction, I trace the origin of design strategies that led to a largely instrumentalist view of personal computing and elevated “transparent design” to a privileged status. I then apply text-mining tools that I built with this historical context in mind to study source code critically, including those features of applications hidden by transparent design strategies. This project’s first three chapters examine how and why strategies of information hiding shaped consumer software design from the 1980s on. In Chapter 1, I analyze technical literature from the 1970s and 80s to show how cognitive psychologists and computer engineers developed an ideal of transparency that discouraged users from accessing information structures underlying personal computers. -

Start-Up Space Report 2020
Start-Up Space Update on Investment in Commercial Space Ventures 2020 i Bryce Space and Technology brycetech.com CONTENTS EXECUTIVE SUMMARY ........................................... III INTRODUCTION. 1 Purpose and Background . 1 Methodology ...................................................1 OVERVIEW OF START-UP SPACE VENTURES. 3 TYPES OF SPACE INVESTOR ......................................4 SPACE INVESTMENT BY THE NUMBERS ...........................11 Seed Funding . 15 Venture Capital . 16 Private Equity . 17 Acquisition ...................................................18 Public Offering ................................................19 Debt Financing . 19 Investment Across All Types .....................................19 Valuation ....................................................21 Casualties ...................................................22 SPACE INVESTORS BY THE NUMBERS ............................23 Overall ......................................................23 Angels ......................................................27 Venture Capital Firms . 28 Private Equity Groups ..........................................31 Corporations . 32 Banks and Other Financial Institutions .............................33 SPECIAL TOPIC: CHINESE ACTIVITY IN START-UP SPACE VENTURES. 35 START-UP SPACE: WHAT’S NEXT?. 38 ACKNOWLEDGEMENTS. 41 ii brycetech.com Bryce Space and Technology EXECUTIVE SUMMARY Three significant trends are shaping the start-up space environment as we enter the 2020s. First, investors continue to pour large amounts -

School Board of National School Boards Association
DOCUMENT RESUME ED 410 678 EA 028 578 TITLE Bringing Tomorrow's Technology to You Today: School Board of Tomorrow Resource Guide. INSTITUTION National School Boards Association, Alexandria, VA. PUB DATE 1997-04-00 NOTE 34p.; Guide to an exhibit at the Annual Meeting of the National School Boards Association (Anaheim, CA, April 26-29, 1997). PUB TYPE Guides Non-Classroom (055) EDRS PRICE MF01/PCO2 Plus Postage. DESCRIPTORS *Boards of Education; *Computer Mediated Communication; Computer Networks; *Computer System Design; Corporate Support; *Educational Technology; Electronic Mail; Elementary Secondary Education; Information Management; Information Networks; Information Services; Information Systems; *Information Technology; *Telecommunications ABSTRACT The National School Boards Association (NSBA), the National School Boards Foundation, NSBA's Institute for the Transfer of Technology to Education, and Apple Computer, Inc., launched "The School Board of Tomorrow Exhibit" at NSBA's 1996 annual conference and exposition in Orlando, Florida. This handbook summarizes the communication technologies featured in the exhibit. The first part provides an overview of the five different environments simulated in the exhibit: a school board member's home office, the family education network (FEN), a superintendent's office, a school board meeting room, and a community forum. The second part of this guide contains five selected NSBA articles from "The Electronic School." The articles offer advice and information on hiring technical constOtants for a school district, conducting successful bond campaigns, using e-mail to conduct school board business, and acquiring funding for technology. A list of technology providers is included. (LMI) ******************************************************************************** Reproductions supplied by EDRS are the best that can be made from the original document. -

Aquene Freechild Submission
Different Comments: Please strengthen Voluntary Voting System Guidelines First Name Last Name Email Date submitted Comment for interference through cyberattacks, it is imperative the VVSG prohibit connectivity to the public Internet through wireless modems or other means. We want to ban modems in vote counting machines both to protect data and to prevent manipulation. Therefore, we urge the Commission to add the following to the guideline under Principle 13: DATA PROTECTION: 'The voting system does not use wireless technology or connect to any public jenbigelow@ 2019-05-02 telecommunications infrastructure.' Indeed, eliminating Jennifer Bigelow hotmail.com 23:32:32 GMT wireless modems and internet connectivity will not the draft Voluntary Voting System Guidelines (VVSG) and commend the robust principles and guidelines for software independence, auditability and ballot secrecy. Given the fact that our election systems are being targeted for interference through cyberattacks, it is imperative the VVSG also prohibit connectivity to the public Internet through wireless modems or other means. We want to ban modems in vote counting machines both to protect data and to prevent manipulation. Therefore, we urge the Commission to add the following to the guideline under bobjanz01@ 2019-05-03 Principle 13: DATA PROTECTION: 'The voting system does Bob JANZ gmail.com 00:43:14 GMT not use wireless technology or connect to any public computer science. As such I speak with some authority when I say I strongly support the draft Voluntary Voting System Guidelines (VVSG). I commend the robust principles and guidelines for software independence, auditability and ballot secrecy. Given the fact that our election systems are being targeted for interference through cyberattacks, it is imperative the VVSG also prohibit connectivity to the public Internet through wireless modems or other means.